Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this article, you learn how to use the connection troubleshoot feature of Azure Network Watcher to diagnose and troubleshoot connectivity issues. For more information about connection troubleshoot, see Connection troubleshoot overview.
Prerequisites
An Azure account with an active subscription. Create a trial subscription.
Network Watcher enabled in the region of the virtual machine (VM) you want to troubleshoot. By default, Azure enables Network Watcher in a region when you create a virtual network in it. For more information, see Enable or disable Azure Network Watcher.
A virtual machine with the following outbound TCP connectivity:
- to 169.254.169.254 over port 80
- to 168.63.129.16 over port 8037
A second virtual machine with inbound TCP connectivity from 168.63.129.16 over the port being tested (for Port scanner diagnostic test).
Test connectivity to a virtual machine
In this section, you test the remote desktop port (RDP) connectivity from one virtual machine to another virtual machine in the same virtual network.
Sign in to the Azure portal.
In the search box at the top of the portal, enter network watcher. Select Network Watcher from the search results.
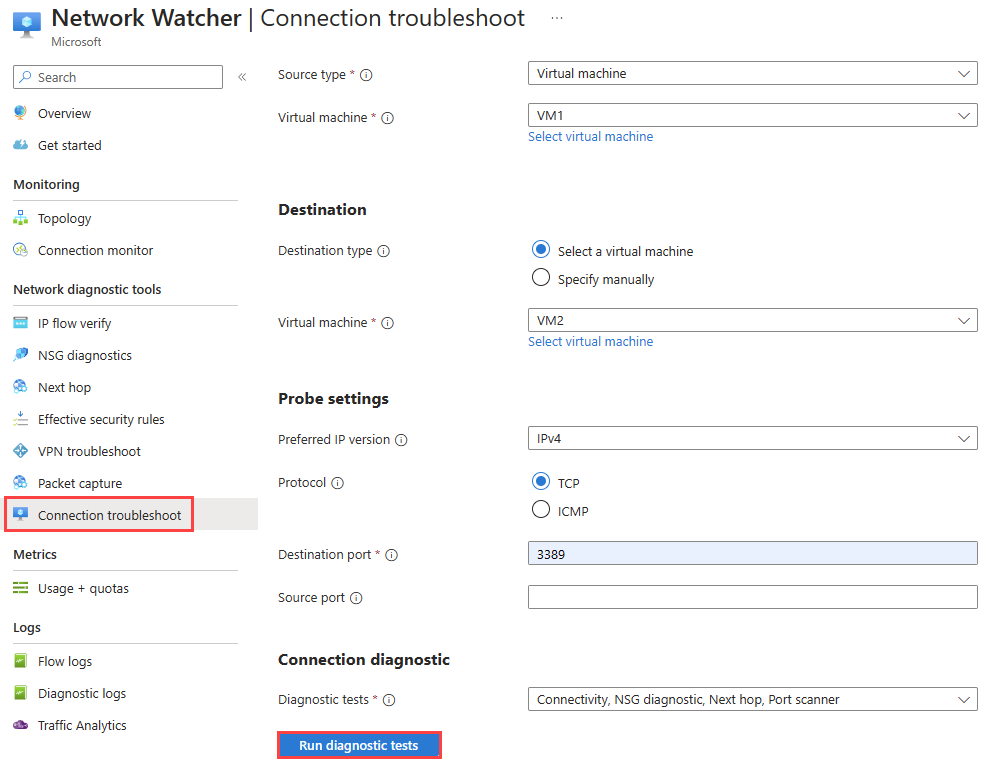
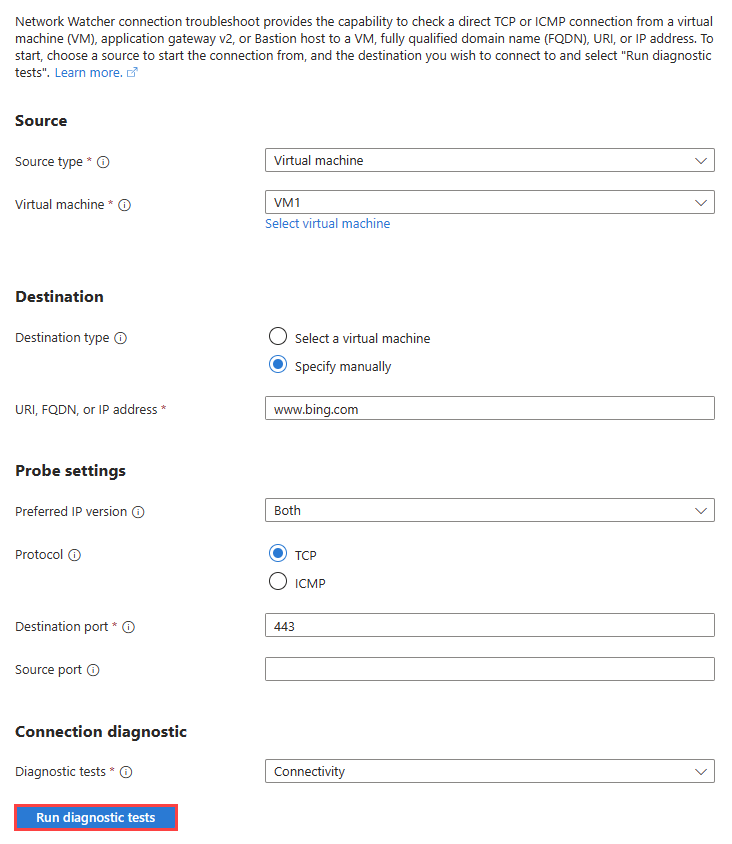
Under Network diagnostic tools, select Connection troubleshoot. Enter or select the following values:
Setting Value Source Source type Select Virtual machine. Virtual machine Select the virtual machine that you want to troubleshoot the connection from. Destination Destination type Select Select a virtual machine. Virtual machine Select the destination virtual machine. Probe Settings Preferred IP version Select IPv4. The other available options are: Both and IPv6. Protocol Select TCP. The other available option is: ICMP. Destination port Enter 3389. Port 3389 is the default port for RDP. Source port Leave blank or enter a source port number that you want to test. Connection Diagnostic Diagnostics tests Select Connectivity, NSG diagnostic, Next hop, and Port scanner. Select Run diagnostic tests.
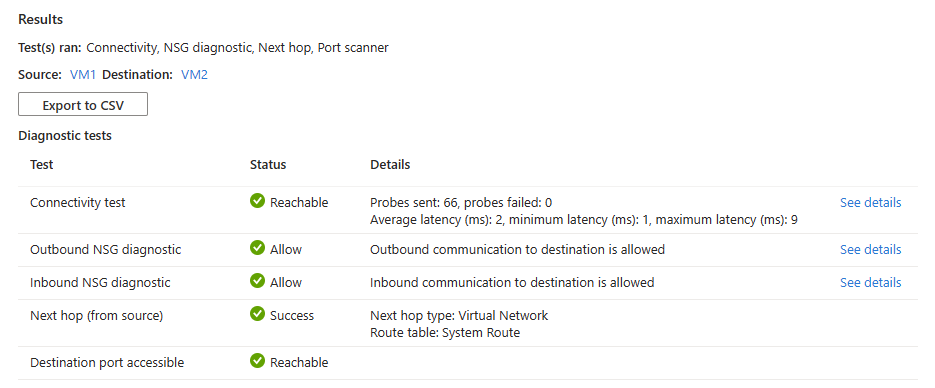
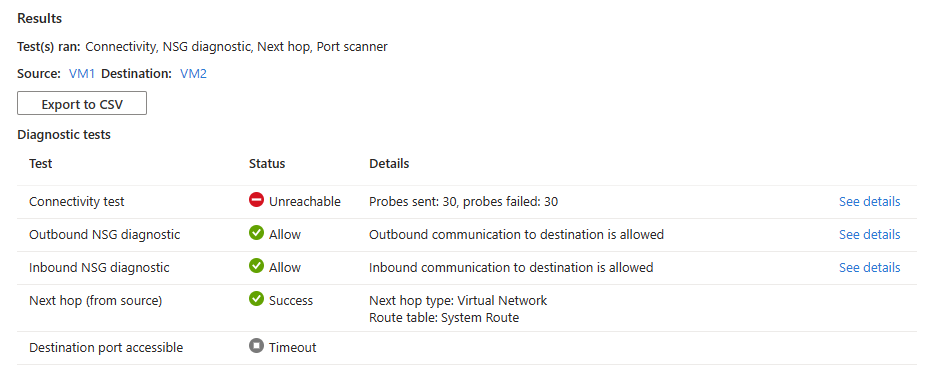
If the two virtual machines are communicating with no issues, you see the following results:
- 66 probes were successfully sent to the destination virtual machine. Select See details to see the next hop details.
