Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Tip
This article is shared for services and products that use the Remote Desktop Protocol (RDP) to provide remote access to Windows desktops and apps.
Select a product using the buttons at the top of this article to show the relevant content.
You can configure the redirection behavior of location information from a local device to a remote session over the Remote Desktop Protocol (RDP). A user's location can be important for some applications, such as mapping and regional services in browsers. Without redirecting location information, the location of a remote session is near the datacenter the user connects to for the remote session.
For Azure Virtual Desktop, location redirection must be configured at the following points. If any of these components aren't configured correctly, location redirection won't work as expected. You can use Microsoft Intune or Group Policy to configure your session hosts and the local device.
- Session host
- Host pool RDP property
- Local device
For Windows 365, location services must be configured on the Cloud PC and the local device. If either of these components aren't configured correctly, location redirection won't work as expected. You can use Microsoft Intune or Group Policy to configure your Cloud PC and the local device. Windows 365 allows location redirection.
For Microsoft Dev Box, location services must be configured on the dev box and the local device. If either of these components aren't configured correctly, location redirection won't work as expected. You can use Microsoft Intune or Group Policy to configure your dev box and the local device. Microsoft Dev Box allows location redirection.
Important
Redirected longitude and latitude information is accurate to 1 meter. Horizontal accuracy is currently set at 10 kilometers, so applications that use the horizontal accuracy value might report that a precise location can't be determined.
This article provides information about the supported redirection methods and how to configure the redirection behavior for location information. To learn more about how redirection works, see Redirection over the Remote Desktop Protocol.
Prerequisites
Before you can configure location redirection, you need:
An existing host pool with session hosts running Windows 11 Enterprise or Windows 11 Enterprise multi-session version 22H2 or later.
A Microsoft Entra ID account that is assigned the Desktop Virtualization Host Pool Contributor built-in role-based access control (RBAC) roles on the host pool as a minimum.
- An existing Cloud PC running Windows 11 Enterprise version 22H2 or later.
- An existing dev box running Windows 11 Enterprise, version 22H2 or later.
To configure Microsoft Intune, you need:
- Microsoft Entra ID account that is assigned the Policy and Profile manager built-in RBAC role.
- A group containing the devices you want to configure.
To configure Group Policy, you need:
- A domain account that has permission to create or edit Group Policy objects.
- A security group or organizational unit (OU) containing the devices you want to configure.
You need to connect to a remote session from a supported app and platform. To view redirection support in Windows App and the Remote Desktop app, see Compare Windows App features across platforms and devices and Compare Remote Desktop app features across platforms and devices.
Session host configuration
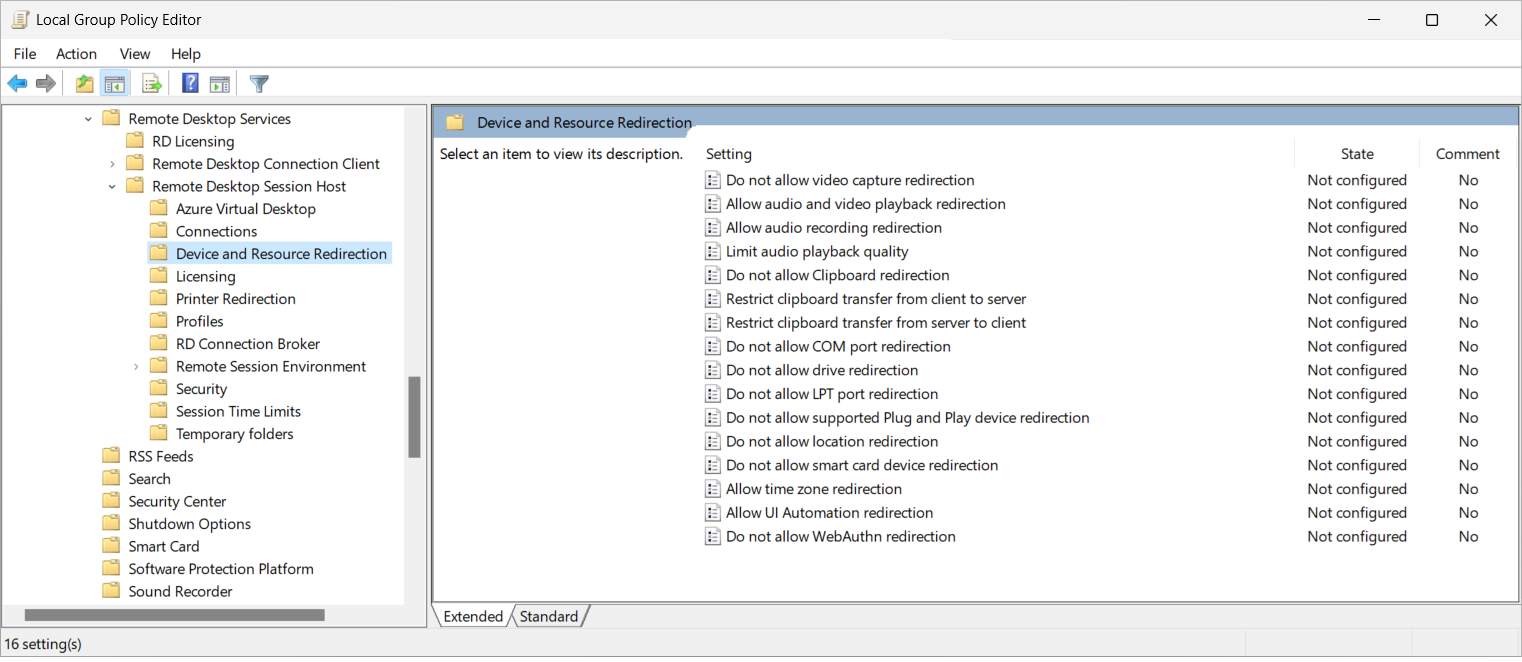
To configure a session host for location redirection, you need to enable and configure location services. You can do this using Microsoft Intune or Group Policy.
Important
If you use a multi-session edition of Windows, when you enable location services on a session host, it's enabled for all users. You can specify which apps can access location information on a per-user basis based on your requirements.
Cloud PC configuration
To configure a Cloud PC for location redirection, you need to enable and configure location services. You can do this using Microsoft Intune or Group Policy.
Dev box configuration
To configure a dev box for location redirection, you need to enable and configure location services. You can do this using Microsoft Intune or Group Policy.
Select the relevant tab for your scenario.
To enable location services using Microsoft Intune:
Sign in to the Microsoft Intune admin center.
Create or edit a configuration profile for Windows 10 and later devices, with the Settings catalog profile type.
In the settings picker, select System. Check the box for Allow Location, then close the settings picker.
Expand the System category, then from the drop-down menu select Force Location On. All Location Privacy settings are toggled on and grayed out. Users cannot change the settings and all consent permissions will be automatically suppressed.
Select Next.
Optional: On the Scope tags tab, select a scope tag to filter the profile. For more information about scope tags, see Use role-based access control (RBAC) and scope tags for distributed IT.
On the Assignments tab, select the group containing the computers providing a remote session you want to configure, then select Next.
On the Review + create tab, review the settings, then select Create.
Once the policy applies to the computers providing a remote session, restart them for the settings to take effect.
You need to enable the location setting Allow location override for the location to be updated in the remote session, which you can do by configuring a registry value and is set per user. Users can still change this setting in Windows location settings.
You can do this by creating a PowerShell script and using it as a custom script remediation in Intune. When you create the custom script remediation, you must set Run this script using the logged-on credentials to Yes.
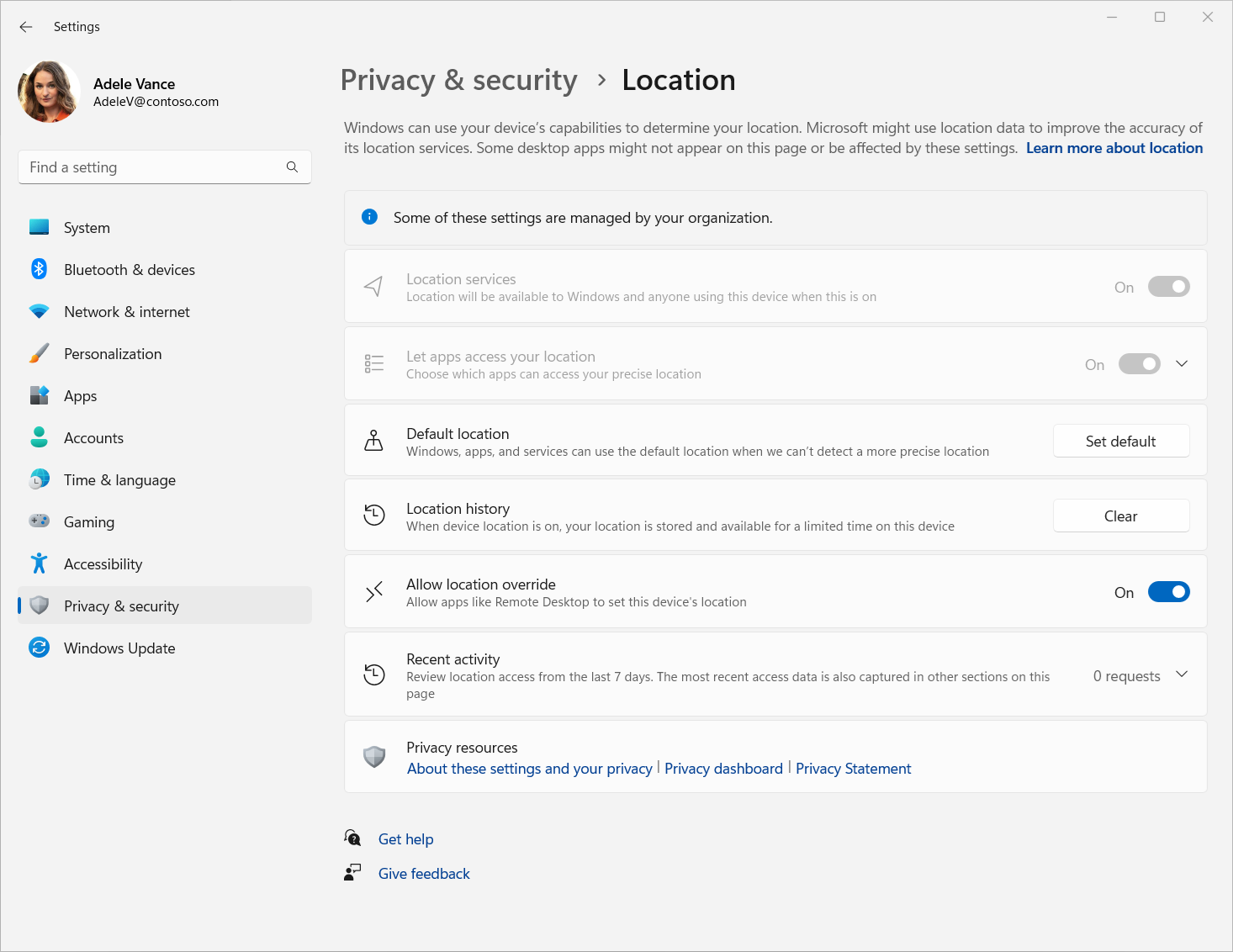
try { New-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\CPSS\Store\UserLocationOverridePrivacySetting" -Name Value -PropertyType DWORD -Value 1 -Force exit 0 } catch{ $errMsg = $_.Exception.Message Write-Error $errMsg exit 1 }Once you have made the changes, location services in the Windows Settings app should look similar to the following image:
Host pool configuration
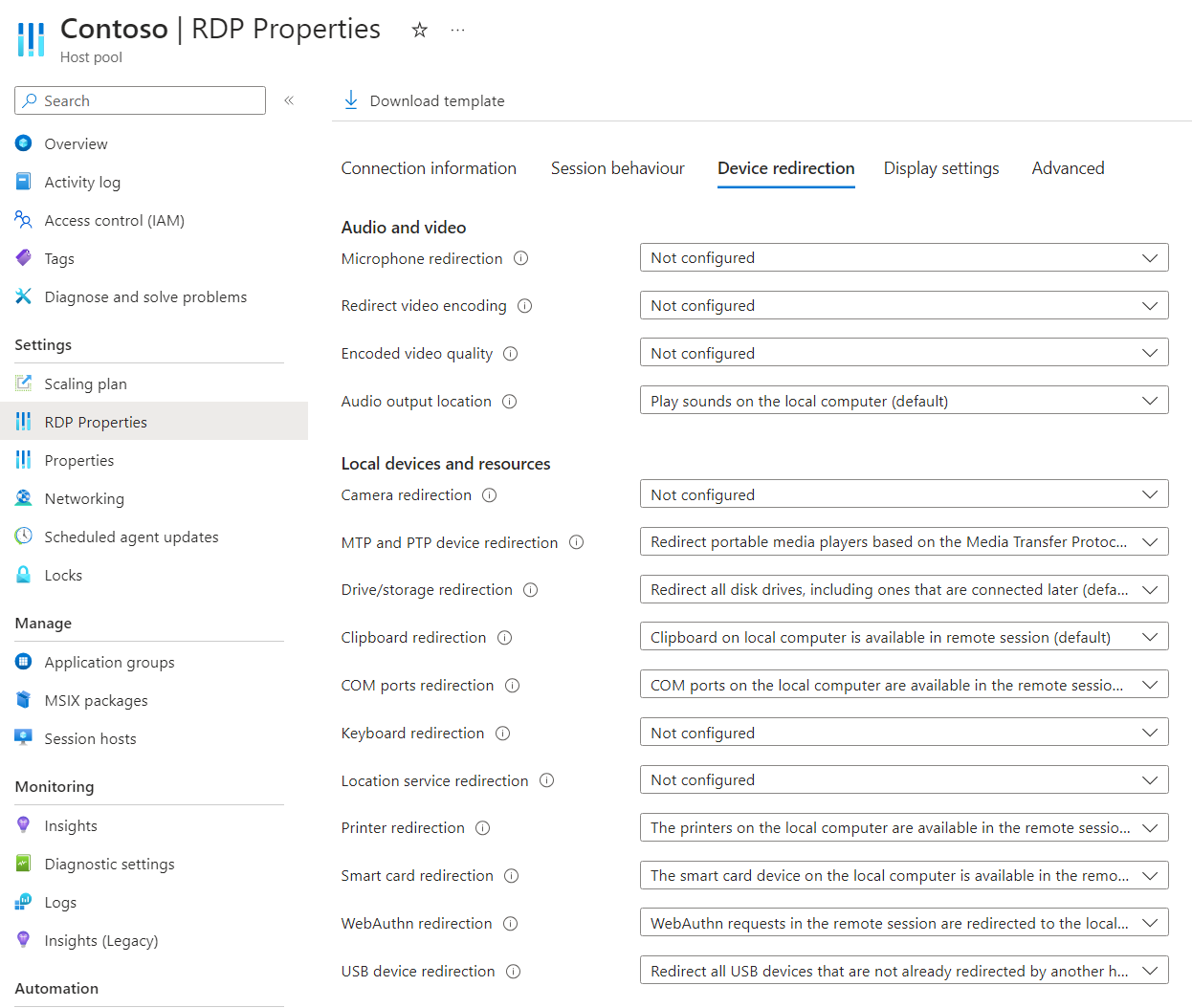
The Azure Virtual Desktop host pool setting Location service redirection controls whether to redirect location information from the local device to the remote session. The corresponding RDP property is redirectlocation:i:<value>. For more information, see Supported RDP properties.
To configure location redirection using host pool RDP properties:
Sign in to the Azure portal.
In the search bar, type Azure Virtual Desktop and select the matching service entry.
Select Host pools, then select the host pool you want to configure.
Select RDP Properties, then select Device redirection.
For Location service redirection, select the drop-down list, then select Enable location sharing from the local device and redirection to apps in the remote session.
Select Save.
Local device configuration
You need to use a supported app and platform connect to a remote session and enable location services on a local device. How you achieve this depends on your requirements, the platform you're using, and whether the device is managed or unmanaged.
To view redirection support in Windows App and the Remote Desktop app, see Compare Windows App features across platforms and devices and Compare Remote Desktop app features across platforms and devices.
On Windows, you can enable location services in the Windows Settings app. For more information, see Windows location service and privacy. The steps in this article to enable location services in a remote session using Intune and Group Policy can also be applied to local Windows devices.
To enable location services on other platforms, refer to the relevant manufacturer's documentation.
Test location redirection
Once you configure your session hosts, host pool RDP property, and local devices, you can test location redirection.
Once you configure your Cloud PCs and local devices, you can test location redirection.
Once you configure your dev boxes and local devices, you can test location redirection.
To test location redirection:
Connect to a remote session using Window App or the Remote Desktop app on a platform that supports location redirection. For more information, see Compare Windows App features across platforms and devices and Compare Remote Desktop app features across platforms and devices.
Check the user's location information is available in the remote session. Here are some ways to check:
Open a web browser and go to a website that uses location information, such as Bing Maps. In Bing Maps, select the icon for the button Locate me. The website should show the user's location as the location of the local device.
Open a PowerShell prompt in the remote session and run the following commands to get the latitude and longitude values. You can also run these commands on a local Windows device to check they are consistent.
Add-Type -AssemblyName System.Device $GeoCoordinateWatcher = New-Object System.Device.Location.GeoCoordinateWatcher $GeoCoordinateWatcher.Start() Start-Sleep -Milliseconds 500 If ($GeoCoordinateWatcher.Permission -eq "Granted") { While ($GeoCoordinateWatcher.Status -ne "Ready") { Start-Sleep -Milliseconds 500 } $GeoCoordinateWatcher.Position.Location | FL Latitude, Longitude } else { Write-Output "Desktop apps aren't allowed to access your location. Please enable access." }The output is similar to the following example:
Latitude : 47.64354 Longitude : -122.13082