Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Attention: All Microsoft Sentinel features will be officially retired in Azure in China regions on August 18, 2026 per the announcement posted by 21Vianet.
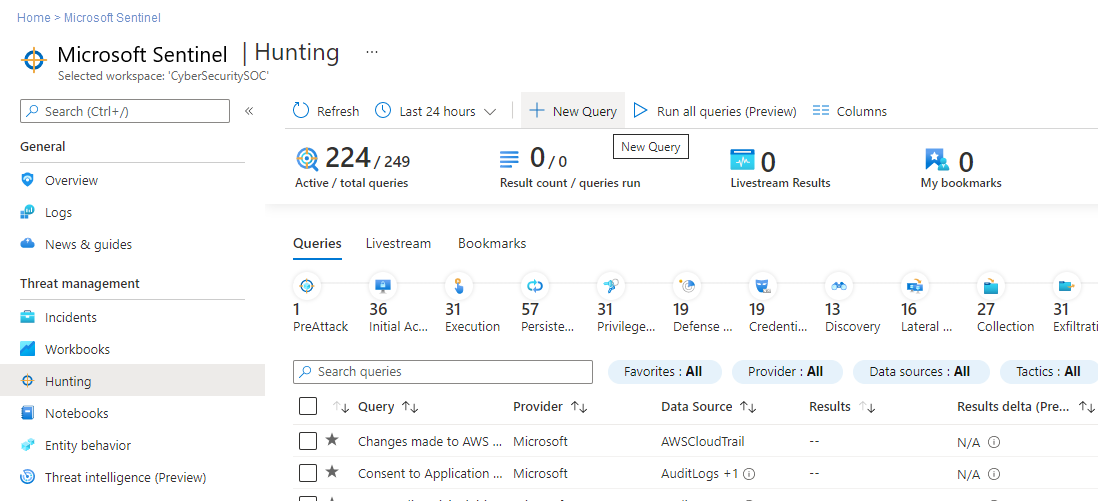
Hunt for security threats across your organization's data sources with custom hunting queries. Microsoft Sentinel provides built-in hunting queries to help you find issues in the data you have on your network. But you can create your own custom queries. For more information about hunting queries, see Threat hunting in Microsoft Sentinel.
Create a new query
In Microsoft Sentinel, create a custom hunting query from the Hunting > Queries tab.
Go to the Azure portal, under Threat management select Hunting.
Select the Queries tab.
From the command bar, select New query.
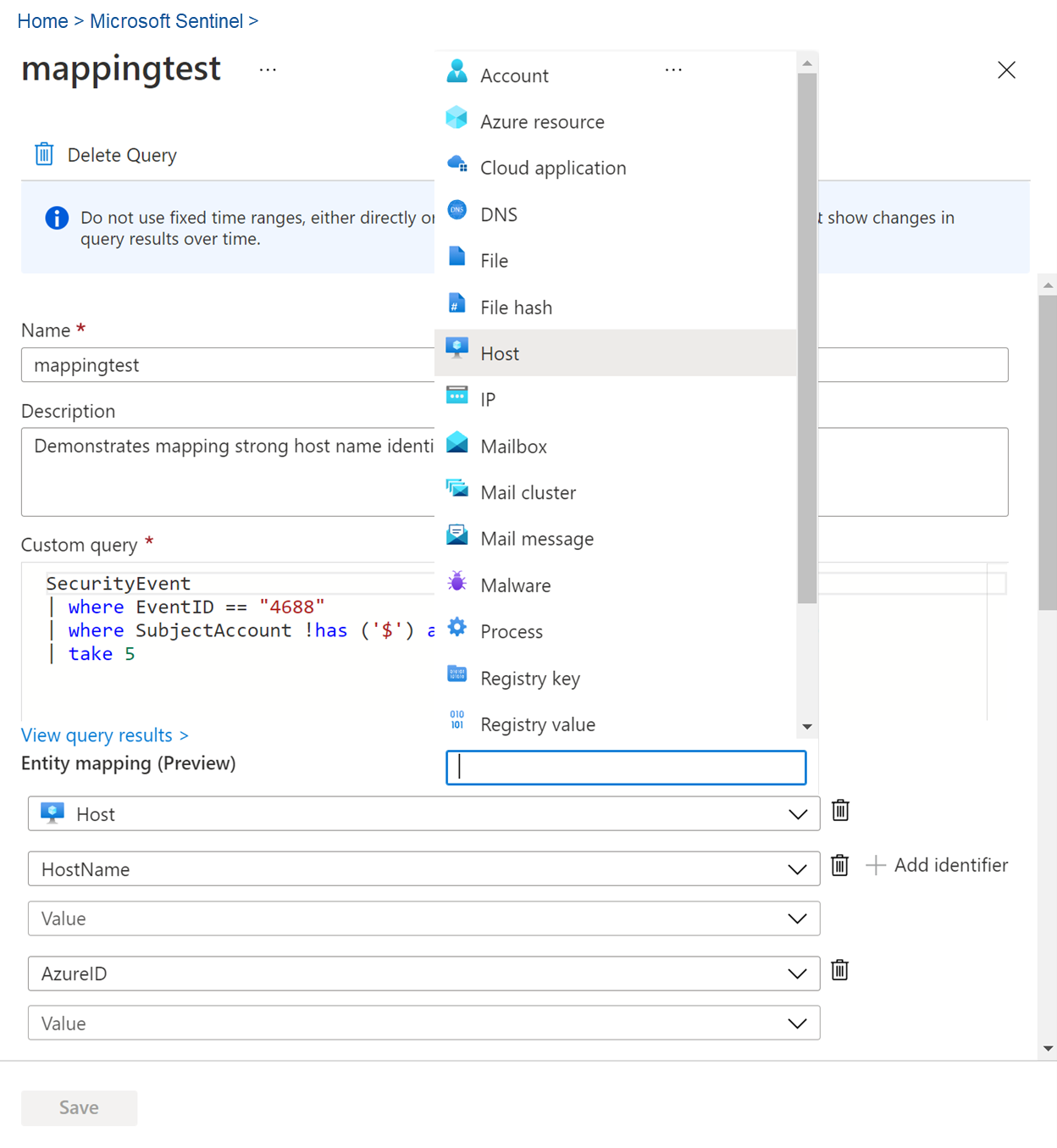
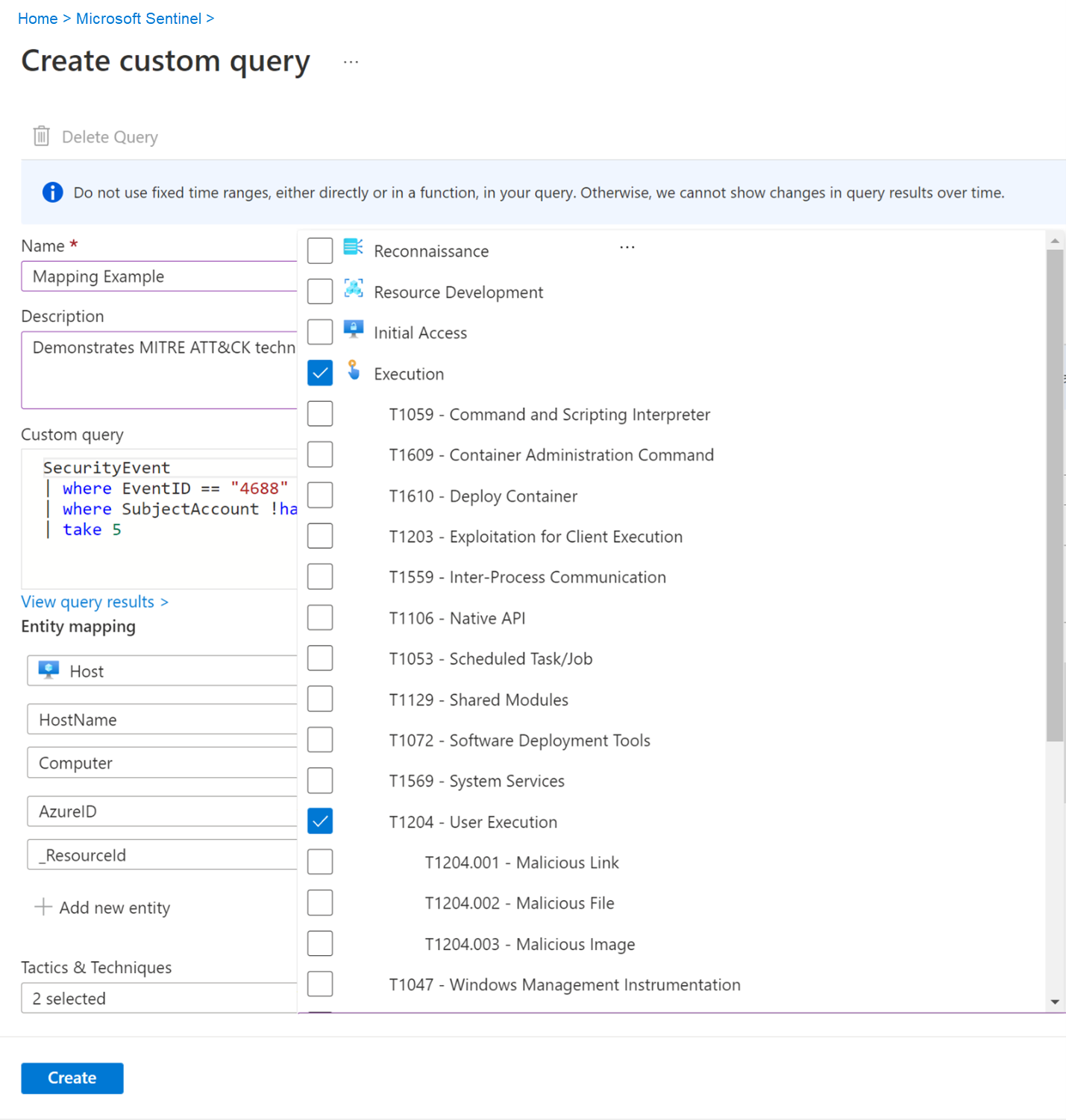
Fill in all the blank fields.
When your finished defining your query, select Create.
Clone an existing query
Clone a custom or built-in query and edit it as needed.
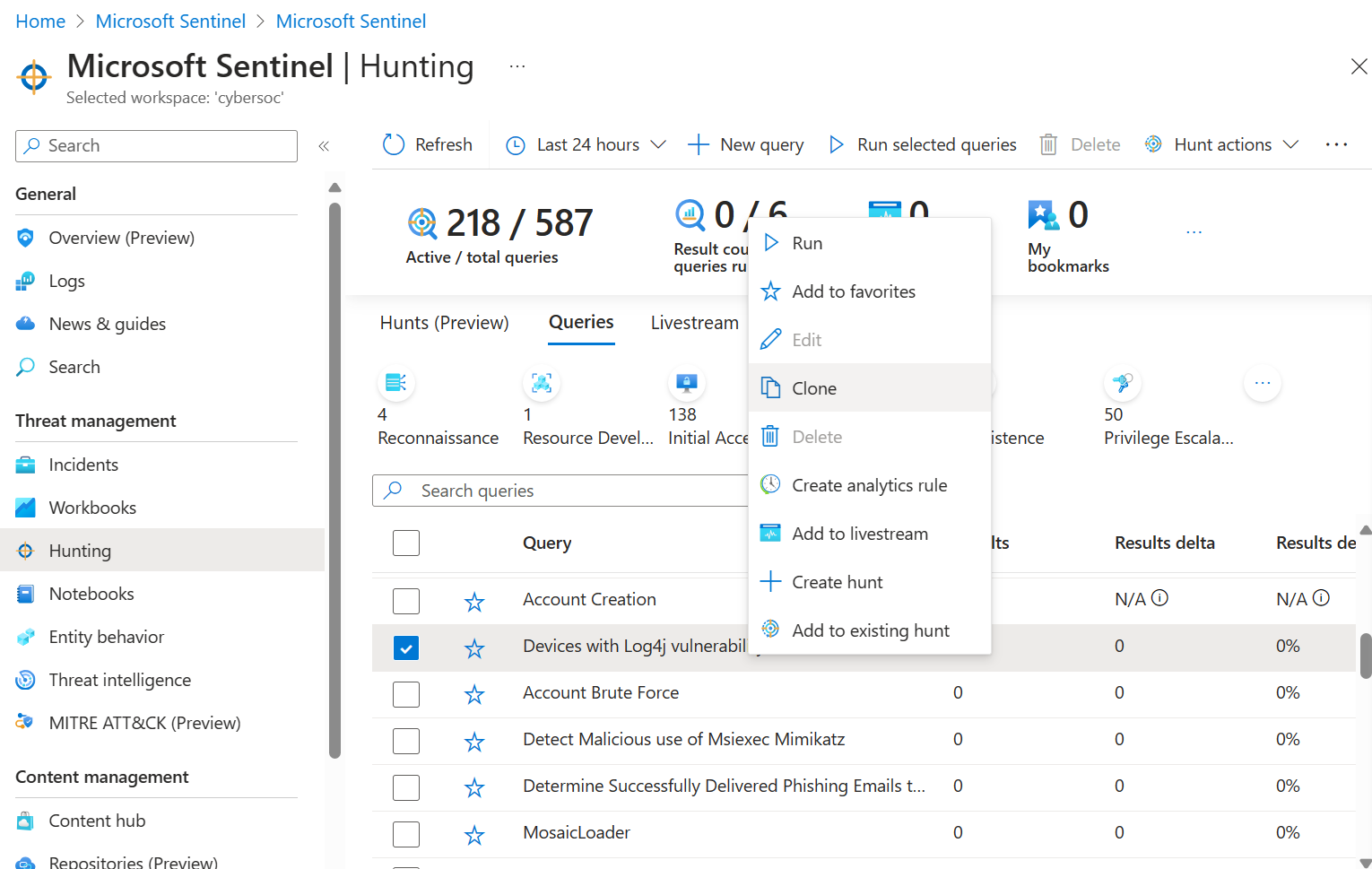
From the Hunting > Queries tab, select the hunting query you want to clone.
Select the ellipsis (...) in the line of the query you want to modify, and select Clone.
Edit the query and other fields as appropriate.
Select Create.
Edit an existing custom query
Only queries that from a custom content source can be edited. Other content sources have to be edited at that source.
From the Hunting > Queries tab, select the hunting query you want to change.
Select the ellipsis (...) in the line of the query you want to change, and select Edit.
Update the Query field with the updated query. You can also change the entity mapping and techniques.
When finished select Save.