重要
- 从 2025 年 4 月 1 日开始,在基于代理的混合辅助角色上运行的所有作业都将停止。
- Azure 自动化基于代理的用户混合 Runbook 辅助角色(Windows 和 Linux)已于 2024 年 8 月 31 日停用,不再受支持。 请按照有关如何从现有的基于代理的用户混合 Runbook 辅助角色迁移到基于扩展的混合辅助角色的指南进行操作。
注意
Azure 自动化运行方式帐户已于 2023 年 9 月 30 日停用,并已被托管标识取代。 请按照有关如何开始迁移 runbook 以使用托管标识的指南进行操作。 有关详细信息,请参阅从现有运行方式帐户迁移到托管标识。
在混合 Runbook 辅助角色上运行的 Runbook 通常用于管理本地计算机上的资源,或部署了辅助角色的本地环境中的资源。 Azure 自动化中的 runbook 通常管理 Azure 云中的资源。 即使使用方式不同,在 Azure 自动化中运行的 Runbook 和在混合 Runbook 辅助角色上运行的 Runbook 结构上是相同的。
创建 Runbook 以在混合 Runbook 辅助角色上运行时,应当在承载辅助角色的计算机内编辑并测试 Runbook。 主机具有管理本地资源时所需的所有 PowerShell 模块和网络访问权限。 在混合 Runbook 辅助角色计算机上测试 Runbook 后,可以将它上传到 Azure 自动化环境,用于在混合辅助角色中运行。
规划受防火墙保护的 Azure 服务
在 Azure 存储、Azure Key Vault 或 Azure SQL 上启用 Azure 防火墙时,会阻止从 Azure 自动化 runbook 进行的针对这些服务的访问。 即使启用了允许受信任 Microsoft 服务的防火墙例外,访问也将被阻止,因为自动化不是受信任服务列表的一部分。 启用防火墙后,只能使用混合 Runbook 辅助角色和虚拟网络服务终结点进行访问。
计划 Runbook 作业行为
Azure 自动化处理混合 Runbook 辅助角色上的作业的方式不同于处理云沙盒中运行的作业的方式。 对于长时间运行的 runbook,请确保它能在重启后复原。 有关作业行为的详细信息,请参阅混合 Runbook 辅助角色作业。
服务帐户
Windows 混合辅助角色
混合 Runbook 辅助角色的作业在本地系统帐户下运行。
注意
- 基于扩展的 Runbook 和基于代理的 Windows Hybrid Runbook Workers 都支持 PowerShell 5.1、PowerShell 7.1(预览版)、Python 2.7 和 Python 3.8 Runbooks。 对于基于代理的辅助角色,请确保 Windows 混合辅助角色版本为 7.3.12960 或更高。
基于扩展的混合工作者
注意
若要在 Windows 系统中创建环境变量,请执行以下步骤:
- 转到“控制面板”>“系统”>“高级系统设置”。
- 在“系统属性”中选择“环境变量”。
- 在“系统变量”中选择“新建”。
- 提供变量名称和变量值,然后选择“确定”。
- 重启 VM,或者从当前用户注销再登录,以实施环境变量的更改。
