Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article describes how to enable diagnostic log delivery for your Azure Databricks workspaces.
Note
Diagnostic logs require the Premium plan.
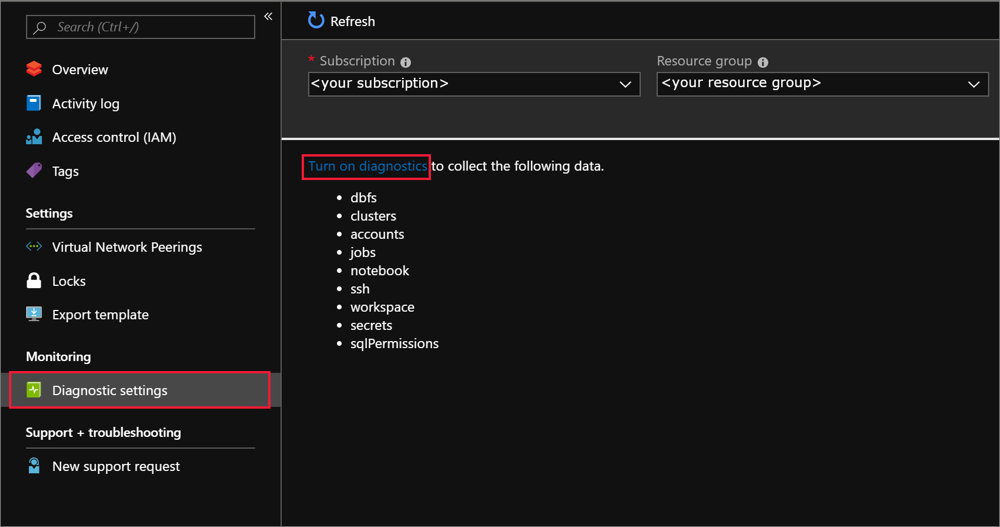
Log in to the Azure portal as an Owner, Contributor, or as a user with a custom role with the
Microsoft.Databricks/workspaces/assignWorkspaceAdmin/actionpermission for the Azure Databricks workspace. Then click your Azure Databricks service resource.In the Monitoring section of the sidebar, click the Diagnostic settings tab.
Click Add diagnostic setting.
On the Diagnostic settings page, provide the following configuration:
Name
Enter a name for the logs to create.
Archive to a storage account
To use this option, you need an existing storage account to connect to. To create a new storage account in the portal, see Create a storage account and follow the instructions to create an Azure Resource Manager, general-purpose account. Then return to this page in the portal to select your storage account. It might take a few minutes for newly created storage accounts to appear in the drop-down menu. For information about additional costs incurred by writing to a storage account, see Azure Storage pricing.
Stream to an event hub
To use this option, you need an existing Azure Event Hubs namespace and event hub to connect to. To create an Event Hubs namespace, see Create an Event Hubs namespace and an event hub by using the Azure portal. Then return to this page in the portal to select the Event Hubs namespace and policy name. For information about additional costs incurred by writing to an event hub, see Azure Event Hubs pricing.
Send to Log Analytics workspace
To use this option, either use an existing Log Analytics workspace or create a new one by following the steps to Create a new workspace in the portal. For information about additional costs incurred by sending logs to Log Analytics, see Azure Monitor pricing.
