Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this article, you create a linked service in Azure Data Factory to connect to an Azure Database for PostgreSQL flexible server instance using a private endpoint.
Azure Data Factory is a fully managed, serverless, data integration service built to orchestrate and operationalize complex hybrid extract-transform-load (ETL), extract-load-transform (ELT), and data integration projects. An Azure integration runtime supports connecting to data stores and compute services with public accessible endpoints. If you enable the managed virtual network feature of an Azure integration runtime, it supports connecting to data stores using Azure Private Link service in private network environments.
Data Factory offers an Azure Database for PostgreSQL connector with support for various capabilities, depending on the integration runtime selected.
Prerequisites
- An Azure Database for PostgreSQL flexible server instance with its network connectivity method configured as Public access (allowed IP addresses) so that you can create private endpoints to connect to it privately using Azure Private Link.
- An Azure integration runtime created within a managed virtual network.
Create a private endpoint in Data Factory
Using the Azure Database for PostgreSQL connector you can connect to an Azure Database for PostgreSQL flexible server instance routing all traffic privately, through a managed private endpoint.
You can create the managed private endpoint using the user interface provided for such purpose in the Managed private endpoints option, under the Security section of the Manage hub of Azure Data Factory Studio, as described in managed private endpoints. As an alternative, you can use the corresponding Azure CLI command, az datafactory managed-private-endpoint create, to create a managed private endpoint in Azure Data Factory.
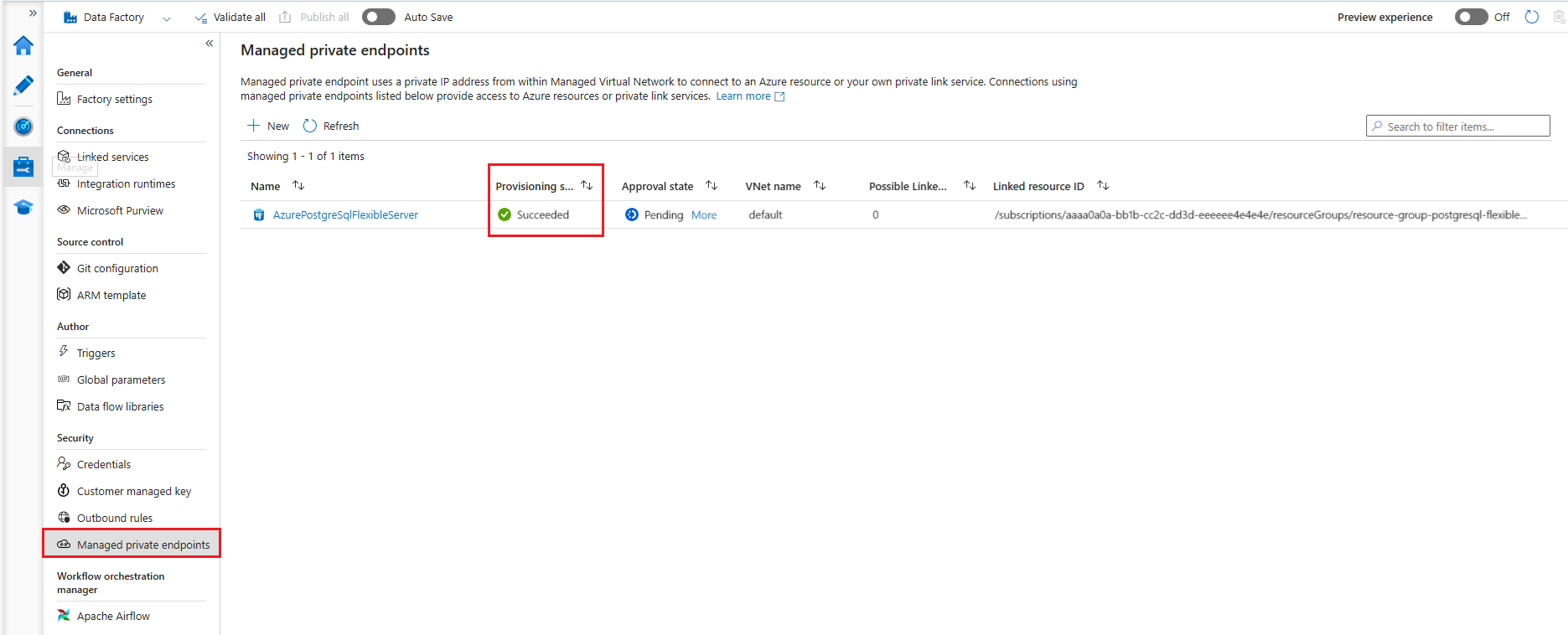
After successfully deployed, the managed private endpoint shows like this in the Managed private endpoints page of Azure Data Factory Studio:
Approve a private endpoint
After you deploy a private endpoint, you must approve it to permit incoming traffic. Suppose you have access to Azure Data Factory and have permission to approve private endpoints created against the instance of Azure Database for PostgreSQL flexible server. In that case, you can use the Managed private endpoints page of Azure Data Factory Studio, select the name of the managed private endpoint and, on the opening pane, select Manage approvals in Azure portal.
The previous action takes you to the Networking page of the Azure Database for PostgreSQL flexible server instance, to which the Azure Data Factory managed private endpoint points.
If you don't have permission to approve the private endpoint, ask someone with such permissions to do so for you.
The data factory might take several minutes to discover that the private endpoint is approved.
