Renew certificates for Network Controller
Applies to: Azure Stack HCI, versions 22H2; Windows Server 2022 and Windows Server 2019
This article provides instructions on how to renew or change Network Controller certificates, both automatically and manually. If you face any issues in renewing your Network Controller certificates, contact Azure Support.
In your Software Defined Networking (SDN) infrastructure, the Network Controller uses certificate-based authentication to secure Northbound communication channels with management clients and Southbound communications with network devices, such as the Software Load Balancer. The Network Controller certificates come with a validity period, after which they become invalid and can no longer be trusted for use. We highly recommend that you renew them before they expire.
For an overview of Network Controller, see What is Network Controller?
When to renew or change Network Controller certificates
You can renew or change Network Controller certificates when:
The certificates are nearing expiry. You can indeed renew Network Controller certificates at any point before they expire.
Note
If you renew existing certificates with the same key, you are all set and don't need to do anything.
You want to replace a self-signed certificate with a Certificate Authority (CA)-signed certificate.
Note
While changing the certificates, ensure that you use the same subject name as of the old certificate.
Types of Network Controller certificates
In Azure Stack HCI, each Network Controller VM uses two types of certificates:
REST certificate. A single certificate for Northbound communication with REST clients (such as Windows Admin Center) and Southbound communication with Hyper-V hosts and software load balancers. This same certificate is present on all Network Controller VMs. To renew REST certificates, see Renew REST certificates.
Network Controller node certificate. A certificate on each Network Controller VM for inter-node authentication. To renew Network Controller node certificates, see Renew node certificates.
Warning
Don't let these certificate expire. Renew them before expiry to avoid any authentication issues. Also, don't remove any existing expired certificates before renewing them. To find out the expiration date of a certificate, see View certificate expiry.
View certificate expiry
Use the following cmdlet on each Network Controller VM to check the expiration date of a certificate:
Get-ChildItem Cert:\LocalMachine\My | where{$_.Subject -eq "CN=<Certificate-subject-name>"} | Select-Object NotAfter, Subject
To get the expiry of a REST certificate, replace "Certificate-subject-name" with the RestIPAddress or RestName of the Network Controller. You can get this value from the
Get-NetworkControllercmdlet.To get the expiry of a node certificate, replace "Certificate-subject-name" with the fully qualified domain name (FQDN) of the Network Controller VM. You can get this value from the
Get-NetworkControllercmdlet.
Renew Network Controller certificates
You can renew your Network Controller certificates either automatically or manually.
The Start-SdnCertificateRotation cmdlet enables you to automate renewal of your Network Controller certificates. Certificate automatic renewal helps minimize any downtime or unplanned outages caused due to certificate expiry issues.
Here are the scenarios where you can use the Start-SdnCertificateRotation cmdlet to automatically renew Network Controller certificates:
- Self-signed certificates. Use the
Start-SdnCertificateRotationcmdlet to generate self-signed certificates and renew those certificates in all the Network Controller nodes. - Bring your own certificates. You bring your own certificates, either self-signed or CA-signed and use the
Start-SdnCertificateRotationcmdlet for certificate renewal. The cmdlet installs the certificates on all the Network Controller nodes and distributes them to other SDN infrastructure components. - Preinstalled certificates. You have the required certificates already installed on the Network Controller nodes. Use the
Start-SdnCertificateRotationcmdlet to renew those certificates to other SDN infrastructure components.
For more information about how to create and manage SDN certificates, see Manage certificates for Software Defined Networking.
Requirements
Here are the requirements for automatic renewal of certificate:
You must run the
Start-SdnCertificateRotationcmdlet on one of the Network Controller nodes. For installation instructions, see Install SdnDiagnostics module.You must have credentials for the following two types of accounts to authorize communication between Network Controller nodes:
Credentialto specify a user account with local admin privileges on Network Controller.NcRestCredentialto specify a user account with access to Network Controller REST API. It's a member ofClientSecurityGroupfromGet-NetworkController. This account is used to call REST API to update credential resource with the new certificate.
For more information about configuring authorization for Network Controller Northbound communication, see Authorization for Northbound communication.
Renew self-signed certificates automatically
You can use the Start-SdnCertificateRotation cmdlet to generate new self-signed certificates and automatically renew them to all the Network Controller nodes. By default, the cmdlet generates certificates with a validity period of three years, but you can specify a different validity period.
Perform these steps on one of the Network Controller nodes to generate self-signed certificates and automatically renew them:
To generate self-signed certificates, run the
Start-SdnCertificateRotationcmdlet. You can use the-Forceparameter with the cmdlet to avoid any prompts for confirmation or manual inputs during the rotation process.To generate self-signed certificates with the default three years validity period, run the following commands:
Import-Module -Name SdnDiagnostics -Force Start-SdnCertificateRotation -GenerateCertificate -CertPassword (Get-Credential).Password -Credential (Get-Credential)To generate self-signed certificates with a specific validity period, use the
NotAfterparameter to specify the validity period.For example, to generate self-signed certificates with a validity period of five years, run the following commands:
Import-Module -Name SdnDiagnostics -Force Start-SdnCertificateRotation -GenerateCertificate -CertPassword (Get-Credential).Password -NotAfter (Get-Date).AddYears(5) -Credential (Get-Credential)
Enter the credentials. You get two prompts to provide two types of credentials:
- In the first prompt, enter the password to protect the generated certificate. The username can be anything and isn't used.
- In the second prompt, use the credential that has admin access to all the Network Controller nodes.
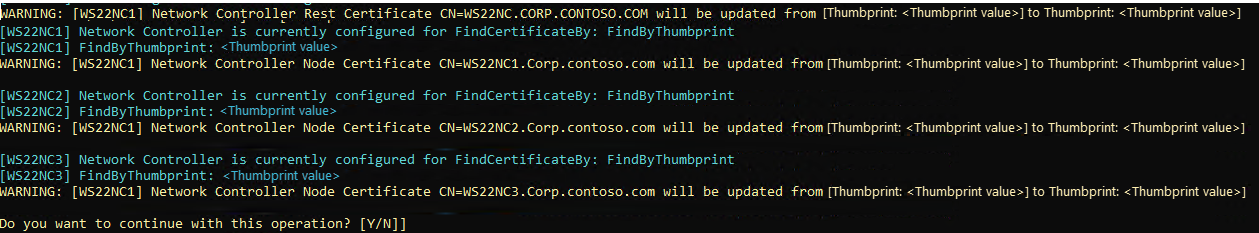
After the new certificates are generated, you get a warning to confirm if you want to continue with the certificate rotation process. The warning text displays the list of Network Controller certificates that will be replaced with the newly generated ones. Type
Yto confirm.Here's a sample screenshot of the warning:
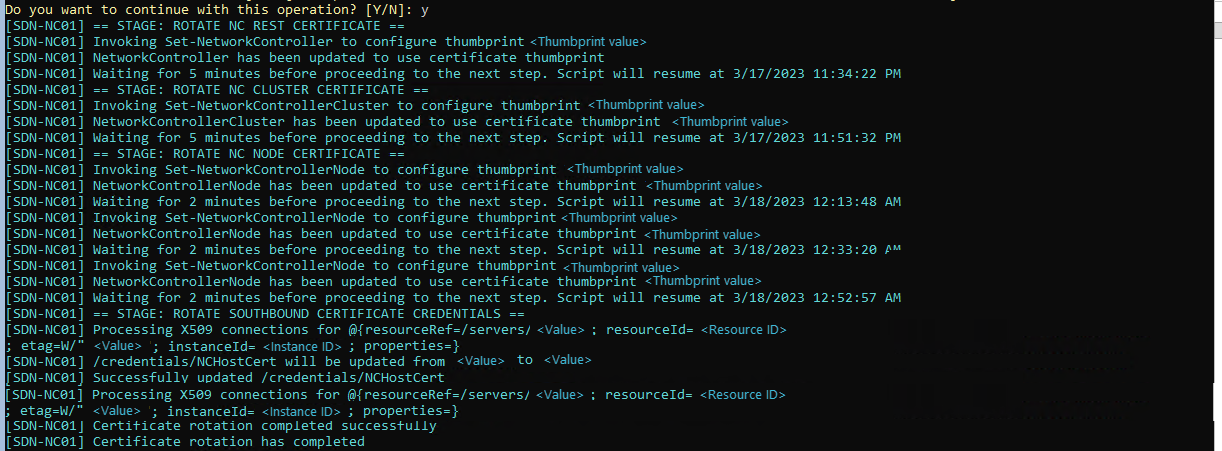
After you confirm to continue with the certificate rotation, you can view the status of the ongoing operations in the PowerShell command window.
Important
Don't close the PowerShell window until the cmdlet finishes. Depending on your environment, such as the number of Network Controller nodes in the cluster, it may take several minutes or more than an hour to finish.
Here's a sample screenshot of the PowerShell command window showing the status of ongoing operations:
Renew your own certificates automatically
In addition to generating self-signed Network Controller certificates, you can also bring your own certificates, either self-signed or CA-signed, and use the Start-SdnCertificateRotation cmdlet to renew those certificates.
