Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article explains how to create a custom role with permissions to manage enterprise app assignments for users and groups in Microsoft Entra ID. For the elements of roles assignments and the meaning of terms such as subtype, permission, and property set, see the custom roles overview.
Prerequisites
- Microsoft Entra ID P1 or P2 license
- Privileged Role Administrator
- Microsoft Graph PowerShell module when using PowerShell
For more information, see Prerequisites to use PowerShell.
Enterprise app role permissions
There are two enterprise app permissions discussed in this article. All examples use the update permission.
- To read the user and group assignments at scope, grant the
microsoft.directory/servicePrincipals/appRoleAssignedTo/readpermission - To manage the user and group assignments at scope, grant the
microsoft.directory/servicePrincipals/appRoleAssignedTo/updatepermission
Granting the update permission results in the assignee being able to manage assignments of users and groups to enterprise apps. The scope of user and/or group assignments can be granted for a single application or granted for all applications. If granted at an organization-wide level, the assignee can manage assignments for all applications. If made at an application level, the assignee can manage assignments for only the specified application.
Granting the update permission is done in two steps:
- Create a custom role with permission
microsoft.directory/servicePrincipals/appRoleAssignedTo/update - Grant users or groups permissions to manage user and group assignments to enterprise apps. This is when you can set the scope to the organization-wide level or to a single application.
Create a new custom role
In the Microsoft Entra Admin Center, you can create and manage custom roles to control access and permissions for enterprise apps.
Note
Custom roles are created and managed at an organization-wide level and are available only from the organization's Overview page.
Sign in to the Microsoft Entra admin center as at least a Privileged Role Administrator.
Browse to Entra ID > Roles & admins.
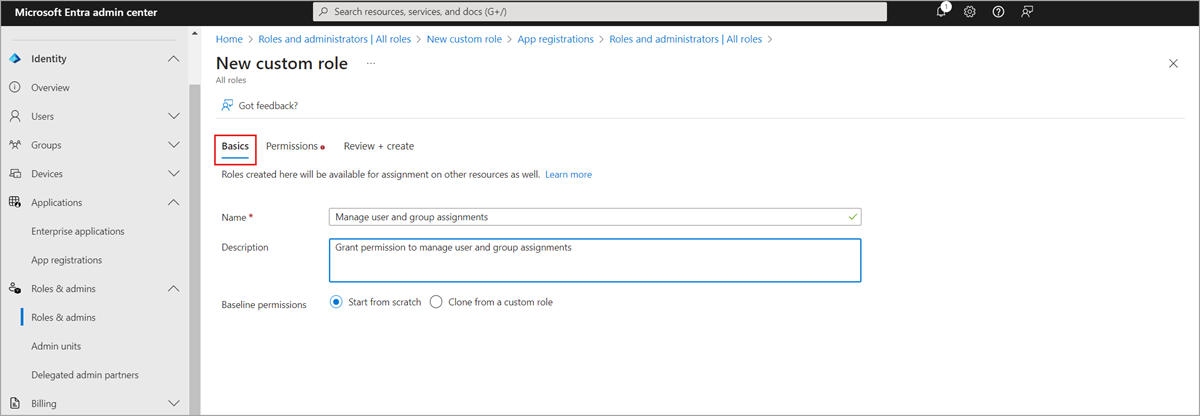
Select New custom role.
On the Basics tab, provide "Manage user and group assignments" for the name of the role and "Grant permissions to manage user and group assignments" for the role description, then select Next.
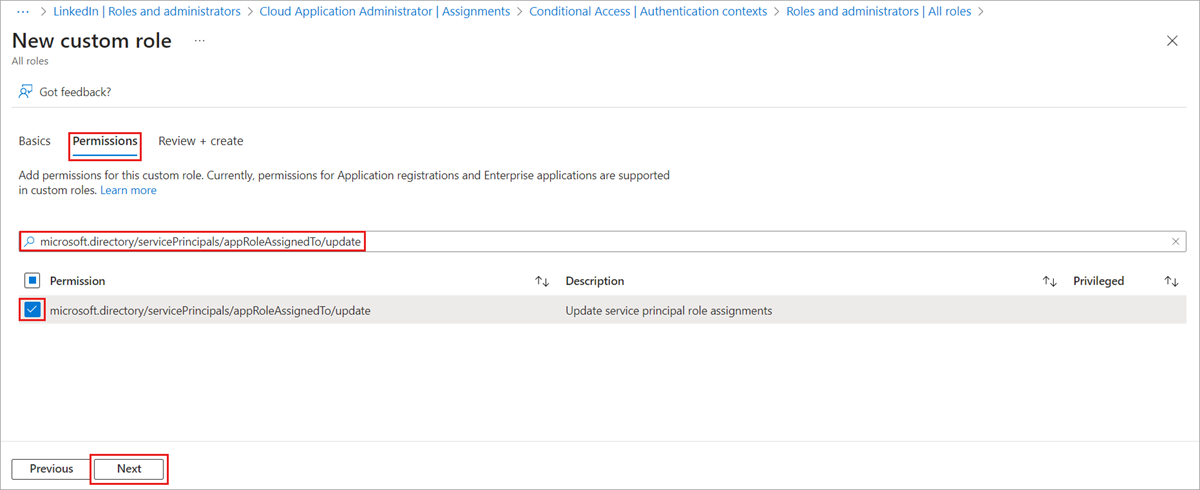
On the Permissions tab, enter "microsoft.directory/servicePrincipals/appRoleAssignedTo/update" in the search box, select the checkboxes next to the desired permissions, then select Next.
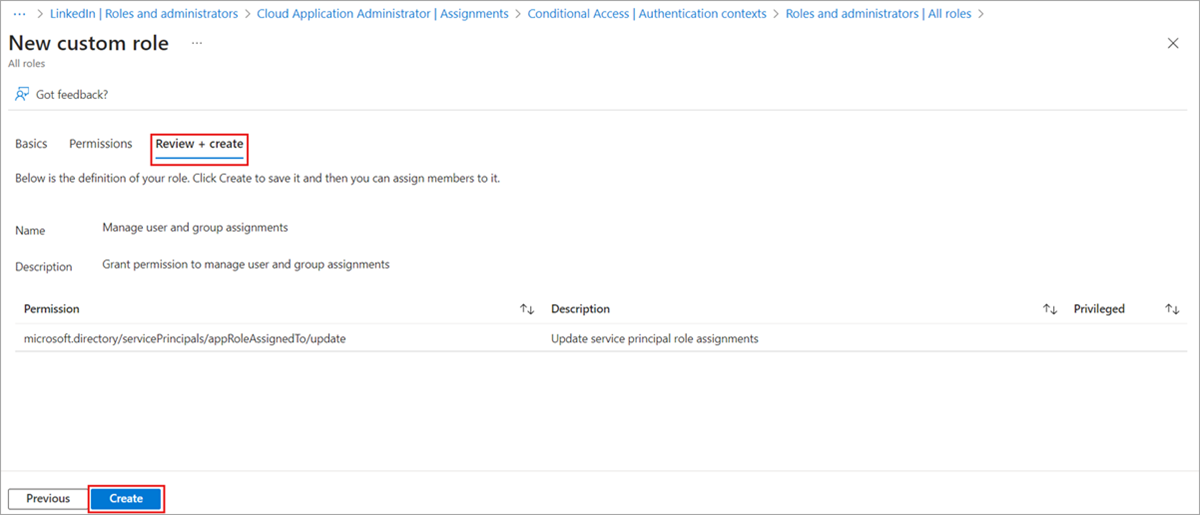
On the Review + create tab, review the permissions and select Create.
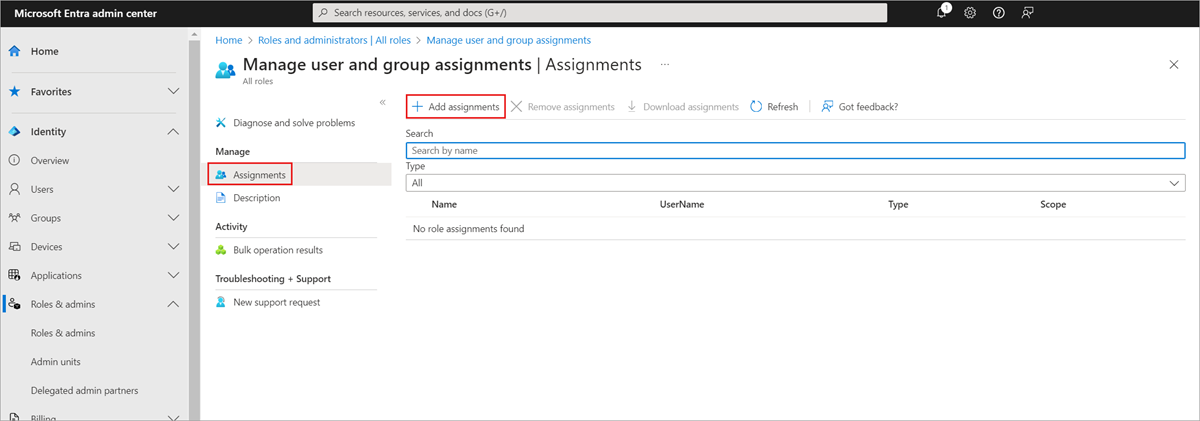
Assign the role to a user using the Microsoft Entra admin center
Sign in to the Microsoft Entra admin center as at least a Privileged Role Administrator.
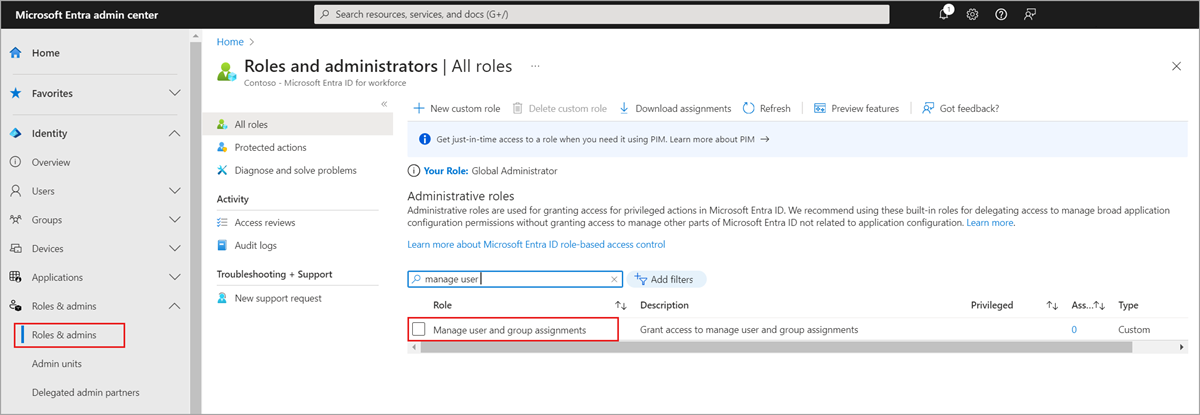
Browse to Entra ID > Roles & admins.
Select the Manage user and group assignments role.
Select Add assignment, select the desired user, and then click Select to add role assignment to the user.
Assignment tips
To grant permissions to assignees to manage users and group access for all enterprise apps organization-wide, start from the organization-wide Roles and Administrators list on the Microsoft Entra ID Overview page for your organization.
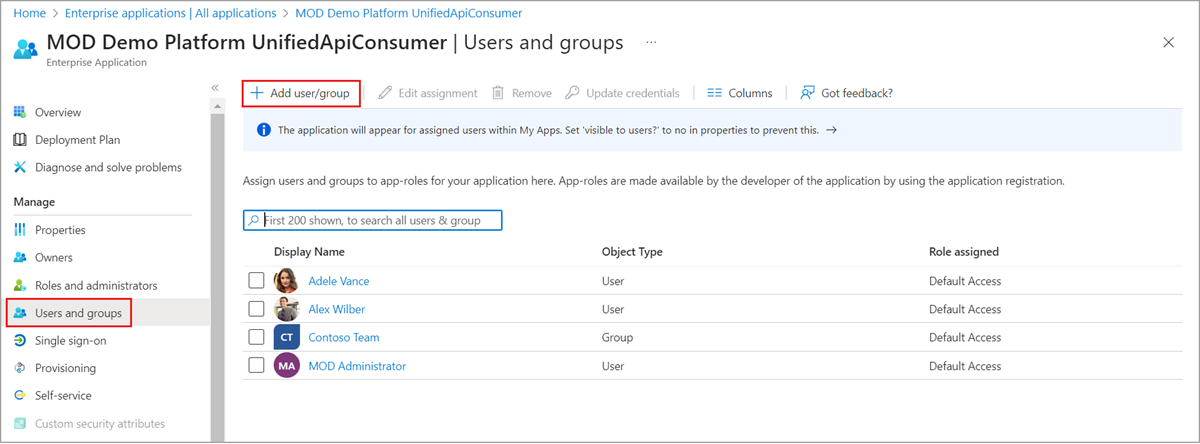
To grant permissions to assignees to manage users and group access for a specific enterprise app, go to that app in Microsoft Entra ID and open in the Roles and Administrators list for that app. Select the new custom role and complete the user or group assignment. The assignees can manage users and group access only for the specific app.
To test your custom role assignment, sign in as the assignee and open an application’s Users and groups page to verify that the Add user option is enabled.