应用程序网关日志提供有关与资源及其操作相关的事件的详细信息。 这些日志可用于访问、活动、防火墙和性能等事件(仅适用于 V1)。 使用此原始数据排查问题或生成分析仪表板时,日志中的精细信息非常有用。
日志可用于应用程序网关的所有资源;但是,要使用它们,必须在所选的存储位置启用其集合。 Azure 应用程序网关中的日志记录由 Azure Monitor 服务启用。 建议使用 Log Analytics 工作区,因为可以轻松使用其预定义的查询,并根据特定的日志条件设置警报。
资源日志的类型
可在 Azure 中使用不同类型的日志来对应用程序网关进行管理和故障排除。
- 活动日志
- 应用程序网关访问日志
- 应用程序网关性能日志(仅适用于 v1 SKU)
- 应用程序网关防火墙日志
注意
日志仅适用于在 Azure 资源管理器部署模型中部署的 Azure 资源。 你不能将日志用于经典部署模型中的资源。 若要更好地了解两种模型,请参阅了解 Resource Manager 部署和经典部署一文。
诊断日志的存储位置
Azure Monitor 根据分析、保留和集成要求提供多个选项来存储资源日志。 配置诊断设置时,可以选择一个或多个日志收集目标。
Log Analytics 工作区(建议) Log Analytics 工作区是收集和分析应用程序网关资源日志的建议目标。 它可以实现以下功能:
- 使用预定义的查询和可视化
- 基于特定日志条件创建警报
- 与 Log Analytics 中的 Azure Monitor 功能和见解集成后,用于存储诊断日志的表取决于诊断设置中配置的收集类型。
Log Analytics 中的集合类型
Azure 诊断(旧版): 选择 Azure 诊断时,所有日志都会写入共享的 AzureDiagnostics 表。由于此表在许多资源类型之间共享,因此每个服务都会写入其自己的自定义字段。 当自定义字段数超过 500 时,其他字段将作为键/值对存储在 AdditionalFields 动态属性下。 这可能会导致可发现性降低,并使查询变得更加复杂。
特定于资源(建议): 选择特定于资源时,日志将写入每个类别的专用表中。 特定于资源的模式提供:
- 使用可预测架构简化查询
- 改进了字段和表结构的可发现性
- 由于引入延迟较低和查询执行速度更快,性能更佳
- 通过在表级别分配访问权限来实现细粒度的基于角色的访问控制
对于应用程序网关,资源专用模式将创建以下表格:
在 Log Analytics 中选择集合类型
Azure 服务正在转换为特定于资源的模式。 作为此迁移的一部分,诊断设置中提供了一个切换来选择以下任一选项:
- 资源特定(默认设置)
- Azure 诊断
该开关确定所选类别的日志是路由到专用表还是路由到 AzureDiagnostics 表。 切换到特定于资源的模式时,只有新选择的类别才使用专用表;现有流将继续保持不变,直到重新配置。
通过工作区转换,选择特定于资源的模式可以增强灵活性,从而在引入之前预处理数据。有关配置工作区转换的指导,请参阅: 教程:使用 Azure 门户将工作区转换添加到 Azure Monitor 日志
