Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Entra Health provides tenant-level metrics and health signals for several key identity scenarios. These signals are fed into an anomaly detection service, which triggers alerts when significant changes are detected. You can configure email and webhook notifications for when an alert is triggered.
This article describes how to configure email and webhook notifications for Microsoft Entra Health monitoring alerts.
Important
Microsoft Entra Health scenario monitoring and alerts are currently in PREVIEW. This information relates to a prerelease product that might be substantially modified before release. Microsoft makes no warranties, expressed or implied, with respect to the information provided here. The Microsoft Entra admin center experience is being released to customers in phases, so you might not see all the features described in this article.
Prerequisites
There are different roles, permissions, and license requirements to view health monitoring signals and configure and receive alerts. We recommend using a role with least privilege access to align with the Zero Trust guidance.
- A tenant with a Microsoft Entra P1 or P2 license is required to view the Microsoft Entra health scenario monitoring signals.
- A tenant with both a non-trial Microsoft Entra P1 or P2 license and at least 100 monthly active users is required to view alerts and receive alert notifications.
- The Reports Reader role is the least privileged role required to view scenario monitoring signals, alerts, and alert configurations.
- The Helpdesk Administrator is the least privileged role required to update alerts and update alert notification configurations.
- The
Group.Read.Allpermission is the least privileged permission required to view groups. - The
HealthMonitoringAlert.Read.Allpermission is required to view the alerts using the Microsoft Graph API. - The
HealthMonitoringAlert.ReadWrite.Allpermission is required to view and modify the alerts using the Microsoft Graph API. - The
HealthMonitoringAlertConfig.Read.Allpermission is required to view the configured email notifications using Microsoft Graph /reports/healthmonitoring/alertConfigurations/{alertType} API or to view the configured webhook notifications using Microsoft Graph /subscriptions API. - The
HealthMonitoringAlertConfig.ReadWrite.Allpermission is required to view and modify email notifications using Microsoft Graph /reports/healthmonitoring/alertConfigurations/{alertType} API or to view and modify the configured webhook notifications using Microsoft Graph /subscriptions API. - For a full list of roles, see Least privileged role by task.
Note
- Newly onboarded tenants might not have enough data to generate alerts for about 30 days.
- If you see error due to missing required Microsoft Graph permissions, see Microsoft Graph permissions to get more information about Microsoft Graph permissions.
Determine email notification recipients
We recommend daily review of the Microsoft Entra Health monitoring scenarios so you're familiar with the baseline metrics and so you can identify trends. It's important to also configure email notifications for when an alert is triggered.
Email notifications are sent to the Microsoft Entra group of your choice. We recommend sending alerts to users with the appropriate access to investigate and take action on the alerts. Not every role can take the same action, so consider including a group with the following roles:
Configure email notifications
Email notification settings can be configured for each scenario in the Microsoft Entra admin center.
Sign in to the Microsoft Entra admin center as at least a Helpdesk Administrator.
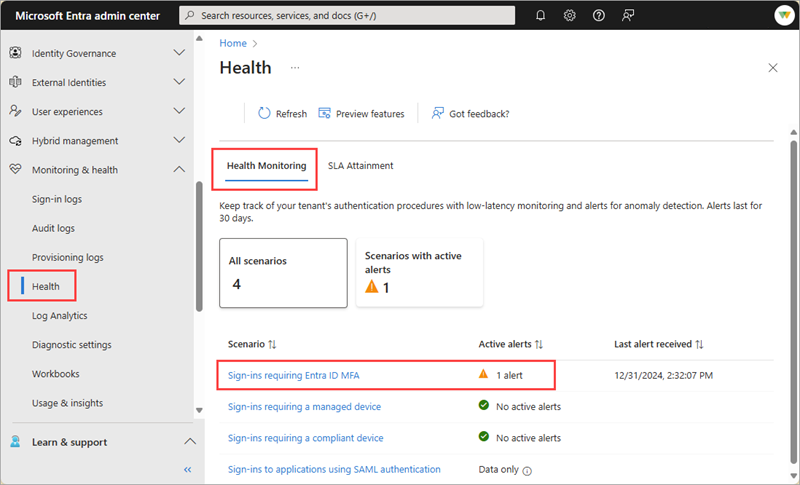
Browse to Entra ID > Monitoring & health > Health and select the Health monitoring tab.
Select the scenario you want to configure email notifications for.
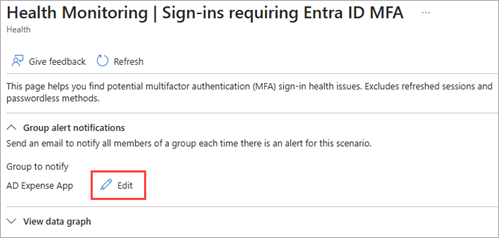
From the Group alert notifications section, select either the +Select or Edit button.
- If no group is selected, the +Select button is displayed.
- If a group is already selected, the Edit button is displayed.
From the panel that opens, select the group you want to receive the alerts and select the Select button.
- Only one group can be selected.
- The group is updated in the Group alert notifications section of the scenario page.
Members of the selected group will receive an email notification the next time an alert is triggered for the scenario. Repeat this process for the other scenarios.
Note
If the selected group has other groups added as members of that group, the notifications are sent to only the top three groups in the hierarchy.
Configure webhook notifications
Microsoft Graph change notifications allow your application to receive real-time alerts whenever a resource is created, updated, or deleted. Unlike email notifications, these alerts are delivered directly to a secure HTTPS endpoint that you specify, making them ideal for automated workflows and integrations. Currently, change notifications for health monitoring alert creations are supported through webhooks. Microsoft Graph supports notifications for create, update, and delete operations, but at this time only alert creation notifications are available for health monitoring alerts.
To start receiving notifications, your application sends a POST request to the /subscriptions endpoint to subscribe to a specific resource, in this case, health monitoring alerts. Microsoft Graph then validates the request and confirms the subscription. Once the subscription is active, Microsoft Graph sends a notification to your designated endpoint whenever the subscribed resource is created. For more information, see Microsoft Graph change notifications.
Note
If you see an error due to missing required Microsoft Graph permissions, see Microsoft Graph permissions.
After receiving a notification, you should investigate the alert through the Microsoft Entra admin center. If you need to assess the alert's impact, we recommend either polling or introducing a short delay before calling the health monitoring alert API for impact assessment data to be available. For more information, see How to investigate health scenario alerts.
The following example shows a basic request to subscribe to changes to Health Monitoring alert changes.
Example subscription request
POST https://microsoftgraph.chinacloudapi.cn/**beta**/subscriptions
Content-Type: application/json
{
"changeType": "created",
"notificationUrl": "https://webhook.chinacloudsites.cn/notificationClient",
"lifecycleNotificationUrl": "https://webhook.chinacloudsites.cn/api/lifecycleNotifications",
"resource": "/reports/healthmonitoring/alerts",
"expirationDateTime": "2025-08-30T11:00:00.0000000Z",
"clientState": "SecretClientState"
}
If you want to subscribe to notifications for only one specific alert type, amend the request to include the following details:
"notificationQueryOptions":"$filter=alertType eq 'mfaSignInFailure'