PowerShell 7.1
若要在 Windows 混合辅助角色上运行 PowerShell 7.1 Runbook,请在混合辅助角色上安装 PowerShell。 请参阅在 Windows 上安装 PowerShell。 确保将 PowerShell 文件添加到 PATH 环境变量,并在安装后重启混合 Runbook 辅助角色。
Python 3.8
若要在 Windows 混合辅助角色上运行 Python 3.8 Runbook,请在混合辅助角色上安装 Python。 请参阅在 Windows 上安装 Python。 为 Python 3.8 Runbook 创建环境变量 PYTHON_3_PATH,并确保将 Python 可执行文件的位置添加为变量值。 成功创建环境变量后,重启混合 Runbook 辅助角色。
如果 Python 可执行文件位于默认位置 C:\WPy64-3800\python-3.8.0.amd64\python.exe,则无需创建环境变量。
Python 2.7
若要在 Windows 混合辅助角色上运行 Python 2.7 Runbook,请在混合辅助角色上安装 Python。 请参阅在 Windows 上安装 Python。 为 Python 2.7 Runbook 创建环境变量 PYTHON_2_PATH,并确保将 Python 可执行文件的位置添加为变量值。 成功创建环境变量后,重启混合 Runbook 辅助角色。
如果 Python 可执行文件位于默认位置 C:\Python27\python.exe,则无需创建环境变量。
PowerShell 7.1
若要在 Windows 混合辅助角色上运行 PowerShell 7.1 Runbook,请在混合辅助角色上安装 PowerShell。 请参阅 在 Windows 上安装 PowerShell。 确保将 PowerShell 文件添加到 PATH 环境变量,并在安装后重启混合 Runbook 辅助角色。
Python 3.8
若要在 Windows 混合辅助角色上运行 Python 3.8 Runbook,请在混合辅助角色上安装 Python。 请参阅 在 Windows 上安装 Python。 为 Python 3.8 Runbook 创建环境变量 PYTHON_3_PATH,并确保将 Python 可执行文件的位置添加为变量值。 成功创建环境变量后,重启混合 Runbook 辅助角色。
如果 Python 可执行文件位于默认位置 C:\WPy64-3800\python-3.8.0.amd64\python.exe,则无需创建环境变量。
Python 2.7
若要在 Windows 混合辅助角色上运行 Python 2.7 Runbook,请在混合辅助角色上安装 Python。 请参阅 在 Windows 上安装 Python。 为 Python 2.7 Runbook 创建环境变量 PYTHON_2_PATH,并确保将 Python 可执行文件的位置添加为变量值。 成功创建环境变量后,重启混合 Runbook 辅助角色。
如果 Python 可执行文件位于默认位置 C:\Python27\python.exe,则无需创建环境变量。
Linux 混合辅助角色
注意
- 基于扩展和基于代理的 Linux 混合 Runbook 工作器均支持 PowerShell 5.1、PowerShell 7.1(预览版)、Python 2.7、Python 3.8 的 Runbook。 对于基于代理的辅助角色,请确保 Linux 混合 Runbook 辅助角色版本为 1.7.5.0 或更高。
基于扩展的混合工作者
注意
若要在 Linux 系统中创建环境变量,请执行以下步骤:
- 打开 /etc/environment。
- 通过在 /etc/environment 的新行中添加 VARIABLE_NAME="variable_value" 来创建新的环境变量(VARIABLE_NAME 是新环境变量的名称,variable_value 表示要分配的值)。
- 保存对 /etc/environment 的更改后,重启 VM,或者从当前用户注销再登录,以实施环境变量的更改。
Python 3.8
若要在 Linux 混合辅助角色上运行 Python 3.8 Runbook,请在混合辅助角色上安装 Python。 确保将 Python 可执行文件添加到 PATH 环境变量,并在安装后重启混合 Runbook 辅助角色。
Python 2.7
若要在 Linux 混合辅助角色上运行 Python 2.7 Runbook,请在混合辅助角色上安装 Python。 确保将 Python 可执行文件添加到 PATH 环境变量,并在安装后重启混合 Runbook 辅助角色。
配置 runbook 权限
通过以下方式定义 Runbook 的权限以在混合 Runbook 辅助角色上运行:
- 让 Runbook 向本地资源提供自己的身份验证。
- 配置使用 Azure 资源托管标识进行身份验证。
- 指定混合辅助角色凭据,为所有 Runbook 提供用户上下文。
对本地资源使用 Runbook 身份验证
如果准备向资源提供其身份验证的 Runbook,请在 Runbook 中使用凭据和证书资产。 可以通过多个 cmdlet 来指定凭据,以便 Runbook 可以对不同资源进行身份验证。 下面的示例显示了用于重新启动计算机的 Runbook 的一部分。 它从凭据资产检索凭据,从变量资产检索计算机的名称,并将这些值用于 Restart-Computer cmdlet。
$Cred = Get-AutomationPSCredential -Name "MyCredential"
$Computer = Get-AutomationVariable -Name "ComputerName"
Restart-Computer -ComputerName $Computer -Credential $Cred
还可以使用 InlineScript 活动。
InlineScript 允许你在具有凭据的另一台计算机上运行代码块。
将 Runbook 身份验证与托管标识结合使用
Azure 虚拟机上的混合 Runbook 辅助角色可以使用托管标识来向 Azure 资源进行身份验证。 使用 Azure 资源的托管标识(而不是运行方式帐户)有一些好处,因为无需执行以下操作:
