Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Entra Kerberos is a cloud-native authentication protocol that bridges hybrid identity scenarios by enabling secure access to both cloud and on-premises resources. It extends traditional Kerberos capabilities into the Microsoft Entra ecosystem, so that organizations can modernize their identity infrastructure without sacrificing compatibility with legacy systems. It also enables seamless single sign-on (SSO) to on-premises resources for users authenticated with modern credentials like Windows Hello for Business or FIDO2 security keys.
Microsoft Entra Kerberos was introduced in 2021 to help bridge the gap between legacy on-premises authentication protocols and modern cloud identity. In practice, Microsoft Entra Kerberos turns Microsoft Entra ID into a cloud-based Key Distribution Center (KDC) for Kerberos authentication. This capability allows Microsoft Entra ID to issue Kerberos tickets for users, extending traditional Kerberos authentication beyond on-premises Active Directory.
In a hybrid scenario, where accounts exist in on-premises Active Directory Domain Services (AD DS) and those users are synchronized to Microsoft Entra ID, Microsoft Entra Kerberos plays a crucial role. It enables these hybrid users to authenticate to cloud and on-premises resources by using Kerberos without needing a direct line of sight to domain controllers. For example, if a Microsoft Entra ID-joined Windows client accesses a file share or application over the internet, Microsoft Entra ID can issue the necessary Kerberos tickets on behalf of the on-premises Active Directory environment.
For more information about Kerberos in Windows, see Kerberos authentication overview in Windows Server.
Microsoft Entra Kerberos works with hybrid identities as well as cloud-only identities when the service supports.
Hybrid identity
A hybrid identity refers to a user identity that exists both in on-premises AD DS and in Microsoft Entra ID. These identities are synchronized through tools like Microsoft Entra Connect, so users can access both cloud-based and on-premises resources by using a single set of credentials.
This setup enables seamless authentication and SSO experiences across environments. It's ideal for organizations that want to transition to the cloud while maintaining legacy infrastructure.
Cloud only identity (Preview)
A cloud-only identity refers to a user account that exists only in Microsoft Entra ID (formerly Azure AD) and does not have a corresponding account in an on-premises Active Directory.
Key features and benefits
Seamless hybrid authentication: Microsoft Entra Kerberos allows users whose accounts reside in on-premises AD DS and are synchronized to Microsoft Entra ID to authenticate across cloud and on-premises resources. It reduces (and in some cases, eliminates) the need for direct connectivity to domain controllers.
For example, when a Microsoft Entra ID-joined Windows client accesses a file share or application over the internet, Microsoft Entra ID can issue the necessary Kerberos tickets as a KDC associated with the resource.
Cloud-only identity support (Preview): Cloud-only identities can now use Kerberos authentication for workloads like Azure Files without requiring on-premises AD DS. This is enabled by Entra Kerberos, which acts as a cloud-based KDC.
Enhanced security with modern credentials support: Users can sign in by using passwordless methods such as Windows Hello for Business or FIDO2 security keys, yet still access on-premises resources that have Kerberos protections. This ability enables multifactor authentication (MFA) and passwordless authentication to reduce the risks associated with password theft and phishing attacks.
Secure ticket exchange: Microsoft Entra Kerberos uses a Ticket Granting Ticket (TGT) exchange model for enhanced security.
Scalable group memberships: Microsoft Entra Kerberos addresses traditional Kerberos limitations with large or dynamic group memberships to improve reliability and user experience. In scenarios that involve large groups of users, performance is optimized through automatic load distribution across all domain controllers (DCs) within a site. For deployments in Azure Virtual Desktop environments, we recommend ensuring that sufficient DCs are available and geographically close to the environment, to maintain responsiveness.
How Microsoft Entra Kerberos works
In hybrid scenarios, Microsoft Entra Kerberos allows your Microsoft Entra ID tenant to operate as a dedicated Kerberos realm alongside your existing on-premises Active Directory realm. When a user signs in to a Windows device that's either Microsoft Entra ID joined or hybrid joined, the device authenticates with Microsoft Entra ID and receives a Primary Refresh Token (PRT).
In addition to the PRT, Microsoft Entra ID issues a Cloud TGT for the realm KERBEROS.MICROSOFTONLINE.COM. This is a partial TGT to access on-premises resources. In this model, Microsoft Entra ID acts as the KDC to facilitate seamless authentication.