Perform these steps on one of the Network Controller nodes to automatically renew your own certificates:
Prepare your certificates in
.pfxformat and save in a folder on one of the Network Controller nodes from where you run theStart-SdnCertificateRotationcmdlet. You can use the-Forceparameter with the cmdlet to avoid any prompts for confirmation or manual inputs during the rotation process.To start certificate renewal, run the following commands:
Import-Module -Name SdnDiagnostics -Force Start-SdnCertificateRotation -CertPath "<Path where you put your certificates>" -CertPassword (Get-Credential).Password -Credential (Get-Credential)Enter the credentials. You get two prompts to provide two types of credentials:
- In the first prompt, enter the password of your certificate. The username can be anything and isn't used.
- In the second prompt, use the credential that has admin access to all the Network Controller nodes.
You get a warning to confirm if you want to continue with the certificate rotation process. The warning text displays the list of Network Controller certificates that will be replaced with the newly generated ones. Type
Yto confirm.Here's a sample screenshot of the warning:
After you confirm to continue with the certificate rotation, you can view the status of the ongoing operations in the PowerShell command window.
Important
Don't close the PowerShell window until the cmdlet finishes. Depending on your environment, such as the number of Network Controller nodes in the cluster, it may take several minutes or more than an hour to finish.
Renew preinstalled certificates automatically
In this scenario, you have the required certificates installed on the Network Controller nodes. Use the Start-SdnCertificateRotation cmdlet to renew those certificates on other SDN infrastructure components.
Perform these steps on one of the Network Controller nodes to automatically renew the preinstalled certificates:
Install the Network Controller certificates on all the Network Controller nodes as per your preferred method. Ensure the certificates are trusted by other SDN infrastructure components, including SDN MUX servers and SDN hosts.
Create certificate rotation configuration:
To generate the default certificate rotation configuration, run the following commands:
Import-Module -Name SdnDiagnostics -Force $certConfig = New-SdnCertificateRotationConfig $certConfigReview the default certificate rotation configuration to confirm if the auto-detected certificates are the ones that you want to use. By default, it retrieves the latest issued certificate to be used.
Here's a sample certificate rotation configuration:
PS C:\Users\LabAdmin> $certConfig Name Value ---- ----- ws22ncl.corp.contoso.com F4AAF14991DAF282D9056E147AE60C2C5FE80A49 ws22nc3.corp.contoso.com BC3E6B090E2AA80220B7BAED7F8F981A1E1DD115 ClusterCredentialType X509 ws22nc2.corp.contoso.corn 75DC229A8E61AD855CC445C42482F9F919CC1077 NcRestCert 029D7CA0067A60FB24827D8434566787114AC30Cwhere:
- ws22ncx.corp.contoso.com shows the certificate's thumbprint for each Network Controller node.
- ClusterCredentialType shows the Network Controller Cluster authentication type. If the authentication type isn't X509, the node certificate isn't used and isn't shown in the output.
- NcRestCert shows the thumbprint of the Network Controller Rest certificate.
(Optional) If the generated
$certConfigisn't correct, you can change it by specifying a new certificate's thumbprint. For example, to change the thumbprint of the Network Controller Rest certificate, run the following command:$certConfig.NcRestCert = <new certificate thumbprint>
Start certificate rotation. You can use the
-Forceparameter with the cmdlet to avoid any prompts for confirmation or manual inputs during the rotation process.Import-Module -Name SdnDiagnostics -Force Start-SdnCertificateRotation -CertRotateConfig $certConfig -Credential (Get-Credential)When prompted for credentials, enter the credential that has admin access all Network Controller Nodes.
You get a warning to confirm if you want to continue with auto rotation of certificates. The warning displays the list of Network Controller certificates that will be replaced with your own certificates. Type
Yto confirm.Here's a sample screenshot of the warning that prompts you to confirm the rotation of certificates:
After you confirm to continue with the certificate rotation, you can view the status of the ongoing operations in the PowerShell command window.
Important
Don't close the PowerShell window until the cmdlet finishes. Depending on your environment, such as the number of Network Controller nodes in the cluster, it may take several minutes or more than an hour to finish.
Re-import certificates in Windows Admin Center
If you have renewed the Network Controller REST certificate and you are using Windows Admin Center to manage SDN, you must remove the Azure Stack HCI cluster from Windows Admin Center and add it again. By doing this, you ensure that Windows Admin Center imports the renewed certificate and uses it for SDN management.
Follow these steps to re-import the renewed certificate in Windows Admin Center:
- In Windows Admin Center, select Cluster Manager from the top drop-down menu.
- Select the cluster you want to remove and then select Remove.
- Select Add, enter the cluster name, and then select Add.
- Once the cluster is loaded, select SDN Infrastructure. This forces Windows Admin Center to automatically re-import the renewed certificate.