Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Attention: All Microsoft Defender for Cloud features will be officially retired in Azure in China region on August 18, 2026 per the announcement posted by 21Vianet.
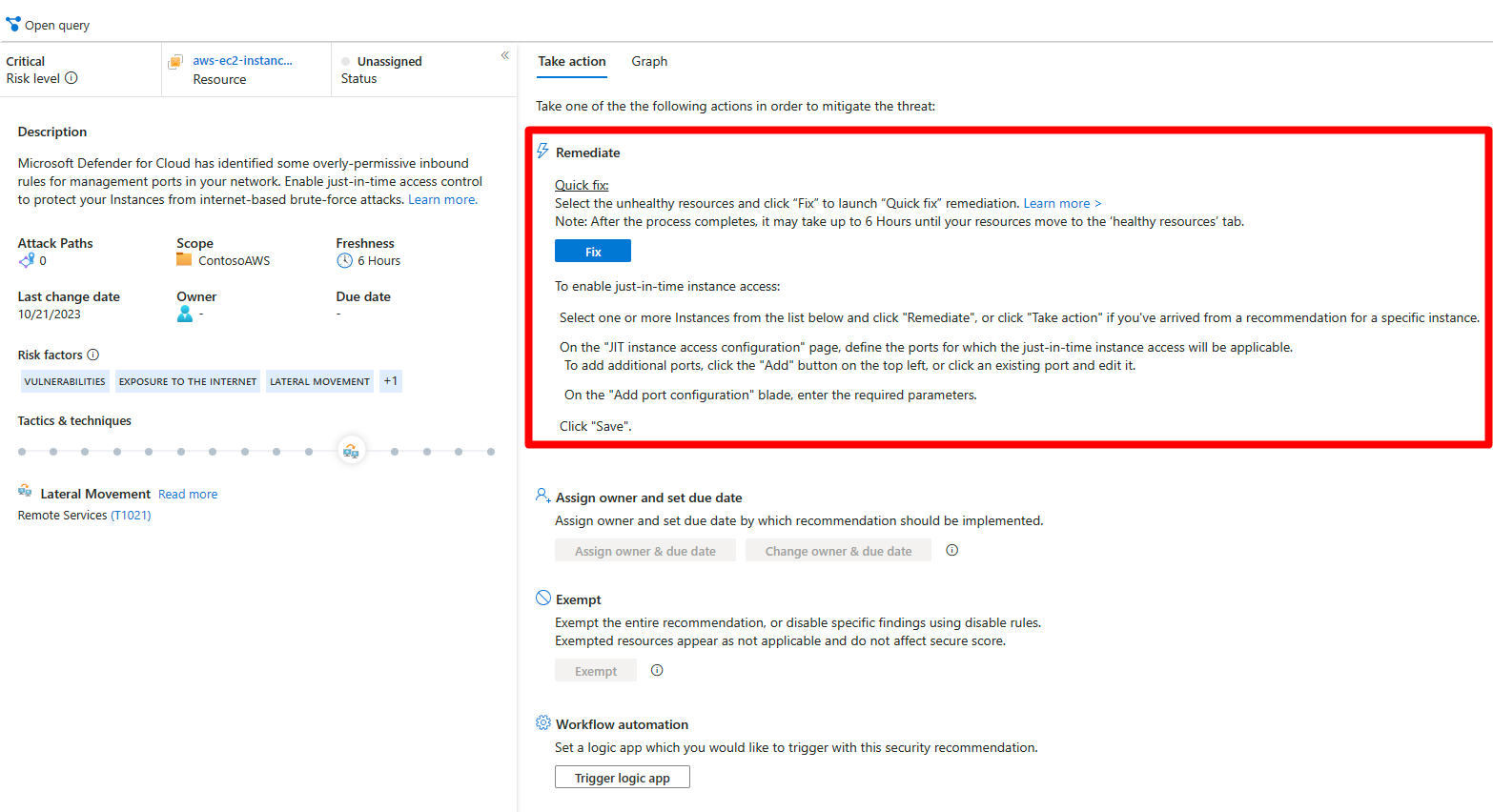
Recommendations give you suggestions on how to better secure your resources. You implement a recommendation by following the remediation steps provided in the recommendation.
Remediation steps
After reviewing all the recommendations, decide which one to remediate first. We recommend that you prioritize the security controls with the highest potential to increase your secure score.
From the list, select a recommendation.
Follow the instructions in the Remediation steps section. Each recommendation has its own set of instructions. The following screenshot shows remediation steps for configuring applications to only allow traffic over HTTPS.
Once completed, a notification appears informing you whether the issue is resolved.