Cloud only identities scenarios (Preview)
Cloud-only identities support for Entra Kerberos requires Microsoft Entra ID tenant with Entra Kerberos enabled and Windows 10/11 device that is Microsoft Entra-joined.
Support for Microsoft Entra ID with Entra Kerberos for cloud-only identities allows Entra-joined session hosts to authenticate and access cloud resources like Azure file shares without relying on traditional Active Directory infrastructure. This capability is essential for organizations adopting a cloud-only strategy, as it removes the need for domain controllers while preserving enterprise-grade security, access control, and encryption.
Currently the supported workloads are Azure Files, Azure Virtual Desktop and Windows authentication access to Azure SQL Managed Instance.
Authentication flow
1. User authentication
The user signs in to a Windows device that's either Microsoft Entra joined or hybrid joined.
The Local Security Authority (LSA) uses the Cloud Authentication Provider (CloudAP) to authenticate via OAuth to Microsoft Entra ID.
2. Token issuance
Upon successful authentication, Microsoft Entra ID issues a PRT that contains user and device information. Alongside the PRT, Microsoft Entra ID issues a Cloud TGT for the realm KERBEROS.MICROSOFTONLINE.COM.
Microsoft Entra ID also issues an OnPremTgt (partial TGT) that contains the user's security identifier (SID) but no group claims. This partial TGT is not sufficient for direct access to on-premises resources.
Cloud TGT issuance
Microsoft Entra ID acts as a KDC for cloud resources by issuing a Cloud TGT to the client when appropriate. The client recognizes the Microsoft Entra ID tenant as a separate Kerberos realm for cloud resources, and the TGT is stored in the client's Kerberos ticket cache. The Cloud TGT is cached locally and can be verified using PowerShell command 'klist cloud_debug'.
The Cloud TGT that Microsoft Entra ID issues:
- Is for the realm
KERBEROS.MICROSOFTONLINE.COM. - Enables access to cloud-based resources such as Azure Files, Azure SQL, and other services that are integrated with Microsoft Entra Kerberos.
- Contains authorization data that's specific to cloud services and is used directly to request Kerberos service tickets for cloud resources.
- Is always issued when a user signs in to a Windows device by using supported credentials (for example, Windows Hello for Business or FIDO2).
- Has no dependency on on-premises domain controllers.
Note
The Cloud TGT isn't a replacement for the on-premises TGT. It's another ticket that allows access to cloud resources. The on-premises TGT is still required for accessing on-premises resources.
OnPremTgt issuance for on-premises access
These prerequisites apply:
- Users must be synchronized from on-premises Active Directory to Microsoft Entra ID via Microsoft Entra Connect.
- A Kerberos server object must exist in on-premises Active Directory and be synchronized to Microsoft Entra ID. This object allows Microsoft Entra ID to issue OnPremTgt that on-premises domain controllers can redeem.
- Devices must be running Windows 10 (2004 or later) or Windows 11.
- Devices should be Microsoft Entra joined or hybrid joined.
- We recommend Windows Hello for Business or FIDO2 authentication methods for optimal integration.
- On-premises domain controllers must be patched to support Kerberos Cloud Trust.
- Ensure line of sight between client devices and domain controllers for ticket exchange.
If the user signs in by using a passwordless method (such as FIDO2 or Windows Hello for Business) on devices with Windows 10 (2004 or later) or Windows 11, Microsoft Entra ID issues an OnPremTgt for the user's on-premises Active Directory domain. This OnPremTgt contains the user's SID but no authorization data.
The OnPremTgt that Microsoft Entra ID issues:
- Enables access to on-premises resources by acting as a bridge between Microsoft Entra ID and Active Directory.
- Contains limited data (for example, the user's SID) and no group claims. It's not sufficient on its own to access on-premises resources.
- Is issued only if the environment is configured to support it. For example, you have a hybrid identity setup and a Microsoft Entra Kerberos server object in Active Directory.
- Must be exchanged with an on-premises Active Directory domain controller for a full TGT that includes the user's SID, full PAC (all group memberships), session key and other access control data. The full TGT is then used to access resources like Server Message Block (SMB) shares or SQL servers.
The dsregcmd /status command will show the result for both TGT. More information at Troubleshoot devices by using the dsregcmd command.
- OnPremTgt: Set the state to YES if a Cloud Kerberos ticket to access on-premises resources is present on the device for the logged-in user.
- CloudTgt: Set the state to YES if a Cloud Kerberos ticket to access cloud resources is present on the device for the logged-in user.
Microsoft Entra Kerberos TGT and Active Directory access control
Possessing a Microsoft Entra Kerberos TGT for a user's on-premises Active Directory domain does not automatically grant access to a full Active Directory TGT.
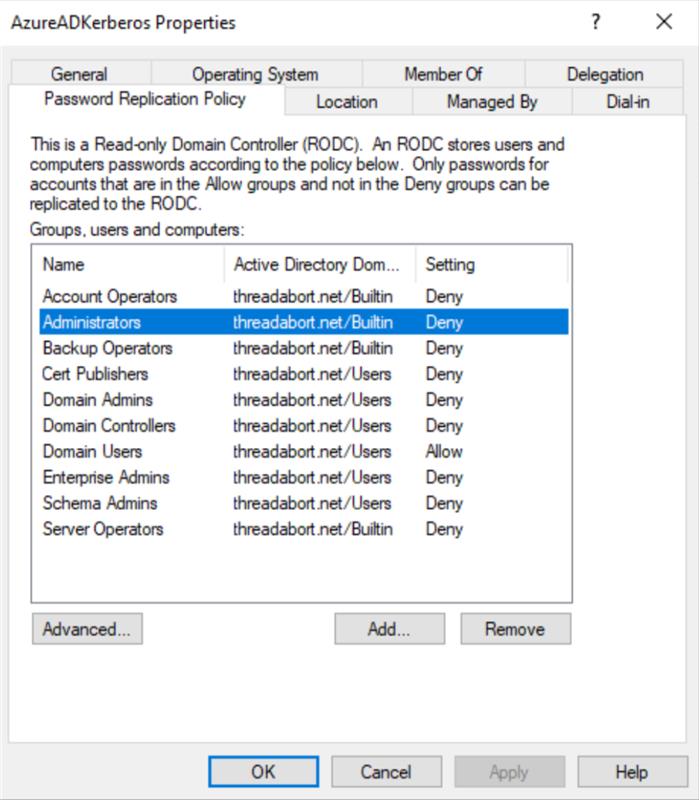
Microsoft Entra Kerberos uses the Read-Only Domain Controller (RODC) object's allowlist and blocklist to control which users can receive partial TGTs from Microsoft Entra ID for on-premises resource access. This mechanism is critical for limiting exposure and enforcing security boundaries. This mechanism is especially critical in hybrid environments where Microsoft Entra ID issues partial TGTs that must be redeemed with on-premises Active Directory domain controllers for a full TGT.
To complete the exchange, the user must be listed in the allowlist on the RODC object and not in the blocklist.
During the exchange process, a partial Microsoft Entra Kerberos TGT is converted into a full Active Directory TGT. Microsoft Entra ID evaluates the lists to determine access eligibility. If the user is in the allowlist, Microsoft Entra ID issues the full TGT. If the user is in the blocklist, Microsoft Entra ID rejects the request and authentication fails.
As a best practice, set the default configuration to Deny. Grant explicit Allow permissions only to groups that are authorized to use Microsoft Entra Kerberos.
Important
Only on-premises Active Directory recognizes the partial TGT. Having access to a partial TGT doesn't provide access to resources outside Active Directory.
Realm mapping
Realm mapping is the mechanism that allows Windows clients to determine which Kerberos realm to contact when a user is accessing a resource. This mechanism is especially important when an organization uses both on-premises Active Directory and Microsoft Entra ID in the same environment.
Windows uses the namespace of the service (for example, *.file.core.chinacloudapi.cn) to decide whether to contact Active Directory or Microsoft Entra ID for a Kerberos ticket. Because both cloud and on-premises services might share the same namespace, Windows can't distinguish them automatically.
To resolve this situation, admins configure mappings of host name to Kerberos realm via:
- Group Policy: Computer Configuration > Administrative Templates > System > Kerberos > Define host name-to-Kerberos realm mappings
- Intune Policy configuration service provider (CSP): Kerberos/HostToRealm
An example mapping for contoso.com is .file.core.chinacloudapi.cn to KERBEROS.MICROSOFTONLINE.COM. This mapping tells Windows to use Microsoft Entra Kerberos for specific Azure Files instances, while defaulting others to on-premises Active Directory.
Azure tenant information in Microsoft Entra Kerberos
Microsoft Entra ID acts as a KDC for cloud resources. It maintains tenant-specific configurations that guide how Kerberos tickets are issued and validated:
- Cloud TGT: Microsoft Entra ID issues this TGT for the realm
KERBEROS.MICROSOFTONLINE.COM. It's stored in the client's Kerberos ticket cache and used for cloud resource access. - KDC Proxy: This protocol routes Kerberos traffic securely over the internet to Microsoft Entra ID. This routing enables clients to obtain tickets without direct connectivity to domain controllers.
- Azure tenant recognition: The Kerberos stack uses realm mapping and the tenant ID to validate the Cloud TGT and issue service tickets.
3. Service ticket request and issuance
For client access to on-premises resources (hybrid scenario):
- Microsoft Entra ID issues a partial TGT.
- The client contacts an on-premises Active Directory domain controller to exchange the partial TGT for a full TGT.
- The full TGT is used to access on-premises resources like SMB shares or SQL servers.
The client uses the Cloud TGT to request service tickets for cloud resources. No interaction with on-premises Active Directory is needed. For client access to cloud resources:
- When the user accesses a service (for example, Azure Files), the client requests a service ticket from Microsoft Entra ID by presenting the TGT.
- The client sends a Ticket Granting Service Request (TGS-REQ) to Microsoft Entra ID.
- Kerberos identifies the service (for example,
cifs/mystuff.file.core.chinacloudapi.cn) and maps the domain toKERBEROS.MICROSOFTONLINE.COM. The KDC Proxy protocol enables Kerberos communication over the internet. - Microsoft Entra ID verifies the Cloud TGT and the user's identity. It also looks up the requested service principal name (SPN) for the Azure Files resource registered in Microsoft Entra ID.
- Microsoft Entra ID generates a service ticket and encrypts it by using the service principal's key. Microsoft Entra ID returns the ticket to the client in a Ticket Granting Service Reply (TGS-REP).
- The Kerberos stack processes the TGS-REP, extracts the ticket, and generates an Application Request (AP-REQ).
- The AP-REQ is provided to SMB, which includes it in the request to Azure Files.
- Azure Files decrypts the ticket and grants access. FSLogix can now read the user profile from Azure Files and load the Azure Virtual Desktop session.
For client access to cloud resources:
- The user with cloud only identity accesses a cloud resource (e.g., Azure Files share).
- The SMB client requests a Kerberos service ticket for the resource SPN (e.g.,
cifs/<storageaccount>.file.core.chinacloudapi.cn). - Entra Kerberos issues the service ticket based on the Cloud TGT. The ticket includes the user's Entra ID identity and group claims.
- Azure Files validates the Kerberos ticket against Entra ID. Authorization is enforced using Azure RBAC roles (e.g., Storage File Data SMB Share Contributor).
- The user gains access to the resource if RBAC permissions are satisfied. No on-premises AD or NTFS ACLs are involved—authorization is fully cloud-based.
Key Differences from Traditional Kerberos:
- No on-premises KDC or Active Directory DS.
- No NTFS ACL enforcement; uses Azure RBAC.
- Kerberos tickets issued by Entra Kerberos in the cloud.
Summary
| Feature | Cloud TGT | On-premises TGT |
|---|---|---|
| Issuer | Microsoft Entra ID | On-premises Active Directory (via exchange) |
| Realm | KERBEROS.MICROSOFTONLINE.COM |
On-premises Active Directory domain |
| Authorization data | Cloud specific | Full Active Directory group memberships |
| Exchange required | No | Yes (partial TGT to full TGT) |
| Use case | Azure Files, Azure SQL | SMB shares, legacy apps |
| Verification tool (macOS) | tgt_cloud |
tgt_ad |
| Verification tool (Windows) | klist cloud_debug |
klist get krbtgt |
Scenarios
Use Microsoft Entra Kerberos for Windows authentication access to Azure SQL Managed Instance
Kerberos authentication for Microsoft Entra ID enables Windows authentication access to Azure SQL Managed Instance. Windows authentication for managed instances empowers customers to move existing services to the cloud while maintaining a seamless user experience. This ability provides the basis for infrastructure modernization.
For detailed information, see What is Windows Authentication for Microsoft Entra principals on Azure SQL Managed Instance?.
Use SSO to sign in to on-premises resources by using FIDO2 keys
Microsoft Entra Kerberos users can sign in to Windows by using modern credentials, such as FIDO2 security keys, and then access traditional Active Directory-based resources.
Enable Kerberos SSO to on-premises Active Directory and Microsoft Entra ID Kerberos resources in Platform SSO
Along with the Platform SSO PRT, Microsoft Entra issues both on-premises and cloud-based Kerberos TGTs. These TGTs are then shared with the native Kerberos stack in macOS via TGT mapping in Platform SSO.
For detailed information, see Enable Kerberos SSO to on-premises Active Directory and Microsoft Entra ID Kerberos resources in Platform SSO.
Store profile containers with FSLogix for Azure Virtual Desktop
To host user profiles for virtual desktops, you can store profiles in an Azure file share accessed via Microsoft Entra Kerberos. Microsoft Entra Kerberos enables Microsoft Entra ID to issue the necessary Kerberos tickets to access the file share through the industry-standard SMB protocol.
For detailed information, see Store FSLogix profile containers on Azure Files using Microsoft Entra ID in a hybrid scenario.
Enable Microsoft Entra Kerberos authentication on Azure Files
Microsoft Entra Kerberos authentication enables hybrid identities as well as cloud only identities to access Azure file shares by using Kerberos authentication. This scenario uses Microsoft Entra ID to issue the necessary Kerberos tickets to access the file share through the SMB protocol.
For detailed information, see Enable Microsoft Entra Kerberos authentication for hybrid identities on Azure Files.
Security considerations
- Microsoft Entra Kerberos doesn't issue partial TGTs to identities that aren't synced to Microsoft Entra ID.
- Microsoft Entra Kerberos uses a secure TGT exchange model via KDC Proxy. This model minimizes exposure to domain controllers and reduces the attack surface.
- Admins can configure group resolution policies to limit which groups are included in Kerberos tickets. These controls are essential for managing ticket size and reducing exposure to unnecessary group data.
- We advise you to maintain clear separation between cloud and on-premises environments. We discourage synchronizing sensitive accounts like
krbtgt_AzureADto on-premises Active Directory due to privilege escalation risks. - Use the RODC object's allowlist and blocklist to control which users can receive partial TGTs from Microsoft Entra ID for on-premises resource access.
Limitations and other considerations
Support for cloud-only user identities (Preview)
Cloud-only user accounts managed solely in Microsoft Entra ID are supported for Kerberos authentication by workloads like Azure Files, Azure Virtual Desktop and Windows authentication access to Azure SQL Managed Instance.
Operating system and device restrictions
Microsoft Entra Kerberos is supported on Microsoft Entra-joined or hybrid-joined Windows 10 (2004 or later) and Windows 11 devices. Some features depend on specific Windows versions and patches.
Network connectivity requirements for ACL configuration
Users can access Azure file shares over the internet without direct connectivity to domain controllers. However, configuring Windows access control lists (ACLs) or file-level permissions for hybrid identities requires unimpeded network access to on-premises domain controllers.
No cross-tenant or guest user support
Business-to-business guest users or users from other Microsoft Entra tenants can't currently authenticate via Microsoft Entra Kerberos.
Password expiration
Service principal passwords for storage accounts expire every six months and need to be rotated to maintain access.
Group membership limits
Kerberos tickets have a size constraint that limits the number of group SIDs that you can include. The default cap is 1,010 groups per ticket. If you exceed that cap, only the first 1,010 are included. The exclusion of the remainder can cause access failures for users in large organizations.
MFA incompatibility for Azure Files authentication
Microsoft Entra Kerberos authentication for Azure file shares doesn't support MFA. Microsoft Entra Conditional Access policies that enforce MFA must exclude the storage account application, or users experience authentication failures.
Exclude Azure Files from Conditional Access policies that require MFA. You can accomplish this task by scoping the policy to exclude the storage account or the specific application that accesses Azure Files.
Attribute synchronization requirements
Proper synchronization of key on-premises Active Directory user attributes is essential for Microsoft Entra Kerberos to work. These attributes include onPremisesDomainName, onPremisesUserPrincipalName, and onPremisesSamAccountName.