使用工作区转换优化访问日志的示例
示例 1:选择性投影列:假设应用程序网关访问日志包含 20 列,但你希望仅分析来自六个特定列的数据。 通过使用工作区转换,可以将这六列投影到工作区中,从而有效地排除其他 14 列。 即使不会存储这些已排除列中的原始数据,但它们的空占位符仍然会出现在“日志”边栏选项卡中。 此方法优化了存储并确保仅保留相关数据进行分析。
注意
在“日志”边栏选项卡中,选择“试用新的 Log Analytics”选项可以更好地控制用户界面中显示的列。
示例 2:重点关注特定的状态代码:在分析访问日志时,无需处理所有日志条目,而可以编写一个查询来仅检索具有特定 HTTP 状态代码(例如 4xx 和 5xx)的行。 由于在理想情况下,大多数请求都属于 2xx 和 3xx 类别(表示成功的响应),因此重点关注有问题的状态代码可以缩小数据集的范围。 这种有针对性的方法使你能够提取最相关和可操作的信息,因此既可以带来便利,也可以产生经济效益。
从 Azure 诊断过渡到资源特定的表的建议策略:
- 评估当前数据保留期:确定 Azure 诊断表中当前保留数据的持续时间(例如:假设诊断表将数据保留 15 天)。
- 建立资源特定的保留:使用资源特定的表实现新的诊断设置。
- 并行数据收集:在临时性的一段时间内,在 Azure 诊断和资源特定的设置中并行收集数据。
- 确认数据准确度:验证两种设置中的数据收集是否准确且一致。
- 删除 Azure 诊断设置:删除 Azure 诊断设置以防止重复进行数据收集。
其他存储位置:
- Azure 存储帐户:如果日志存储时间较长并且希望能根据需要随时查看,最好使用存储帐户。
- Azure 事件中心:要集成其他安全信息和事件管理 (SIEM) 工具以获取资源警报,最好使用事件中心。
- Azure Monitor 合作伙伴集成。
详细了解 Azure Monitor 的诊断设置目标。
通过 PowerShell 启用日志记录
每个 Resource Manager 资源都会自动启用活动日志记录。 必须启用访问和性能日志记录才能开始收集通过这些日志提供的数据。 若要启用日志记录,请执行以下步骤:
记下存储帐户的资源 ID,其中存储日志数据。 此值的格式为:/subscriptions/<subscriptionId>/resourceGroups/<resourceGroupName>/providers/Microsoft.Storage/storageAccounts/<storageAccountName>。 可以使用订阅中的任何存储帐户。 可使用 Azure 门户查找此信息。
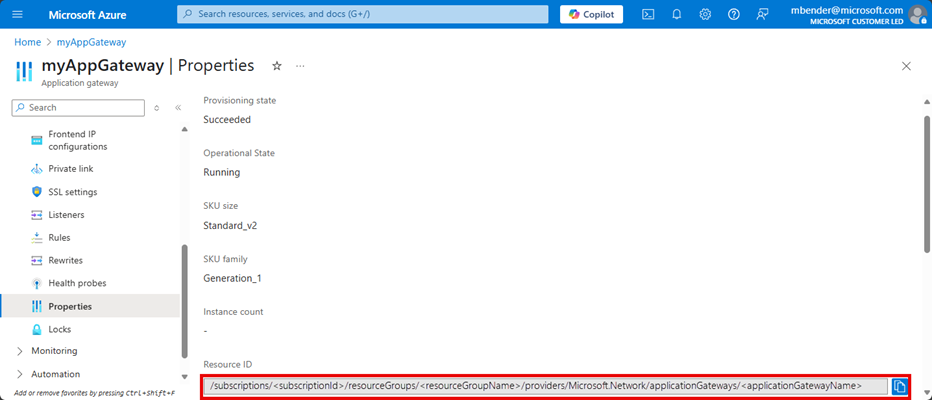
记下为其启用日志记录的应用程序网关的资源 ID。 此值的格式为:/subscriptions/subscriptionId</>resourceGroups/<resourceGroupName>/providers/Microsoft.Network/applicationGateways/<applicationGatewayName>。 可以使用门户查找以下信息。
使用以下 PowerShell cmdlet 启用诊断日志记录:
Set-AzDiagnosticSetting -ResourceId /subscriptions/<subscriptionId>/resourceGroups/<resourceGroupName>/providers/Microsoft.Network/applicationGateways/<applicationGatewayName> -StorageAccountId /subscriptions/<subscriptionId>/resourceGroups/<resourceGroupName>/providers/Microsoft.Storage/storageAccounts/<storageAccountName> -Enabled $true
提示
活动日志不需要单独的存储帐户。 使用存储来记录访问和性能需支付服务费用。
通过 Azure 门户启用日志记录
在 Azure 门户中找到资源,然后选择“诊断设置”。
对于应用程序网关,提供 3 种日志:
- 访问日志
- 性能日志(仅适用于 v1 SKU)
- 防火墙日志
若要开始收集数据,请选择“启用诊断”。
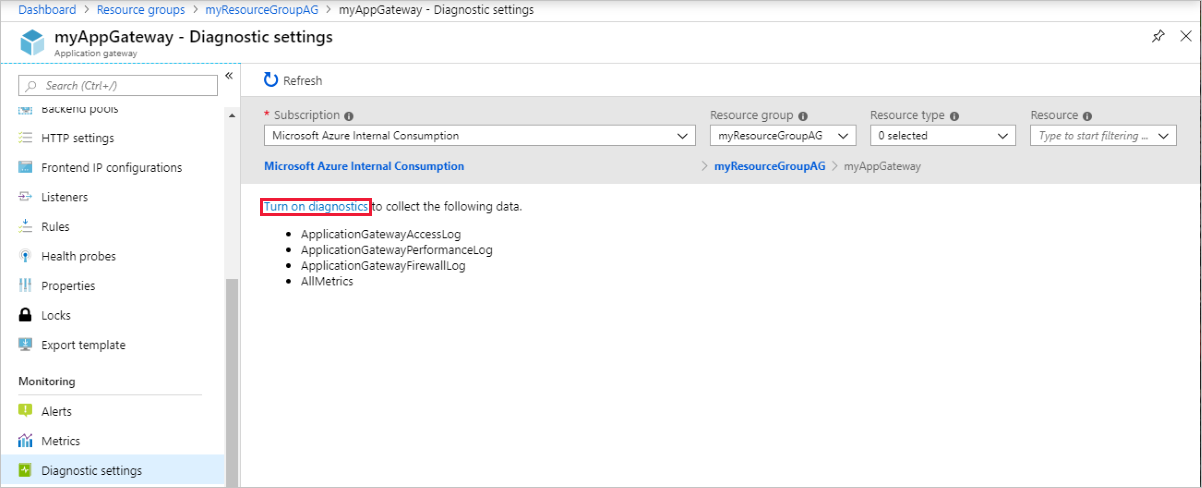
“诊断设置” 页提供用于诊断日志的设置。 本示例使用 Log Analytics 存储日志。 也可使用事件中心和存储帐户保存诊断日志。
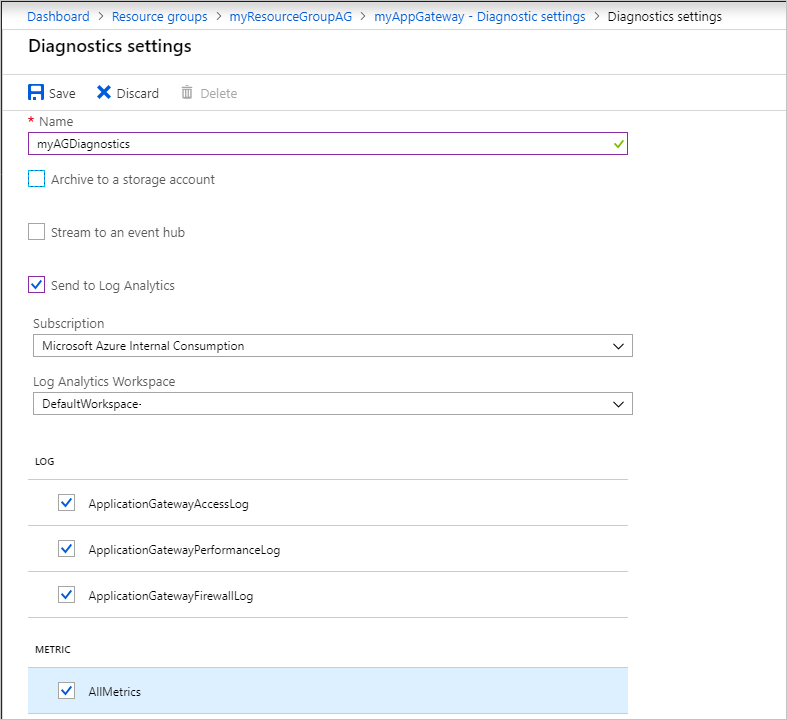
键入设置的名称,确认设置,然后选择“保存”。
若要查看和分析活动日志数据,请参阅“分析监视数据”。
查看并分析访问、性能和防火墙日志
Azure Monitor 日志可从 Blob 存储帐户收集计数器和事件日志文件。 有关详细信息,请参阅“分析监视数据”。
还可以连接到存储帐户并检索访问和性能日志的 JSON 日志条目。 下载 JSON 文件后,可以将其转换为 CSV 并在 Excel、Power BI 或任何其他数据可视化工具中查看。
提示
如果你熟悉 Visual Studio 和更改 C# 中的常量和变量值的基本概念,则可以使用 GitHub 提供的日志转换器工具。
后续步骤
- 使用 Azure Monitor 日志可视化计数器和事件日志。
- Visualize your Azure Activity Log with Power BI(使用 Power BI 直观显示 Azure 活动日志)博客文章。
- View and analyze Azure activity logs in Power BI and more(在 Power BI 和其他组件中查看和分析 Azure 活动日志)博客文章。