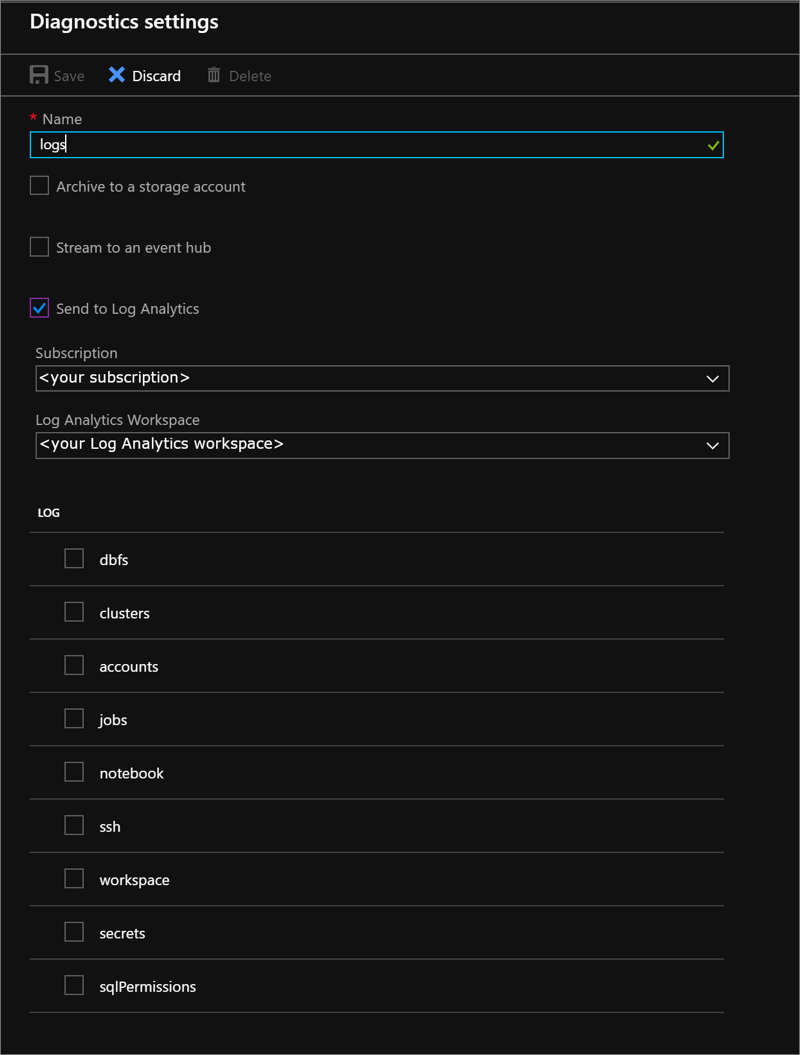
Choose the services you want diagnostic logs for.
Select Save.
If you receive an error that says "Failed to update diagnostics for
<workspace name>. The subscription<subscription id>is not registered to use microsoft.insights," follow the Troubleshoot Azure Diagnostics instructions to register the account and then retry this procedure.If you want to change how your diagnostic logs are saved at any point in the future, return to this page to modify the diagnostic log settings for your account.
Note
If you want to set storage retention policies, configure an Azure lifecycle management policy.
Enable logging using PowerShell
Start an Azure PowerShell session and sign in to your Azure account with the following command:
Connect-AzAccount -Environment AzureChinaCloudTo sign in to your Azure account with a user account or service principal, see Authenticate with Azure PowerShell.
If you do not have Azure Powershell installed already, use the following commands to install Azure PowerShell.
Install-Module -Name Az -AllowClobberIn the pop-up browser window, enter your Azure account user name and password. Azure PowerShell gets all of the subscriptions that are associated with this account, and by default, uses the first one.
If you have more than one subscription, you might have to specify the specific subscription that was used to create your Azure Key Vault. To see the subscriptions for your account, type the following command:
Get-AzSubscriptionTo specify the subscription that's associated with the Azure Databricks account that you're logging, type the following command:
Set-AzContext -SubscriptionId <subscription ID>Set your Log Analytics resource name to a variable named
logAnalytics, whereResourceNameis the name of the Log Analytics workspace.$logAnalytics = Get-AzResource -ResourceGroupName <resource group name> -ResourceName <resource name> -ResourceType "Microsoft.OperationalInsights/workspaces"Set the Azure Databricks service resource name to a variable named
databricks, whereResourceNameis the name of the Azure Databricks service.$databricks = Get-AzResource -ResourceGroupName <your resource group name> -ResourceName <your Azure Databricks service name> -ResourceType "Microsoft.Databricks/workspaces"To enable logging for Azure Databricks, use the New-AzDiagnosticSetting cmdlet with variables for the new storage account, Azure Databricks service, and the category to enable for logging. Run the following command and set the
-Enabledflag to$true:New-AzDiagnosticSetting -ResourceId $databricks.ResourceId -WorkspaceId $logAnalytics.ResourceId -Enabled $true -name "<diagnostic setting name>" -Category <comma separated list>
Enable logging by using Azure CLI
Open PowerShell.
