Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
What is Conditional Access?
The modern security perimeter extends beyond an organization's network to include user and device identity. Organizations can use identity-driven signals as part of their access control decisions. You can use Microsoft Entra Conditional Access to bring signals together, to make decisions, and enforce organizational policies.
Conditional Access policies at their simplest are like if-then statements. If a user wants to access a resource, then they must complete an action. For example, a data engineer wants to access Azure Data Explorer but is required to do multi-factor authentication (MFA) to access it.
In the following example, you'll learn how to configure a Conditional Access policy that enforces MFA for selected users using the Azure Data Explorer web UI. You can use the same steps to create other policies to meet your organization's security requirements.
Prerequisites
Using this feature requires a Microsoft Entra ID P1 or P2 license. To find the right license for your requirements, see Compare available features of Microsoft Entra ID.
Note
Conditional Access policies are only applied to Azure Data Explorer's data administration operations and don't affect any resource administration operations.
Tip
Conditional Access policies are applied at the tenant level; hence, it's applied to all clusters in the tenant.
Configure Conditional Access
Sign in to the Azure portal as at least a Conditional Access Administrator.
Browse to Microsoft Entra ID > Security > Conditional Access.
Select New policy.
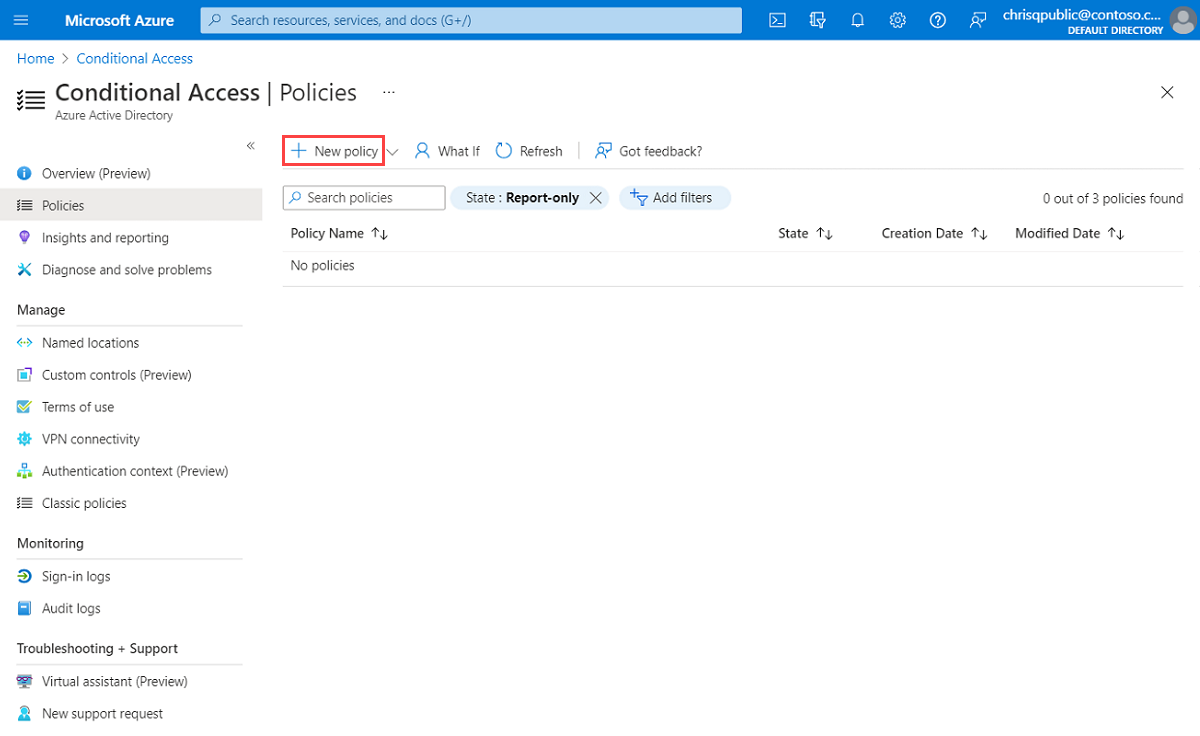
Give your policy a name. We recommend that organizations create a meaningful standard for the names of their policies.
Under Assignments, select Users and groups. Under Include > Select users and groups, select Users and groups, add the user or group you want to include for Conditional Access, and then select Select.