- Outbound connectivity from the source virtual machine is allowed. Select See details to see the security rules that are allowing the outbound communication from the source virtual machine.
- Inbound connectivity to the destination virtual machine is allowed. Select See details to see the security rules that are allowing the inbound communication to the destination virtual machine.
- Azure default system route is used to route traffic between the two virtual machines (Route table ID: System route).
- Port 3389 is reachable on the destination virtual machine.
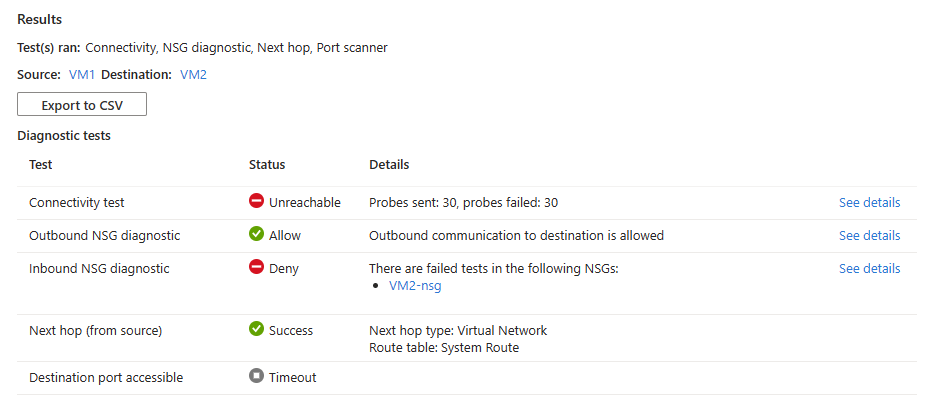
If the destination virtual machine has a network security group that's denying incoming RDP connections, you see the following results:
- 30 probes were sent and failed to reach the destination virtual machine. Select See details to see the next hop details.
- Outbound connectivity from the source virtual machine is allowed. Select See details to see the security rules that are allowing the outbound communication from the source virtual machine.
- Inbound connectivity to the destination virtual machine is denied. Select See details to see the security rule that is denying the inbound communication to the destination virtual machine.
- Azure default system route is used to route traffic between the two virtual machines (Route table ID: System route).
- Port 3389 is unreachable on the destination virtual machine because of the security rule that is denying inbound communication to the destination port.
Solution: Update the network security group on the destination virtual machine to allow inbound RDP traffic.