When the managed private endpoint is successfully deployed and approved, it shows like this in the Managed private endpoints page of Azure Data Factory Studio:
Add a linked service to connect to your Azure Database for PostgreSQL
With the private endpoint deployed and approved, you can finally use your data factory's Azure Database for PostgreSQL connector to create a linked service. You can connect to your instance of Azure Database for PostgreSQL flexible server through that linked service.
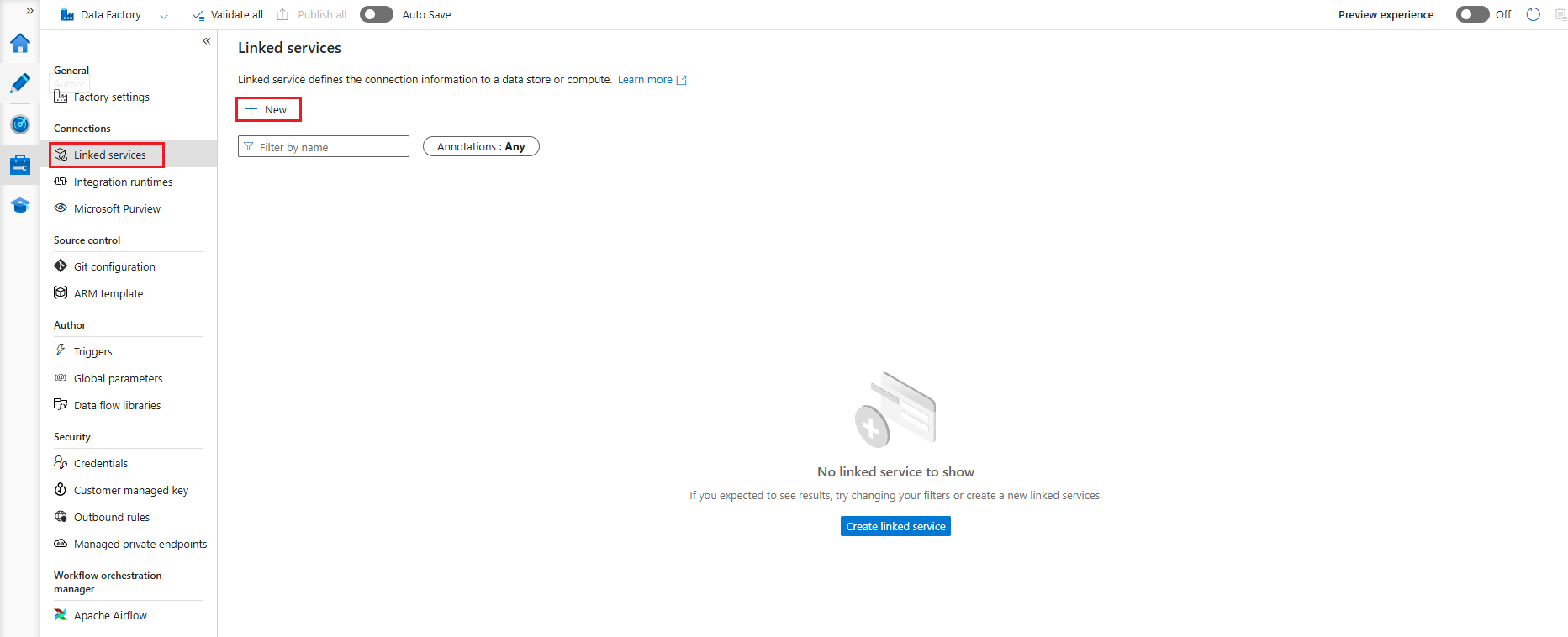
In Azure Data Factory Studio select the Manage hub and, under the Connections section, select Linked services, and select New to create a new linked service:
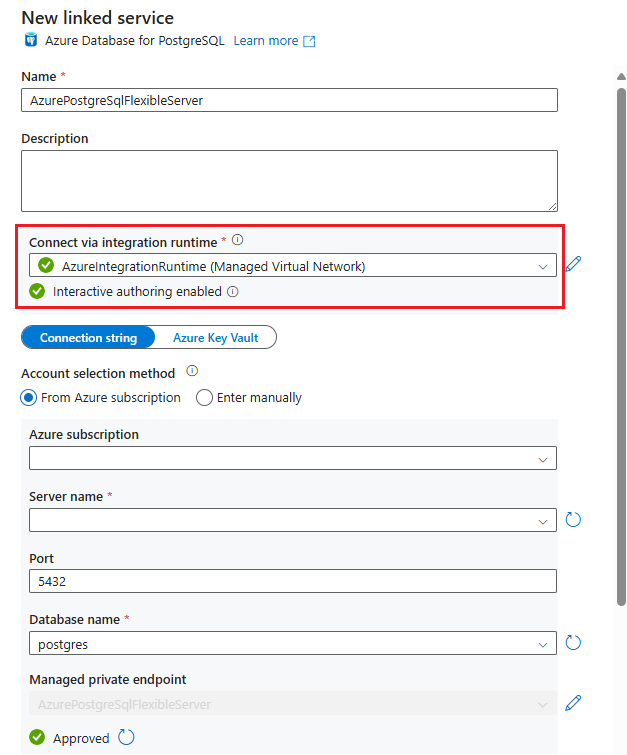
Fill all required fields for the connector. Ensure that the integration runtime selected is the one on which you created the private endpoint in its managed virtual network. Also, make sure that the Interactive authoring feature is enabled on that integration runtime so that you can test the connection when all required information is provided.
Select an Encryption method. If you select No encryption, the connection only succeeds if the server parameter require_secure_transport is set to
off, which isn't a recommended practice since it relaxes security.Select Test connection. A Connection successful message should appear next to the Test connection button.