- 导出运行方式证书,再将其导入到混合 Runbook 辅助角色。
- 续订运行方式帐户使用的证书。
- 在 Runbook 代码中处理运行方式连接对象。
可通过两种方法在混合 Runbook 辅助角色脚本中使用托管标识。
为自动化帐户使用系统分配的托管标识:
为自动化帐户配置系统分配的托管标识。
向此标识授予在订阅中执行其任务所需的权限。
更新 Runbook,将 Connect-AzAccount cmdlet 与
Identity参数一起使用,以便对 Azure 资源进行身份验证。 此配置减少了使用运行方式帐户以及执行关联帐户管理的需求。# Ensures you do not inherit an AzContext in your runbook Disable-AzContextAutosave -Scope Process # Connect to Azure with system-assigned managed identity $AzureContext = (Connect-AzAccount -Environment AzureChinaCloud -Identity).context # set and store context $AzureContext = Set-AzContext -SubscriptionName $AzureContext.Subscription -DefaultProfile $AzureContext # Get all VM names from the subscription Get-AzVM -DefaultProfile $AzureContext | Select Name
注意
不能在混合 Runbook 辅助角色上使用自动化帐户的用户托管标识,它必须是自动化帐户的系统托管标识。
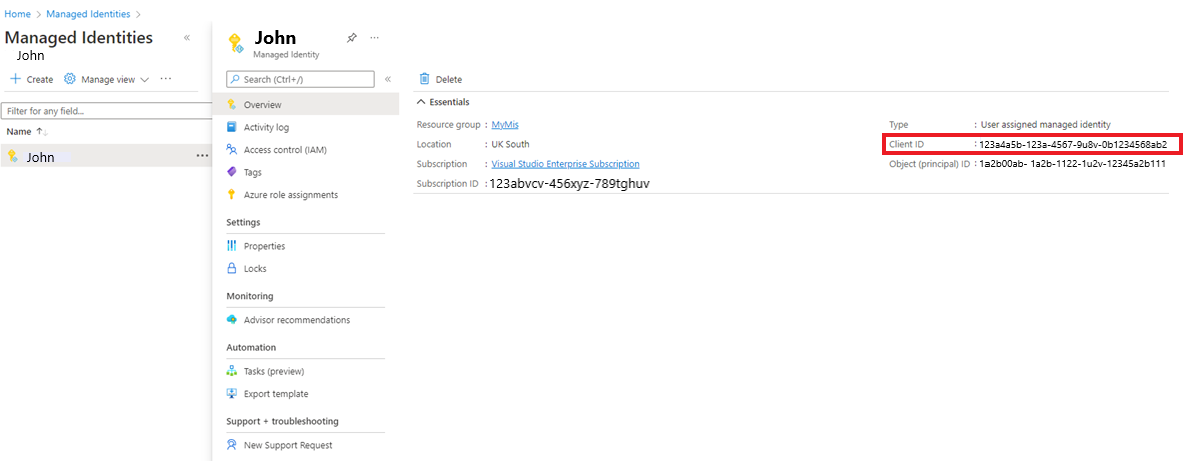
对于作为混合 Runbook 辅助角色运行的 Azure VM,请使用 VM 托管标识。 在这种情况下,可以使用 VM 的用户分配托管标识 或 VM 的系统分配托管标识。
注意
这不适用于已配置了自动化帐户托管标识的自动化帐户。 一旦启用自动化帐户托管标识,便无法再使用 VM 托管标识,然后,只能使用自动化帐户的系统分配托管标识,如上面的选项 1 中所述。
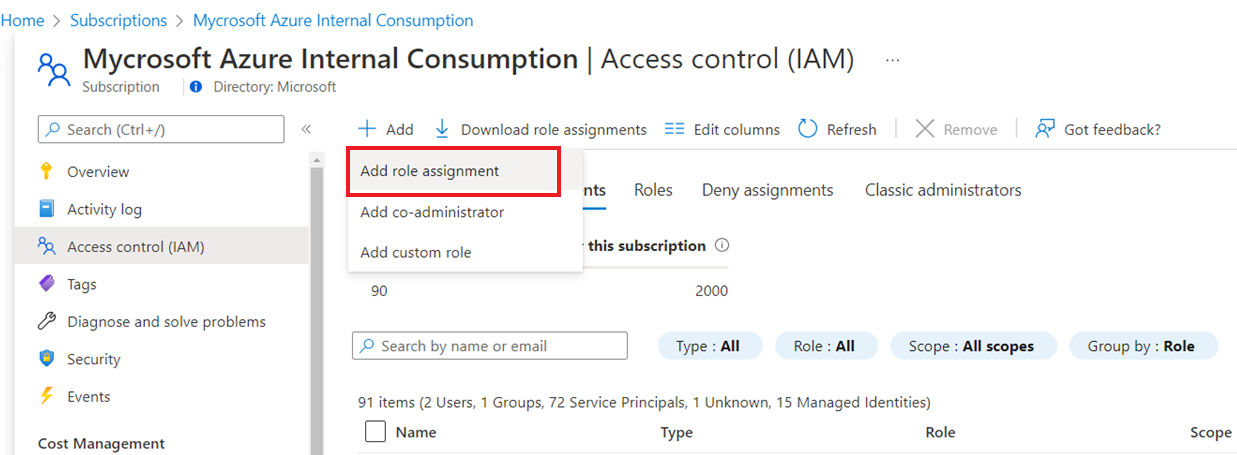
使用以下任一托管标识:
- 为 VM 配置系统托管标识。
- 向此标识授予在订阅中执行其任务所需的权限。
- 更新 Runbook,将 Connect-Az-Account cmdlet 与
Identity参数一起使用,以便向 Azure 资源进行身份验证。 此配置减少了使用运行方式帐户以及执行关联帐户管理的需求。
# Ensures you do not inherit an AzContext in your runbook Disable-AzContextAutosave -Scope Process # Connect to Azure with system-assigned managed identity $AzureContext = (Connect-AzAccount -Environment AzureChinaCloud -Identity).context # set and store context $AzureContext = Set-AzContext -SubscriptionName $AzureContext.Subscription -DefaultProfile $AzureContext # Get all VM names from the subscription Get-AzVM -DefaultProfile $AzureContext | Select Name
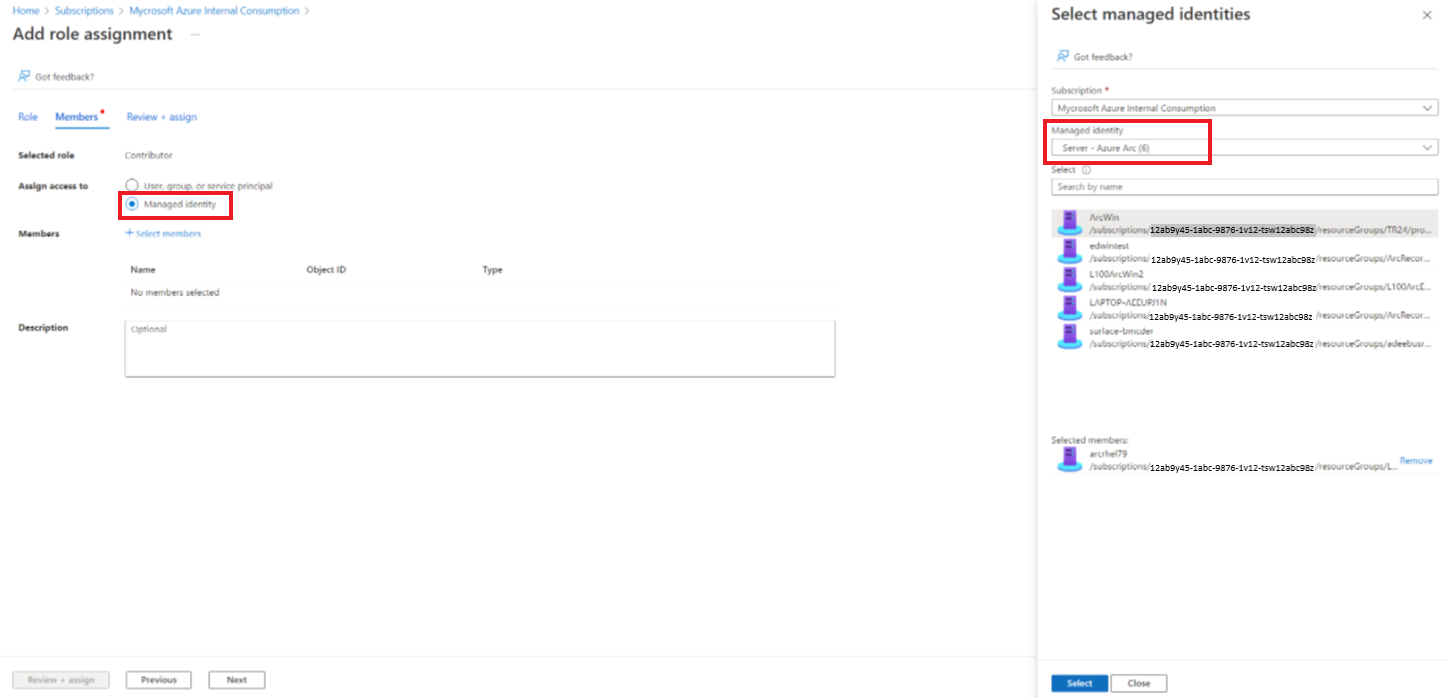
作为混合 Runbook 辅助角色运行的已启用 Arc 的服务器已分配有一个内置的系统托管标识,可以使用该标识进行身份验证。
注意
这不适用于已配置了自动化帐户托管标识的自动化帐户。 一旦启用自动化帐户托管标识,便无法再使用 Arc 托管标识,然后,只能使用自动化帐户的系统分配托管标识,如上面的选项 1 中所述。
注意
在默认情况下,将保存 Azure 上下文以便在 PowerShell 会话之间使用。 如果混合 Runbook 辅助角色上以前某个 Runbook 已向 Azure 进行了身份验证,那么,根据 Azure 上下文和登录凭据 | Microsoft Docs,该上下文就有可能会保留到系统 PowerShell 配置文件中的磁盘。例如,具有 Get-AzVM 的 Runbook 无需调用 Connect-AzAccount -Environment AzureChinaCloud 就可以返回订阅中所有的 VM,并且用户无需在该 Runbook 内进行身份验证就可以访问 Azure 资源。 你可以在 Azure PowerShell 中禁用上下文自动保存,详情请参阅此处。
将 Runbook 身份验证与混合辅助角色凭据配合使用
先决条件
- 应部署混合辅助角色,并且计算机在执行 Runbook 之前应处于运行状态。
混合辅助角色凭据 无需让 Runbook 将自身的身份验证提供给本地资源,可以针对混合 Runbook 辅助角色组指定混合辅助角色凭据。 若要指定混合辅助角色凭据,必须定义有权访问本地资源的凭据资产。 这些资源包括证书存储,所有 Runbook 在组中的混合 Runbook 辅助角色上使用这些凭据运行。
凭据的用户名必须采用以下格式之一:
- 域\用户名
- username@domain
- 用户名(适用于本地计算机的本地帐户)
若要使用 PowerShell runbook Export-RunAsCertificateToHybridWorker,需要在本地计算机上安装适用于 Azure 自动化的 Az 模块。
为混合 Runbook 辅助角色组使用凭据资产
默认情况下,混合作业在系统帐户的上下文下运行。 但是,若要在不同的凭据资产下运行混合作业,请执行以下步骤:
- 创建具有本地资源访问权限的凭据资产。
- 在 Azure 门户中打开 自动化帐户。