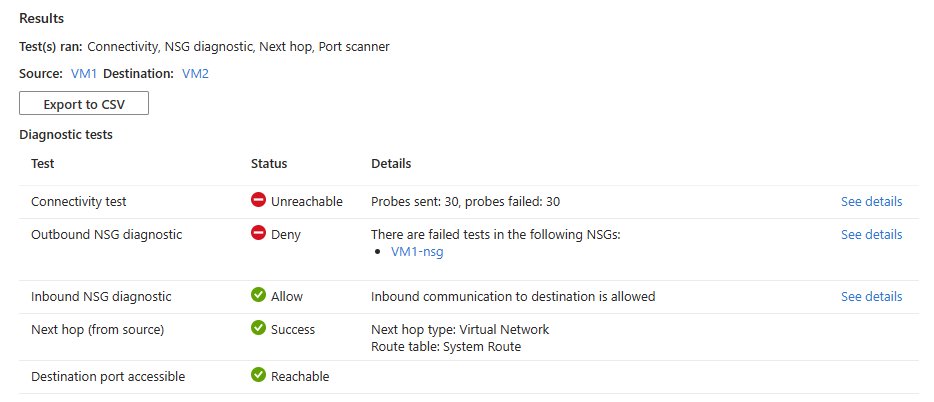
If the source virtual machine has a network security group that's denying RDP connections to the destination, you see the following results:
- 30 probes were sent and failed to reach the destination virtual machine. Select See details to see the next hop details.
- Outbound connectivity from the source virtual machine is denied. Select See details to see security rule that is denying the outbound communication from the source virtual machine.
- Inbound connectivity to the destination virtual machine is allowed. Select See details to see the security rules that are allowing the inbound communication to the destination virtual machine.
- Azure default system route is used to route traffic between the two virtual machines (Route table ID: System route).
- Port 3389 is reachable on the destination virtual machine.
Solution: Update the network security group on the source virtual machine to allow outbound RDP traffic.
If the operating system on the destination virtual machine doesn't accept incoming connections on port 3389, you see the following results:
- 30 probes were sent and failed to reach the destination virtual machine. Select See details to see the next hop details.
- Outbound connectivity from the source virtual machine is allowed. Select See details to see the security rules that are allowing the outbound communication from the source virtual machine.
- Inbound connectivity to the destination virtual machine is allowed. Select See details to see the security rules that are allowing the inbound communication to the destination virtual machine.
- Azure default system route is used to route traffic between the two virtual machines (Route table ID: System route).
- Port 3389 isn't reachable on the destination virtual machine (port 3389 on the operating system isn't accepting incoming RDP connections).
Solution: Configure the operating system on the destination virtual machine to accept inbound RDP traffic.
Select Export to CSV to download the test results in csv format.
Test connectivity to a web address
In this section, you test the connectivity between a virtual machine and a web address.
On the Connection troubleshoot page. Enter or select the following information:
Setting Value Source Source type Select Virtual machine. Virtual machine Select the virtual machine that you want to troubleshoot the connection from. Destination Destination type Select Specify manually. URI, FQDN, or IP address Enter the web address that you want to test the connectivity to. In this example, www.bing.comis used.Probe Settings Preferred IP version Select Both. The other available options are: IPv4 and IPv6. Protocol Select TCP. The other available option is: ICMP. Destination port Enter 443. Port 443 for HTTPS. Source port Leave blank or enter a source port number that you want to test. Connection Diagnostic Diagnostics tests Select Connectivity. Select Run diagnostic tests.
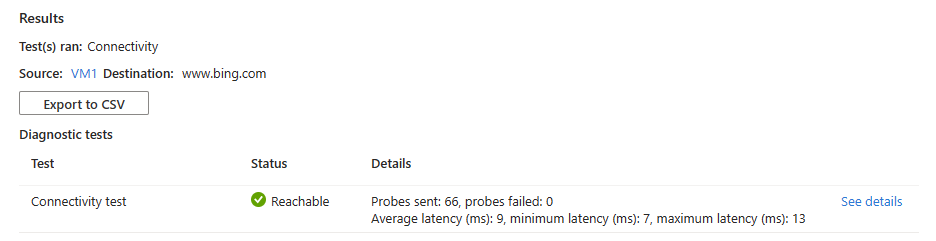
If
www.bing.comis reachable from the source virtual machine, you see the following results:66 probes were successfully sent to
www.bing.com. Select See details to see the next hop details.If
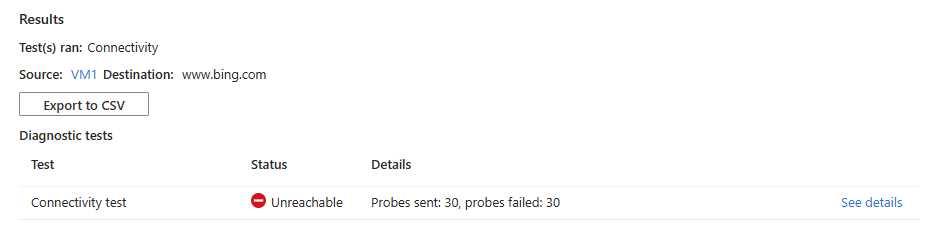
www.bing.comis unreachable from the source virtual machine due to a security rule, you see the following results:30 probes were sent and failed to reach
www.bing.com. Select See details to see the next hop details and the cause of the error.Solution: Update the network security group on the source virtual machine to allow outbound traffic to
www.bing.com.
Select Export to CSV to download the test results in csv format.
Test connectivity to an IP address
In this section, you test the connectivity between a virtual machine and an IP address of another virtual machine.
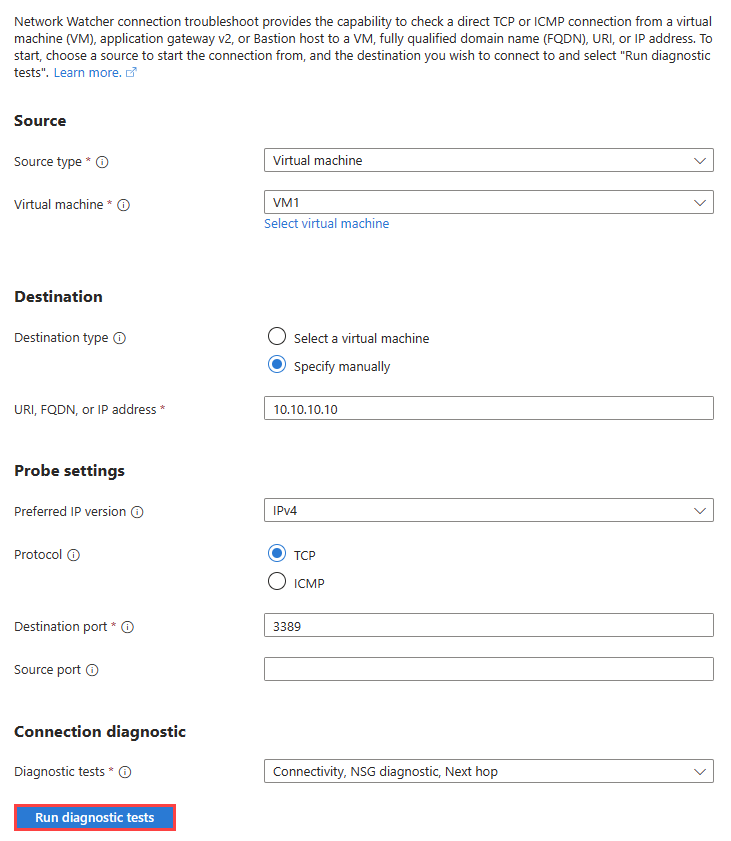
On the Connection troubleshoot page. Enter or select the following information:
Setting Value Source Source type Select Virtual machine. Virtual machine Select the virtual machine that you want to troubleshoot the connection from. Destination Destination type Select Specify manually. URI, FQDN, or IP address Enter the IP address that you want to test the connectivity to. In this example, 10.10.10.10is used.Probe Settings Preferred IP version Select IPv4. The other available options are: Both and IPv6. Protocol Select TCP. The other available option is: ICMP. Destination port Enter 3389. Source port Leave blank or enter a source port number that you want to test. Connection Diagnostic Diagnostics tests Select Connectivity, NSG diagnostic, and Next hop. Select Run diagnostic tests.
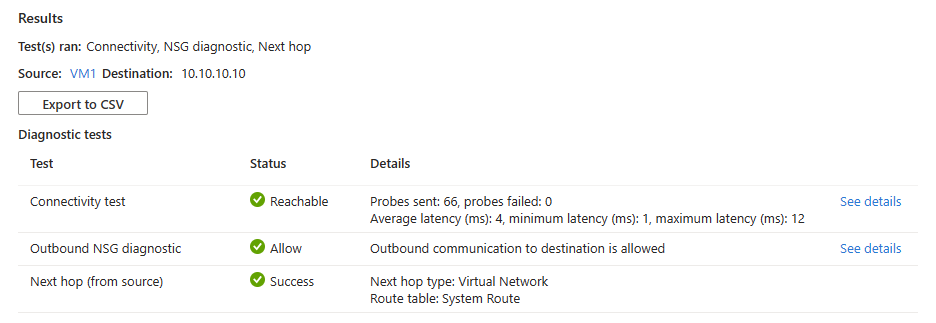
If the IP address is reachable, you see the following results:
- 66 probes were successfully sent with average latency of 4 ms. Select See details to see the next hop details.
- Outbound connectivity from the source virtual machine is allowed. Select See details to see the security rules that are allowing the outbound communication from the source virtual machine.
- Azure default system route is used to route traffic to the IP address, which is in the same virtual network or a peered virtual network. (Route table ID: System route and Next hop type: Virtual Network).
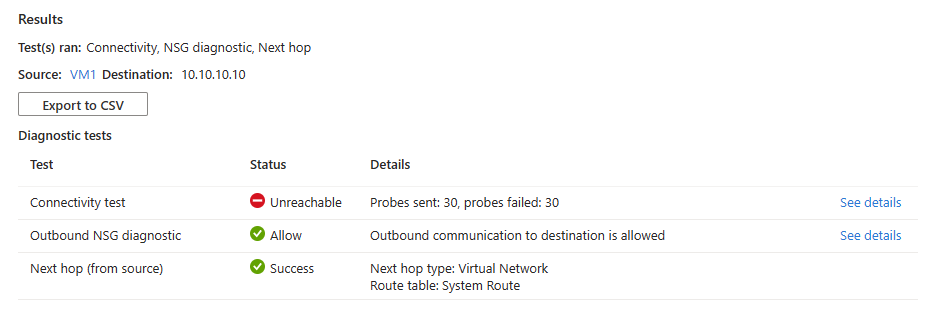
If the IP address is unreachable because the destination virtual machine isn't running, you see the following results:
- 30 probes were sent and failed to reach the destination virtual machine. Select See details to see the next hop details.
- Outbound connectivity from the source virtual machine is allowed. Select See details to see the security rules that are allowing the outbound communication from the source virtual machine.
- Azure default system route is used to route traffic to the IP address, which is in the same virtual network or a peered virtual network. (Route table ID: System route and Next hop type: Virtual Network).
Solution: Start the destination virtual machine.
If there's no route to the IP address in the routing table of the source virtual machine (for example, the IP address isn't in the address space of the VM's virtual network or its peered virtual networks), you see the following results:
- 30 probes were sent and failed to reach the destination virtual machine. Select See details to see the next hop details.
- Outbound connectivity from the source virtual machine is denied. Select See details to see security rule that is denying the outbound communication from the source virtual machine.
- Next hop type is None because there isn't a route to the IP address.
Solution: Associate a route table with a correct route to the subnet of the source virtual machine.
Select Export to CSV to download the test results in csv format.