Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Attention: All Microsoft Defender for Cloud features will be officially retired in Azure in China region on August 18, 2026 per the announcement posted by 21Vianet.
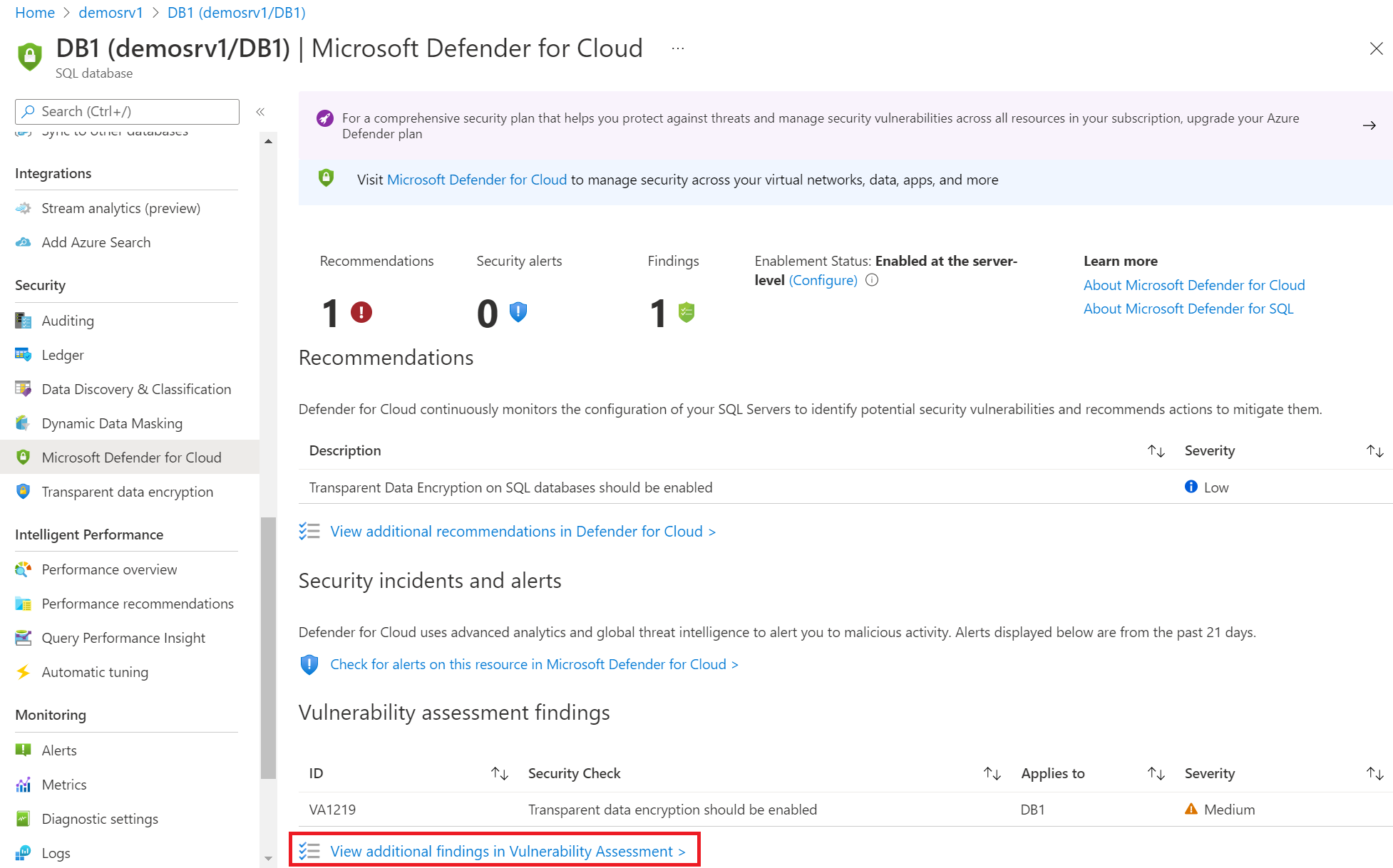
Microsoft Defender for Cloud provides SQL vulnerability assessment for your Azure SQL databases. SQL vulnerability assessment scans your databases for software vulnerabilities and provides a list of findings. Use the findings to fix software vulnerabilities and disable findings.
SQL vulnerability assessment is available in two configurations: express (managed storage in the logical server region) and classic (user-owned storage account in a chosen region).
Prerequisites
Make sure that you know whether you're using the express or classic configurations before you continue.
To see which configuration you're using:
In the Azure portal, open the specific resource in Azure SQL Database, SQL Managed Instance Database, or Azure Synapse.
Under the Security heading, select Defender for Cloud.
In the Enablement Status, select Configure to open the Microsoft Defender for SQL settings pane for either the entire server or managed instance.
If the vulnerability settings show the option to configure a storage account, you're using the classic configuration. If not, you're using the express configuration.
Understanding express and classic configurations
Both configurations provide the same vulnerability scanning capabilities but differ in how and where scan results are stored. This affects permissions, data residency, and how quickly baseline changes are reflected.
Scope: Stores scan results in the same Azure region as the logical SQL server. Microsoft Defender for Cloud fully manages storage (no user-owned storage account required).
Express configuration: permissions and data residency
| Task | Required roles |
|---|---|
| View SQL vulnerability assessment results in Microsoft Defender for Cloud recommendations | Security Admin OR Security Reader |
| Change SQL vulnerability assessment settings | SQL Security Manager |
| Access scan results from automated email links or view resource-level scan results | SQL Security Manager |
Data residency: SQL Vulnerability Assessment queries the SQL server by using publicly available queries under Defender for Cloud recommendations and stores the query results in the same Azure region as the logical server. For example, if you enable vulnerability assessment on a logical server in China North, the scan results are stored in China North. Data is collected only when you enable SQL Vulnerability Assessment on the server.
Configuration comparison summary
The table compares the key differences between the configurations:
| Feature | Express | Classic |
|---|---|---|
| Storage location | Logical server region | User-selected storage account region |
| Storage ownership | Azure-managed | Customer-managed |
| Additional roles beyond SQL Security Manager | None | Storage Blob Data Reader (view email-linked results); Owner + Storage Blob Data Reader (change settings) |
| Baseline refresh needed | No (immediate) | Yes (run new scan) |
| Data residency control | Fixed to server region | Configurable via storage account location |
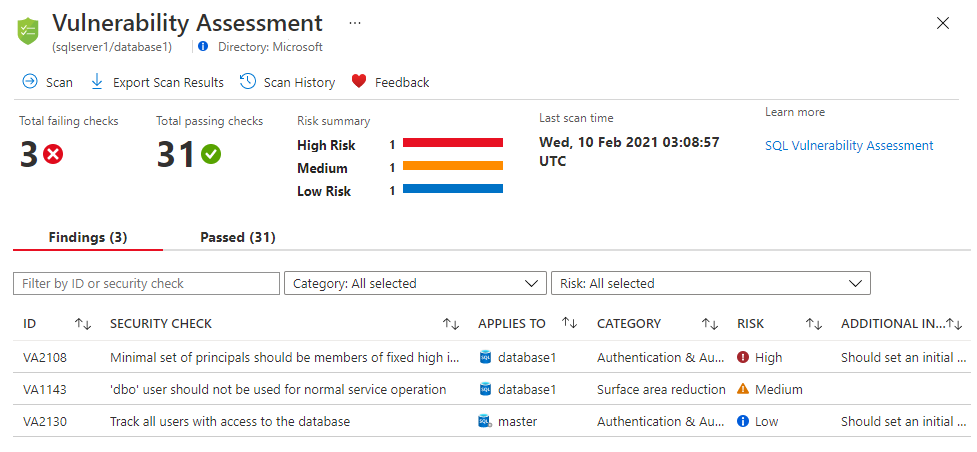
Run scans and manage baselines
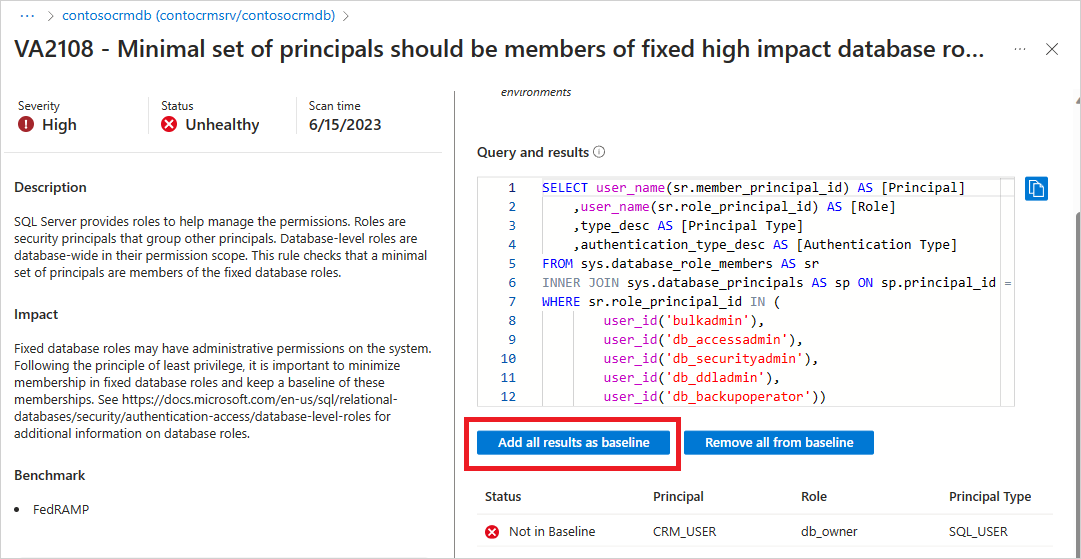
The scan makes no changes to your database, is read-only, and appears in the Vulnerability Assessment tab.
Both configurations use the same scan workflow. The key difference is when they apply the baselines. Express configuration applies it immediately, and classic configuration applies it after you run a new scan.
Perform an on-demand scan
From the resource's Defender for Cloud page, select View additional findings in Vulnerability Assessment to access previous scan results.
Select Scan from the toolbar to run an on-demand SQL vulnerability assessment.
(Optional) Mark acceptable findings as baseline.
View baseline-approved findings in subsequent results (timing differs by configuration).
Manage baselines
Once you run a scan, mark acceptable findings as baseline to customize future results. Configurations with baseline approval pass in later scans.
Baseline outcome quick reference
| Action | Express result timing | Classic result timing |
|---|---|---|
| Approve finding as baseline | Immediately marked Passed | Marked Passed after next scan |
Review and remediate vulnerabilities
After a scan completes, the vulnerability assessment report shows a full view of your database security. Both the express and classic configurations use the same remediation workflow and baseline management.
Understand scan results
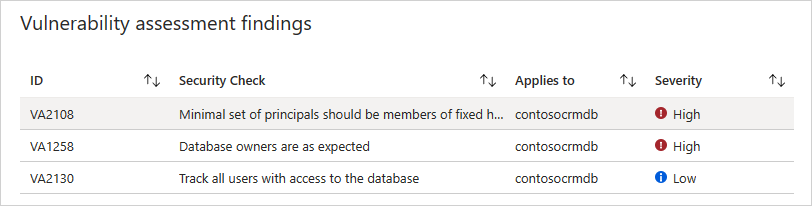
The vulnerability assessment report includes:
- An overview of your security state
- The number of issues found
- A severity summary of risks
- A list of findings for investigation
Remediation and baseline procedure
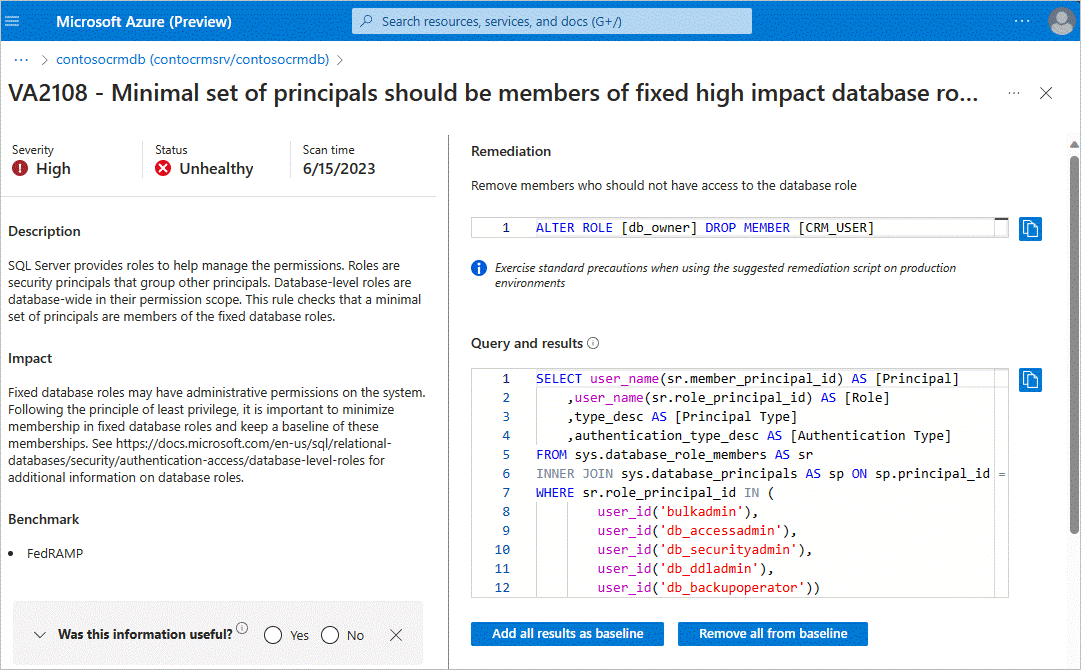
Review scan results to identify security issues relevant to your environment.
Select each failed result to view detailed information, including impact and failure reasons.
Mark acceptable findings as baseline to prevent them from appearing as failures in future scans.
View Passed status for baseline-approved findings:
Outcome: SQL vulnerability assessment scan cycles help maintain a high security level and ensure compliance with organizational security policies.
Troubleshoot common issues
Use this table to resolve common issues when working with SQL vulnerability assessment:
| Issue | Likely cause | Resolution |
|---|---|---|
| Scan results not visible | Missing viewer role | Ensure Security Admin or Security Reader role is assigned. |
| Can't change settings | Insufficient configuration role | Assign SQL Security Manager (and for classic: Owner + Storage Blob Data Reader on storage account). |
| Baseline not reflected (classic) | New scan not run yet | Run another on-demand scan to apply baseline changes. |
| Baseline not reflected (express) | Expectation mismatch | Baseline applies immediately; refresh the Vulnerability Assessment tab. |
| Access error opening email link (classic) | Storage role missing | Add Storage Blob Data Reader for the storage account containing scan results. |
Next steps
- Learn more about Microsoft Defender for Azure SQL.
- Learn more about data discovery and classification.
- Learn more about storing vulnerability assessment scan results in a storage account accessible behind firewalls and VNets.