Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Each node type in a Service Fabric managed cluster is backed by a virtual machine scale set. To allow managed identities to be used with a managed cluster node type, a property vmManagedIdentity has been added to node type definitions containing a list of identities that may be used, userAssignedIdentities. Functionality mirrors how managed identities can be used in non-managed clusters, such as using a managed identity with the Azure Key Vault virtual machine scale set extension.
For an example of a Service Fabric managed cluster deployment that makes use of managed identity on a node type, see these templates. The example has two templates:
Managed identity and role assignment: Template to create the managed identity and the role assignment to allow Service Fabric RP to assign the identity to the managed cluster's virtual machine scale set. This should be deployed only once before using the managed identity on the node type resource.
Managed cluster and node type: Template for the service fabric managed cluster and node type resources using the managed identity created before.
Note
Only user-assigned identities are currently supported for this feature.
Note
See Configure and use applications with managed identity on a Service Fabric managed cluster for application configuration.
Prerequisites
Before you begin:
- If you don't have an Azure subscription, create a trial subscription account before you begin.
- If you plan to use PowerShell, install the Azure CLI to run CLI reference commands.
1. Create identity and role Assignment
Create a user-assigned managed identity
A user-assigned managed identity can be defined in the resources section of an Azure Resource Manager (ARM) template for creation upon deployment:
{
"type": "Microsoft.ManagedIdentity/userAssignedIdentities",
"name": "[parameters('userAssignedIdentityName')]",
"apiVersion": "2023-01-31",
"location": "[resourceGroup().location]"
}
or created via PowerShell:
New-AzResourceGroup -Name <managedIdentityRGName> -Location <location>
New-AzUserAssignedIdentity -ResourceGroupName <managedIdentityRGName> -Name <userAssignedIdentityName>
Add a role assignment with Service Fabric Resource Provider
Add a role assignment to the managed identity with the Service Fabric Resource Provider application. This assignment allows Service Fabric Resource Provider to assign the identity, created on the previous step, to the managed cluster's virtual machine scale set. This is a one time action
Get service principal for Service Fabric Resource Provider application:
Connect-AzAccount -Environment AzureChinaCloud
Select-AzSubscription -SubscriptionId <SubId>
Get-AzADServicePrincipal -DisplayName "Azure Service Fabric Resource Provider"
Note
Make sure you are in the correct subscription, the principal ID will change if the subscription is in a different tenant.
ServicePrincipalNames : {00001111-aaaa-2222-bbbb-3333cccc4444}
ApplicationId : 00001111-aaaa-2222-bbbb-3333cccc4444
ObjectType : ServicePrincipal
DisplayName : Azure Service Fabric Resource Provider
Id : 00000000-0000-0000-0000-000000000000
Use the Id of the previous output as principalId and the role definition ID bellow as roleDefinitionId where applicable on the template or PowerShell command:
| Role definition name | Role definition ID |
|---|---|
| Managed Identity Operator | f1a07417-d97a-45cb-824c-7a7467783830 |
This role assignment can be defined in the resources section template using the Principal ID and role definition ID:
{
"type": "Microsoft.Authorization/roleAssignments",
"apiVersion": "2022-04-01",
"name": "[parameters('vmIdentityRoleNameGuid')]",
"scope": "[concat('Microsoft.ManagedIdentity/userAssignedIdentities', '/', parameters('userAssignedIdentityName'))]",
"dependsOn": [
"[concat('Microsoft.ManagedIdentity/userAssignedIdentities/', parameters('userAssignedIdentityName'))]"
],
"properties": {
"roleDefinitionId": "[resourceId('Microsoft.Authorization/roleDefinitions', 'f1a07417-d97a-45cb-824c-7a7467783830')]",
"principalId": "<Service Fabric Resource Provider ID>"
}
}
Note
vmIdentityRoleNameGuid should be a valid GUID. If you deploy again the same template including this role assignment, make sure the GUID is the same as the one originally used or remove this resource as it just needs to be created once.
or created via PowerShell using the principal ID and role definition name:
New-AzRoleAssignment -PrincipalId "<Service Fabric Resource Provider ID>" -RoleDefinitionName "Managed Identity Operator" -Scope "/subscriptions/<subscriptionId>/resourceGroups/<resourceGroupName>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<userAssignedIdentityName>"
Deploy managed identity and role assignment.
Run the New-AzResourceGroupDeployment cmdlet to create the managed identity and add the role assignment:
New-AzResourceGroupDeployment -ResourceGroupName <managedIdentityRGName> -TemplateFile ".\MangedIdentityAndSfrpRoleAssignment.json" -TemplateParameterFile ".\MangedIdentityAndSfrpRoleAssignment.Parameters.json" -Verbose
2. Assign identity to the node type resource
Add managed identity properties to node type definition
Finally, add the vmManagedIdentity and userAssignedIdentities properties to the managed cluster's node type definition with the full resource ID of the identity created on the first step. Be sure to use 2021-05-01 or later for the apiVersion.
{
"type": "Microsoft.ServiceFabric/managedClusters/nodeTypes",
"apiVersion": "2022-01-01",
"properties": {
"isPrimary": true,
"vmInstanceCount": 5,
"dataDiskSizeGB": 100,
"vmSize": "Standard_D2_v2",
"vmImagePublisher": "MicrosoftWindowsServer",
"vmImageOffer": "WindowsServer",
"vmImageSku": "2019-Datacenter",
"vmImageVersion": "latest",
"vmManagedIdentity": {
"userAssignedIdentities": [
"[parameters('userAssignedIdentityResourceId')]"
]
}
}
}
Deploy the node type resource assigning the identity
Run the New-AzResourceGroupDeployment cmdlet to deploy the service fabric managed clusters template that assigns the managed identity to the node type resource.
New-AzResourceGroupDeployment -ResourceGroupName <sfmcRGName> -TemplateFile ".\SfmcVmMangedIdentity.json" -TemplateParameterFile ".\SfmcVmMangedIdentity.Parameters.json" -Verbose
After deployment, the created managed identity has been added to the designated node type's virtual machine scale set and can be used as expected, just like in any non-managed cluster.
Troubleshooting
Failure to properly add a role assignment will be met with the following error on deployment:
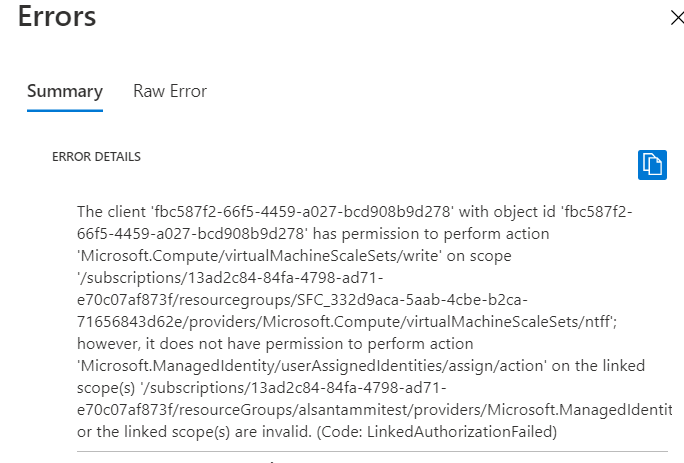
In this case, make sure the role assignment is created successfully with Role "Managed Identity Operator". The role assignment can be found on the Azure portal under access control of the managed identity resource as show below.