Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Restricting outbound access of your cluster is important to mitigate risks like data exfiltration. A malicious actor could potentially create an external table to a storage account and extract large amounts of data. You can control outbound access at the cluster level by enabling restricted outbound access and configuring either FQDN-based allowlists or callout policies.
Important
You can configure either the FQDN-based allowlist or callout policies for restricted outbound access. Configuring both results in an error.
Data Exfiltration Protection
Data exfiltration is a significant concern for enterprises, especially when sensitive or proprietary data is stored in clusters. Without proper controls, malicious actors or misconfigured systems could potentially transfer data to unauthorized external destinations.
The restricted outbound access feature helps mitigate this risk by allowing you to:
- Restrict outbound traffic: Prevent unauthorized data transfers by blocking all outbound traffic except to explicitly allowed destinations.
- Control access with FQDN-based allowlists: Specify the exact Fully Qualified Domain Names (FQDNs) that the cluster can communicate with, ensuring data is only sent to trusted endpoints.
- Enforce callout policies: Define granular rules for specific types of outbound traffic, such as SQL or external data calls, to allow or deny access based on your organization's security requirements.
By implementing restricted outbound access, enterprises can ensure that their Azure Data Explorer clusters are protected against data exfiltration risks, aligning with compliance and security standards.
Enable or disable restricted outbound access
You can enable or disable restricted outbound access at the ARM layer by configuring the restrictOutboundNetworkAccess property in your cluster's ARM template.
Once restricted outbound access is enabled, you can't make changes to the callout policy using the .alter or .alter-merge cluster policy callout commands. To make changes to the callout policy, update the allowedFqdnList or the allowedCallout property in the ARM template or using the Azure CLI.
Example: Enable restricted outbound access
The following ARM template enables restricted outbound access for your cluster:
In the following example, replace <ClusterName> and <ClusterRegion> with your own values.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"resources": [
{
"type": "Microsoft.Kusto/Clusters",
"apiVersion": "2021-02-01",
"name": "<ClusterName>",
"location": "<ClusterRegion>",
"properties": {
"restrictOutboundNetworkAccess": "Enabled"
}
}
]
}
Example: Disable restricted outbound access
To disable restricted outbound access, set the restrictOutboundNetworkAccess property to Disabled:
In the following example, replace <ClusterName> and <ClusterRegion> with your own values.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"resources": [
{
"type": "Microsoft.Kusto/Clusters",
"apiVersion": "2021-02-01",
"name": "<ClusterName>",
"location": "<ClusterRegion>",
"properties": {
"restrictOutboundNetworkAccess": "Disabled"
}
}
]
}
Example: Enable restricted outbound access using the Azure portal
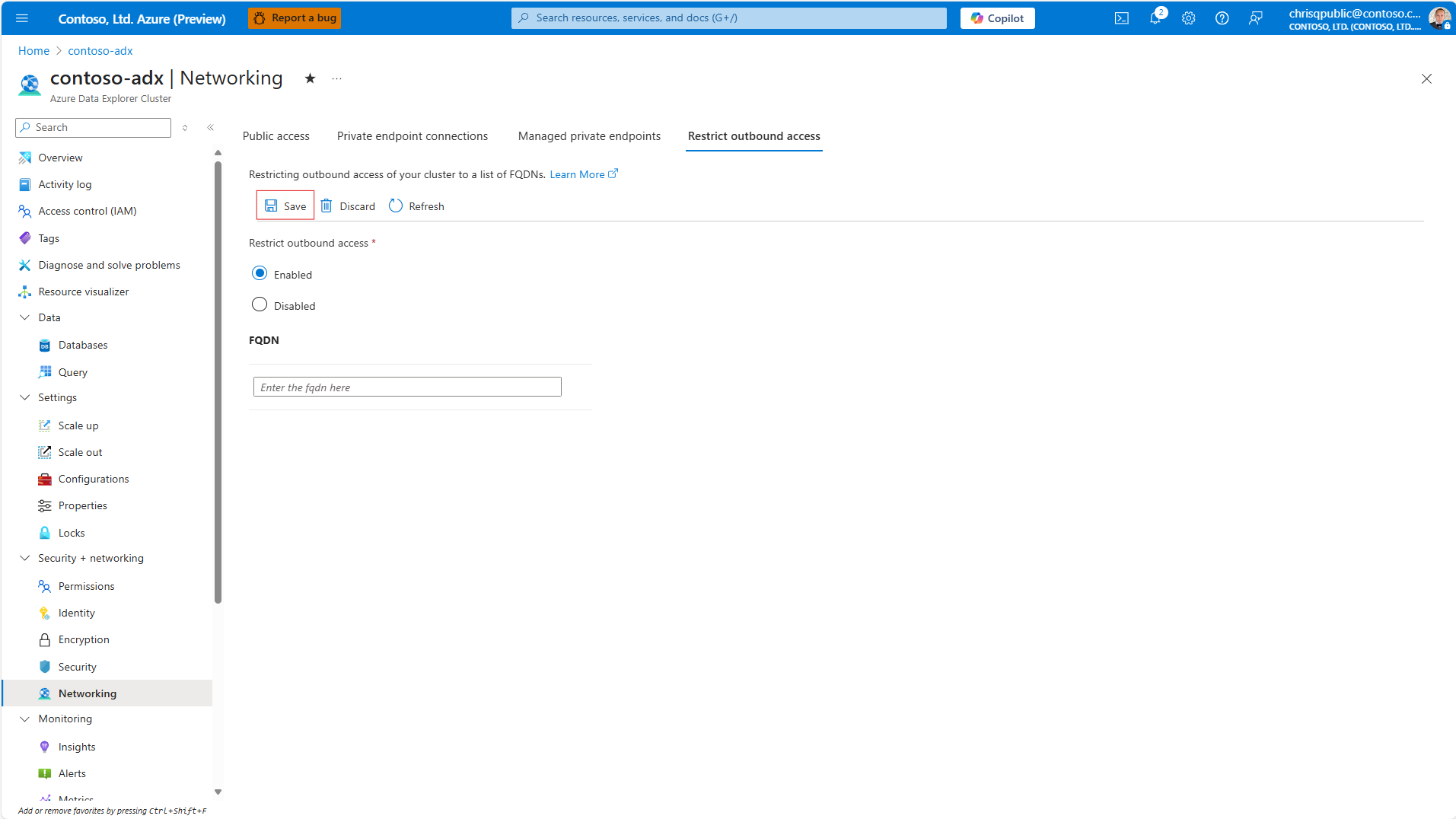
Go to your cluster in the Azure portal.
