对于混合环境,可以配置一个 Microsoft Entra 租户,以使用 Microsoft Entra Connect 来与本地 Active Directory 域服务 (AD DS) 环境保持同步。 默认情况下,Microsoft Entra Connect 不会同步 Microsoft Entra 域服务所需的旧 NT LAN Manager (NTLM) 和 Kerberos 密码哈希。
若要将域服务与从本地 AD DS 环境同步的帐户配合使用,需要将 Microsoft Entra Connect 配置为同步 NTLM 和 Kerberos 身份验证所需的密码哈希。 配置 Microsoft Entra Connect 之后,本地帐户创建或密码更改事件也会将旧密码哈希同步到 Microsoft Entra ID。
如果使用仅限云的帐户且不使用本地 AD DS 环境,则无需执行这些步骤。
在本教程中,学习以下内容:
- 为何需要旧 NTLM 和 Kerberos 密码哈希
- 如何为 Microsoft Entra Connect 配置旧密码哈希同步
如果还没有 Azure 订阅,可以在开始前创建一个帐户。
先决条件
若要完成本教程,需要以下各资源:
- 一个有效的 Azure 订阅。
- 如果你没有 Azure 订阅,请创建一个帐户。
- 与订阅关联的 Microsoft Entra 租户,该租户已使用 Microsoft Entra Connect 同步到本地目录。
- 在 Microsoft Entra 租户中启用和配置的 Microsoft Entra 域服务托管域。
使用 Microsoft Entra Connect 进行密码哈希同步
使用 Microsoft Entra Connect 可将用户帐户和组等对象从本地 AD DS 环境同步到 Microsoft Entra 租户。 在此过程中,密码哈希同步允许帐户在本地 AD DS 环境和 Microsoft Entra ID 中使用相同的密码。
若要对托管域上的用户进行身份验证,域服务需要密码哈希,其格式适用于 NTLM 和 Kerberos 身份验证。 除非为租户启用了域服务,否则 Microsoft Entra ID 不会以 NTLM 或 Kerberos 身份验证所需的格式存储密码哈希。 出于安全考虑,Microsoft Entra ID 也不以明文形式存储任何密码凭据。 因此,Microsoft Entra ID 无法基于用户的现有凭据自动生成这些 NTLM 或 Kerberos 密码哈希。
可将 Microsoft Entra Connect 配置为同步域服务所需的 NTLM 或 Kerberos 密码哈希。 确保已完成为密码哈希同步启用 Microsoft Entra Connect 的步骤。 如果你有 Microsoft Entra Connect 的现有实例,请下载并更新到最新版本,以确保可以同步 NTLM 和 Kerberos 的旧密码哈希。 此功能不可用于早期的 Microsoft Entra Connect 版本或旧式 DirSync 工具。 需要 Microsoft Entra Connect 1.1.614.0 或更高版本。
重要
安装和配置的 Microsoft Entra Connect 应仅用于与本地 AD DS 环境同步。 不支持在域服务托管域中安装 Microsoft Entra Connect 以将对象往回同步到 Microsoft Entra ID。
启用密码哈希同步
安装 Microsoft Entra Connect 并将其配置为与 Microsoft Entra ID 同步后,接下来请配置 NTLM 和 Kerberos 的旧密码哈希同步。 可以使用一个 PowerShell 脚本来配置所需的设置,然后启动与 Microsoft Entra ID 的完全密码同步。 Microsoft Entra Connect 密码哈希同步过程完成后,用户可以通过域服务登录到使用旧 NTLM 或 Kerberos 密码哈希的应用程序。
在安装了 Microsoft Entra Connect 的计算机上,从“开始”菜单中,打开“Microsoft Entra Connect > 同步服务”。
选择“连接器”选项卡。此时会列出用于在本地 AD DS 环境与 Microsoft Entra 之间建立同步的连接信息。
“类型”中会列出“Windows Microsoft Entra ID (Microsoft)”(适用于 Microsoft Entra 连接器)或“Active Directory 域服务”(适用于本地 AD DS 连接器)。 请记下连接器名称,以便在下一步骤所述的 PowerShell 脚本中使用。
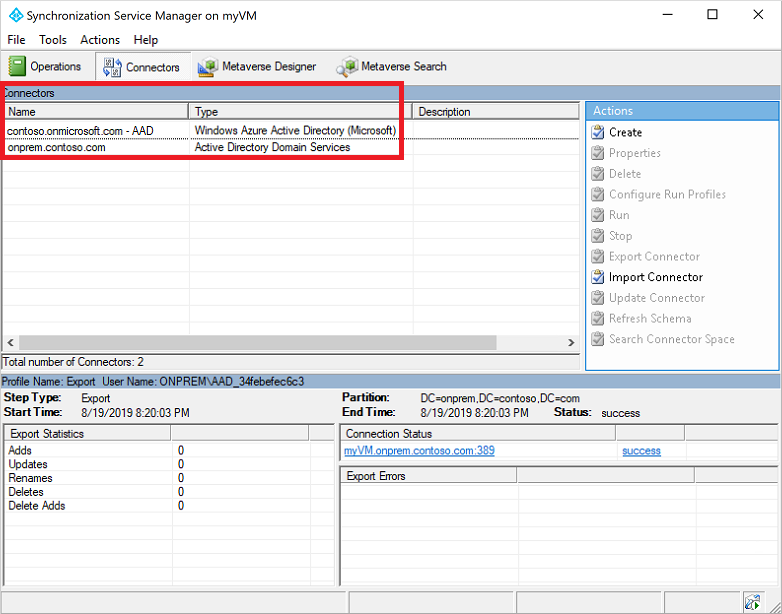
此示例屏幕截图中使用了以下连接器:
- Microsoft Entra 连接器名为“contoso.partner.onmschina.cn - Microsoft Entra ID”
- 本地 AD DS 连接器名为 onprem.contoso.com
将以下 PowerShell 脚本复制并粘贴到安装了 Microsoft Entra Connect 的计算机上。 该脚本触发完全密码同步(包括旧密码哈希)。 使用上一步骤中的连接器名称更新
$azureadConnector和$adConnector变量。在每个 AD 林中运行此脚本,以将本地帐户 NTLM 和 Kerberos 密码哈希同步到 Microsoft Entra ID。
# Define the Azure AD Connect connector names and import the required PowerShell module $azureadConnector = "<CASE SENSITIVE AZURE AD CONNECTOR NAME>" $adConnector = "<CASE SENSITIVE AD DS CONNECTOR NAME>" Import-Module "C:\Program Files\Azure AD Sync\Bin\ADSync\ADSync.psd1" Import-Module "C:\Program Files\Azure Active Directory Connect\AdSyncConfig\AdSyncConfig.psm1" # Create a new ForceFullPasswordSync configuration parameter object then # update the existing connector with this new configuration $c = Get-ADSyncConnector -Name $adConnector $p = New-Object Microsoft.IdentityManagement.PowerShell.ObjectModel.ConfigurationParameter "Microsoft.Synchronize.ForceFullPasswordSync", String, ConnectorGlobal, $null, $null, $null $p.Value = 1 $c.GlobalParameters.Remove($p.Name) $c.GlobalParameters.Add($p) $c = Add-ADSyncConnector -Connector $c # Disable and re-enable Azure AD Connect to force a full password synchronization Set-ADSyncAADPasswordSyncConfiguration -SourceConnector $adConnector -TargetConnector $azureadConnector -Enable $false Set-ADSyncAADPasswordSyncConfiguration -SourceConnector $adConnector -TargetConnector $azureadConnector -Enable $true将旧密码哈希同步到 Microsoft Entra ID 可能需要一段时间,具体时间取决于目录的大小(根据帐户和组的数目度量)。 密码在同步到 Microsoft Entra ID 之后,将同步到托管域。
后续步骤
本教程介绍了以下内容:
- 为何需要旧 NTLM 和 Kerberos 密码哈希
- 如何为 Microsoft Entra Connect 配置旧密码哈希同步