Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article discusses how to disable basic username and password authentication for deploying code to Azure App Service apps. The article explains several ways to disable basic authentication, fallback deployment methods if any, and how to monitor basic authentication access attempts.
App Service provides basic authentication for FTP and Web Deploy clients to connect using username and password deployment credentials. The basic authentication APIs are good for browsing your site's file system, uploading drivers and utilities, and deploying with MSBuild. For more information, see Configure deployment credentials for Azure App Service.
Enterprises often require more secure deployment methods than basic authentication, such as Microsoft Entra ID. Microsoft Entra OAuth 2.0 access tokens have a limited usable lifetime, are specific to the applications and resources they're issued for, and can't be reused. OAuth token-based authorization helps mitigate many problems with basic authentication.
Microsoft Entra also lets you deploy from other Azure services by using managed identities. For more information, see Authentication types by deployment method in Azure App Service.
Prerequisites
- To disable basic authentication for FTP access to an app, you must have owner-level access to the app.
- To create and assign a role to prevent lower-privileged users from enabling basic authentication, you must have Owner or User Access Administrator permissions in the subscription.
Disable basic authentication
For FTP deployment, basic authentication is controlled by the basicPublishingCredentialsPolicies/ftp flag or the FTP Basic Auth Publishing Credentials portal option.
For other deployment methods that use basic authentication, such as Visual Studio, local Git, and GitHub, basic authentication is controlled by the basicPublishingCredentialsPolicies/scm flag or the SCM Basic Auth Publishing Credentials portal option.
Note
SCM basic authentication is required for enabling FTP basic authentication.
To disable basic authentication:
In the Azure portal, search for and select App Services, and then select your app.
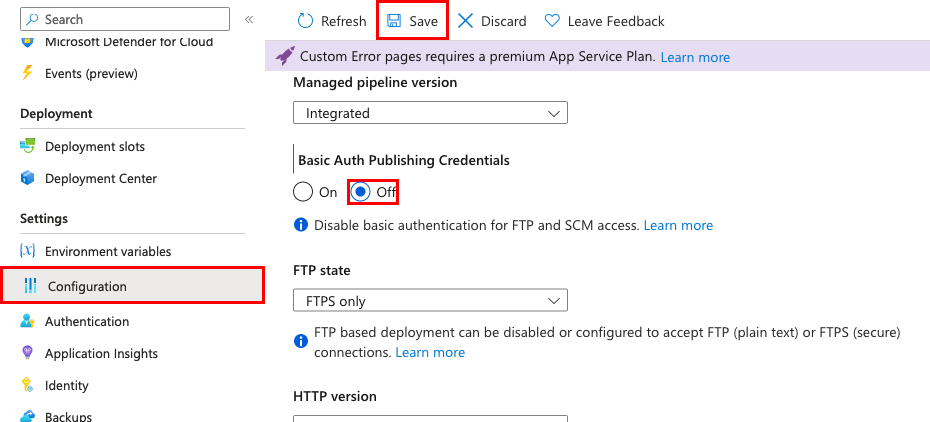
On the app's left navigation menu, select Configuration > General settings.
Select Off for SCM Basic Auth Publishing Credentials, FTP Basic Auth Publishing Credentials, or both, and then select Save.
To confirm that FTP access is blocked, try to connect to your app using FTP/FTPS. You should get a 401 Unauthenticated message.
To confirm that Git access is blocked, try local Git deployment. You should get an Authentication failed message.
Deploy without basic authentication
When you disable basic authentication, deployment methods that depend on basic authentication no longer work. Some deployment methods have fallback deployment mechanisms.
The following table shows how various deployment methods behave when basic authentication is disabled, and the fallback mechanism if any. For more information, see Authentication types by deployment methods in Azure App Service.
| Deployment method | When basic authentication is disabled |
|---|---|
| Visual Studio deployment | Deployment with Microsoft Entra authentication requires Visual Studio 2022 version 17.12 or later. |
| FTP | Doesn't work. |
| Local Git | Doesn't work. |
| Azure CLI | In Azure CLI 2.48.1 or higher, the following commands fall back to Microsoft Entra authentication:az webapp up.az webapp deploy.az webapp log deployment show.az webapp log deployment list.az webapp log download.az webapp log tail.az webapp browse.az webapp create-remote-connection.az webapp ssh.az functionapp deploy.az functionapp log deployment list.az functionapp log deployment show.az functionapp deployment source config-zip. |
| Maven plugin or Gradle plugin | Works. |
| Deployment from the portal creation wizard | If you select a Continuous deployment source when Basic authentication is set to Disable, GitHub Actions is configured with the user-assigned identity option (OpenID Connect). |
Create a custom role to prevent enabling basic authentication
To prevent lower-privileged users from enabling basic authentication for any app, you can create a custom role and assign the users to the role.