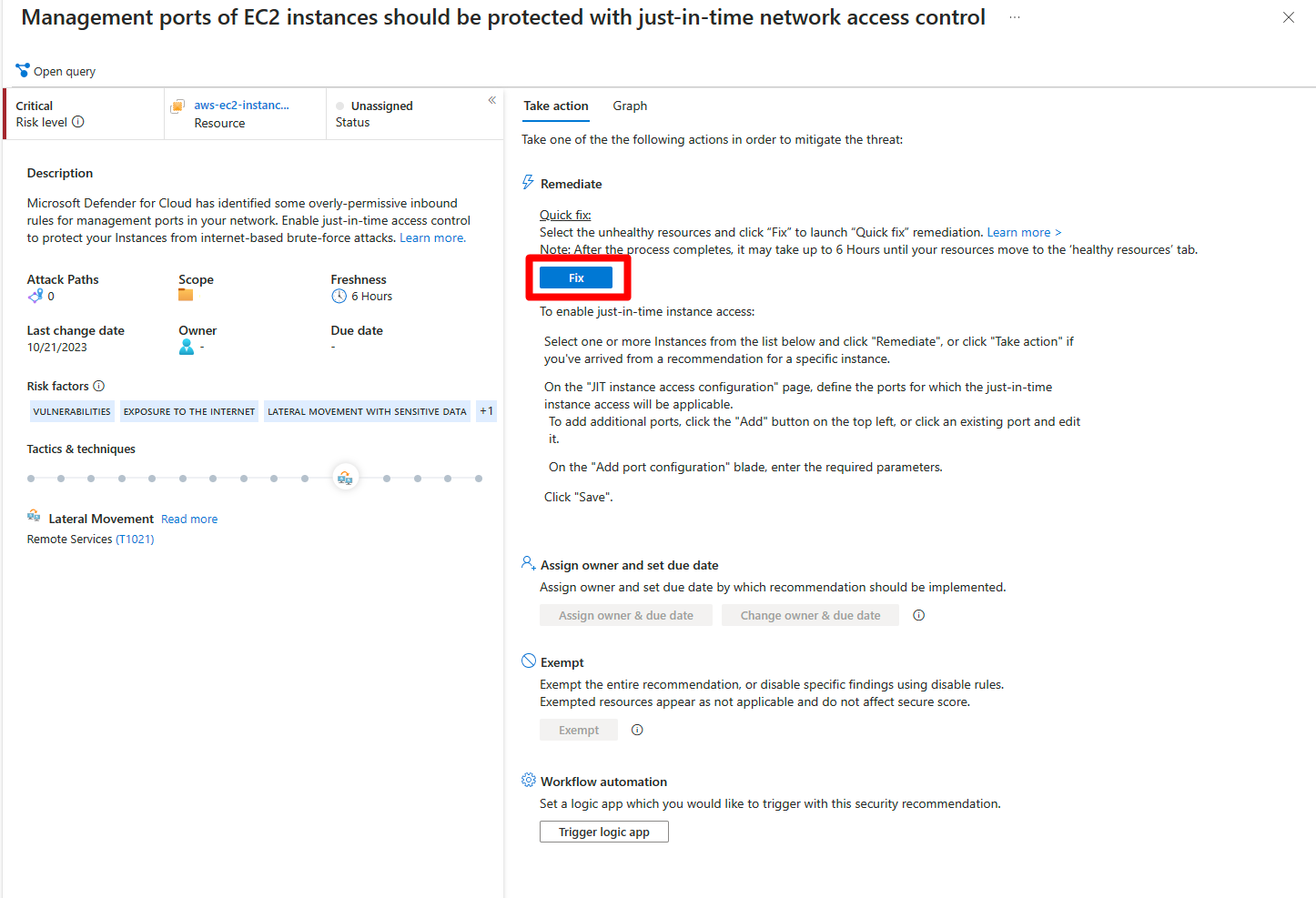
Fix button
To simplify remediation and improve your environment's security (and increase your secure score), many recommendations include a Fix option.
Fix helps you quickly remediate a recommendation on multiple resources.
To implement a Fix:
From the list of recommendations that have the Fix action icon
 , select a recommendation.
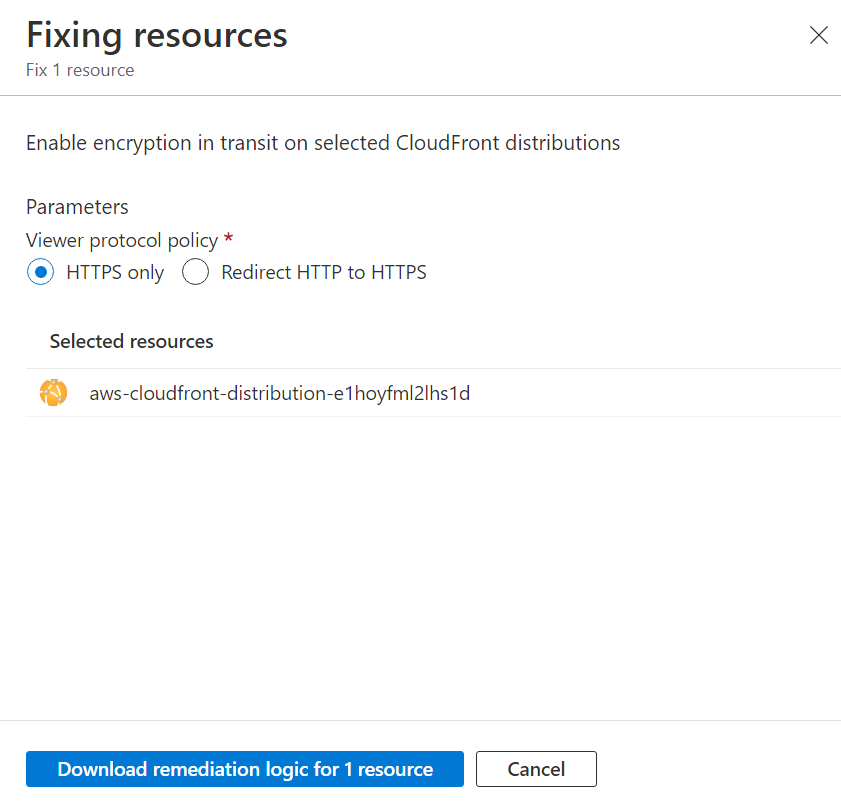
, select a recommendation.From the Unhealthy resources tab, select the resources that you want to implement the recommendation on, and select Fix.
Note
Some of the listed resources might be disabled, because you don't have the appropriate permissions to modify them.
In the confirmation box, read the remediation details and implications.
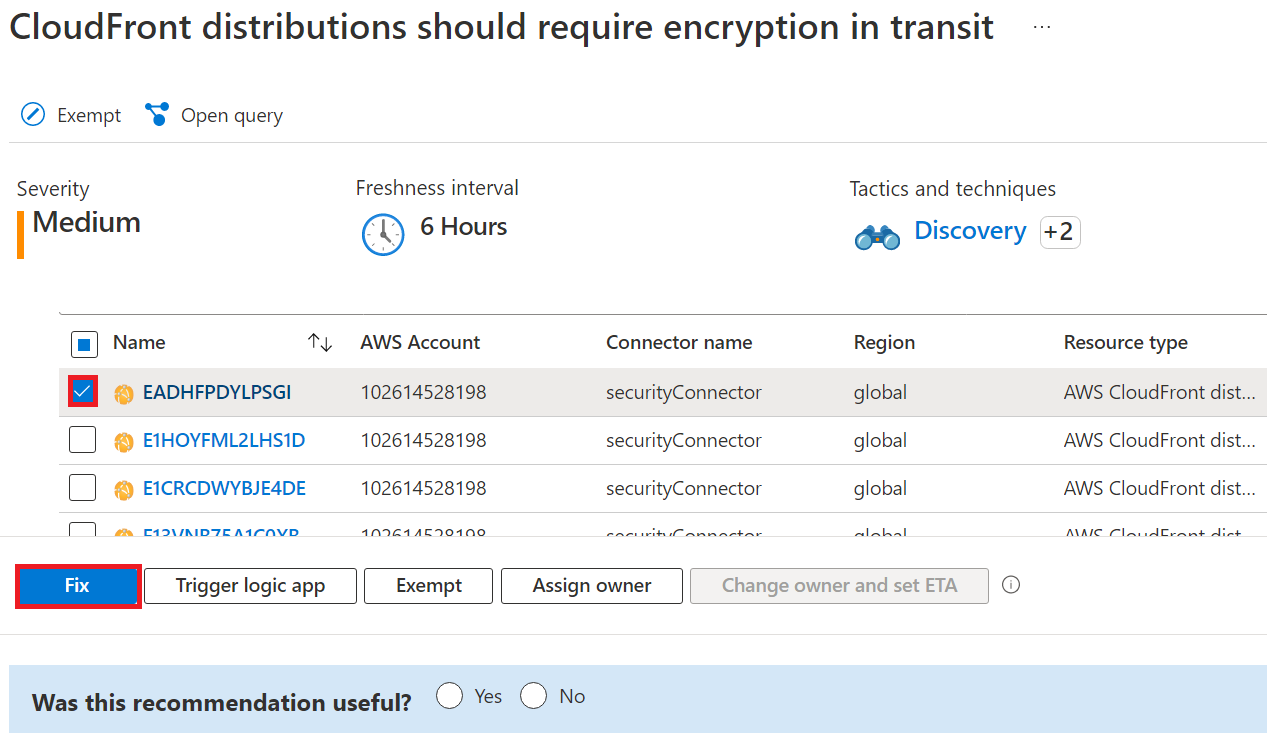
Insert the relevant parameters if necessary, and approve the remediation.
Note
It can take several minutes after remediation completes to see the resources in the Healthy resources tab. To view the remediation actions, check the activity log.
Once completed, a notification appears informing you if the remediation succeeded.
Fix actions logged to the activity log
The remediation operation uses a template deployment or REST API PATCH request to apply the configuration on the resource. These operations are logged in Azure activity log.
Next steps
In this document, you were shown how to remediate recommendations in Defender for Cloud. To learn how recommendations are defined and selected for your environment, see the following page: