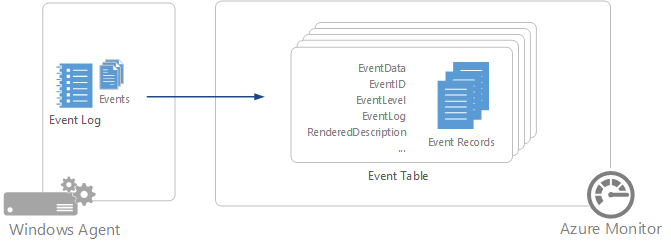
使用 Log Analytics 代理收集 Windows 事件日志数据源
由于许多应用程序都会写入 Windows 事件日志,因此 Windows 事件日志是 Windows 虚拟机上 Log Analytics 代理最常见的数据源之一。 除了由需要监视的应用程序创建的任意自定义日志,还可以从标准日志(如“系统”和“应用程序”)中收集事件。
重要
自 2024 年 8 月 31 日起,旧版 Log Analytics 代理已弃用。 Azure 将不再为 Log Analytics 代理提供任何支持。 如果使用 Log Analytics 代理将数据引入 Azure Monitor,请立即迁移到 Azure Monitor 代理。
配置 Windows 事件日志
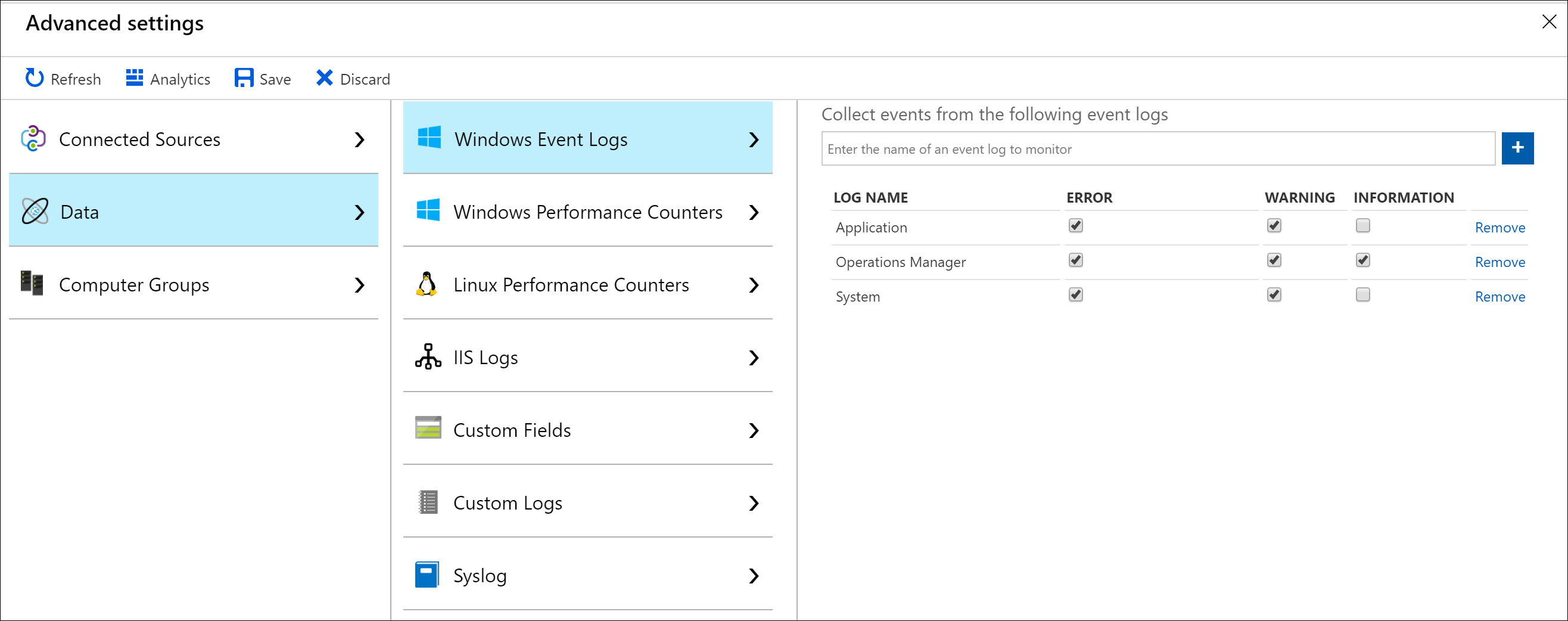
从 Log Analytics 工作区的旧版代理程序管理菜单配置 Windows 事件日志。
Azure Monitor 仅从在设置中指定的 Windows 事件日志收集事件。 可输入日志名称或者选择 + 来添加事件日志。 对于每个日志,仅收集具有所选严重级别的事件。 检查要收集的特定日志的严重级别。 不能向筛选事件提供任何其他条件。
输入事件日志名称时,Azure Monitor 会提供常见事件日志名称的建议。 如果要添加的日志未显示在列表中,仍可以通过输入日志全名添加。 可以使用事件查看器查找日志全名。 在事件查看器中,打开日志的“属性”页面,并从“全名”字段复制字符串。
重要
不能使用 Log Analytics 代理在工作区配置安全事件收集。 必须使用 Microsoft Defender for Cloud 收集安全事件。 Azure Monitor 代理还可用于收集安全事件。
Windows 事件日志中的严重事件在 Azure Monitor 日志中的严重性为“错误”。
数据收集
Azure Monitor 在事件创建时从受监视的事件日志中收集与所选严重级别相匹配的每个事件。 代理会在将其收集到的每个事件日志的位置记录下来。 如果代理在一段时间内处于脱机状态,则它从其上次脱机的位置收集事件,即使这些事件是在代理脱机期间创建的。 如果事件日志在代理脱机时,还有未收集的事件正在被覆盖,则可能无法收集这些事件。
注意
对于其中包含带关键字“经典”或“审核成功”以及 0xa0000000000000 的事件 ID 为 18453 的源 MSSQLSERVER,Azure Monitor 不会从中收集 SQL Server 创建的审核事件。
Windows 事件的记录属性
Windows 事件记录都有一个事件类型,并且具有下表中的属性:
| 属性 | 说明 |
|---|---|
| Computer | 从中收集事件的计算机的名称。 |
| EventCategory | 事件的类别。 |
| EventData | 所有原始格式的事件数据。 |
| EventID | 事件数。 |
| EventLevel | 以数字形式指示的事件严重性。 |
| EventLevelName | 以文本形式指示的事件严重性。 |
| EventLog | 从中收集事件的事件日志名称。 |
| ParameterXml | XML 格式的事件参数值。 |
| ManagementGroupName | System Center Operations Manager 代理的管理组名称。 对于其他代理,该值为 AOI-<workspace ID>。 |
| RenderedDescription | 具有参数值的事件描述。 |
| 源 | 事件源。 |
| SourceSystem | 从中收集事件的代理类型。 OpsManager - Windows 代理,直接连接或由 Operations Manager 托管。 Linux - 所有 Linux 代理。 AzureStorage - Azure 诊断。 |
| TimeGenerated | 在 Windows 中创建事件的日期和时间。 |
| UserName | 记录事件的帐户的用户名。 |
使用 Windows 事件的日志查询
下表提供了检索 Windows 事件记录的不同日志查询的示例。
| 查询 | 说明 |
|---|---|
| 事件 | 所有 Windows 事件。 |
| Event | where EventLevelName == "Error" | 所有 Windows 事件与错误的严重性。 |
| Event | summarize count() by Source | 按源计数 Windows 事件。 |
| Event | where EventLevelName == "Error" | summarize count() by Source | 按源计数 Windows 错误事件。 |