Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
You can use the Microsoft Entra Privileged Identity Management (PIM) audit history to see role assignments changes and activations done through PIM. Data is available for the past 30 days. If you want to retain audit data for longer than the default retention period, you can use Azure Monitor to route it to an Azure storage account. For more information, see Archive Microsoft Entra logs to an Azure storage account. To see full audit history of Microsoft Entra ID activity including administrator, end user, and synchronization activity, you can use the Microsoft Entra security and activity reports.
Follow these steps to view the audit history for Microsoft Entra roles.
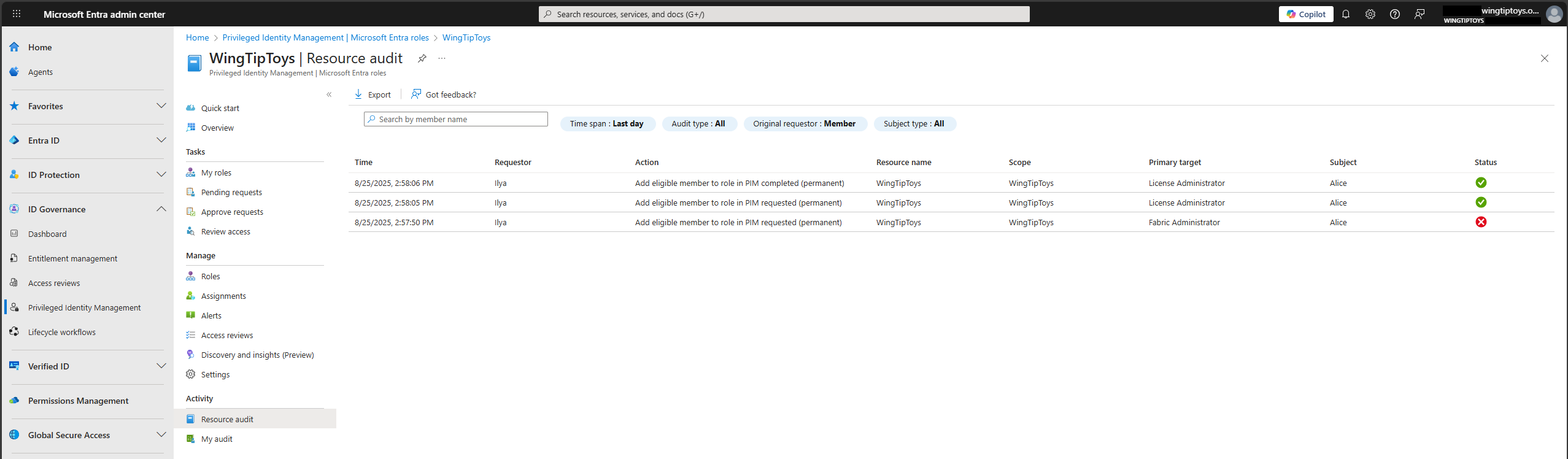
View resource audit history
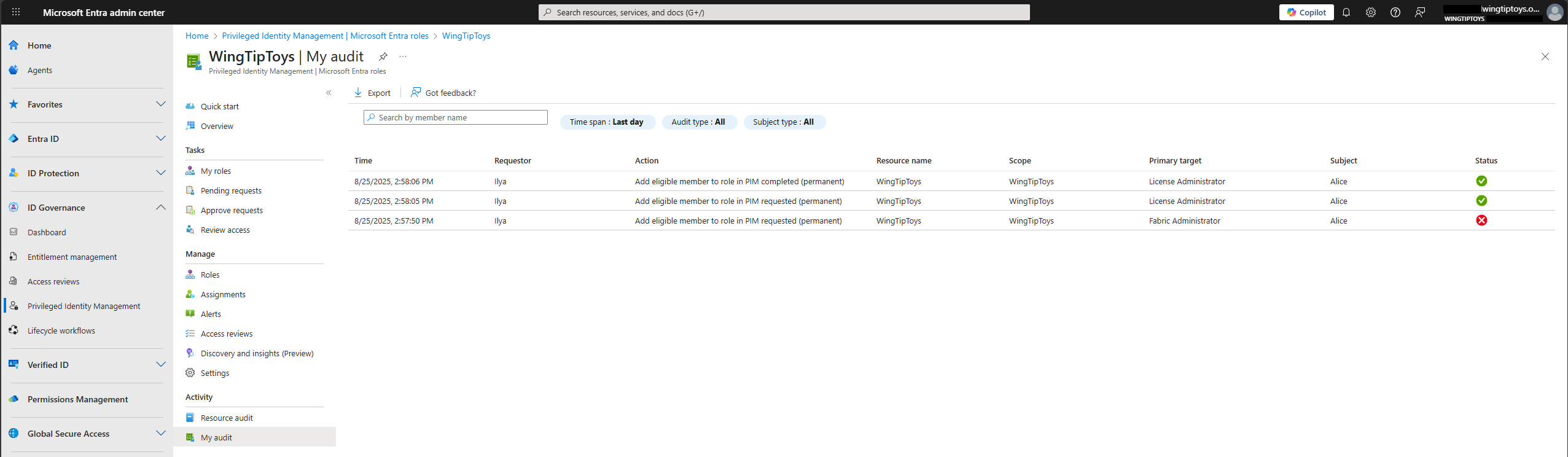
Use Resource audit blade to view all activity associated with your Microsoft Entra role assignment and PIM Policy management in PIM.
Sign in to the Microsoft Entra admin center as a Global Administrator, Global Reader, Privileged Role Administrator, Security Administrator, or Security Reader.
Browse to ID Governance > Privileged Identity Management > Microsoft Entra roles.
Select Resource audit.
Filter the history using a predefined date or custom range.
View my audit
Use My audit blade to view your role activity for Microsoft Entra role assignment and PIM Policy management.
Sign in to the Microsoft Entra admin center.
Browse to ID Governance > Privileged Identity Management > Microsoft Entra roles.
Select My audit.
Filter the history using a predefined date or custom range.