Use the following command to connect to your Azure account:
Note
Before you can use Azure CLI in Microsoft Azure operated by 21Vianet, please run
az cloud set -n AzureChinaCloudfirst to change the cloud environment. If you want to switch back to Azure Public Cloud, runaz cloud set -n AzureCloudagain.az cloud set -n AzureChinaCloud az login # az cloud set -n AzureCloud //means return to Public Azure.To connect with a user account or service principal, see Sign in with the Azure CLI.
Run the following diagnostic setting command:
az monitor diagnostic-settings create --name <diagnostic name> --resource-group <log analytics workspace resource group> --workspace <log analytics name or object ID> --resource <target resource object ID> --logs '[ { \"category\": <category name>, \"enabled\": true } ]'
REST API
Use the LogSettings API.
Request
PUT https://management.chinacloudapi.cn/{resourceUri}/providers/microsoft.insights/diagnosticSettings/{name}?api-version=2017-05-01-preview
Request body
{
"properties": {
"workspaceId": "<log analytics resourceId>",
"logs": [
{
"category": "<category name>",
"enabled": true,
"retentionPolicy": {
"enabled": false,
"days": 0
}
}
]
}
}
Diagnostic log latency
After logging is enabled for your account, Azure Databricks automatically sends diagnostic logs to your delivery location. Logs are typically available within 15 minutes of activation. Azure Databricks auditable events typically appear in diagnostic logs within 15 minutes in Azure Commercial regions.
SSH login logs are delivered with high latency.
Note
While most logs are expected to be delivered within 15 minutes, Azure Databricks does not guarantee a time frame for log delivery.
Diagnostic log schema considerations
- If actions take a long time, the request and response are logged separately but the request and response pair have the same
requestId. - Automated actions, such as resizing a cluster due to autoscaling or launching a job due to scheduling, are performed by the user
System-User. - The
requestParamsfield is subject to truncation. If the size of its JSON representation exceeds 100 KB, values are truncated and the string... truncatedis appended to truncated entries. In rare cases where a truncated map is still larger than 100 KB, a singleTRUNCATEDkey with an empty value is present instead.
Diagnostic log example schema
Audit logs output events in JSON. The serviceName and actionName properties identify the event. The naming convention follows the Databricks REST API.
The following JSON sample is an example of an event logged when a user created a job:
{
"TenantId": "<your-tenant-id>",
"SourceSystem": "|Databricks|",
"TimeGenerated": "2019-05-01T00:18:58Z",
"ResourceId": "/SUBSCRIPTIONS/SUBSCRIPTION_ID/RESOURCEGROUPS/RESOURCE_GROUP/PROVIDERS/MICROSOFT.DATABRICKS/WORKSPACES/PAID-VNET-ADB-PORTAL",
"OperationName": "Microsoft.Databricks/jobs/create",
"OperationVersion": "1.0.0",
"Category": "jobs",
"Identity": {
"email": "mail@example.com",
"subjectName": null
},
"SourceIPAddress": "131.0.0.0",
"LogId": "201b6d83-396a-4f3c-9dee-65c971ddeb2b",
"ServiceName": "jobs",
"UserAgent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.108 Safari/537.36",
"SessionId": "webapp-cons-webapp-01exaj6u94682b1an89u7g166c",
"ActionName": "create",
"RequestId": "ServiceMain-206b2474f0620002",
"Response": {
"statusCode": 200,
"result": "{\"job_id\":1}"
},
"RequestParams": {
"name": "Untitled",
"new_cluster": "{\"node_type_id\":\"Standard_DS3_v2\",\"spark_version\":\"5.2.x-scala2.11\",\"num_workers\":8,\"spark_conf\":{\"spark.databricks.delta.preview.enabled\":\"true\"},\"cluster_creator\":\"JOB_LAUNCHER\",\"spark_env_vars\":{\"PYSPARK_PYTHON\":\"/databricks/python3/bin/python3\"},\"enable_elastic_disk\":true}"
},
"Type": "DatabricksJobs"
}