Navigate to Security + networking > Networking > Restrict outbound access.
Select Enabled to enable the restricted outbound access.
Select Save to submit the configuration.
Configure FQDN-based allowlists
When restricted outbound access is enabled, you can allow specific FQDNs by adding them to the allowedFqdnList property in your cluster's ARM template.
Example: Allow specific FQDNs using ARM templates
The following ARM template allows outbound access to specific FQDNs while keeping restricted outbound access enabled:
In the following example, replace <ClusterName> and <ClusterRegion> with your own values.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"resources": [
{
"type": "Microsoft.Kusto/Clusters",
"apiVersion": "2021-02-01",
"name": "<ClusterName>",
"location": "<ClusterRegion>",
"properties": {
"restrictOutboundNetworkAccess": "Enabled",
"allowedFqdnList": [
"example.blob.core.chinacloudapi.cn"
]
}
}
]
}
Example: Allow specific FQDNs using the Azure portal
Go to your cluster in the Azure portal.
Navigate to Security + networking > Networking > Restrict outbound access.
Select Enabled to enable the restricted outbound access and configure the FQDNs.
Select Save to submit the configuration.
Configure callout policies (preview)
Alternatively, you can configure callout policies directly in the ARM template or using the Azure CLI. Callout policies allow you to define specific rules for outbound access to SQL, storage, or other endpoints.
Note
You can't configure callout policies with restricted outbound access directly through the Azure portal.
Example: Configure callout policies using ARM template
The following ARM template configures callout policies along with restricted outbound access:
In the following example, replace <ClusterName> and <ClusterRegion> with your own values.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"resources": [
{
"type": "Microsoft.Kusto/Clusters",
"apiVersion": "2021-02-01",
"name": "<ClusterName>",
"location": "<ClusterRegion>",
"properties": {
"restrictOutboundNetworkAccess": "Enabled",
"calloutPolicies": [
{
"calloutType": "sql",
"calloutUriRegex": "[a-z0-9][a-z0-9\\-]{0,61}[a-z0-9]?\\.database\\.chinacloudapi\\.cn/?$",
"outboundAccess": "Allow"
},
{
"calloutType": "external_data",
"calloutUriRegex": ".*",
"outboundAccess": "Deny"
}
]
}
}
]
}
Example: Configure callout policies using Azure CLI
You can also configure callout policies using the Azure CLI. The following command sets the callout policies for a cluster:
In the following example, replace <ResourceGroupName> and <ClusterName> with your own values.
az resource update --resource-group <ResourceGroupName> \
--name <ClusterName> \
--resource-type Microsoft.Kusto/clusters \
--set properties.calloutPolicies='[
{
"calloutType": "sql",
"calloutUriRegex": "sqlname\\.database\\.chinacloudapi\\.cn/?$",
"outboundAccess": "Allow"
}
]'
Verify restricted outbound access and policies
After enabling restricted outbound access or configuring callout policies, you can verify the configuration by running the following management command in the Azure Data Explorer web UI:
.show cluster policy callout
This command displays the current callout policies and allowed FQDNs.
Note
There are default policies set for a cluster to communicate with its internal storage layer, which exposes no risk of data exfiltration.
Limitations
While restricted outbound access offers robust security, it's important to be aware of some limitations:
- FQDN-based allowlists don't support webapi callouts.
- You can configure either FQDN-based allowlists or callout policies, but not both. Attempting to configure both results in a configuration error.
- Clusters have a set of default policies for internal communication with its storage layer. These policies can't be changed and don't pose a risk for data exfiltration.
- You can't configure callout policies with restricted outbound access directly through the Azure portal.