In the Azure portal, select the subscription where you want to create the custom role.
On the left navigation menu, select Access Control (IAM) > Add > Add custom role.
On the Create a custom role page, give the role a name and then select Next.
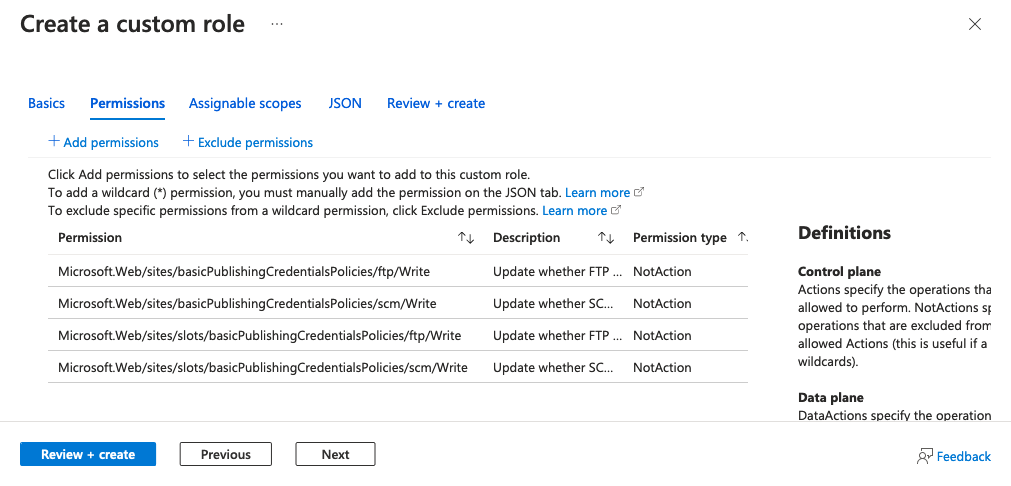
In the Permissions tab, select Exclude permissions.
Search and select Microsoft Web Apps.
Search for and expand microsoft.web/sites/basicPublishingCredentialsPolicies.
Select the box for Write, and then select Add. This step adds the operation to NotActions for the role.
Select Exclude permissions again.
Search for and expand microsoft.web/sites/slots/basicPublishingCredentialsPolicies, select the Write box, and then select Add.
Your Permissions tab should now look like the following screenshot. Select Review + create, and then select Create.
You can now assign this role to your organization's users. For more information, see Create or update Azure custom roles by using the Azure portal.
Monitor for basic authentication attempts
All successful and attempted logins are logged to the Azure Monitor AppServiceAuditLogs log type. To audit attempted and successful logins on FTP and Web Deploy, follow the steps at Send logs to Azure Monitor and enable shipping of the AppServiceAuditLogs log type.
To confirm that the logs are shipped to your selected services, try logging in via FTP or Web Deploy. The following example shows a storage account log.
{
"time": "2023-10-16T17:42:32.9322528Z",
"ResourceId": "/SUBSCRIPTIONS/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/RESOURCEGROUPS/MYRESOURCEGROUP/PROVIDERS/MICROSOFT.WEB/SITES/MY-DEMO-APP",
"Category": "AppServiceAuditLogs",
"OperationName": "Authorization",
"Properties": {
"User": "$my-demo-app",
"UserDisplayName": "$my-demo-app",
"UserAddress": "24.19.191.170",
"Protocol": "FTP"
}
}
Use basic authentication-related policies
Azure Policy can help you enforce organizational standards and assess compliance at scale. You can use Azure Policy to audit for any apps that still use basic authentication, and remediate any noncompliant resources. The following list shows built-in policies for auditing and remediating basic authentication on App Service:
The following list shows corresponding policies for slots: