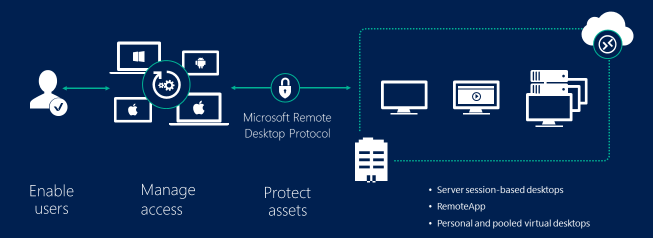
若要保护对 Microsoft Entra 域服务托管域中运行的虚拟机 (VM) 的远程访问,可以使用远程桌面服务 (RDS) 和网络策略服务器 (NPS)。 域服务在用户请求通过 RDS 环境进行访问时对用户进行身份验证。 为了提高安全性,你可以集成 Microsoft Entra 多重身份验证,以便在发生登录事件期间提供其他的身份验证提示。 Microsoft Entra 多重身份验证使用 NPS 的一个扩展来提供此功能。
重要
若要安全地连接到域服务托管域中的 VM,建议使用 Azure Bastion,这是在虚拟网络中预配的一项完全由平台托管的 PaaS 服务。 堡垒主机直接在 Azure 门户中通过 SSL 提供与 VM 的安全无缝远程桌面协议 (RDP) 连接。 通过堡垒主机进行连接时,VM 不需要公共 IP 地址,你无需使用网络安全组在 TCP 端口 3389 上公开对 RDP 的访问。
强烈建议你在支持 Azure Bastion 的所有区域中使用它。 在不可使用 Azure Bastion 的区域中,请按本文中详述的步骤操作,直到 Azure Bastion 可用。 向已加入允许所有传入 RDP 流量的域服务的 VM 分配公共 IP 地址时一定要谨慎。
有关详细信息,请参阅什么是 Azure Bastion?。
本文介绍如何在域服务中配置 RDS,并选择性地使用 Microsoft Entra 多重身份验证 NPS 扩展。
先决条件
若要完成本文,需准备好以下资源:
- 一个有效的 Azure 订阅。
- 如果你没有 Azure 订阅,请创建一个帐户。
- 与订阅关联的 Microsoft Entra 租户,可以与本地目录或仅限云的目录同步。
- 在 Microsoft Entra 租户中启用和配置的 Microsoft Entra 域服务托管域。
- 在你的 Microsoft Entra 域服务虚拟网络中创建的“工作负载”子网。
- 属于 Microsoft Entra 租户中“AAD DC 管理员”组的成员的用户帐户。
部署和配置远程桌面环境
若要开始,请至少创建两个运行 Windows Server 2016 或 Windows Server 2019 的 Azure VM。 为了实现远程桌面 (RD) 环境的冗余性和高可用性,你可以在以后添加主机并对其进行负载均衡。
建议的 RDS 部署包含以下两个 VM:
- RDGVM01 - 运行 RD 连接代理服务器、RD Web 访问服务器和 RD 网关服务器。
- RDSHVM01 - 运行 RD 会话主机服务器。
请确保将 VM 部署到域服务虚拟网络的“工作负载”子网中,然后将 VM 加入托管域。 有关详细信息,请参阅如何创建 Windows Server VM 并将其加入托管域。
RD 环境部署包含许多步骤。 可以使用现有的 RD 部署指南,不需要进行任何特定变更便可在托管域中使用:
- 使用属于“AD DC 管理员”组中的帐户(例如 contosoadmin)登录到为 RD 环境创建的 VM。
- 若要创建和配置 RDS,请使用现有的远程桌面环境部署指南。 根据需要将 RD 服务器组件分布到各个 Azure VM。
- 特定于域服务 - 配置 RD 许可时,请将其设置为“每设备”模式而不是“每用户”模式,如部署指南中所述。
- 如果要使用 Web 浏览器提供访问,请为用户设置远程桌面 Web 客户端。
将 RD 部署到托管域后,你可以像使用本地 AD DS 域一样管理和使用该服务。
部署和配置 NPS 以及 Microsoft Entra 多重身份验证 NPS 扩展
如果希望提高用户登录体验的安全性,可以选择将 RD 环境与 Microsoft Entra 多重身份验证集成。 使用此配置,用户会在登录过程中收到用于确认其身份的其他提示。
为了提供此功能,会在你的环境中随 Microsoft Entra 多重身份验证 NPS 扩展一起安装一个网络策略服务器 (NPS)。 此扩展与 Microsoft Entra ID 集成,用于请求并返回多重身份验证提示的状态。
用户必须[注册为使用 Microsoft Entra 多重身份验证][user-mfa-registration],这可能需要其他Microsoft Entra ID 许可证。 有关详细信息,请参阅“Microsoft Entra 计划与定价”。
若要将 Microsoft Entra 多重身份验证集成到远程桌面环境中,请创建 NPS 服务器并安装该扩展:
- 创建其他 Windows Server 2016 或 2019 VM(如 NPSVM01),它连接到域服务虚拟网络中的工作负载子网。 将 VM 加入托管域。
- 以属于 AAD DC 管理员组的帐户(如 contosoadmin)的身份登录到 NPS VM。
- 在“服务器管理器”中,选择“添加角色和功能”,然后安装“网络策略和访问服务”角色 。
- 将 RAS 和 IAS 服务器组的完全控制权限委托给AAD DC 管理员组。 NPS 或 Radius 服务器设置需要此步骤。
- 使用现有的操作方法文章 [安装和配置 Microsoft Entra 多重身份验证 NPS 扩展][nps-extension]。
在安装了 NPS 服务器和 Microsoft Entra 多重身份验证 NPS 扩展后,请完成下一部分,以将其配置为与 RD 环境配合使用。
集成远程桌面网关和 Microsoft Entra 多重身份验证
若要集成 Microsoft Entra 多重身份验证 NPS 扩展,请使用现有的指南文章来[集成你的远程桌面网关基础结构,使用网络策略服务器(NPS)扩展和 Microsoft Entra ID][azure-mfa-nps-integration]。
与托管域集成需要以下配置选项:
请勿 [在 Active Directory 中注册 NPS 服务器][register-nps-ad]。 此步骤在托管域中会失败。
在[配置网络策略的步骤 4][create-nps-policy]中,还选中“ 忽略用户帐户拨入属性”框。
如果为 NPS 服务器和 Microsoft Entra 多重身份验证 NPS 扩展使用 Windows Server 2019,请运行以下命令来更新安全通道,以便 NPS 服务器能够正确通信:
sc sidtype IAS unrestricted
现在,当用户登录时,系统会提示用户提供短信或 Microsoft Authenticator 应用中的提示等其他身份验证因素。
后续步骤
若要详细了解如何提高部署复原能力,请参阅远程桌面服务 - 高可用性。
若要详细了解如何保护用户登录,请参阅工作原理:Microsoft Entra 多重身份验证。