Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
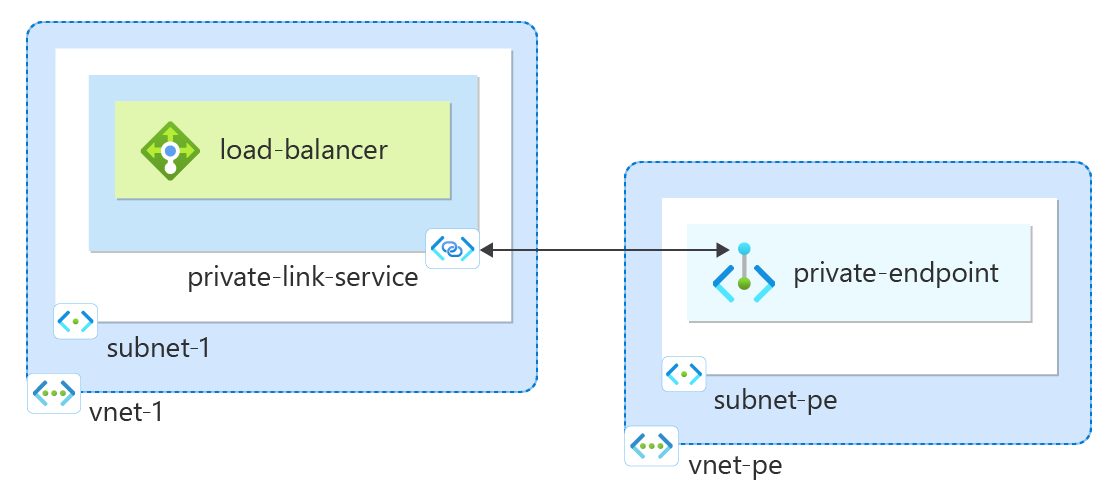
Get started creating a Private Link service that refers to your service. Give Private Link access to your service or resource deployed behind an Azure Standard Load Balancer. Users of your service have private access from their virtual network.
Prerequisites
An Azure account with an active subscription. Create a trial subscription.
Azure PowerShell.
You can install Azure PowerShell locally to run the cmdlets. The steps in this article require Azure PowerShell module version 5.4.1 or later. Run
Get-Module -ListAvailable Azto find your installed version. If you need to upgrade, see Update the Azure PowerShell module.If you run PowerShell locally, run
Connect-AzAccount -Environment AzureChinaCloudto connect to Azure.
Create a resource group
An Azure resource group is a logical container into which Azure resources are deployed and managed.
Create a resource group with New-AzResourceGroup:
New-AzResourceGroup -Name 'test-rg' -Location 'chinaeast2'
Create an internal load balancer
In this section, you create a virtual network and an internal Azure Load Balancer.
Virtual network
In this section, you create a virtual network and subnet to host the load balancer that accesses your Private Link service.
- Create a virtual network with New-AzVirtualNetwork.
## Create backend subnet config ##
$subnet = @{
Name = 'subnet-1'
AddressPrefix = '10.0.0.0/24'
}
$subnetConfig = New-AzVirtualNetworkSubnetConfig @subnet
## Create the virtual network ##
$net = @{
Name = 'vnet-1'
ResourceGroupName = 'test-rg'
Location = 'chinaeast2'
AddressPrefix = '10.0.0.0/16'
Subnet = $subnetConfig
}
$vnet = New-AzVirtualNetwork @net
Create standard load balancer
This section details how you can create and configure the following components of the load balancer:
Create a front-end IP with New-AzLoadBalancerFrontendIpConfig for the frontend IP pool. This IP receives the incoming traffic on the load balancer
Create a back-end address pool with New-AzLoadBalancerBackendAddressPoolConfig for traffic sent from the frontend of the load balancer. This pool is where your backend virtual machines are deployed.
Create a health probe with Add-AzLoadBalancerProbeConfig that determines the health of the backend VM instances.
Create a load balancer rule with Add-AzLoadBalancerRuleConfig that defines how traffic is distributed to the VMs.
Create a public load balancer with New-AzLoadBalancer.
## Place virtual network created in previous step into a variable. ##
$vnet = Get-AzVirtualNetwork -Name 'vnet-1' -ResourceGroupName 'test-rg'
## Create load balancer frontend configuration and place in variable. ##
$lbip = @{
Name = 'frontend'
PrivateIpAddress = '10.0.0.4'
SubnetId = $vnet.subnets[0].Id
}
$feip = New-AzLoadBalancerFrontendIpConfig @lbip
## Create backend address pool configuration and place in variable. ##
$bepool = New-AzLoadBalancerBackendAddressPoolConfig -Name 'backend-pool'
## Create the health probe and place in variable. ##
$probe = @{
Name = 'health-probe'
Protocol = 'http'
Port = '80'
IntervalInSeconds = '360'
ProbeCount = '5'
RequestPath = '/'
}
$healthprobe = New-AzLoadBalancerProbeConfig @probe
## Create the load balancer rule and place in variable. ##
$lbrule = @{
Name = 'http-rule'
Protocol = 'tcp'
FrontendPort = '80'
BackendPort = '80'
IdleTimeoutInMinutes = '15'
FrontendIpConfiguration = $feip
BackendAddressPool = $bePool
}
$rule = New-AzLoadBalancerRuleConfig @lbrule -EnableTcpReset
## Create the load balancer resource. ##
$loadbalancer = @{
ResourceGroupName = 'test-rg'
Name = 'load-balancer'
Location = 'chinaeast2'
Sku = 'Standard'
FrontendIpConfiguration = $feip
BackendAddressPool = $bePool
LoadBalancingRule = $rule
Probe = $healthprobe
}
New-AzLoadBalancer @loadbalancer
Disable network policy
Before a private link service can be created in the virtual network, the setting privateLinkServiceNetworkPolicies must be disabled.
- Disable the network policy with Set-AzVirtualNetwork.
## Place the subnet name into a variable. ##
$subnet = 'subnet-1'
## Place the virtual network configuration into a variable. ##
$net = @{
Name = 'vnet-1'
ResourceGroupName = 'test-rg'
}
$vnet = Get-AzVirtualNetwork @net
## Set the policy as disabled on the virtual network. ##
($vnet | Select -ExpandProperty subnets | Where-Object {$_.Name -eq $subnet}).privateLinkServiceNetworkPolicies = "Disabled"
## Save the configuration changes to the virtual network. ##
$vnet | Set-AzVirtualNetwork
Create a private link service
In this section, create a private link service that uses the Standard Azure Load Balancer created in the previous step.
Create the private link service IP configuration with New-AzPrivateLinkServiceIpConfig.
Create the private link service with New-AzPrivateLinkService.
## Place the virtual network into a variable. ##
$vnet = Get-AzVirtualNetwork -Name 'vnet-1' -ResourceGroupName 'test-rg'
## Create the IP configuration for the private link service. ##
$ipsettings = @{
Name = 'ipconfig-1'
PrivateIpAddress = '10.0.0.5'
Subnet = $vnet.subnets[0]
}
$ipconfig = New-AzPrivateLinkServiceIpConfig @ipsettings
## Place the load balancer frontend configuration into a variable. ##
$par = @{
Name = 'load-balancer'
ResourceGroupName = 'test-rg'
}
$fe = Get-AzLoadBalancer @par | Get-AzLoadBalancerFrontendIpConfig
## Create the private link service for the load balancer. ##
$privlinksettings = @{
Name = 'private-link-service'
ResourceGroupName = 'test-rg'
Location = 'chinaeast2'
LoadBalancerFrontendIpConfiguration = $fe
IpConfiguration = $ipconfig
}
New-AzPrivateLinkService @privlinksettings
Your private link service is created and can receive traffic. If you want to see traffic flows, configure your application behind your standard load balancer.
Create private endpoint
In this section, you map the private link service to a private endpoint. A virtual network contains the private endpoint for the private link service. This virtual network contains the resources that access your private link service.
Create private endpoint virtual network
- Create a virtual network with New-AzVirtualNetwork.
## Create backend subnet config ##
$subnet = @{
Name = 'subnet-pe'
AddressPrefix = '10.1.0.0/24'
}
$subnetConfig = New-AzVirtualNetworkSubnetConfig @subnet
## Create the virtual network ##
$net = @{
Name = 'vnet-pe'
ResourceGroupName = 'test-rg'
Location = 'chinaeast2'
AddressPrefix = '10.1.0.0/16'
Subnet = $subnetConfig
}
$vnetpe = New-AzVirtualNetwork @net
Create endpoint and connection
Use Get-AzPrivateLinkService to place the configuration of the private link service you created early into a variable for later use.
Use New-AzPrivateLinkServiceConnection to create the connection configuration.
Use New-AzPrivateEndpoint to create the endpoint.
## Place the private link service configuration into variable. ##
$par1 = @{
Name = 'private-link-service'
ResourceGroupName = 'test-rg'
}
$pls = Get-AzPrivateLinkService @par1
## Create the private link configuration and place in variable. ##
$par2 = @{
Name = 'connection-1'
PrivateLinkServiceId = $pls.Id
}
$plsConnection = New-AzPrivateLinkServiceConnection @par2
## Place the virtual network into a variable. ##
$par3 = @{
Name = 'vnet-pe'
ResourceGroupName = 'test-rg'
}
$vnetpe = Get-AzVirtualNetwork @par3
## Create private endpoint ##
$par4 = @{
Name = 'private-endpoint'
ResourceGroupName = 'test-rg'
Location = 'chinaeast2'
Subnet = $vnetpe.subnets[0]
PrivateLinkServiceConnection = $plsConnection
}
New-AzPrivateEndpoint @par4 -ByManualRequest
Approve the private endpoint connection
In this section, you approve the connection you created in the previous steps.
- Use Approve-AzPrivateEndpointConnection to approve the connection.
## Place the private link service configuration into variable. ##
$par1 = @{
Name = 'private-link-service'
ResourceGroupName = 'test-rg'
}
$pls = Get-AzPrivateLinkService @par1
$par2 = @{
Name = $pls.PrivateEndpointConnections[0].Name
ServiceName = 'private-link-service'
ResourceGroupName = 'test-rg'
Description = 'Approved'
PrivateLinkResourceType = 'Microsoft.Network/privateLinkServices'
}
Approve-AzPrivateEndpointConnection @par2
IP address of private endpoint
In this section, you find the IP address of the private endpoint that corresponds with the load balancer and private link service.
- Use Get-AzPrivateEndpoint to retrieve the IP address.
## Get private endpoint and the IP address and place in a variable for display. ##
$par1 = @{
Name = 'private-endpoint'
ResourceGroupName = 'test-rg'
ExpandResource = 'networkinterfaces'
}
$pe = Get-AzPrivateEndpoint @par1
## Display the IP address by expanding the variable. ##
$pe.NetworkInterfaces[0].IpConfigurations[0].PrivateIpAddress
❯ $pe.NetworkInterfaces[0].IpConfigurations[0].PrivateIpAddress
10.1.0.4
Clean up resources
When no longer needed, you can use the Remove-AzResourceGroup command to remove the resource group, load balancer, and the remaining resources.
Remove-AzResourceGroup -Name 'test-rg'
Next steps
In this quickstart, you:
Created a virtual network and internal Azure Load Balancer.
Created a private link service
To learn more about Azure Private endpoint, continue to: