在 Azure 应用服务中使用 TLS/SSL 绑定保护自定义 DNS 名称
本文介绍如何通过创建证书绑定来确保应用服务应用或函数应用中自定义域的安全。 完成后,可访问自定义 DNS 名称(例如,https://www.contoso.com)的 https:// 终结点处的应用服务应用。

先决条件
- 将你的应用服务应用纵向扩展到受支持的定价层之一:基本、标准、高级。
- 将域名映射到应用。
1. 添加绑定
在 Azure 门户中:
在左侧菜单中,选择“应用服务”>“<app-name>”。
在应用的左侧导航栏中,选择“自定义域”
在自定义域旁边,选择“添加绑定”
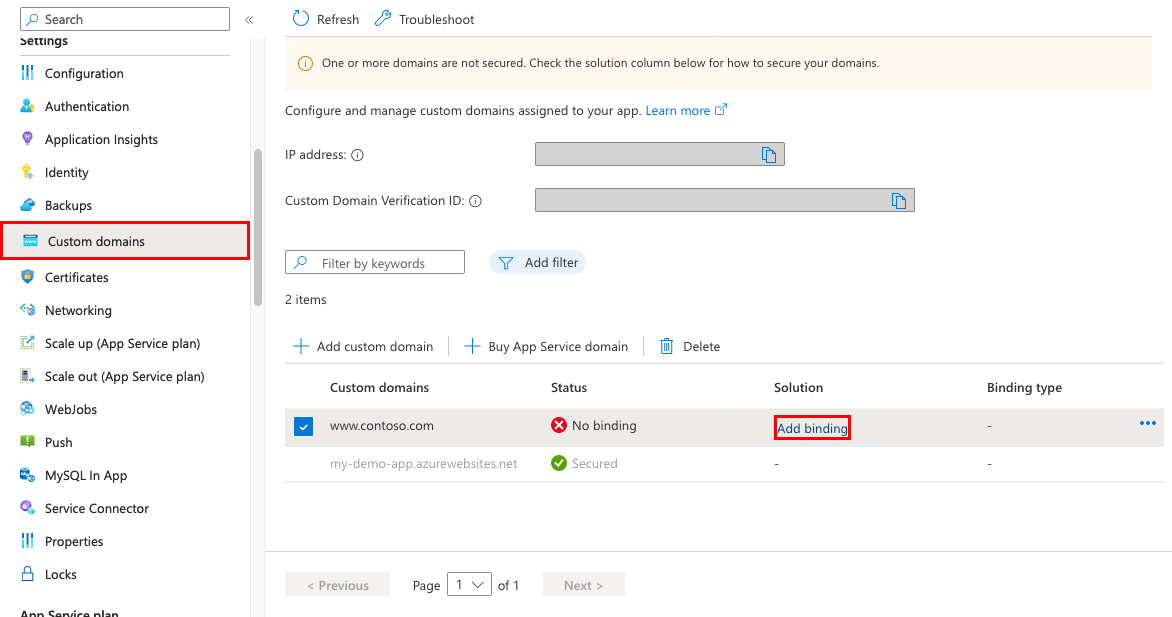
如果你的应用已有所选自定义域的证书,则可以在“证书”中选择它。 如果没有,则必须使用“源”中的选项之一添加证书。
- 创建应用服务托管证书 - 允许应用服务为所选域创建托管证书。 此选项是最简单的。
- 导入应用服务证书 - 在“应用服务证书”中,选择一个应用服务证书。
- 上传证书 (.pfx) - 按照上传专用证书中的工作流从本地计算机上传 PFX 证书并指定证书密码。
- 从密钥保管库导入 - 选择“选择密钥保管库证书”,并在对话框中选择证书。
在 TLS/SSL 类型中,在 SNI SSL 和基于 IP 的 SSL 之间进行选择。
- SNI SSL:可添加多个 SNI SSL 绑定。 选择此选项可以使用多个 TLS/SSL 证书来保护同一 IP 地址上的多个域。 大多数新式浏览器(包括 Internet Explorer、Chrome、Firefox 和 Opera)都支持 SNI。
-
- 基于 IP 的 SSL:只能添加一个 IP SSL 绑定。 选择此选项只能使用一个 TLS/SSL 证书来保护专用公共 IP 地址。 配置绑定后,请按照 2. 重新映射基于 IP 的 SSL 的记录中的步骤进行操作。
IP SSL 仅在“基本”层或更高层中受支持。
- 基于 IP 的 SSL:只能添加一个 IP SSL 绑定。 选择此选项只能使用一个 TLS/SSL 证书来保护专用公共 IP 地址。 配置绑定后,请按照 2. 重新映射基于 IP 的 SSL 的记录中的步骤进行操作。
添加新证书时,通过选择“验证”来验证新证书。
选择 添加 。
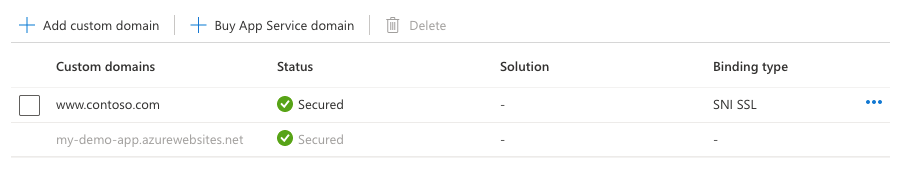
操作完成之后,自定义域的 TLS/SSL 状态会更改为“安全” 。
注意
“自定义域”中的状态为“安全”意味着已使用证书保护该域,但应用服务并未检查该证书是自签名证书还是已过期证书,这可能也会导致浏览器异常,例如显示错误或警告。
2. 为基于 IP 的 SSL 重新映射记录
只有基于 IP 的 SSL 才需要此步骤。 对于 SNI SSL 绑定,请跳到测试自定义域的 HTTPS。
可能需要进行两项更改:
默认情况下,应用使用共享的公共 IP 地址。 将证书与 IP SSL 绑定时,应用服务会为应用创建新的专用 IP 地址。 如果已将 A 记录映射到应用,请使用这个新的专用 IP 地址更新域注册表。
将使用新的专用 IP 地址更新应用的“自定义域”页。 复制此 IP 地址,然后将 A 记录重新映射到此新 IP 地址。
如果已有到
<app-name>.chinacloudsites.cn的 SNI SSL 绑定,请重新映射任何 CNAME 映射,让其改为指向sni.<app-name>.chinacloudsites.cn(添加sni前缀)。
3. 测试 HTTPS
在不同的浏览器中,导航到 https://<your.custom.domain> 以核实其是否适合应用。

应用程序代码可以通过“x-appservice-proto”标头检查协议。 标头具有 http 或 https 值。
注意
如果应用显示证书验证错误,可能是因为使用自签名证书。
如果不是这样,可能是在将证书导出为 PFX 文件时遗漏了中间证书。
常见问题
如何确保在更改证书绑定时应用的 IP 地址不会更改?
在删除某个绑定时,即使该绑定是 IP SSL,入站 IP 地址也可能会更改。 在续订已进行 IP SSL 绑定的证书时,了解这一点尤为重要。 若要避免应用的 IP 地址更改,请按顺序执行以下步骤:
- 上传新证书。
- 将新证书绑定到所需的自定义域,不要删除旧证书。 此操作替换而不是删除旧的绑定。
- 删除旧证书。
是否可以禁用从 HTTP 到 HTTPS 的强制重定向?
默认情况下,应用服务强制从 HTTP 请求重定向到 HTTPS。 若要禁用此行为,请参阅配置常规设置。
如何更改应用的最低 TLS 版本?
应用默认情况下允许 TLS 1.2,这是行业标准(例如 PCI DSS)建议的 TLS 级别。 若要强制实施不同的 TLS 版本,请参阅配置常规设置。
如何在应用服务中处理 TLS 终止?
在应用服务中,TLS 终止在网络负载均衡器上发生,因此,所有 HTTPS 请求将以未加密的 HTTP 请求形式访问你的应用。 如果应用逻辑需要检查用户请求是否已加密,可以检查 X-Forwarded-Proto 标头。
特定于语言的配置指南,如 Linux Node.js 配置指南,介绍如何在应用程序代码中检测 HTTPS 会话。
使用脚本自动化
Azure CLI
PowerShell
$fqdn="<Replace with your custom domain name>"
$pfxPath="<Replace with path to your .PFX file>"
$pfxPassword="<Replace with your .PFX password>"
$webappname="mywebapp$(Get-Random)"
$location="China North"
# Create a resource group.
New-AzResourceGroup -Name $webappname -Location $location
# Create an App Service plan in Free tier.
New-AzAppServicePlan -Name $webappname -Location $location `
-ResourceGroupName $webappname -Tier Free
# Create a web app.
$webapp = New-AzWebApp -Name $webappname -Location $location -AppServicePlan $webappname `
-ResourceGroupName $webappname
Write-Host "Sign in to your domain provider's website and configure the following records:"
Write-Host "A CNAME record that maps $fqdn to $webappname.chinacloudsites.cn"
Write-Host "A TXT record that maps asuid.$fqdn to the domain verification ID $($webapp.CustomDomainVerificationId)"
Read-Host "Press [Enter] key when ready ..."
# Before continuing, go to your DNS configuration UI for your custom domain and follow the
# instructions at /app-service/app-service-web-tutorial-custom-domain#step-2-create-the-dns-records to configure a CNAME record for the
# hostname "www" and point it your web app's default domain name.
# Upgrade App Service plan to Basic tier (minimum required by custom SSL certificates)
Set-AzAppServicePlan -Name $webappname -ResourceGroupName $webappname `
-Tier Basic
# Add a custom domain name to the web app.
Set-AzWebApp -Name $webappname -ResourceGroupName $webappname `
-HostNames @($fqdn,"$webappname.chinacloudsites.cn")
# Upload and bind the SSL certificate to the web app.
New-AzWebAppSSLBinding -WebAppName $webappname -ResourceGroupName $webappname -Name $fqdn `
-CertificateFilePath $pfxPath -CertificatePassword $pfxPassword -SslState SniEnabled