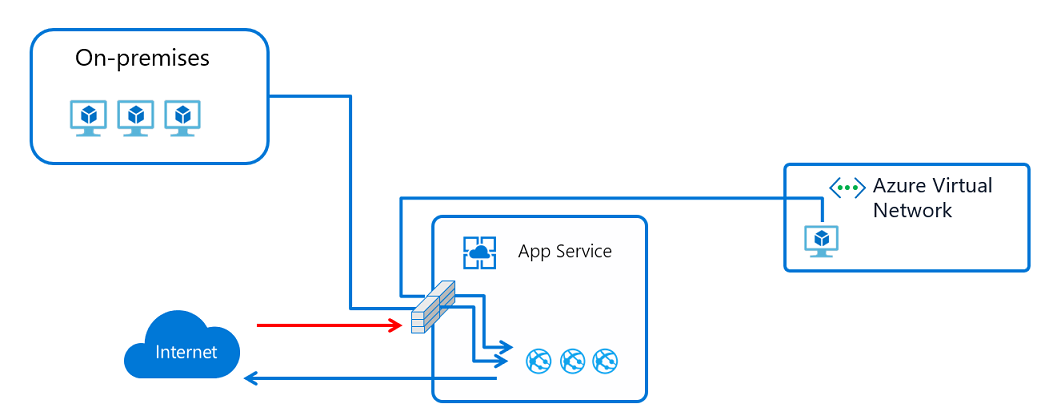
设置访问限制后,可以定义一个按优先级排序的允许/拒绝列表,用于控制在网络中对应用的访问。 该列表可以包含 IP 地址或 Azure 虚拟网络子网。 如果存在一个或多个条目,则列表末尾会存在一个隐式的“全部拒绝”。 有关详细信息,请参阅 Azure 应用服务访问限制。
访问限制功能适用于所有 Azure 应用服务托管的工作负载。 工作负载可包括 Web 应用、API 应用、Linux 应用、Linux 自定义容器和 Azure Functions 应用。
当有人向应用发出请求时,会根据访问限制列表中的规则评估 FROM 地址。 如果 FROM 地址位于配置为使用 Microsoft.Web 服务终结点的子网中,则会根据访问限制列表中的虚拟网络规则比较源子网。 如果列表中的规则不允许访问该地址,则服务会以“HTTP 403”状态代码进行答复。
访问限制功能是在应用服务前端角色(即代码运行所在的辅助角色主机中的上游)中实现的。 因此,访问限制是有效的网络访问控制列表 (ACL)。
限制从 Azure 虚拟网络访问 Web 应用的功能使用服务终结点。 使用服务终结点,你可以限制从选定的子网对多租户服务进行访问。 对托管在应用服务环境中的应用的流量进行限制不起作用。 如果处于应用服务环境中,可应用 IP 地址规则控制对应用的访问。
注意
必须在网络端以及要对其启用服务终结点的 Azure 服务上同时启用服务终结点。 有关支持服务终结点的 Azure 服务列表,请参阅虚拟网络服务终结点。
在门户中管理访问限制规则
若要向应用添加访问限制规则,请执行以下操作:
登录 Azure 门户。
选择要为其添加访问限制的应用。
在左侧菜单中,选择“设置”“网络”。>
在“网络”窗格的“入站流量配置”下,选择“公用网络访问”设置。
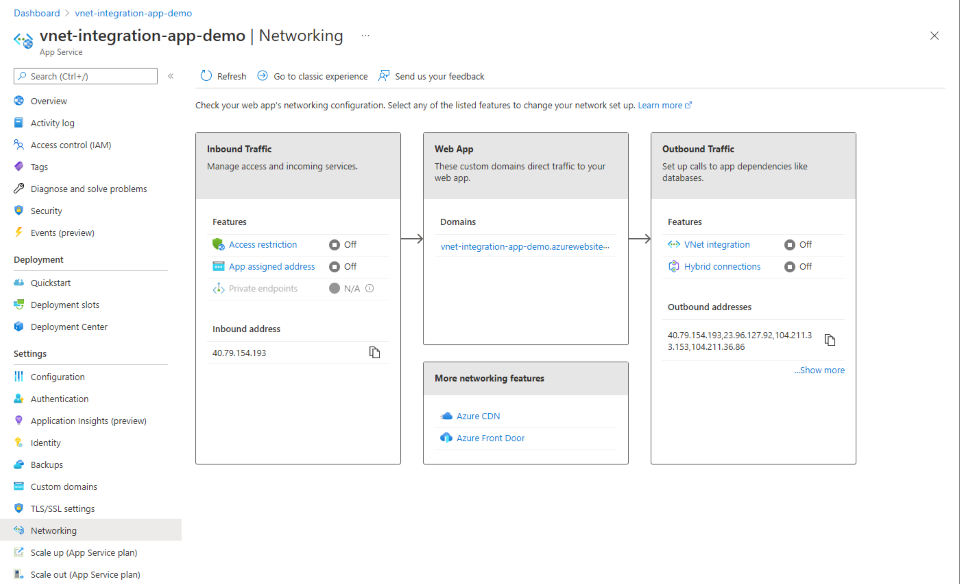
在“访问限制”窗格上查看为应用定义的访问限制规则列表。
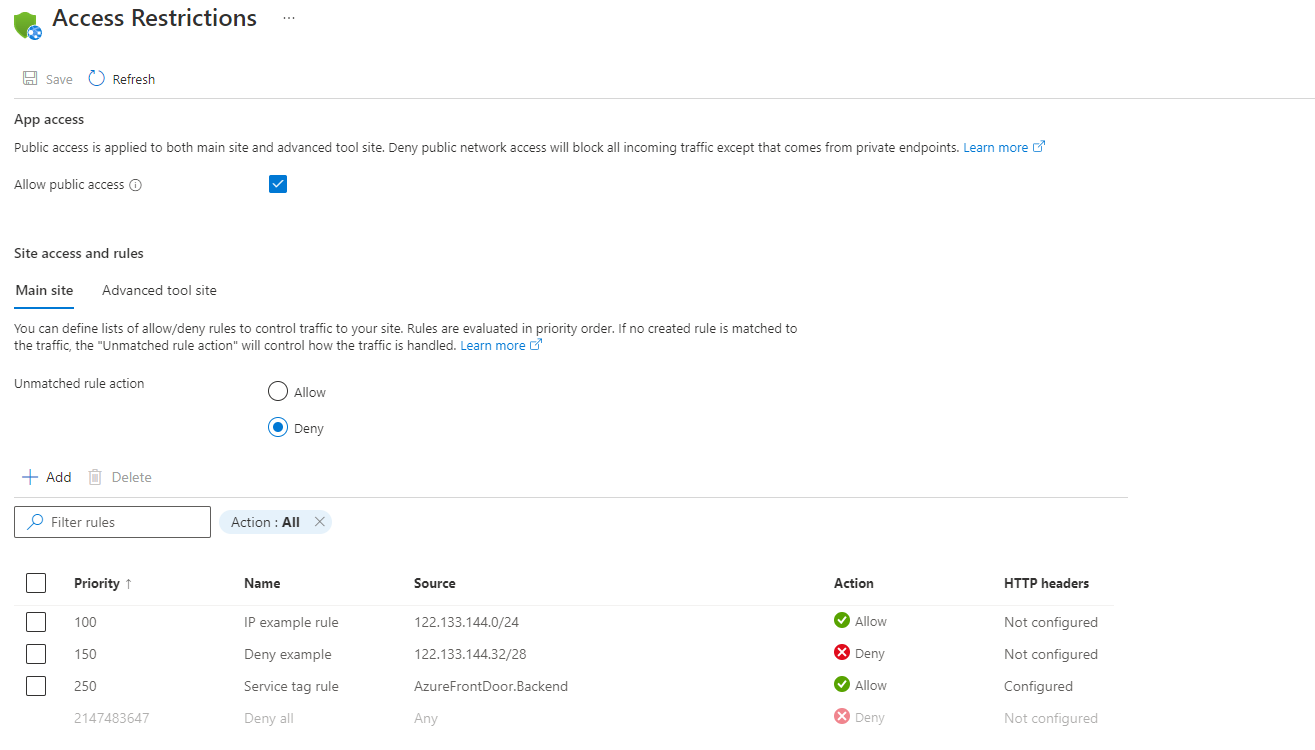
列表显示当前应用于该应用的限制。 如果存在对应用的虚拟网络限制,该表将显示是否为
Microsoft.Web启用了服务终结点。 如果应用未定义任何限制,并且不匹配的规则未设置为“拒绝”,则可从任何位置访问该应用。
权限
必须具有子网的以下基于角色的访问控制权限或更高级别权限,才能通过 Azure 门户、CLI 或在直接设置 site config 时来配置访问限制:
| 操作 | 说明 |
|---|---|
Microsoft.Web/sites/config/read |
获取 Web 应用配置设置。 |
Microsoft.Web/sites/config/write |
更新 Web 应用的配置设置。 |
Microsoft.Network/virtualNetworks/subnets/joinViaServiceEndpoint/action* |
将存储帐户或 SQL 数据库等资源加入到子网。 |
Microsoft.Web/sites/write** |
更新 Web 应用设置。 |
*只在添加虚拟网络(服务终结点)规则时需要
**仅当通过 Azure 门户更新访问限制时需要
如果要添加基于服务终结点的规则,并且虚拟网络与应用位于不同的订阅中,则必须确保已为 Microsoft.Web 资源提供程序注册了使用虚拟网络的订阅。 可以显式注册提供程序,也可在订阅中创建第一个 Web 应用时自动注册。 有关详细信息,请参阅注册资源供应商。
添加访问限制规则
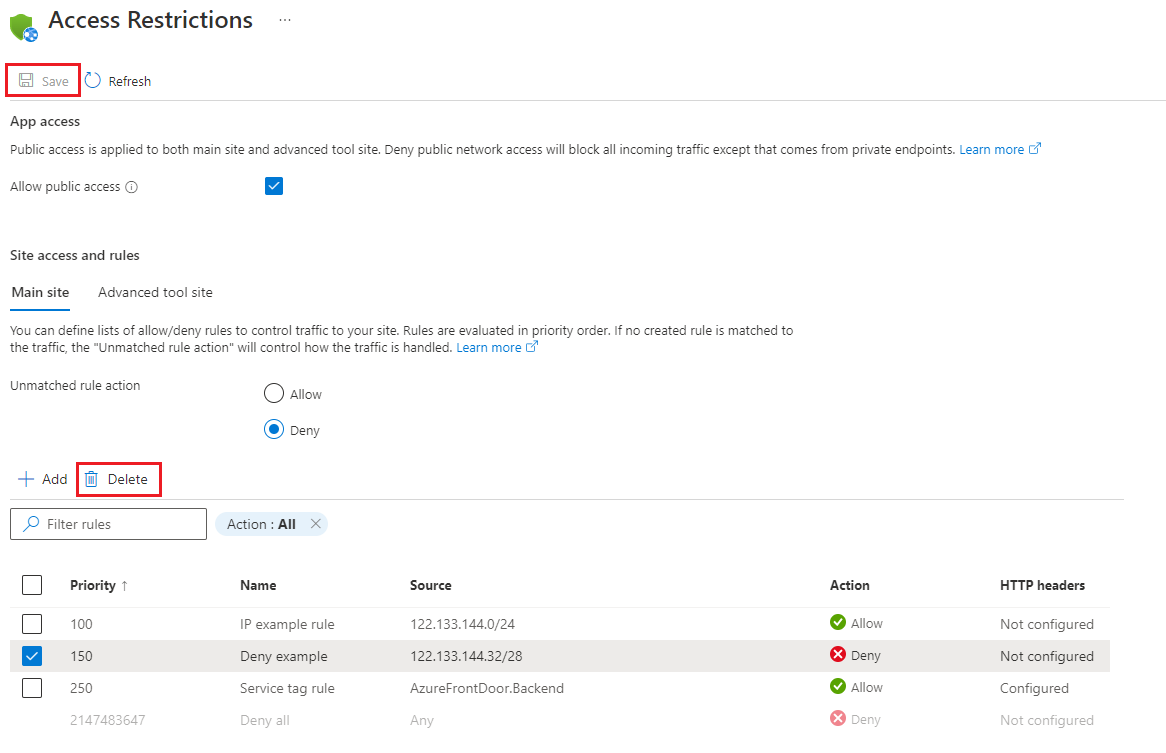
若要向应用添加访问限制规则,请在“访问限制”窗格中选择“添加”。 该规则仅在保存后有效。
系统会从“优先级”列中最小的数字开始,按优先级顺序强制执行规则。 如果未配置不匹配的规则,当添加了一条规则时,一个隐式的“全部拒绝”也会立即生效。
在“添加访问限制”窗格上创建规则时,请执行以下操作:
- 在“操作”下,选择“允许”或“拒绝” 。
- 输入规则名称和说明(可选)。
- 在“优先级”框中,输入一个优先级值。
- 在“类型”下拉列表中,选择规则类型。 以下部分介绍了不同类型的规则。
- 键入特定于规则的输入。 选择“添加规则”将规则添加到列表中。
- 在“访问限制”窗格上选择“保存”。
注意
访问限制规则有最多 512 条的限制。 如果需要超过 512 条访问限制规则,建议你考虑使用独立的安全产品。 请考虑 Azure Front Door、Azure 应用程序网关或其他 Web 应用程序防火墙 (WAF)。
设置基于 IP 地址的规则
按照上一部分所述的过程操作,但有以下新增内容:
- 在步骤 4 的“类型”下拉列表中,选择“IPv4”或“IPv6”。
以无类别域际路由选择 (CIDR) 表示法为 IPv4 和 IPv6 地址指定 IP 地址块。 若要指定地址,可以使用类似 1.2.3.4/32 的格式,其中前四个八位字节代表自己的 IP 地址,/32 为掩码。 所有地址的 IPv4 CIDR 表示法都为 0.0.0.0/0。
注意
基于 IP 的访问限制规则仅在应用位于应用服务环境中时处理虚拟网络地址范围。 如果应用位于多租户服务中,则需要使用服务终结点,以仅允许虚拟网络中选定子网的流量。
设置基于服务终结点的规则
在步骤 4 的“类型”下拉列表中,选择“虚拟网络”。
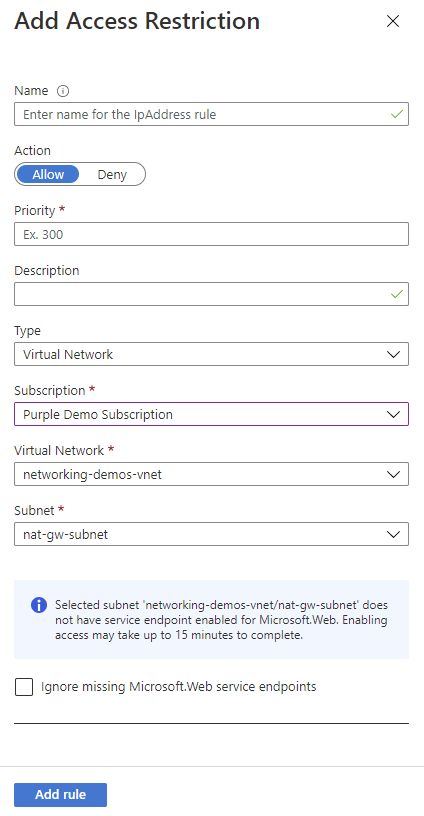
指定“订阅”、“虚拟网络”和“子网”下拉列表,以匹配要限制访问的内容。
使用服务终结点可以限制对所选 Azure 虚拟网络子网的访问。 如果尚未使用 Microsoft.Web 为所选子网启用服务终结点,则除非选择“忽略缺少的 Microsoft.Web 服务终结点”,否则会自动启用这些终结点。 是否要在应用上而不是子网上启用服务终结点取决于你是否有权在子网上启用它们。
如果需要其他人在子网上启用服务终结点,请选择“忽略缺少的 Microsoft.Web 服务终结点”。 已针对服务终结点配置应用。 稍后可以在子网上启用。
不能使用服务终结点来限制对在应用服务环境中运行的应用程序的访问。 当应用处于应用服务环境中时,可以应用 IP 访问规则来控制对它的访问。
借助服务终结点,可以使用应用程序网关或其他 Web 应用程序防火墙 (WAF) 设备来配置应用。 你还可以配置具有安全后端的多层应用程序。 有关详细信息,请参阅应用服务网络功能和应用程序网关集成。
注意
对于通过虚拟 IP 使用基于 IP 的 TLS/SSL 绑定的 Web 应用,不支持服务终结点。
设置基于服务标记的规则
在步骤 4 的“类型”下拉列表中,选择“服务标记”。
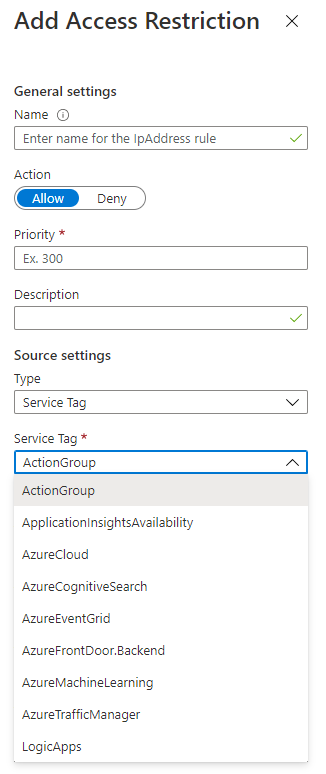
访问限制规则支持所有公开可用服务标记。 每个服务标记代表 Azure 服务中的 IP 范围列表。 这些服务的列表以及指向特定范围的链接可以在服务标记文档中找到。 使用 Azure 资源管理器模板或脚本配置更高级的规则,如区域范围内的规则。
注意
通过 Azure 门户或 Azure CLI 创建基于服务标记的规则时,需要订阅级别的读取访问权限才能获取供选择/验证的服务标记的完整列表。 此外,还需要在订阅上注册 Microsoft.Network 资源提供程序。
编辑规则
若要编辑现有的访问限制规则,请转到“访问限制”窗格,然后选择要编辑的规则。
在“编辑访问限制”窗格上,进行更改,然后选择“更新规则” 。
选择“保存”,保存更改。
注意
编辑规则时,不能在规则类型之间切换。
删除规则
若要删除规则,请在“访问限制”窗格上选择要删除的规则,然后选择“删除”。
选择“保存”,保存更改。
访问限制高级方案
以下各部分介绍了如何在高级方案中使用访问限制。
按 HTTP 标头筛选
可以将 HTTP 标头筛选器添加到任何规则。 支持以下 HTTP 标头名称:
X-Forwarded-ForX-Forwarded-HostX-Azure-FDIDX-FD-HealthProbe
++ 有关 X-FD-HealthProbe 的详细信息,请参阅 站点访问限制规则的 HTTP 标头筛选。
对于每个标头名称,最多可以添加 8 个以逗号分隔的值。 在规则本身之后评估 HTTP 标头筛选器,并且必须满足两个条件才能应用规则。
多源规则
多源规则允许在单个规则中合并多达 8 个 IP 范围或 8 个服务标记。 如果 IP 范围超过 512 个,或者想要创建逻辑规则,请使用多源规则。 例如:逻辑规则可以将多个 IP 范围与单个 HTTP 标头筛选器相结合。
多源规则定义方式与单源规则相同,但每个范围用逗号分隔。
PowerShell 示例:
Add-AzWebAppAccessRestrictionRule -ResourceGroupName "ResourceGroup" -WebAppName "AppName" `
-Name "Multi-source rule" -IpAddress "192.168.1.0/24,192.168.10.0/24,192.168.100.0/24" `
-Priority 100 -Action Allow
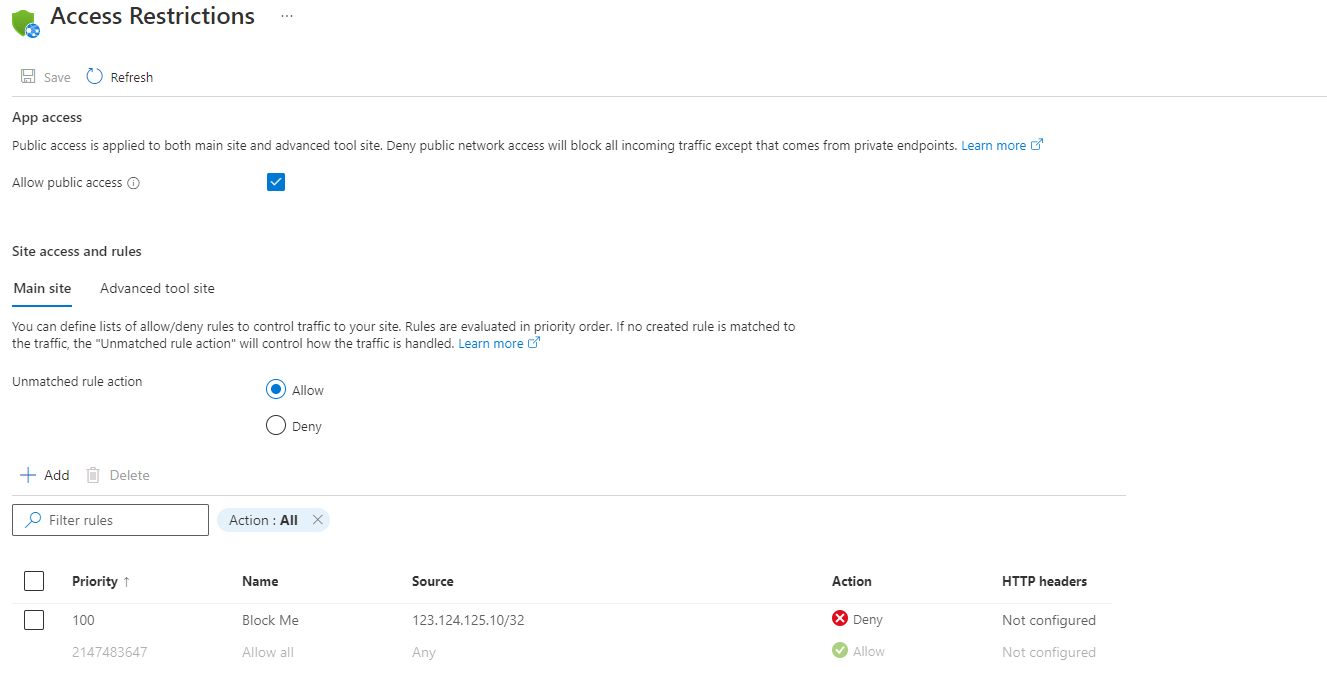
阻止单个 IP 地址
如果你希望明确阻止单个 IP 地址或一组 IP 地址,但同时要允许访问其他所有地址,可以为特定 IP 地址添加“拒绝”规则。 然后,将未匹配规则操作配置为“允许”。
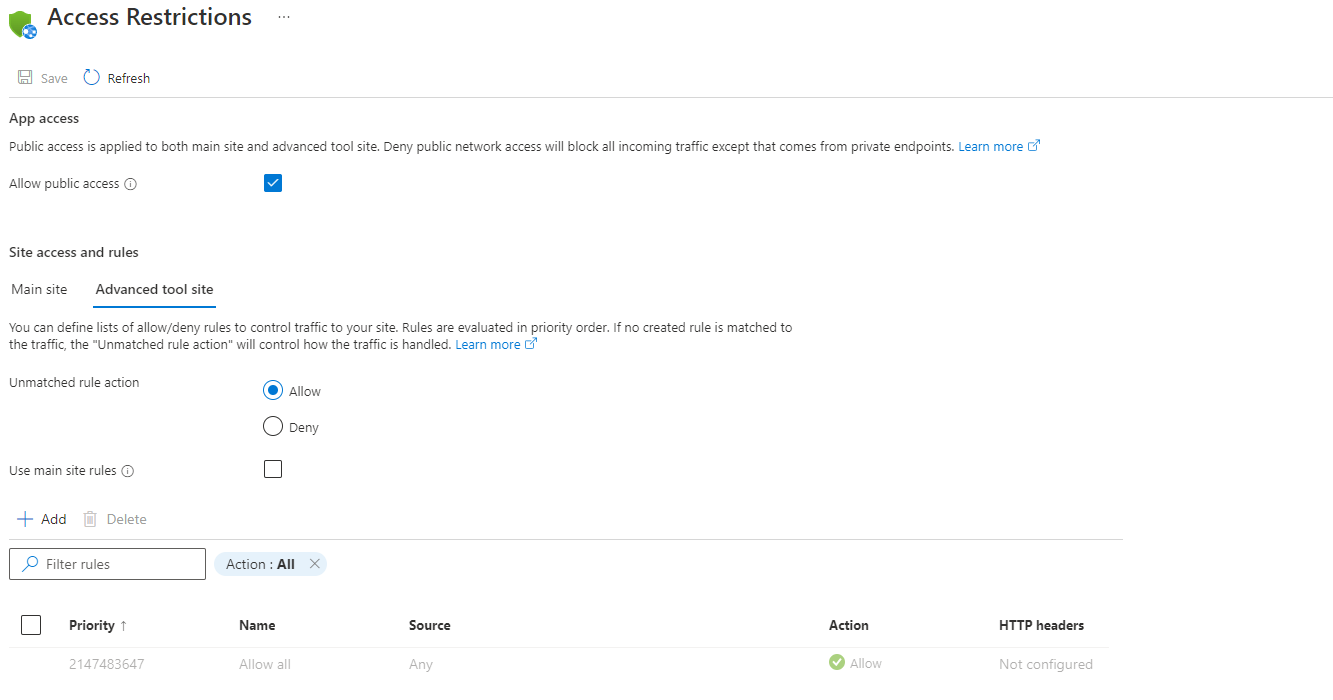
限制对 SCM 站点的访问
除了能够控制对应用的访问以外,还可以限制对应用所用的源代码管理 (SCM) 高级工具站点的访问。 SCM 站点既是 Web 部署终结点,也是 Kudu 控制台。 你可以从应用程序单独分配对 SCM 站点的访问限制,也可以对应用和 SCM 站点使用相同的限制设置。 如果选中“使用主站点规则”,将隐藏规则列表。 SCM 站点使用主站点的规则。 如果取消选中该复选框,SCM 站点设置会再次显示。
限制对特定 Azure Front Door 实例的访问
从 Azure Front Door 流向应用程序的流量始发自 AzureFrontDoor.Backend 服务标记中定义的一组已知 IP 范围。 使用服务标记限制规则,可以限制流量只能源自 Azure Front Door。 为确保流量仅来自特定实例,需要根据 Azure Front Door 发送的唯一 HTTP 标头进一步筛选传入的请求。
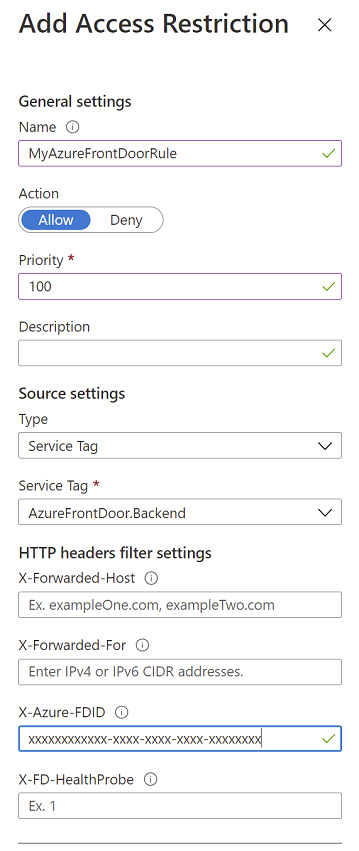
PowerShell 示例:
$afd = Get-AzFrontDoor -Name "MyFrontDoorInstanceName"
Add-AzWebAppAccessRestrictionRule -ResourceGroupName "ResourceGroup" -WebAppName "AppName" `
-Name "Front Door example rule" -Priority 100 -Action Allow -ServiceTag AzureFrontDoor.Backend `
-HttpHeader @{'x-azure-fdid' = $afd.FrontDoorId}
以编程方式管理访问限制
还可通过编程方式管理访问限制。 以下示例介绍了如何为访问限制添加规则,以及如何为主站点和高级工具站点更改不匹配的规则操作。
为主站添加访问限制规则
可以通过选择以下选项之一来以编程方式为主站点添加访问限制规则:
可以在 Azure CLI 中运行以下命令。 有关命令的详细信息,请参阅 az webapp config access-restriction。
az webapp config access-restriction add --resource-group ResourceGroup --name AppName \
--rule-name 'IP example rule' --action Allow --ip-address 122.133.144.0/24 --priority 100
az webapp config access-restriction add --resource-group ResourceGroup --name AppName \
--rule-name "Azure Front Door example" --action Allow --priority 200 --service-tag AzureFrontDoor.Backend \
--http-header x-azure-fdid=xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
为高级工具站点添加访问限制规则
可以通过编程方式为高级工具站点添加访问限制规则。 选择以下选项之一:
可以在 Azure CLI 中运行以下命令。 有关命令的详细信息,请参阅 az webapp config access-restriction。
az webapp config access-restriction add --resource-group ResourceGroup --name AppName \
--rule-name 'IP example rule' --action Allow --ip-address 122.133.144.0/24 --priority 100 --scm-site true
为主站点更改不匹配的规则操作
可以通过选择以下选项之一,以编程方式为主站点更改不匹配的规则操作:
可以在 Azure CLI 中运行以下命令。 有关此命令的更多信息,请参阅 az resource。
ipSecurityRestrictionsDefaultAction 的可接受值为 Allow 或 Deny。
az resource update --resource-group ResourceGroup --name AppName --resource-type "Microsoft.Web/sites" \
--set properties.siteConfig.ipSecurityRestrictionsDefaultAction=Allow
为高级工具站点更改不匹配的规则操作
可以通过选择以下选项之一,以编程方式为高级工具站点更改不匹配的规则操作:
可以在 Azure CLI 中运行以下命令。 有关此命令的更多信息,请参阅 az resource。
scmIpSecurityRestrictionsDefaultAction 的可接受值为 Allow 或 Deny。
az resource update --resource-group ResourceGroup --name AppName --resource-type "Microsoft.Web/sites" \
--set properties.siteConfig.scmIpSecurityRestrictionsDefaultAction=Allow
设置 Azure Functions 访问限制
访问限制也适用于与应用服务计划具有相同功能的函数应用。 启用访问限制时,还可针对任何不允许的 IP 禁用 Azure 门户代码编辑器。