Single Active Directory method per Azure Storage account
For Azure Files identity-based authentication, you can enable only one Active Directory method at a time per storage account. These methods include Microsoft Entra Kerberos, on-premises AD DS, and Microsoft Entra Domain Services. Switching between methods requires disabling the current method first.
Kerberos encryption settings
Kerberos ticket encryption with Microsoft Entra Kerberos uses AES-256 exclusively. You can configure SMB channel encryption separately, based on your requirements.
Getting started with Microsoft Entra Kerberos
To authenticate hybrid identities, you must first set up Microsoft Entra Connect to synchronize on-premises AD DS users to Microsoft Entra ID. For details, see the Microsoft Entra Connect installation guide.
Configure Azure Files or other services to use Microsoft Entra Kerberos authentication. For instructions, see Enable Microsoft Entra Kerberos authentication.
Ensure that Windows clients are up to date and configured for Microsoft Entra Kerberos.
Monitor and rotate service principal passwords as required.
Use Microsoft Entra ID reports and monitoring tools to keep track of authentication events.
Group SID limit in Entra Kerberos (Preview)
Kerberos tickets can include a maximum of 1,010 Security Identifiers (SIDs) for groups. This is a Windows specification limit. With Entra Kerberos now supporting cloud-only identities (in addition to hybrid), tickets must include both on-premises group SIDs and cloud group SIDs. Large enterprises often have users in hundreds or thousands of groups, including nested and dynamic memberships. If the combined group SIDs exceed 1,010, the Kerberos ticket cannot be issued and authentication fails. This is especially problematic for SMB access scenarios like Azure Files, where NTFS ACL checks depend on complete group membership in the ticket.
As a short-term solution, apps using Entra Kerberos for cloud-only identities can add a Tag in their application manifest. When the Kerberos service sees this tag, it knows the request involves cloud-only identities. Sign-in and PRT issuance succeed; however, failures may happen at service ticket time when the user accesses a Kerberos protected resource and exceeds the 1010 group SIDs limit.
Typical end-user errors
Windows SMB / Azure Files - Mapping/mount attempts may fail with generic SMB errors (for example System error 86 or 1327 can appear in other policy conflicts like MFA). - Access may succeed for smaller-group users but intermittently fail for heavily grouped users in the same tenant due to user exceeding the 1010 group SIDs limit.
Sign in vs. resource access - Sign-in and PRT issuance succeed; failures happen at service ticket time (when the user accesses a Kerberos protected resource).
Entra Sign-in log entry - The error 140011 - KerberosUsersGroupNumberExceeded in the Entra sign-in log indicates that the Kerberos ticket issuance process failed because the user's effective group membership exceeded the maximum allowed number of Security Identifiers (SIDs) in a Kerberos ticket. Admin should reduce group memberships for affected users (especially nested/dynamic groups).
How to update Tags attribute in application manifest file
Option 1: Update Tags in the Entra Admin Portal
- Sign in to Microsoft Entra admin center or Cloud Application Administrator role.
- Navigate to:
- Entra ID → App registrations → Select your application.
- Under Manage, click Manifest.
- In the JSON editor, locate the tags property and add "kdc_enable_cloud_group_sids".
- Click Save to apply changes.
Option 2: Update Tags Using Microsoft Graph API (Permissions: Application.ReadWrite.All)
Request body
PATCH https://microsoftgraph.chinacloudapi.cn/v1.0/applications/{applicationObjectId}
Content-Type: application/json
{
"tags": [
"kdc_enable_cloud_group_sids"
]
}
Option 3: Update Tags Using PowerShell cmdlets
Start PowerShell with administrator privileges.
Install and import the Microsoft Graph PowerShell SDK.
Install-Module Microsoft.Graph -Scope CurrentUser Import-Module Microsoft.Graph.Authentication Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope CurrentUserConnect to the tenant and accept all.
Connect-MgGraph -Environment China -ClientId 'YOUR_CLIENT_ID' -TenantId 'YOUR_TENANT_ID' -Scopes "Application.ReadWrite.All"List certificateUserIds attribute of a given user.
Update-MgApplication -ApplicationId "<AppObjectId>" -Tags @("kdc_enable_cloud_group_sids")