Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Attention: All Microsoft Sentinel features will be officially retired in Azure in China regions on August 18, 2026 per the announcement posted by 21Vianet.
This article describes how to define an access restriction policy for Microsoft Sentinel Standard-plan playbooks, so that they can support private endpoints.
Define an access restriction policy to ensure that only Microsoft Sentinel has access to the Standard logic app containing your playbook workflows.
For more information, see:
- Secure traffic between Standard logic apps and Azure virtual networks using private endpoints
- Supported logic app types
Important
The new version of access restriction policies is currently in PREVIEW. See the Supplemental Terms of Use for Azure Previews for additional legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
Define an access restriction policy
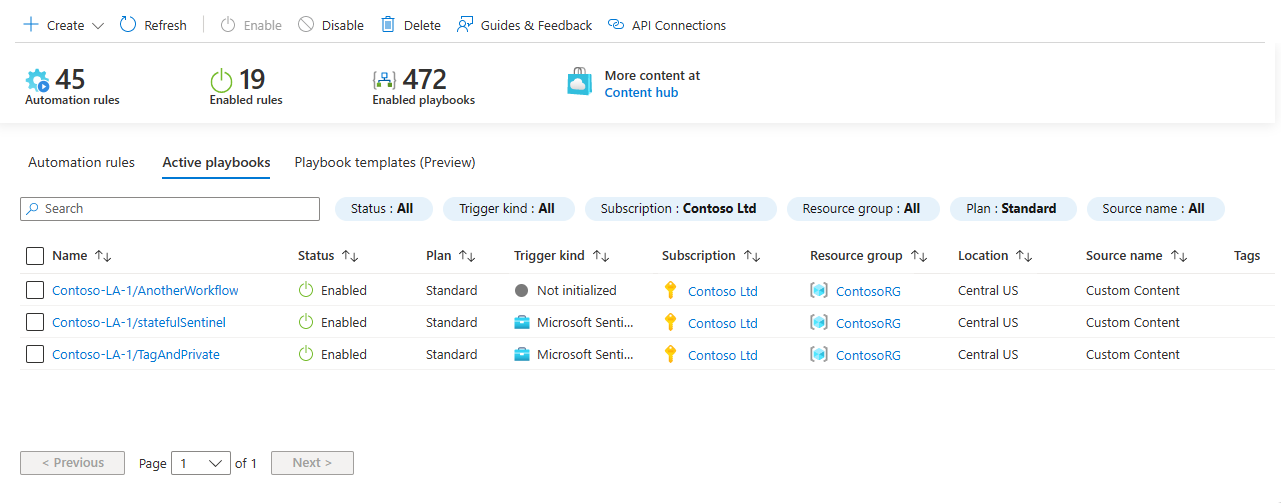
In the Azure portal, select the Configuration > Automation page.
On the Automation page, select the Active playbooks tab.
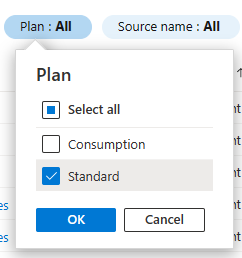
Filter the list for Standard-plan apps. Select the Plan filter and clear the Consumption checkbox, and then select OK. For example:
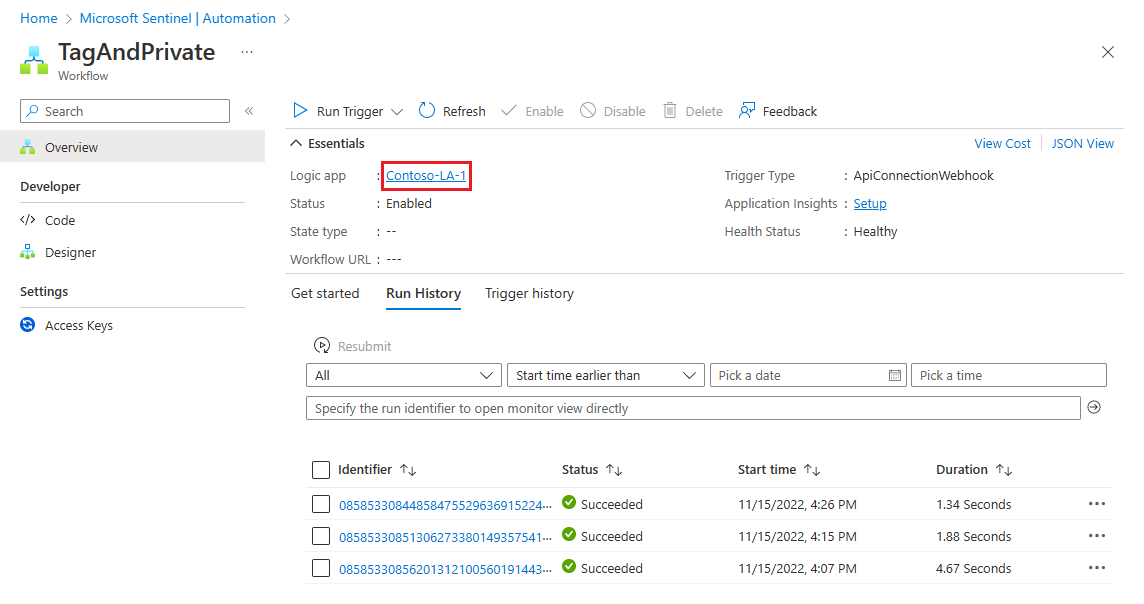
Select a playbook to which you want to restrict access. For example:
Select the logic app link on the playbook screen. For example:
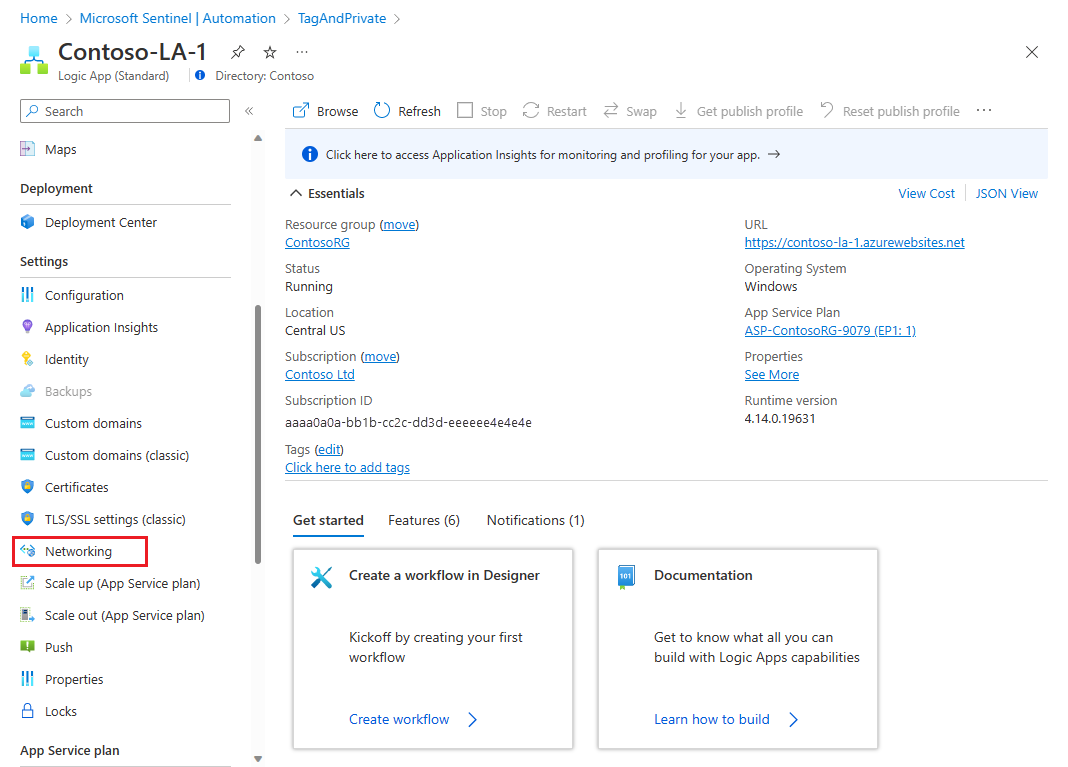
From the navigation menu of your logic app, under Settings, select Networking. For example:
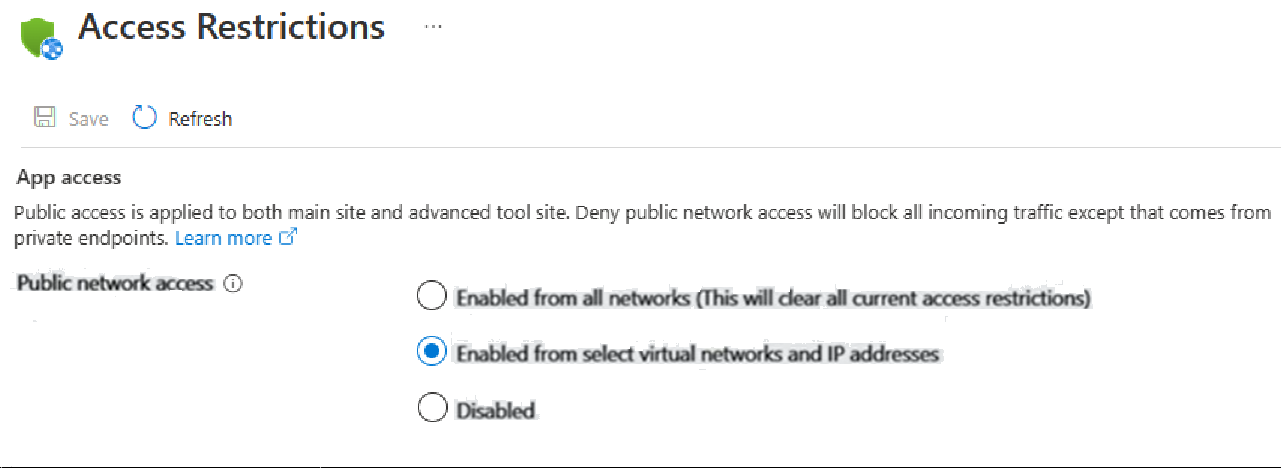
In the Inbound traffic configuration area, select Public network access.
In the Access Restrictions page, select the Enabled from select virtual networks and IP addresses checkbox.
