Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
The preview of Group Writeback v2 in Microsoft Entra Connect Sync is deprecated and no longer supported.
If you provision Microsoft 365 groups to AD DS, you can keep using Group Writeback v1.
Group writeback is a feature that you can use to write cloud groups back to your on-premises Active Directory instance by using Microsoft Entra Connect Sync. Group writeback V2 using Microsoft Entra Connect was deprecated. Group writeback V1 using Microsoft Entra Connect still functions, and you should use it if you're synchronizing Microsoft 365 groups.
This article provides information and walks you through how to enable group writeback V1.
Important
This article describes how to enable group writeback V1 with Microsoft Entra Connect Sync. Only customers who provision Microsoft 365 groups to Active Directory should use it.
Prerequisites and information
To enable group writeback, you must have:
- Microsoft Entra Premium licenses for your tenant.
- A hybrid deployment configured between your Exchange on-premises organization and Microsoft 365 and verify that it's functioning correctly.
- A supported version of Exchange installed on-premises.
- Single sign-on configured by using Microsoft Entra Connect.
Consider the following information when you use group writeback V1 with Microsoft Entra Connect Sync:
- Microsoft 365 groups with up to 250,000 members can be written back to on-premises.
- If you don't want to write back all existing Microsoft 365 groups to Active Directory, make changes to group writeback default behavior before you perform the steps in this article to enable the feature. For more information, see Modify Microsoft 365 groups.
Enable group writeback
To enable group writeback, follow these steps:
Open the Microsoft Entra Connect wizard, select Configure, and then select Next.
Select Customize synchronization options and then select Next.
On the Connect to Azure AD page, enter your credentials. Select Next.
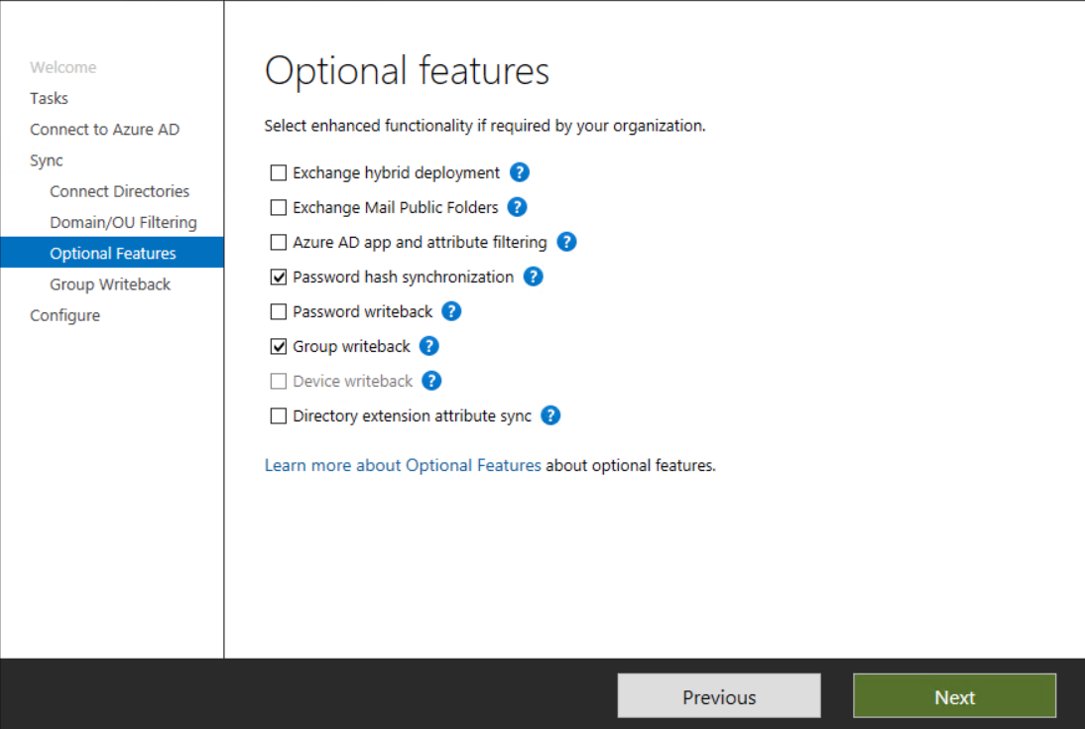
On the Optional features page, verify that the options you previously configured are still selected.
Select Group writeback and then select Next.
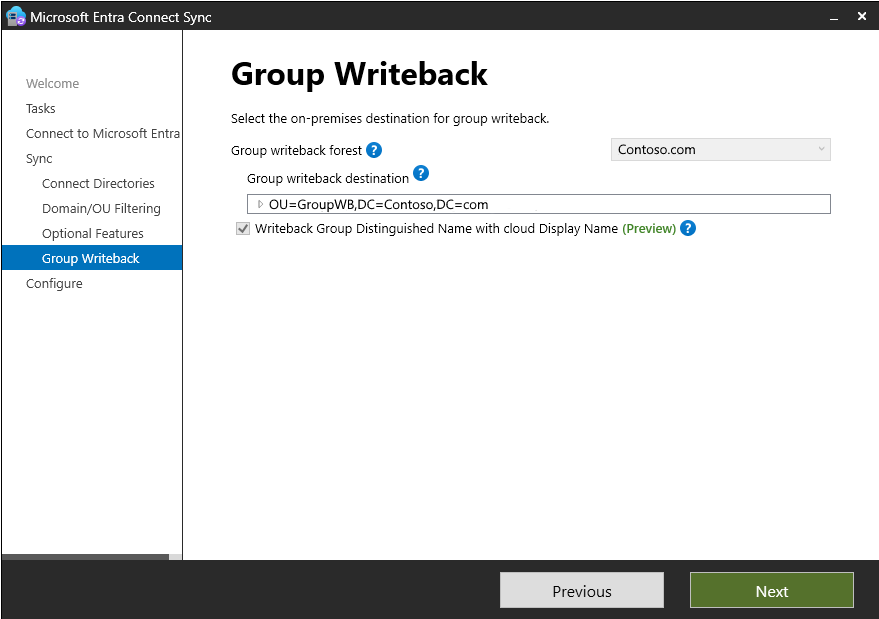
On the Group Writeback page, select an Active Directory organizational unit to store objects that are synced from Microsoft 365 to your on-premises organization. Then select Next.
To make it easier to find groups being written back from Microsoft Entra ID to Active Directory, select the Writeback group Distinguished Name with cloud Display Name option:
Default format:
CN=Group_3a5c3221-c465-48c0-95b8-e9305786a271, OU=WritebackContainer, DC=domain, DC=comNew format:
CN=Administrators_e9305786a271, OU=WritebackContainer, DC=domain, DC=com
When you configure group writeback, a checkbox appears at the bottom of the configuration window. Select it to enable this feature.
Groups that are written back from Microsoft Entra ID to Active Directory have a source of authority in the cloud. Any changes made on-premises to groups that are written back from Microsoft Entra ID are overwritten in the next sync cycle.
On the Ready to configure page, select Configure.
When the wizard is complete, on the Configuration complete page, select Exit.
Open Windows PowerShell as an administrator on the Microsoft Entra Connect server, and run the following commands:
$AzureADConnectSWritebackAccountDN = <MSOL_ account DN> Import-Module "C:\Program Files\Azure Active Directory Connect\AdSyncConfig\AdSyncConfig.psm1" # To grant the <MSOL_account> permission to all domains in the forest: Set-ADSyncUnifiedGroupWritebackPermissions -ADConnectorAccountDN $AzureADConnectSWritebackAccountDN # To grant the <MSOL_account> permission to specific OU (eg. the OU chosen to writeback Office 365 Groups to): $GroupWritebackOU = <DN of OU where groups are to be written back to> Set-ADSyncUnifiedGroupWritebackPermissions -ADConnectorAccountDN $AzureADConnectSWritebackAccountDN -ADObjectDN $GroupWritebackOU
For more information on how to configure Microsoft 365 groups, see Configure Microsoft 365 groups with on-premises Exchange hybrid.
Disable group writeback
To disable group writeback, follow these steps:
Open the Microsoft Entra Connect wizard and go to the Additional tasks page. Select the Customize synchronization options task and select Next.
On the Optional features page, clear the Group writeback checkbox. A warning states that you are about to delete groups. Select Yes.
When you disable group writeback, any groups that were previously created with this feature are deleted from your local Active Directory instance on the next sync cycle.
Select Next.
Select Configure.
Disabling group writeback sets the Full Import and Full Synchronization flags to true on the Microsoft Entra Connector. The rule changes propagate through on the next sync cycle and delete the groups that were previously written back to Active Directory.
Modify default behavior for Microsoft 365 groups
The following sections provide guidance on how to modify the default behavior for Microsoft 365 groups.
Write back Microsoft 365 groups with up to 250,000 members
Because the default synchronization rule that limits the group size is created when group writeback is enabled, you must complete the following steps after you enable group writeback:
On your Microsoft Entra Connect server, open a PowerShell prompt as an administrator.
Disable the Microsoft Entra Connect Sync scheduler:
Set-ADSyncScheduler -SyncCycleEnabled $falseOpen the Synchronization Rules Editor.
Set the direction to Outbound.
Locate and disable the Out to AD - Group Writeback Member Limit synchronization rule.
Enable the Microsoft Entra Connect Sync scheduler:
Set-ADSyncScheduler -SyncCycleEnabled $true
Disabling the synchronization rule sets the flag for full synchronization to true on the Microsoft Entra Connector. This change causes the rule changes to propagate through on the next sync cycle.