重要
自 2025 年 5 月 1 日起,Azure AD B2C 将不再可供新客户购买。 在我们的常见问题解答中了解详细信息。
从另一个标识提供者迁移到 Azure Active Directory B2C(Azure AD B2C)可能还需要迁移现有的用户帐户。 此处讨论了两种迁移方法: 迁移前 和 无缝迁移。 无论采用哪种方法,都需要编写使用 Microsoft 图形 API 在 Azure AD B2C 中创建用户帐户的应用程序或脚本。
注释
在开始迁移之前,请确保 Azure AD B2C 租户的未使用配额可以容纳你期望迁移的所有用户。 了解如何获取租户使用情况。 如果需要提高租户的配额限制,请联系 Microsoft支持部门。
迁移前
在预迁移流中,迁移应用程序针对每个用户帐户执行以下步骤:
- 从原身份提供者读取用户帐户,包括其当前认证信息(用户名和密码)。
- 使用当前凭据在 Azure AD B2C 目录中创建相应的帐户。
在以下两种情况下之一使用预迁移流:
- 你有权访问用户的纯文本凭据(其用户名和密码)。
- 凭据已加密,但可以解密凭据。
有关以编程方式创建用户帐户的信息,请参阅 使用 Microsoft Graph 管理 Azure AD B2C 用户帐户。
无缝迁移
如果旧标识提供者中的纯文本密码不可访问,请使用无缝迁移流。 例如,何时:
- 密码以单向加密格式存储,例如使用哈希函数。
- 密码由旧标识提供者以无法访问的方式存储。 例如,当标识提供者通过调用 Web 服务来验证凭据时。
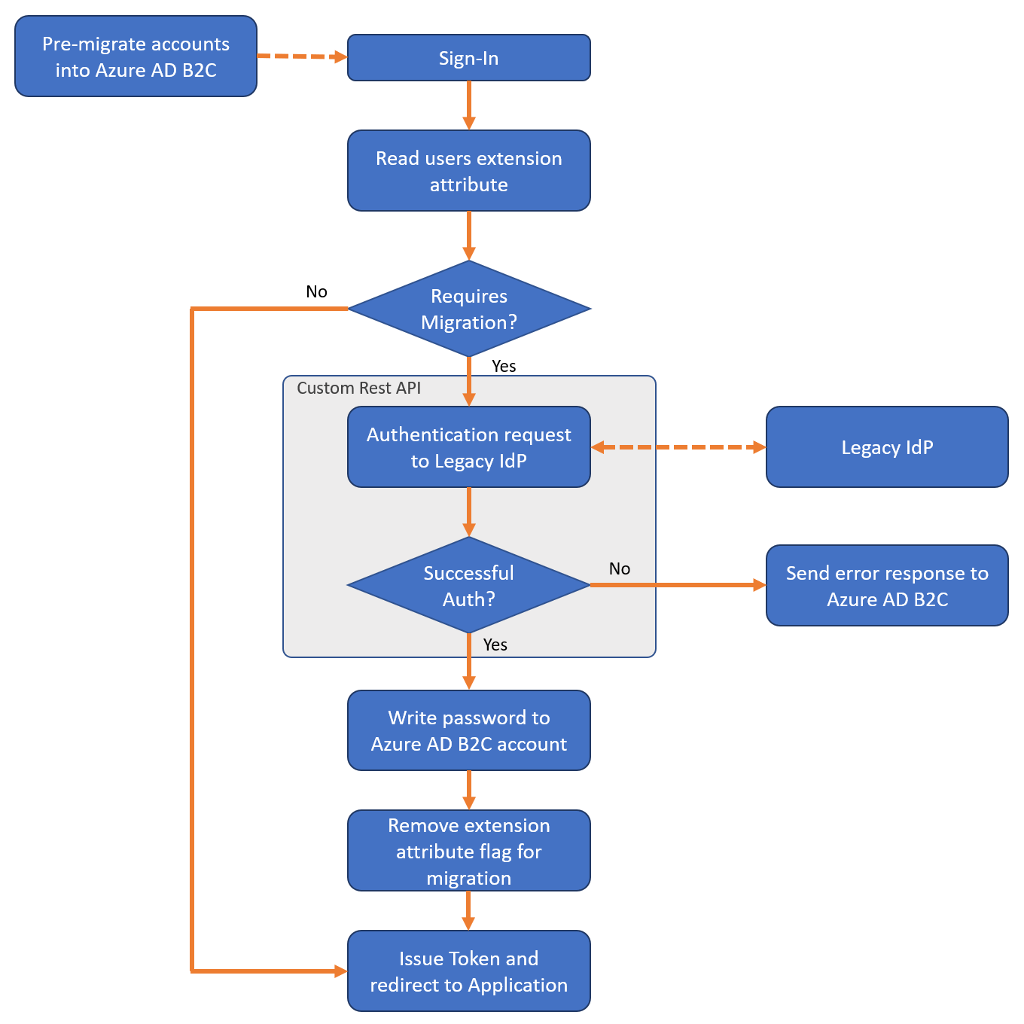
无缝迁移流仍需要预先迁移用户帐户,但随后使用 自定义策略 查询 REST API(你创建该 API)以在首次登录时设置每个用户的密码。
无缝迁移流由两个阶段组成: 迁移前 和 设置凭据。
阶段 1:迁移前
- 迁移应用程序从旧标识提供者读取用户帐户。
- 迁移应用程序会在 Azure AD B2C 目录中创建相应的用户帐户,但 设置生成的随机密码 。
阶段 2:设置凭据
在完成帐户的预迁移后,您的自定义策略和 REST API 在用户登录时执行以下操作:
- 读取与输入的电子邮件地址对应的 Azure AD B2C 用户帐户。
- 通过评估布尔扩展属性检查帐户是否被标记用于迁移。
- 如果扩展属性返回
True,请调用 REST API 以针对旧标识提供者验证密码。- 如果 REST API 确定密码不正确,请向用户返回友好错误。
- 如果 REST API 确定密码正确,请将密码写入 Azure AD B2C 帐户,并将布尔扩展属性更改为
False。
- 如果布尔扩展属性返回
False,请照常继续登录过程。
- 如果扩展属性返回
若要查看自定义策略和 REST API 的示例,请参阅 GitHub 上的 无缝用户迁移示例 。
安全
无缝迁移方法使用自己的自定义 REST API 针对旧标识提供者验证用户的凭据。
必须保护 REST API 免受暴力攻击。 攻击者可以提交多个密码,希望最终猜出用户的凭据。 为了帮助击败此类攻击,请在登录尝试次数通过特定阈值时停止向 REST API 提供服务请求。 此外,保护 Azure AD B2C 与 REST API 之间的通信。
用户属性
并非所有旧标识提供者中的信息都应迁移到 Azure AD B2C 目录。 在迁移之前,确定要存储在 Azure AD B2C 中的相应用户属性集。
-
DO 存储在 Azure AD B2C 中:
- 用户名、密码、电子邮件地址、电话号码、成员身份号码/标识符。
- 隐私政策和最终用户许可协议的同意标识。
-
请勿 存储在 Azure AD B2C 中:
- 信用卡号、社会安全号码(SSN)、医疗记录或其他受政府或行业合规机构监管的数据等敏感数据。
- 营销或通信首选项、用户行为和见解。
目录清理
在开始迁移过程之前,请有机会清理目录。
- 确定要存储在 Azure AD B2C 中的用户属性集,并只迁移必要的部分。 如有必要,可以 创建自定义属性 来存储有关用户的更多数据。
- 如果要从具有多个身份验证源的环境迁移(例如,每个应用程序都有自己的用户目录),请迁移到 Azure AD B2C 中的统一帐户。
- 如果多个应用程序具有不同的用户名,则可以使用标识集合将所有用户名存储在 Azure AD B2C 用户帐户中。 关于密码,让用户选择一个密码,并在目录中设置它。 例如,使用无缝迁移,应仅将所选密码存储在 Azure AD B2C 帐户中。
- 删除未使用的用户帐户,或不迁移过时的帐户。
密码策略
如果要迁移的帐户的密码强度比 Azure AD B2C 强制实施的 强密码强度 弱,则可以禁用强密码要求。 有关详细信息,请参阅 密码策略属性。
后续步骤
azure-ad-b2c/user-migration GitHub 上的存储库包含无缝迁移自定义策略示例和 REST API 代码示例: