通用警报模式对 Azure Monitor 警报通知的使用体验进行了标准化。 过去,活动日志、指标和日志搜索警报都有自己的电子邮件模板和 Webhook 架构。 通用警报架构为所有警报通知提供一个标准化架构。
使用标准化架构有助于最大程度地减少集成数,这可以简化管理和维护集成的过程。 通过此通用架构,可在 Azure 门户和 Azure 移动应用中实现更丰富的警报使用体验。
通用警报架构为以下各项提供一致的结构:
电子邮件模板:使用详细的电子邮件模板一目了然地诊断问题。 嵌入式链接指向门户中的警报实例和受影响的资源,确保你可以快速跳转到修正过程。
JSON 结构:使用一致的 JSON 结构,使用以下方法为所有警报类型生成集成:
- Azure Logic Apps
- Azure Functions
- Azure 自动化 Runbook
注意
- 默认情况下,智能检测警报使用通用架构。 无需为智能检测警报启用通用架构。
通用架构的结构
通用架构在以下部分中包含有关受影响资源和警报原因的信息:
概要:标准化字段,由描述受警报影响的资源和常见警报元数据(如严重性或说明)的所有警报类型使用。
如果要基于资源组等条件将警报实例路由到特定团队,可使用“概要”部分中的字段为所有警报类型提供路由逻辑。 然后,接收警报通知的团队可使用上下文字段进行调查。
警报上下文:根据警报类型而变化的字段。 警报上下文字段描述警报的原因。 例如,指标警报将在警报上下文中包含指标名称和指标值等字段。 活动日志警报将包含有关生成警报的事件的信息。
自定义属性:默认情况下,可以使用自定义属性将警报有效负载中未包含的其他信息包含在警报有效负载中。 自定义属性是一个“键:值”对,可以包含警报规则中配置的任何信息。
示例警报有效负载
{
"schemaId": "azureMonitorCommonAlertSchema",
"data": {
"essentials": {
"alertId": "/subscriptions/<subscription ID>/providers/Microsoft.AlertsManagement/alerts/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e",
"alertRule": "WCUS-R2-Gen2",
"severity": "Sev3",
"signalType": "Metric",
"monitorCondition": "Resolved",
"monitoringService": "Platform",
"alertTargetIDs": [
"/subscriptions/<subscription ID>/resourcegroups/pipelinealertrg/providers/microsoft.compute/virtualmachines/wcus-r2-gen2"
],
"configurationItems": [
"wcus-r2-gen2"
],
"originAlertId": "3f2d4487-b0fc-4125-8bd5-7ad17384221e_PipeLineAlertRG_microsoft.insights_metricAlerts_WCUS-R2-Gen2_-117781227",
"firedDateTime": "2019-03-22T13:58:24.3713213Z",
"resolvedDateTime": "2019-03-22T14:03:16.2246313Z",
"description": "",
"essentialsVersion": "1.0",
"alertContextVersion": "1.0"
},
"alertContext": {
"properties": null,
"conditionType": "SingleResourceMultipleMetricCriteria",
"condition": {
"windowSize": "PT5M",
"allOf": [
{
"metricName": "Percentage CPU",
"metricNamespace": "Microsoft.Compute/virtualMachines",
"operator": "GreaterThan",
"threshold": "25",
"timeAggregation": "Average",
"dimensions": [
{
"name": "ResourceId",
"value": "3efad9dc-3d50-4eac-9c87-8b3fd6f97e4e"
}
],
"metricValue": 7.727
}
]
}
},
"customProperties": {
"Key1": "Value1",
"Key2": "Value2"
}
}
}
有关使用通用架构的示例警报,请参阅示例警报有效负载。
“概要”字段
| 字段 | 说明 |
|---|---|
| alertId | 用于标识警报实例的唯一资源 ID。 |
| 报警规则 | 生成了警报实例的警报规则的名称。 |
| 严重性 | 警报严重性。 可能的值为 Sev0、Sev1、Sev2、Sev3 或 Sev4。 |
| 信号类型 | 标识其上定义了警报规则的信号。 可能的值为 Metric、Log 或 Activity Log。 |
| 监控状态 | 当警报触发时,警报的监视条件设置为“已触发”。 当导致警报触发的基础条件清除时,监视条件设置为“已解决”。 |
| 监控服务 | 生成了警报的监视服务或解决方案。 监视服务确定了警报上下文中的字段。 |
| 警报目标ID | 作为警报的受影响目标的 Azure 资源管理器 ID 的列表。 对于在 Log Analytics 工作区或 Application Insights 实例上定义的日志搜索警报,则为各自的工作区或应用程序。 |
| 配置项 | 警报的受影响资源的列表。 在某些情况下,配置项可能与警报目标不同。 例如,在 Log Analytics 工作区上定义的 metric-for-log 或日志搜索警报中,配置项是发送数据的实际资源,而不是工作区。
configurationItems 字段用于将警报关联到配置管理数据库中的资源。 |
| 原始警报编号 | 警报实例的 ID,由生成警报实例的监视服务生成。 |
| firedDateTime | 警报实例的触发日期和时间,采用协调世界时 (UTC)。 |
| resolvedDateTime | 当警报实例的监视条件设置为“已解决”时的日期和时间 (UTC)。 目前只适用于指标警报。 |
| 描述 | 警报规则中定义的说明。 |
| 警报规则ID | 已生成警报实例的警报规则的 ID。 |
| 资源类型 | 受警报影响的资源类型。 |
| 资源组名称 | 受影响资源的资源组的名称。 |
| essentialsVersion | “基本要素”部分的版本号。 |
| alertContextVersion | “alertContext”部分的版本号。 |
| investigationLink | 用于调查 Azure Monitor 中的警报的链接。 目前需要有限的预览注册。 |
指标警报的警报上下文字段
| 字段 | 说明 |
|---|---|
| 属性 | (可选)由客户定义的属性的集合。 |
| 条件类型 | 为警报规则选择的条件类型:
|
| 条件 | |
| 窗口大小 | 由警报规则分析的时间段。 |
| 所有 | 指示必须满足警报规则中定义的所有条件才能触发警报。 |
| 警报敏感度 | 在具有动态阈值的警报规则中,指示规则的敏感度,或者该值可以偏离上限或下限的偏差程度。 |
| 故障时期 | 在具有动态阈值的警报规则中,如果计算周期数量不满足警报阈值,则将触发警报。 例如,当上次五个计算周期中有三个周期不在警报阈值范围时,可以指示触发警报。 |
| 评估周期数 | 计算的总数。 |
| 最小失败周期警报 | 不符合警报规则条件的最小计算数。 |
| 忽略之前的数据 | (可选)在具有动态阈值的警报规则中,计算阈值的起始日期。 使用此值指示规则不应使用指定日期之前的数据计算动态阈值。 |
| metricName (指标名称) | 将由警报规则监视的指标名称。 |
| metricNamespace | 将由警报规则监视的指标命名空间。 |
| 操作员 | 警报规则的逻辑运算符。 |
| 阈值 | 警报规则中定义的阈值。 对于具有动态阈值的警报规则,此值是经过计算的阈值。 |
| 时间聚合 | 警报规则聚合类型。 |
| 尺寸 | 触发警报的指标维度。 |
| 姓名 | 维度名称。 |
| 价值 | 维度值。 |
| 度量值 | 违反阈值时的指标值。 |
| webTestName | 如果条件类型为 webtest,则为 Webtest 的名称。 |
| 窗口开始时间 | 触发警报的评估窗口的起始时间。 |
| 窗口结束时间 | 触发警报的评估窗口的结束时间。 |
monitoringService = Platform 时,具有静态阈值的示例指标警报
{
"alertContext": {
"properties": null,
"conditionType": "SingleResourceMultipleMetricCriteria",
"condition": {
"windowSize": "PT5M",
"allOf": [
{
"metricName": "Percentage CPU",
"metricNamespace": "Microsoft.Compute/virtualMachines",
"operator": "GreaterThan",
"threshold": "25",
"timeAggregation": "Average",
"dimensions": [
{
"name": "ResourceId",
"value": "3efad9dc-3d50-4eac-9c87-8b3fd6f97e4e"
}
],
"metricValue": 31.1105
}
],
"windowStartTime": "2019-03-22T13:40:03.064Z",
"windowEndTime": "2019-03-22T13:45:03.064Z"
}
}
}
monitoringService = Platform 时,具有动态阈值的示例指标警报
{
"alertContext": {
"properties": null,
"conditionType": "DynamicThresholdCriteria",
"condition": {
"windowSize": "PT5M",
"allOf": [
{
"alertSensitivity": "High",
"failingPeriods": {
"numberOfEvaluationPeriods": 1,
"minFailingPeriodsToAlert": 1
},
"ignoreDataBefore": null,
"metricName": "Egress",
"metricNamespace": "microsoft.storage/storageaccounts",
"operator": "GreaterThan",
"threshold": "47658",
"timeAggregation": "Total",
"dimensions": [],
"metricValue": 50101
}
],
"windowStartTime": "2021-07-20T05:07:26.363Z",
"windowEndTime": "2021-07-20T05:12:26.363Z"
}
}
}
monitoringService = Platform 时,可用性测试的示例指标警报
{
"alertContext": {
"properties": null,
"conditionType": "WebtestLocationAvailabilityCriteria",
"condition": {
"windowSize": "PT5M",
"allOf": [
{
"metricName": "Failed Location",
"metricNamespace": null,
"operator": "GreaterThan",
"threshold": "2",
"timeAggregation": "Sum",
"dimensions": [],
"metricValue": 5,
"webTestName": "myAvailabilityTest-myApplication"
}
],
"windowStartTime": "2019-03-22T13:40:03.064Z",
"windowEndTime": "2019-03-22T13:45:03.064Z"
}
}
}
日志搜索警报的警报上下文字段
注意
启用通用架构时,有效负载中的字段将重置为通用架构字段。 因此,日志搜索警报在通用架构方面具有以下限制:
对于使用具有自定义电子邮件主题和/或 JSON 有效负载的 WebHook 的日志搜索警报,通用架构不受支持,因为通用架构会覆盖自定义配置。
对于使用通用架构的警报,每个警报的大小上限为 256KB。 如果日志搜索警报有效负载包含导致警报超过大小上限的搜索结果,则搜索结果不会嵌入到日志搜索警报有效负载中。 可检查有效负载是否包含带
IncludedSearchResults标志的搜索结果。 如果不包含该搜索结果,请使用LinkToFilteredSearchResultsAPI或LinkToSearchResultsAPI通过 Log Analytics API 访问查询结果。
| 字段 | 说明 |
|---|---|
| SearchQuery | 警报规则中定义的查询。 |
| SearchIntervalStartTimeUtc | 触发警报的评估窗口的起始时间(UTC)。 |
| 搜索区间结束时间Utc | 触发警报的评估窗口的结束时间(UTC)。 |
| 结果计数 | 查询返回的记录数。 根据指标度量规则,数字或记录符合特定维度组合。 |
| 链接至搜索结果 | 指向搜索结果的链接。 |
| 链接到筛选搜索结果的用户界面 | 根据指标度量规则,该链接指向的搜索结果根据维度组合经过了筛选。 |
| LinkToSearchResultsAPI (链接至搜索结果API) | 指向使用 Log Analytics API 得到的查询结果的链接。 |
| 指向过滤搜索结果接口API | 根据指标度量规则,该链接指向的搜索结果根据维度组合经过了筛选。 |
| 搜索间隔持续时间(分钟) | 搜索间隔中的总分钟数。 |
| SearchIntervalInMin (搜索间隔时间,以分钟为单位) | 搜索间隔中的总分钟数。 |
| 阈值 | 警报规则中定义的阈值。 |
| 操作员 | 警报规则中定义的运算符。 |
| ApplicationID | 触发警报的 Application Insights ID。 |
| 维度 | 根据指标度量规则,指标维度可触发警报。 |
| 姓名 | 维度名称。 |
| 价值 | 维度值。 |
| 搜索结果 | 完整的搜索结果。 |
| 表 | 搜索结果中的结果表。 |
| 姓名 | 搜索结果中的表名。 |
| 列 | 表中的列。 |
| 姓名 | 列的名称。 |
| 类型 | 列的类型。 |
| 行 | 表中的行。 |
| 数据源 | 触发警报的数据源。 |
| 资源ID | 受警报影响的资源 ID。 |
| 表 | 查询中包含的响应表(草稿)。 |
| 包含的搜索结果 | 指示有效负载是否应包含结果的标志。 |
| 警报类型 | 警报类型: - 指标度量 - 结果数 |
monitoringService = Log Analytics 时的示例日志搜索警报
{
"alertContext": {
"SearchQuery": "Perf | where ObjectName == \"Processor\" and CounterName == \"% Processor Time\" | summarize AggregatedValue = avg(CounterValue) by bin(TimeGenerated, 5m), Computer",
"SearchIntervalStartTimeUtc": "3/22/2019 1:36:31 PM",
"SearchIntervalEndtimeUtc": "3/22/2019 1:51:31 PM",
"ResultCount": 2,
"LinkToSearchResults": "https://portal.azure.cn/#Analyticsblade/search/index?_timeInterval.intervalEnd=2018-03-26T09%3a10%3a40.0000000Z&_timeInterval.intervalDuration=3600&q=Usage",
"LinkToFilteredSearchResultsUI": "https://portal.azure.cn/#Analyticsblade/search/index?_timeInterval.intervalEnd=2018-03-26T09%3a10%3a40.0000000Z&_timeInterval.intervalDuration=3600&q=Usage",
"LinkToSearchResultsAPI": "https://api.loganalytics.io/v1/workspaces/workspaceID/query?query=Heartbeat×pan=2020-05-07T18%3a11%3a51.0000000Z%2f2020-05-07T18%3a16%3a51.0000000Z",
"LinkToFilteredSearchResultsAPI": "https://api.loganalytics.io/v1/workspaces/workspaceID/query?query=Heartbeat×pan=2020-05-07T18%3a11%3a51.0000000Z%2f2020-05-07T18%3a16%3a51.0000000Z",
"SeverityDescription": "Warning",
"WorkspaceId": "12345a-1234b-123c-123d-12345678e",
"SearchIntervalDurationMin": "15",
"AffectedConfigurationItems": [
"INC-Gen2Alert"
],
"SearchIntervalInMinutes": "15",
"Threshold": 10000,
"Operator": "Less Than",
"Dimensions": [
{
"name": "Computer",
"value": "INC-Gen2Alert"
}
],
"SearchResults": {
"tables": [
{
"name": "PrimaryResult",
"columns": [
{
"name": "$table",
"type": "string"
},
{
"name": "Computer",
"type": "string"
},
{
"name": "TimeGenerated",
"type": "datetime"
}
],
"rows": [
[
"Fabrikam",
"33446677a",
"2018-02-02T15:03:12.18Z"
],
[
"Contoso",
"33445566b",
"2018-02-02T15:16:53.932Z"
]
]
}
],
"dataSources": [
{
"resourceId": "/subscriptions/bbbb1b1b-cc2c-dd3d-ee4e-ffffff5f5f5f/resourcegroups/test/providers/microsoft.operationalinsights/workspaces/test",
"tables": [
"Heartbeat"
]
}
]
},
"IncludedSearchResults": "True",
"AlertType": "Metric measurement"
}
}
monitoringService = Application Insights 时的示例日志搜索警报
{
"alertContext": {
"SearchQuery": "requests | where resultCode == \"500\" | summarize AggregatedValue = Count by bin(Timestamp, 5m), IP",
"SearchIntervalStartTimeUtc": "3/22/2019 1:36:33 PM",
"SearchIntervalEndtimeUtc": "3/22/2019 1:51:33 PM",
"ResultCount": 2,
"LinkToSearchResults": "https://portal.azure.cn/AnalyticsBlade/subscriptions/12345a-1234b-123c-123d-12345678e/?query=search+*+&timeInterval.intervalEnd=2018-03-26T09%3a10%3a40.0000000Z&_timeInterval.intervalDuration=3600&q=Usage",
"LinkToFilteredSearchResultsUI": "https://portal.azure.cn/AnalyticsBlade/subscriptions/12345a-1234b-123c-123d-12345678e/?query=search+*+&timeInterval.intervalEnd=2018-03-26T09%3a10%3a40.0000000Z&_timeInterval.intervalDuration=3600&q=Usage",
"LinkToSearchResultsAPI": "https://api.applicationinsights.io/v1/apps/0MyAppId0/metrics/requests/count",
"LinkToFilteredSearchResultsAPI": "https://api.applicationinsights.io/v1/apps/0MyAppId0/metrics/requests/count",
"SearchIntervalDurationMin": "15",
"SearchIntervalInMinutes": "15",
"Threshold": 10000.0,
"Operator": "Less Than",
"ApplicationId": "00001111-aaaa-2222-bbbb-3333cccc4444",
"Dimensions": [
{
"name": "IP",
"value": "1.1.1.1"
}
],
"SearchResults": {
"tables": [
{
"name": "PrimaryResult",
"columns": [
{
"name": "$table",
"type": "string"
},
{
"name": "Id",
"type": "string"
},
{
"name": "Timestamp",
"type": "datetime"
}
],
"rows": [
[
"Fabrikam",
"33446677a",
"2018-02-02T15:03:12.18Z"
],
[
"Contoso",
"33445566b",
"2018-02-02T15:16:53.932Z"
]
]
}
],
"dataSources": [
{
"resourceId": "/subscriptions/cccc2c2c-dd3d-ee4e-ff5f-aaaaaa6a6a6a/resourcegroups/test/providers/microsoft.operationalinsights/workspaces/test",
"tables": [
"Heartbeat"
]
}
]
},
"IncludedSearchResults": "True",
"AlertType": "Metric measurement"
}
}
monitoringService = Log Alerts V2 时的示例日志搜索警报
注意
API 版本 2020-05-01 中的日志搜索警报规则使用此有效负载类型,该类型仅支持通用架构。 使用此版本时,搜索结果不会嵌入到日志搜索警报有效负载中。 使用维度来提供已触发警报的上下文。 还可以使用 LinkToFilteredSearchResultsAPI 或 LinkToSearchResultsAPI 通过 Log Analytics API 访问查询结果。 如果必须嵌入结果,请使用包含所提供链接的逻辑应用,以生成自定义有效负载。
{
"alertContext": {
"properties": {
"name1": "value1",
"name2": "value2"
},
"conditionType": "LogQueryCriteria",
"condition": {
"windowSize": "PT10M",
"allOf": [
{
"searchQuery": "Heartbeat",
"metricMeasureColumn": "CounterValue",
"targetResourceTypes": "['Microsoft.Compute/virtualMachines']",
"operator": "LowerThan",
"threshold": "1",
"timeAggregation": "Count",
"dimensions": [
{
"name": "Computer",
"value": "TestComputer"
}
],
"metricValue": 0.0,
"failingPeriods": {
"numberOfEvaluationPeriods": 1,
"minFailingPeriodsToAlert": 1
},
"linkToSearchResultsUI": "https://portal.azure.cn#@12345a-1234b-123c-123d-12345678e/blade/Microsoft_Azure_Monitoring_Logs/LogsBlade/source/Alerts.EmailLinks/scope/%7B%22resources%22%3A%5B%7B%22resourceId%22%3A%22%2Fsubscriptions%212345a-1234b-123c-123d-12345678e%2FresourceGroups%2FContoso%2Fproviders%2FMicrosoft.Compute%2FvirtualMachines%2FContoso%22%7D%5D%7D/q/eJzzSE0sKklKTSypUSjPSC1KVQjJzE11T81LLUosSU1RSEotKU9NzdNIAfJKgDIaRgZGBroG5roGliGGxlYmJlbGJnoGEKCpp4dDmSmKMk0A/prettify/1/timespan/2020-07-07T13%3a54%3a34.0000000Z%2f2020-07-09T13%3a54%3a34.0000000Z",
"linkToFilteredSearchResultsUI": "https://portal.azure.cn#@12345a-1234b-123c-123d-12345678e/blade/Microsoft_Azure_Monitoring_Logs/LogsBlade/source/Alerts.EmailLinks/scope/%7B%22resources%22%3A%5B%7B%22resourceId%22%3A%22%2Fsubscriptions%212345a-1234b-123c-123d-12345678e%2FresourceGroups%2FContoso%2Fproviders%2FMicrosoft.Compute%2FvirtualMachines%2FContoso%22%7D%5D%7D/q/eJzzSE0sKklKTSypUSjPSC1KVQjJzE11T81LLUosSU1RSEotKU9NzdNIAfJKgDIaRgZGBroG5roGliGGxlYmJlbGJnoGEKCpp4dDmSmKMk0A/prettify/1/timespan/2020-07-07T13%3a54%3a34.0000000Z%2f2020-07-09T13%3a54%3a34.0000000Z",
"linkToSearchResultsAPI": "https://api.loganalytics.io/v1/subscriptions/12345a-1234b-123c-123d-12345678e/resourceGroups/Contoso/providers/Microsoft.Compute/virtualMachines/Contoso/query?query=Heartbeat%7C%20where%20TimeGenerated%20between%28datetime%282020-07-09T13%3A44%3A34.0000000%29..datetime%282020-07-09T13%3A54%3A34.0000000%29%29×pan=2020-07-07T13%3a54%3a34.0000000Z%2f2020-07-09T13%3a54%3a34.0000000Z",
"linkToFilteredSearchResultsAPI": "https://api.loganalytics.io/v1/subscriptions/12345a-1234b-123c-123d-12345678e/resourceGroups/Contoso/providers/Microsoft.Compute/virtualMachines/Contoso/query?query=Heartbeat%7C%20where%20TimeGenerated%20between%28datetime%282020-07-09T13%3A44%3A34.0000000%29..datetime%282020-07-09T13%3A54%3A34.0000000%29%29×pan=2020-07-07T13%3a54%3a34.0000000Z%2f2020-07-09T13%3a54%3a34.0000000Z"
}
],
"windowStartTime": "2020-07-07T13:54:34Z",
"windowEndTime": "2020-07-09T13:54:34Z"
}
}
}
活动日志警报的警报上下文字段
有关活动日志警报中字段的详细信息,请参阅 Azure 活动日志事件架构。
monitoringService = Activity Log - Administrative 时的示例活动日志警报
{
"alertContext": {
"authorization": {
"action": "Microsoft.Compute/virtualMachines/restart/action",
"scope": "/subscriptions/<subscription ID>/resourceGroups/PipeLineAlertRG/providers/Microsoft.Compute/virtualMachines/WCUS-R2-ActLog"
},
"channels": "Operation",
"claims": "{\"aud\":\"https://management.core.chinacloudapi.cn/\",\"iss\":\"https://sts.chinacloudapi.cn/12345a-1234b-123c-123d-12345678e/\",\"iat\":\"1553260826\",\"nbf\":\"1553260826\",\"exp\":\"1553264726\",\"aio\":\"42JgYNjdt+rr+3j/dx68v018XhuFAwA=\",\"appid\":\"11112222-bbbb-3333-cccc-4444dddd5555\",\"appidacr\":\"2\",\"http://schemas.microsoft.com/identity/claims/identityprovider\":\"https://sts.chinacloudapi.cn/12345a-1234b-123c-123d-12345678e/\",\"http://schemas.microsoft.com/identity/claims/objectidentifier\":\"22223333-cccc-4444-dddd-5555eeee6666\",\"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier\":\"22223333-cccc-4444-dddd-5555eeee6666\",\"http://schemas.microsoft.com/identity/claims/tenantid\":\"12345a-1234b-123c-123d-12345678e\",\"uti\":\"v5wYC9t9ekuA2rkZSVZbAA\",\"ver\":\"1.0\"}",
"caller": "22223333-cccc-4444-dddd-5555eeee6666",
"correlationId": "aaaa0000-bb11-2222-33cc-444444dddddd",
"eventSource": "Administrative",
"eventTimestamp": "2019-03-22T13:56:31.2917159+00:00",
"eventDataId": "161fda7e-1cb4-4bc5-9c90-857c55a8f57b",
"level": "Informational",
"operationName": "Microsoft.Compute/virtualMachines/restart/action",
"operationId": "310db69b-690f-436b-b740-6103ab6b0cba",
"status": "Succeeded",
"subStatus": "",
"submissionTimestamp": "2019-03-22T13:56:54.067593+00:00"
}
}
monitoringService = Activity Log - Policy 时的示例活动日志警报
{
"alertContext": {
"authorization": {
"action": "Microsoft.Resources/checkPolicyCompliance/read",
"scope": "/subscriptions/<GUID>"
},
"channels": "Operation",
"claims": "{\"aud\":\"https://management.chinacloudapi.cn/\",\"iss\":\"https://sts.chinacloudapi.cn/<GUID>/\",\"iat\":\"1566711059\",\"nbf\":\"1566711059\",\"exp\":\"1566740159\",\"aio\":\"42FgYOhynHNw0scy3T/bL71+xLyqEwA=\",\"appid\":\"<GUID>\",\"appidacr\":\"2\",\"http://schemas.microsoft.com/identity/claims/identityprovider\":\"https://sts.chinacloudapi.cn/<GUID>/\",\"http://schemas.microsoft.com/identity/claims/objectidentifier\":\"<GUID>\",\"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier\":\"<GUID>\",\"http://schemas.microsoft.com/identity/claims/tenantid\":\"<GUID>\",\"uti\":\"Miy1GzoAG0Scu_l3m1aIAA\",\"ver\":\"1.0\"}",
"caller": "<GUID>",
"correlationId": "<GUID>",
"eventSource": "Policy",
"eventTimestamp": "2019-08-25T11:11:34.2269098+00:00",
"eventDataId": "<GUID>",
"level": "Warning",
"operationName": "Microsoft.Authorization/policies/audit/action",
"operationId": "<GUID>",
"properties": {
"isComplianceCheck": "True",
"resourceLocation": "chinanorth2",
"ancestors": "<GUID>",
"policies": "[{\"policyDefinitionId\":\"/providers/Microsoft.Authorization/policyDefinitions/<GUID>/\",\"policySetDefinitionId\":\"/providers/Microsoft.Authorization/policySetDefinitions/<GUID>/\",\"policyDefinitionReferenceId\":\"vulnerabilityAssessmentMonitoring\",\"policySetDefinitionName\":\"<GUID>\",\"policyDefinitionName\":\"<GUID>\",\"policyDefinitionEffect\":\"AuditIfNotExists\",\"policyAssignmentId\":\"/subscriptions/<GUID>/providers/Microsoft.Authorization/policyAssignments/SecurityCenterBuiltIn/\",\"policyAssignmentName\":\"SecurityCenterBuiltIn\",\"policyAssignmentScope\":\"/subscriptions/<GUID>\",\"policyAssignmentSku\":{\"name\":\"A1\",\"tier\":\"Standard\"},\"policyAssignmentParameters\":{}}]"
},
"status": "Succeeded",
"subStatus": "",
"submissionTimestamp": "2019-08-25T11:12:46.1557298+00:00"
}
}
monitoringService = Activity Log - Autoscale 时的示例活动日志警报
{
"alertContext": {
"channels": "Admin, Operation",
"claims": "{\"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/spn\":\"Microsoft.Insights/autoscaleSettings\"}",
"caller": "Microsoft.Insights/autoscaleSettings",
"correlationId": "<GUID>",
"eventSource": "Autoscale",
"eventTimestamp": "2019-08-21T16:17:47.1551167+00:00",
"eventDataId": "<GUID>",
"level": "Informational",
"operationName": "Microsoft.Insights/AutoscaleSettings/Scaleup/Action",
"operationId": "<GUID>",
"properties": {
"description": "The autoscale engine attempting to scale resource '/subscriptions/d<GUID>/resourceGroups/testRG/providers/Microsoft.Compute/virtualMachineScaleSets/testVMSS' from 9 instances count to 10 instances count.",
"resourceName": "/subscriptions/<GUID>/resourceGroups/voiceassistancedemo/providers/Microsoft.Compute/virtualMachineScaleSets/alexademo",
"oldInstancesCount": "9",
"newInstancesCount": "10",
"activeAutoscaleProfile": "{\r\n \"Name\": \"Auto created scale condition\",\r\n \"Capacity\": {\r\n \"Minimum\": \"1\",\r\n \"Maximum\": \"10\",\r\n \"Default\": \"1\"\r\n },\r\n \"Rules\": [\r\n {\r\n \"MetricTrigger\": {\r\n \"Name\": \"Percentage CPU\",\r\n \"Namespace\": \"microsoft.compute/virtualmachinescalesets\",\r\n \"Resource\": \"/subscriptions/<GUID>/resourceGroups/testRG/providers/Microsoft.Compute/virtualMachineScaleSets/testVMSS\",\r\n \"ResourceLocation\": \"chinanorth\",\r\n \"TimeGrain\": \"PT1M\",\r\n \"Statistic\": \"Average\",\r\n \"TimeWindow\": \"PT5M\",\r\n \"TimeAggregation\": \"Average\",\r\n \"Operator\": \"GreaterThan\",\r\n \"Threshold\": 0.0,\r\n \"Source\": \"/subscriptions/<GUID>/resourceGroups/testRG/providers/Microsoft.Compute/virtualMachineScaleSets/testVMSS\",\r\n \"MetricType\": \"MDM\",\r\n \"Dimensions\": [],\r\n \"DividePerInstance\": false\r\n },\r\n \"ScaleAction\": {\r\n \"Direction\": \"Increase\",\r\n \"Type\": \"ChangeCount\",\r\n \"Value\": \"1\",\r\n \"Cooldown\": \"PT1M\"\r\n }\r\n }\r\n ]\r\n}",
"lastScaleActionTime": "Wed, 21 Aug 2019 16:17:47 GMT"
},
"status": "Succeeded",
"submissionTimestamp": "2019-08-21T16:17:47.2410185+00:00"
}
}
monitoringService = Activity Log - Security 时的示例活动日志警报
{
"alertContext": {
"channels": "Operation",
"correlationId": "<GUID>",
"eventSource": "Security",
"eventTimestamp": "2019-08-26T08:34:14+00:00",
"eventDataId": "<GUID>",
"level": "Informational",
"operationName": "Microsoft.Security/locations/alerts/activate/action",
"operationId": "<GUID>",
"properties": {
"threatStatus": "Quarantined",
"category": "Virus",
"threatID": "2147519003",
"filePath": "C:\\AlertGeneration\\test.eicar",
"protectionType": "Windows Defender",
"actionTaken": "Blocked",
"resourceType": "Virtual Machine",
"severity": "Low",
"compromisedEntity": "testVM",
"remediationSteps": "[\"No user action is necessary\"]",
"attackedResourceType": "Virtual Machine"
},
"status": "Active",
"submissionTimestamp": "2019-08-26T09:28:58.3019107+00:00"
}
}
monitoringService = ServiceHealth 时的示例活动日志警报
{
"alertContext": {
"authorization": null,
"channels": 1,
"claims": null,
"caller": null,
"correlationId": "bbbb1111-cc22-3333-44dd-555555eeeeee",
"eventSource": "ServiceHealth,
"eventTimestamp": "2019-06-24T11:31:19.0312699+00:00",
"httpRequest": null,
"eventDataId": "<GUID>",
"level": "Informational",
"operationName": "Microsoft.ServiceHealth/maintenance/action",
"operationId": "<GUID>",
"properties": {
"title": "Azure Synapse Analytics Scheduled Maintenance Pending",
"service": "Azure Synapse Analytics",
"region": "China North",
"communication": "<MESSAGE>",
"incidentType": "Maintenance",
"trackingId": "<GUID>",
"impactStartTime": "2019-06-26T04:00:00Z",
"impactMitigationTime": "2019-06-26T12:00:00Z",
"impactedServices": "[{\"ImpactedRegions\":[{\"RegionName\":\"China North\"}],\"ServiceName\":\"Azure Synapse Analytics\"}]",
"impactedServicesTableRows": "<tr>\r\n<td align='center' style='padding: 5px 10px; border-right:1px solid black; border-bottom:1px solid black'>Azure Synapse Analytics</td>\r\n<td align='center' style='padding: 5px 10px; border-bottom:1px solid black'>China North<br></td>\r\n</tr>\r\n",
"defaultLanguageTitle": "Azure Synapse Analytics Scheduled Maintenance Pending",
"defaultLanguageContent": "<MESSAGE>",
"stage": "Planned",
"communicationId": "<GUID>",
"maintenanceId": "<GUID>",
"isHIR": "false",
"version": "0.1.1"
},
"status": "Active",
"subStatus": null,
"submissionTimestamp": "2019-06-24T11:31:31.7147357+00:00",
"ResourceType": null
}
}
monitoringService = ResourceHealth 时的示例活动日志警报
{
"alertContext": {
"channels": "Admin, Operation",
"correlationId": "<GUID>",
"eventSource": "ResourceHealth",
"eventTimestamp": "2019-06-24T15:42:54.074+00:00",
"eventDataId": "<GUID>",
"level": "Informational",
"operationName": "Microsoft.Resourcehealth/healthevent/Activated/action",
"operationId": "<GUID>",
"properties": {
"title": "This virtual machine is stopping and deallocating as requested by an authorized user or process",
"details": null,
"currentHealthStatus": "Unavailable",
"previousHealthStatus": "Available",
"type": "Downtime",
"cause": "UserInitiated"
},
"status": "Active",
"submissionTimestamp": "2019-06-24T15:45:20.4488186+00:00"
}
}
Prometheus 警报的警报上下文字段
有关 Prometheus 警报中字段的详细信息,请参阅适用于 Prometheus 规则组的 Azure Monitor 托管服务。
示例 Prometheus 警报
{
"alertContext": {
"interval": "PT1M",
"expression": "sql_up > 0",
"expressionValue": "0",
"for": "PT2M",
"labels": {
"Environment": "Prod",
"cluster": "myCluster1"
},
"annotations": {
"summary": "alert on SQL availability"
},
"ruleGroup": "/subscriptions/<subscription ID>/resourceGroups/myResourceGroup/providers/Microsoft.AlertsManagement/prometheusRuleGroups/myRuleGroup"
}
}
自定义属性字段
如果生成警报的警报规则包含操作组,则自定义属性可以包含有关警报的其他信息。 自定义属性部分包含添加到 Webhook 通知的“键:值”对象。
如果未在警报规则中设置自定义属性,则字段将为 null。
启用通用警报架构
使用 Azure 门户中的操作组或使用 REST API 启用通用警报架构。 架构是在操作级别定义的。 例如,对于电子邮件操作和 Webhook 操作,必须单独选启用架构。
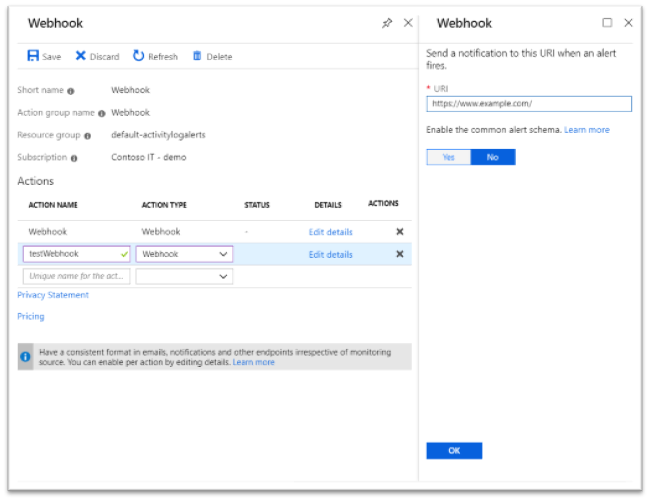
在 Azure 门户中启用通用架构
- 在操作组中打开现有的或新的操作。
- 选择“是”以启用通用警报架构。
使用 REST API 启用通用架构
也可使用操作组 API 来选择加入通用警报架构。 在 创建或更新 REST API 调用中:
- 将“useCommonAlertSchema”标志设置为
true以启用通用架构 - 将“useCommonAlertSchema”标志设置为
false,以对电子邮件、Webhook、逻辑应用、Azure Functions 或自动化 Runbook 操作使用非通用架构。
使用通用架构的示例 REST API 调用
以下创建或更新 REST API 请求:
- 针对电子邮件操作“John Doe 的电子邮件”启用通用警报架构。
- 针对电子邮件操作“Jane Smith 的电子邮件”禁用通用警报架构。
- 针对 Webhook 操作“示例 Webhook”启用通用警报架构。
{
"properties": {
"groupShortName": "sample",
"enabled": true,
"emailReceivers": [
{
"name": "John Doe's email",
"emailAddress": "johndoe@email.com",
"useCommonAlertSchema": true
},
{
"name": "Jane Smith's email",
"emailAddress": "janesmith@email.com",
"useCommonAlertSchema": false
}
],
"smsReceivers": [
{
"name": "John Doe's mobile",
"countryCode": "1",
"phoneNumber": "1234567890"
},
{
"name": "Jane Smith's mobile",
"countryCode": "1",
"phoneNumber": "0987654321"
}
],
"webhookReceivers": [
{
"name": "Sample webhook",
"serviceUri": "http://www.example.com/webhook",
"useCommonAlertSchema": true
}
]
},
"location": "Global",
"tags": {}
}