重要
本文介绍用于独立应用服务计划的应用服务环境 v2。 应用服务环境 v1 和 v2 于 2024 年 8 月 31 日停用。 应用服务环境有新版本,此版本更易于使用并在更强大的基础结构上运行。 若要详细了解该新版本,请先参阅应用服务环境简介。 如果你当前正在使用应用服务环境 v1,请按照本文中的步骤迁移到新版本。
从 2024 年 8 月 31 日开始,服务级别协议 (SLA) 和服务额度不再适用于继续投入生产的应用服务环境 v1 和 v2 工作负载,因为这些产品已经停用。 应用服务环境 v1 和 v2 硬件已开始停用,这可能会影响你的应用和数据的可用性和性能。
必须立即完成到应用服务环境 v3 的迁移,否则你的应用和资源可能会被删除。 我们将使用就地迁移功能在最大程度上努力尝试自动迁移任何剩余的应用服务环境 v1 和 v2,但 Microsoft 对自动迁移后的应用程序可用性不作任何声明或保证。 你可能需要执行手动配置来完成迁移,并优化应用服务计划 SKU 选项来满足需求。 如果无法进行自动迁移,你的资源和关联的应用数据会被删除。 我们强烈建议你立即采取行动,以避免发生这两种极端情况之一。
如果你需要更多时间,我们可以提供一次性的 30 天宽限期,以便你完成迁移。 如需了解更多信息并申请此宽限期,请查看宽限期概述,然后转到 Azure 门户并访问每个应用服务环境的“迁移”窗格。
有关应用服务环境 v1/v2 停用的最新信息,请参阅应用服务环境 v1 和 v2 停用更新。
总结
应用服务环境 (ASE) 是在 Azure 虚拟网络中运行的 Azure 应用服务的单租户部署。 尽管 ASE 确实在虚拟网络中运行,但仍必须能够从可供 Azure 应用服务用来管理服务的多个专用 IP 地址访问 ASE。 使用 ASE 时,管理流量将遍历用户控制的网络。 如果此流量被阻塞或被错误路由,则 ASE 将会挂起。 有关 ASE 网络依赖项的详细信息,请阅读网络注意事项和应用服务环境。 有关 ASE 的一般信息,请先阅读应用服务环境简介。
所有 ASE 都有一个公用 VIP,管理流量将从其中进入。 来自这些地址的传入管理流量将传入到 ASE 的公共 VIP 上的端口 454 和 455。 本文档列出了发往 ASE 的管理流量的应用服务源地址。 这些地址也位于名为 AppServiceManagement 的 IP 服务标记中。
可以在路由表中配置 AppServiceManagement 服务标记中的地址,以避免管理流量出现非对称路由问题。 如果可能,应使用服务标记而不是单个地址。 路由在 IP 级别作用于流量,但不区分流量方向,也不知道流量是否为 TCP 回复消息的一部分。 如果 TCP 请求的回复地址不同于其发送到的地址,则表示出现了非对称路由问题。 若要避免 ASE 管理流量出现非对称路由问题,需确保从回复发送到的地址发回回复。 要详细了解如何配置 ASE 以在从本地发送出站流量的环境中运行,请阅读为 ASE 配置强制隧道。
管理地址的列表
如果需要查看管理地址的 IP,请下载你的区域的服务标记参考以获取最新的地址列表。 应用服务环境管理地址列在 AppServiceManagement 服务标记中。
| 区域 | 服务标记参考 |
|---|---|
| 由世纪互联运营的 Azure | 42.159.4.236、42.159.80.125 |
配置网络安全组
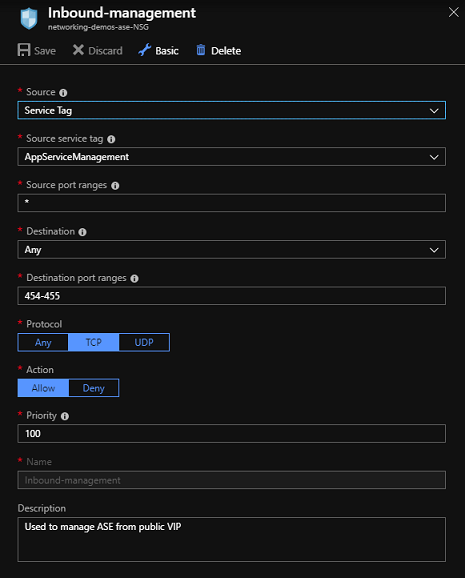
如果使用网络安全组,则不需要考虑单个地址的分配,也无需维护自己的配置。 名为 AppServiceManagement 的 IP 服务标记将与所有地址保持同步。 若要在 NSG 中使用此 IP 服务标记,请转到门户,打开网络安全组 UI,并选择“入站安全规则”。 如果入站管理流量存在现有的规则,请编辑该规则。 如果未对 ASE 创建此 NSG,或者此 NSG 是全新的,请选择“添加”。 在“源”下拉列表中,选择“服务标记”。 在“源服务标记”下,选择“AppServiceManagement”。 将源端口范围设置为 *,将“目标”设置为“任何”,将目标端口范围设置为 454-455,将“协议”设置为“TCP”,将“操作”设置为“允许”。 若要启用该规则,需要设置优先级。
配置路由表
可将管理地址放在包含 Internet 下一跃点的路由表中,以确保所有入站管理流量能够通过同一路径返回。 配置强制隧道时需要这些路由。 如果可能,请使用 AppServiceManagement 服务标记而不是单个地址。 若要创建路由表,可以使用门户、PowerShell 或 Azure CLI。 下面是在 PowerShell 提示符下使用 Azure CLI 创建路由表的命令。
$sub = "subscription ID"
$rg = "resource group name"
$rt = "route table name"
$location = "azure location"
az network route-table route create --subscription $sub -g $rg --route-table-name $rt -n 'AppServiceManagement' --address-prefix 'AppServiceManagement' --next-hop-type 'Internet'
创建路由表后,需在 ASE 子网中设置该路由表。
通过 API 获取管理地址
可以使用以下 API 调用列出与 ASE 匹配的管理地址。
get /subscriptions/<subscription ID>/resourceGroups/<resource group>/providers/Microsoft.Web/hostingEnvironments/<ASE Name>/inboundnetworkdependenciesendpoints?api-version=2016-09-01
API 返回一个 JSON 文档,其中包含 ASE 的所有入站地址。 地址列表包括管理地址、ASE 使用的 VIP 和 ASE 子网地址范围本身。
若要使用 armclient 调用此 API,请使用以下命令,但请替换为你的订阅 ID、资源组和 ASE 名称。
armclient login
armclient get /subscriptions/<subscription ID>/resourceGroups/<resource group>/providers/Microsoft.Web/hostingEnvironments/<ASE Name>/inboundnetworkdependenciesendpoints?api-version=2016-09-01