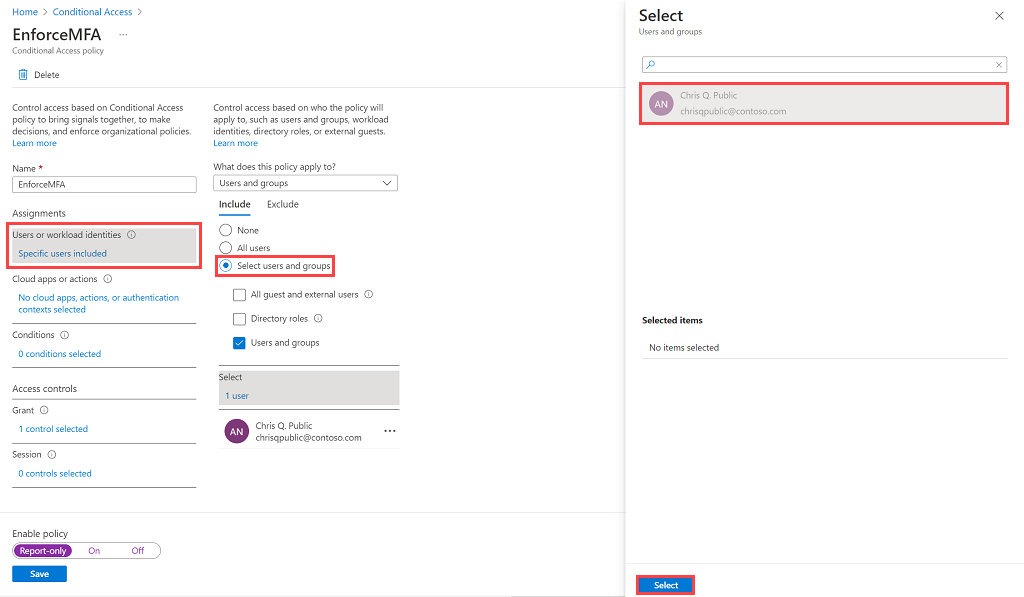
Under Cloud apps or actions, select Cloud apps. Under Include, select Select apps to see a list of all apps available for Conditional Access. Select Azure Data Explorer > Select.
Note
In some cases, the application name might be displayed as KustoService.
Tip
Please make sure you select the Azure Data Explorer app with the following GUID: 2746ea77-4702-4b45-80ca-3c97e680e8b7.
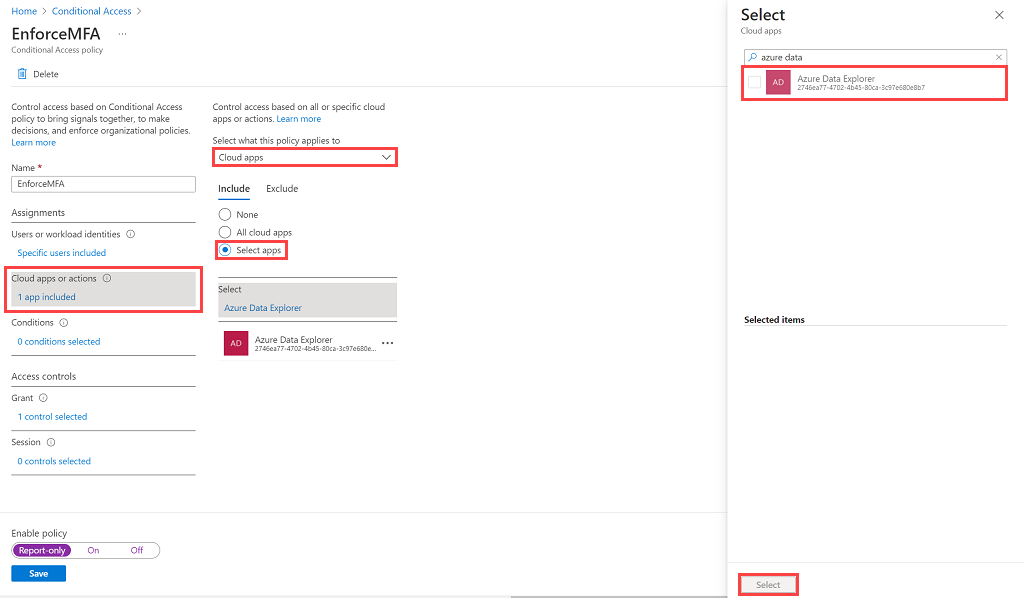
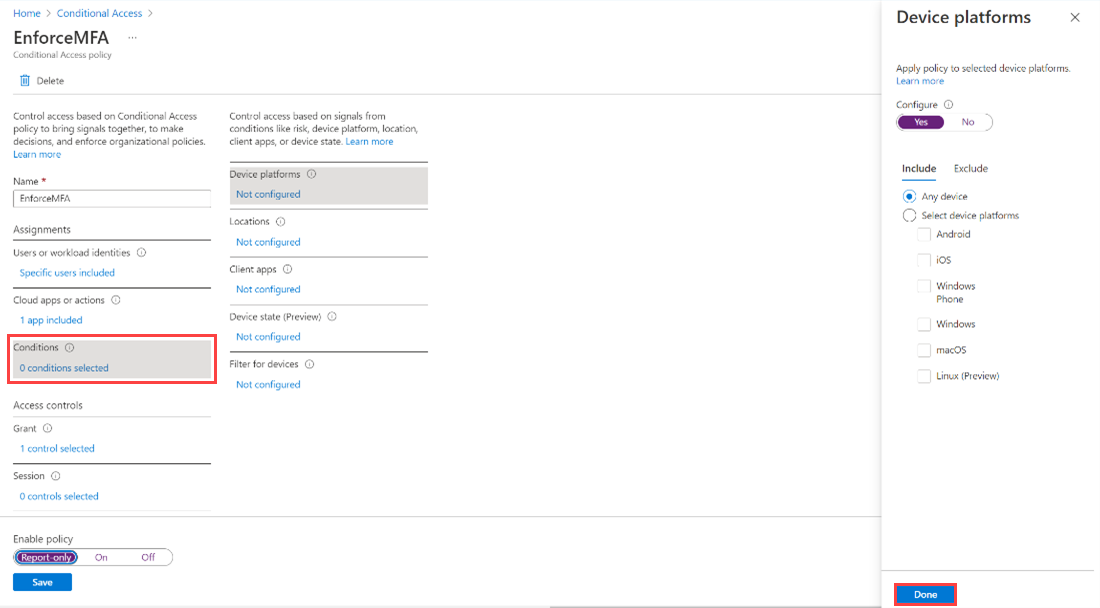
Under Conditions, set the conditions you want to apply for all device platforms and then select Done. For more information, see Microsoft Entra Conditional Access : Conditions.
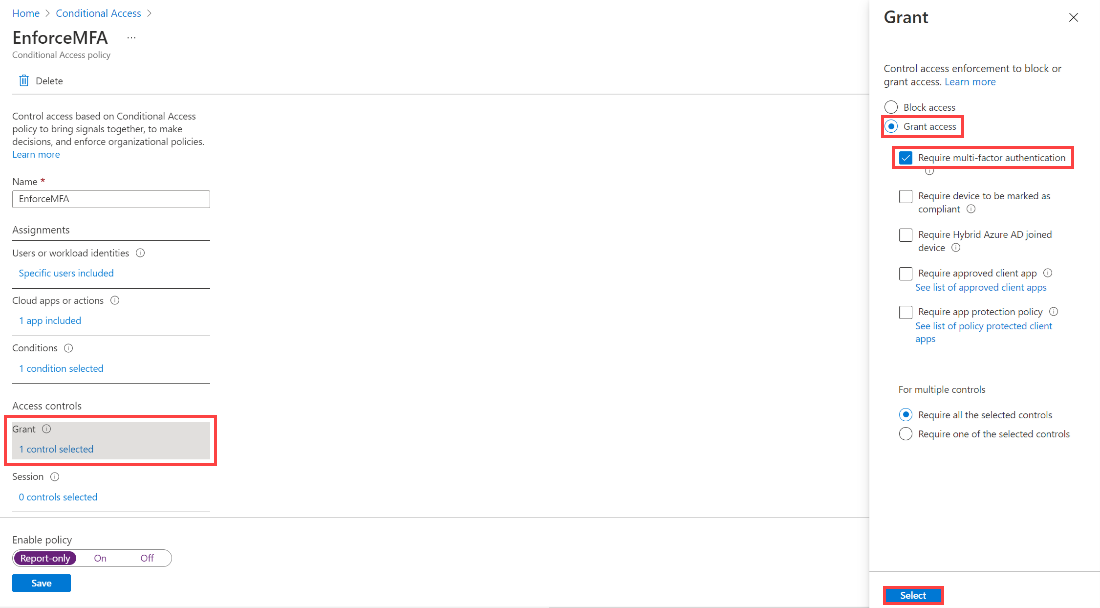
Under Access controls, select Grant, select Require multi-factor authentication, and then select Select.
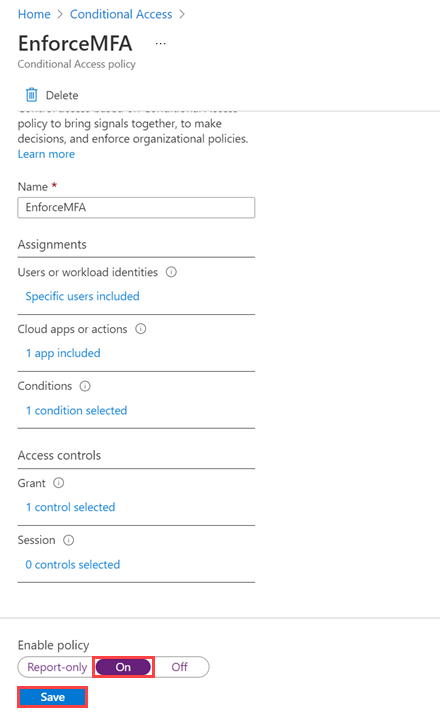
Set Enable policy to On, and then select Save.
Verify the policy by asking an assigned user to access the Azure Data Explorer web UI. The user should be prompted for MFA.