Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Warning
This is not a security posture feature. Use it in scenarios where you want constraints to prevent accidental changes to the Azure Subscription. When a user is delegated rights to this custom role, the user has rights to edit permissions and elevate rights. Only assign users you trust to the custom role.
During Azure Stack Hub registration, you must sign in with a Microsoft Entra account. The account requires the following Microsoft Entra permissions and Azure Subscription permissions:
App registration permissions in your Microsoft Entra tenant: Admins have app registration permissions. The permission for users is a global setting for all users in the tenant. To view or change the setting, see create a Microsoft Entra app and service principal that can access resources.
The user can register applications setting must be set to Yes for you to enable a user account to register Azure Stack Hub.
A set of sufficient Azure Subscription permissions: Users that belong to the Owner role have sufficient permissions. For other accounts, you can assign the permission set by assigning a custom role as outlined in the following sections.
Rather than using an account that has Owner permissions in the Azure subscription, you can create a custom role to assign permissions to a less-privileged user account. This account can then be used to register your Azure Stack Hub.
Create a custom role using PowerShell
To create a custom role, you must have the Microsoft.Authorization/roleDefinitions/write permission on all AssignableScopes, such as Owner or User Access Administrator. Use the following JSON template to simplify creation of the custom role. The template creates a custom role that allows the required read and write access for Azure Stack Hub registration.
Create a JSON file. For example,
C:\CustomRoles\registrationrole.json.Add the following JSON to the file. Replace
<SubscriptionID>with your Azure subscription ID.{ "Name": "Azure Stack Hub registration role", "Id": null, "IsCustom": true, "Description": "Allows access to register Azure Stack Hub", "Actions": [ "Microsoft.Resources/subscriptions/resourceGroups/write", "Microsoft.Resources/subscriptions/resourceGroups/read", "Microsoft.AzureStack/registrations/*", "Microsoft.AzureStack/register/action", "Microsoft.Authorization/roleAssignments/read", "Microsoft.Authorization/roleAssignments/write", "Microsoft.Authorization/roleAssignments/delete", "Microsoft.Authorization/permissions/read", "Microsoft.Authorization/locks/read", "Microsoft.Authorization/locks/write" ], "NotActions": [ ], "AssignableScopes": [ "/subscriptions/<SubscriptionID>" ] }In PowerShell, connect to Azure to use Azure Resource Manager. When prompted, authenticate using an account with sufficient permissions such as Owner or User Access Administrator.
Connect-AzAccount -EnvironmentName AzureChinaCloudTo create the custom role, use New-AzRoleDefinition specifying the JSON template file.
New-AzRoleDefinition -InputFile "C:\CustomRoles\registrationrole.json"
Assign a user to registration role
After the registration custom role is created, assign the role to the user account that will be used for registering Azure Stack Hub.
Sign in with the account with sufficient permission on the Azure subscription to delegate rights--such as Owner or User Access Administrator .
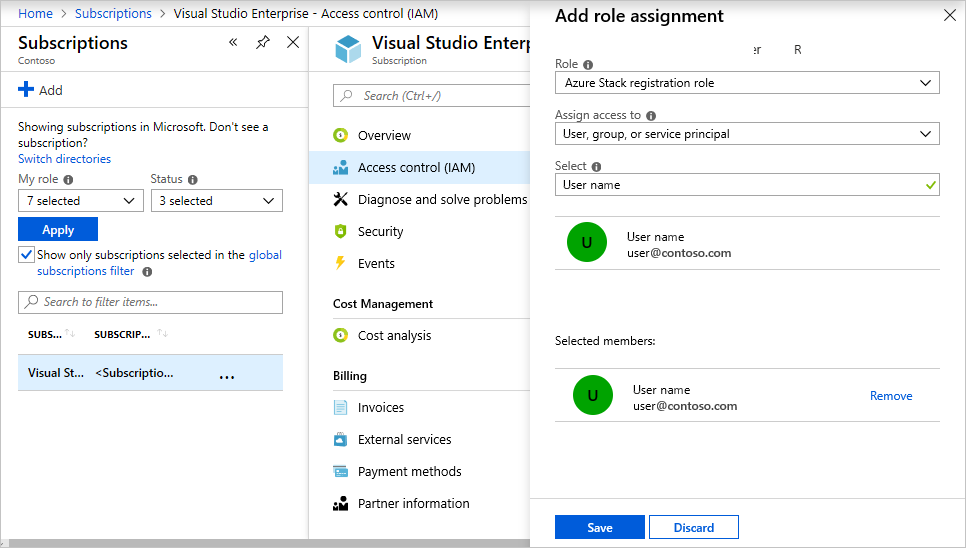
In Subscriptions, select Access control (IAM) > Add role assignment.
In Role, choose the custom role you created: Azure Stack Hub registration role.
Select the users you want to assign to the role.
Select Save to assign the selected users to the role.
For more information on using custom roles, see manage access using RBAC and the Azure portal.