- 选择混合辅助角色组,并选择特定组。
- 选择“设置”。
- 将“混合辅助角色凭据”的值从“默认”改为“自定义”。
- 选择凭据,然后选择“ 保存”。
- 如果未为自定义用户分配以下权限,作业可能会暂停。
| 资源类型 | 文件夹权限 |
|---|---|
| Azure VM | C:\Packages\Plugins\Microsoft.Azure.Automation.HybridWorker.HybridWorkerForWindows(读取和执行) |
| 已启用 Arc 的服务器 | C:\ProgramData\AzureConnectedMachineAgent\Tokens(读取) C:\Packages\Plugins\Microsoft.Azure.Automation.HybridWorker.HybridWorkerForWindows(读取和执行) |
注意
Linux 混合辅助角色不支持混合辅助角色凭据。
在混合 Runbook 辅助角色中启动 Runbook
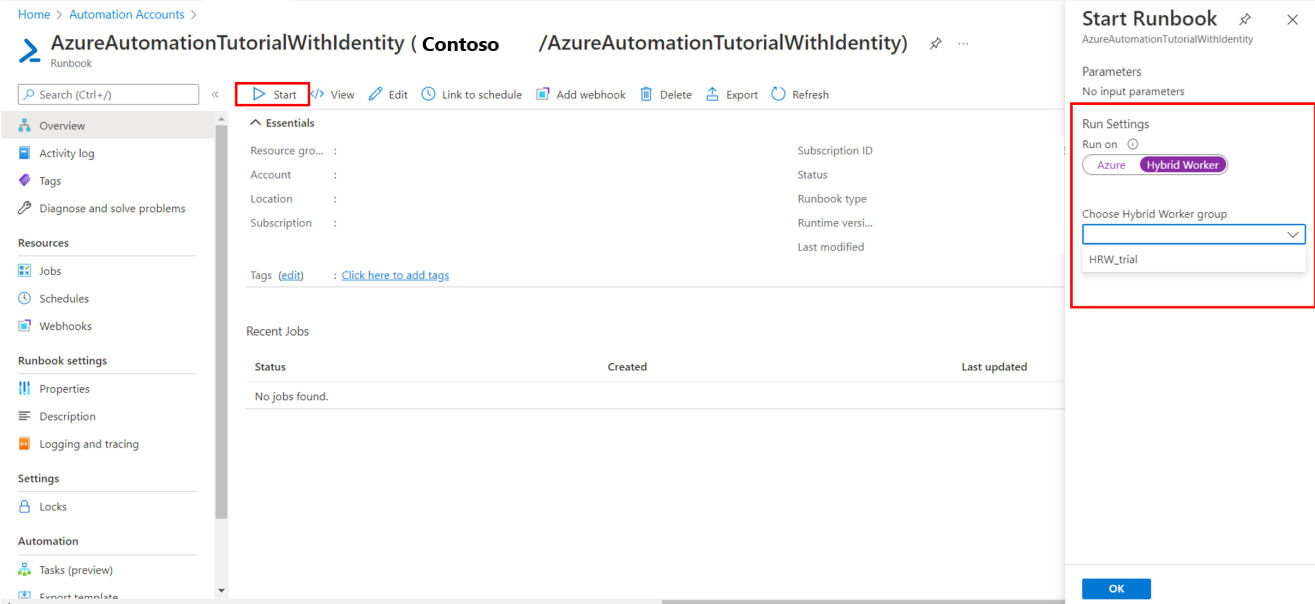
在 Azure 自动化中启动 Runbook 介绍了用于启动 Runbook 的不同方法。 在混合 Runbook 辅助角色上启动 Runbook 的操作将使用“运行位置”选项,该选项允许你指定混合 Runbook 辅助角色组的名称。 指定组时,该组中的其中一个辅助角色检索和运行 Runbook。 如果 Runbook 未指定此选项,Azure 自动化会照常运行 Runbook。
在 Azure 门户中启动 Runbook 时,会看到一个“运行位置”选项,可以在其中选择“Azure”或“混合辅助角色”。 选择“混合辅助角色”,从下拉列表中选择混合 Runbook 辅助角色组。
使用 PowerShell 启动 Runbook 时,请将 RunOn 参数与 Start-AzAutomationRunbook cmdlet 一起使用。 以下示例使用 Windows PowerShell 在名为 MyHybridGroup 的混合 Runbook 辅助角色组中启动名为 Test-Runbook 的 Runbook。
Start-AzAutomationRunbook -AutomationAccountName "MyAutomationAccount" -Name "Test-Runbook" -RunOn "MyHybridGroup"
在 Windows 混合 Runbook 辅助角色上使用已签名 Runbook
你可以将 Windows 混合 Runbook 辅助角色配置为仅运行已签名 Runbook。
重要
将混合 Runbook 辅助角色配置为仅运行已签名 Runbook 后,未签名的 Runbook 将无法在该辅助角色上执行。
注意
PowerShell 7.x 不支持适用于 Windows 和 Linux 混合 Runbook 辅助角色的已签名 runbook。
创建签名证书
以下示例创建可用于对 Runbook 签名的自签名证书。 此代码会创建证书并将其导出,使混合 Runbook 辅助角色以后可以导入它。 还会返回指纹,以备以后用于引用证书。
# Create a self-signed certificate that can be used for code signing
$SigningCert = New-SelfSignedCertificate -CertStoreLocation cert:\LocalMachine\my `
-Subject "CN=contoso.com" `
-KeyAlgorithm RSA `
-KeyLength 2048 `
-Provider "Microsoft Enhanced RSA and AES Cryptographic Provider" `
-KeyExportPolicy Exportable `
-KeyUsage DigitalSignature `
-Type CodeSigningCert
# Export the certificate so that it can be imported to the hybrid workers
Export-Certificate -Cert $SigningCert -FilePath .\hybridworkersigningcertificate.cer
# Import the certificate into the trusted root store so the certificate chain can be validated
Import-Certificate -FilePath .\hybridworkersigningcertificate.cer -CertStoreLocation Cert:\LocalMachine\Root
# Retrieve the thumbprint for later use
$SigningCert.Thumbprint
导入证书并配置辅助角色以进行签名验证
将创建的证书复制到组中的每个混合 Runbook 辅助角色。 运行以下脚本,以导入证书并将辅助角色配置为在 Runbook 上使用签名验证。
# Install the certificate into a location that will be used for validation.
New-Item -Path Cert:\LocalMachine\AutomationHybridStore
Import-Certificate -FilePath .\hybridworkersigningcertificate.cer -CertStoreLocation Cert:\LocalMachine\AutomationHybridStore
# Import the certificate into the trusted root store so the certificate chain can be validated
Import-Certificate -FilePath .\hybridworkersigningcertificate.cer -CertStoreLocation Cert:\LocalMachine\Root
# Configure the hybrid worker to use signature validation on runbooks.
Set-HybridRunbookWorkerSignatureValidation -Enable $true -TrustedCertStoreLocation "Cert:\LocalMachine\AutomationHybridStore"
使用证书对 Runbook 签名
将混合 Runbook 辅助角色配置为仅使用已签名 Runbook 后,必须对要在混合 Runbook 辅助角色上使用的 Runbook 签名。 使用以下示例 PowerShell 代码对这些 Runbook 签名。
$SigningCert = ( Get-ChildItem -Path cert:\LocalMachine\My\<CertificateThumbprint>)
Set-AuthenticodeSignature .\TestRunbook.ps1 -Certificate $SigningCert
对 Runbook 签名后,必须将其导入自动化帐户并与签名块一起发布。 若要了解如何导入 Runbook,请参阅导入 Runbook。
注意
在 runbook 代码(包括注释)中,只能使用明文字符。 使用 á 或 ñ 等带音调符号的字符将导致错误。 Azure 自动化下载代码时,字符将被替换为问号,签名将失败并显示“签名哈希验证失败”消息。
在 Linux 混合 Runbook 辅助角色上使用已签名 Runbook
为了能够使用签名的 Runbook,Linux 混合 Runbook 辅助角色必须在本地计算机上具有 GPG 可执行文件。
重要
将混合 Runbook 辅助角色配置为仅运行已签名 Runbook 后,未签名的 Runbook 将无法在该辅助角色上执行。
你将执行以下步骤来完成此配置:
- 创建 GPG keyring 和密钥对
- 使 keyring 可供混合 Runbook 辅助角色使用
- 验证签名验证是否已打开
- 对 runbook 签名
注意
- PowerShell 7.x 不支持适用于基于代理的 Windows 和基于代理的 Linux 混合 Runbook 辅助角色的已签名 runbook。
- 基于扩展的 Linux 混合辅助角色不支持已签名的 PowerShell 和 Python runbook。
创建 GPG keyring 和密钥对
注意
创建 GPG keyring 和密钥对仅适用于基于代理的混合辅助角色。
若要创建 GPG 密钥环和密钥对,请使用 Hybrid Runbook Worker:
使用 sudo 应用程序以 nxautomation 帐户登录。
sudo su - nxautomation使用 nxautomation 后,以 root 身份生成 GPG 密钥对。 GPG 将引导你完成每个步骤。 必须提供姓名、电子邮件地址、过期时间和密码。 然后等待,直到计算机上有足够的熵用于生成密钥。
sudo gpg --generate-key由于 GPG 目录是使用 sudo 生成的,因此必须以 root 身份使用以下命令将其所有者更改为 nxautomation。
sudo chown -R nxautomation ~/.gnupg
使 keyring 可供混合 Runbook 辅助角色使用
创建 keyring 后,需要使其可供混合 Runbook 辅助角色使用。 修改设置文件 home/nxautomation/state/worker.conf,在该文件的 [worker-optional] 节下添加以下示例代码。
gpg_public_keyring_path = /home/nxautomation/run/.gnupg/pubring.kbx
验证签名验证是否已打开
如果计算机上已禁用签名验证,必须以 root 身份运行以下命令将其启用。 使用工作区 ID 替换 <LogAnalyticsworkspaceId>。
sudo python /opt/microsoft/omsconfig/modules/nxOMSAutomationWorker/DSCResources/MSFT_nxOMSAutomationWorkerResource/automationworker/scripts/require_runbook_signature.py --true <LogAnalyticsworkspaceId>
对 runbook 签名
配置签名验证后,即可使用以下 GPG 命令对 Runbook 签名。
gpg --clear-sign <runbook name>
签名的 runbook 称为 <runbook name>.asc。
已签名 Runbook 现在可上传到 Azure 自动化中,并且可以像常规 Runbook 一样执行。
日志记录
为了协助排查在基于扩展的混合运行簿工作器上运行的运行簿出现的问题,日志存储在本地以下位置:
在 Windows 的
C:\WindowsAzure\Logs\Plugins\Microsoft.Azure.Automation.HybridWorker.HybridWorkerForWindows<version>处获取详细的扩展和作业运行时进程日志记录。 概要 runbook 作业状态事件将写入 Applications and Services Logs/Microsoft-SMA/Operational 事件日志中。在 Linux 上,可以在
/home/hweautomation/run/worker.log和/var/log/azure/Microsoft.Azure.Automation.HybridWorker.HybridWorkerForLinux处找到基于扩展的混合辅助角色日志。
后续步骤
- 有关混合 Runbook 辅助角色的详细信息,请参阅自动化混合 Runbook 辅助角色。
- 如果 Runbook 未成功完成,请查看 Runbook 执行失败相关故障排除指南。
- 有关 PowerShell 的详细信息(包括语言参考和学习模块),请参阅 PowerShell 文档。
- 了解如何通过混合 Runbook 辅助角色使用 Azure Policy 管理 Runbook 执行。
- 有关 PowerShell cmdlet 参考,请参阅 Az.Automation。