Under Site access and rules, select + Add. The Add rule panel opens on the side. For example:
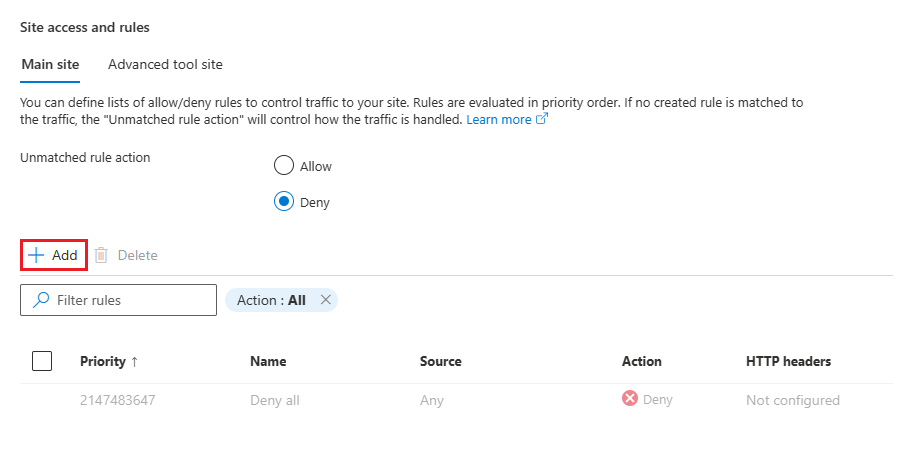
In the Add rule pane, enter the following details.
The name and optional description should reflect that this rule allows only Microsoft Sentinel to access the logic app. Leave the fields not mentioned below as they are.
Field Enter or select Name Enter SentinelAccessor another name of your choosing.Action Allow Priority Enter 1Description Optional. Add a description of your choosing. Type Select Service Tag. Service Tag
(will appear only after you
select Service Tag above.)Search for and select AzureSentinel. Select Add rule.
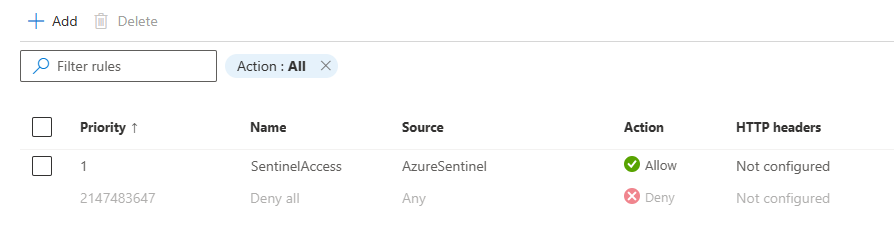
Sample policy
After following the procedure in this article, your policy should look as follows:
Related content
For more information, see: