使用 Azure SignalR 服务,可以根据请求类型和网络子集来保护和管理对服务终结点的访问。 配置网络访问控制规则时,只有发出来自指定网络的请求的应用程序才能访问 SignalR 服务。

重要
在网络访问控制规则生效的情况下访问 SignalR 服务的应用程序仍需要在请求中提供适当的授权。
公用网络访问
我们提供单一、统一的开关,以简化公共网络访问的配置。 该开关具有以下选项:
- 已禁用:完全阻止公用网络访问。 对于公用网络,将忽略所有其他网络访问控制规则。
- 启用:允许公共网络访问,该访问进一步受其他网络访问控制规则的监管。
转到要保护的 SignalR 服务实例。
从左侧菜单中选择“网络”。 选择“公共访问”选项卡:
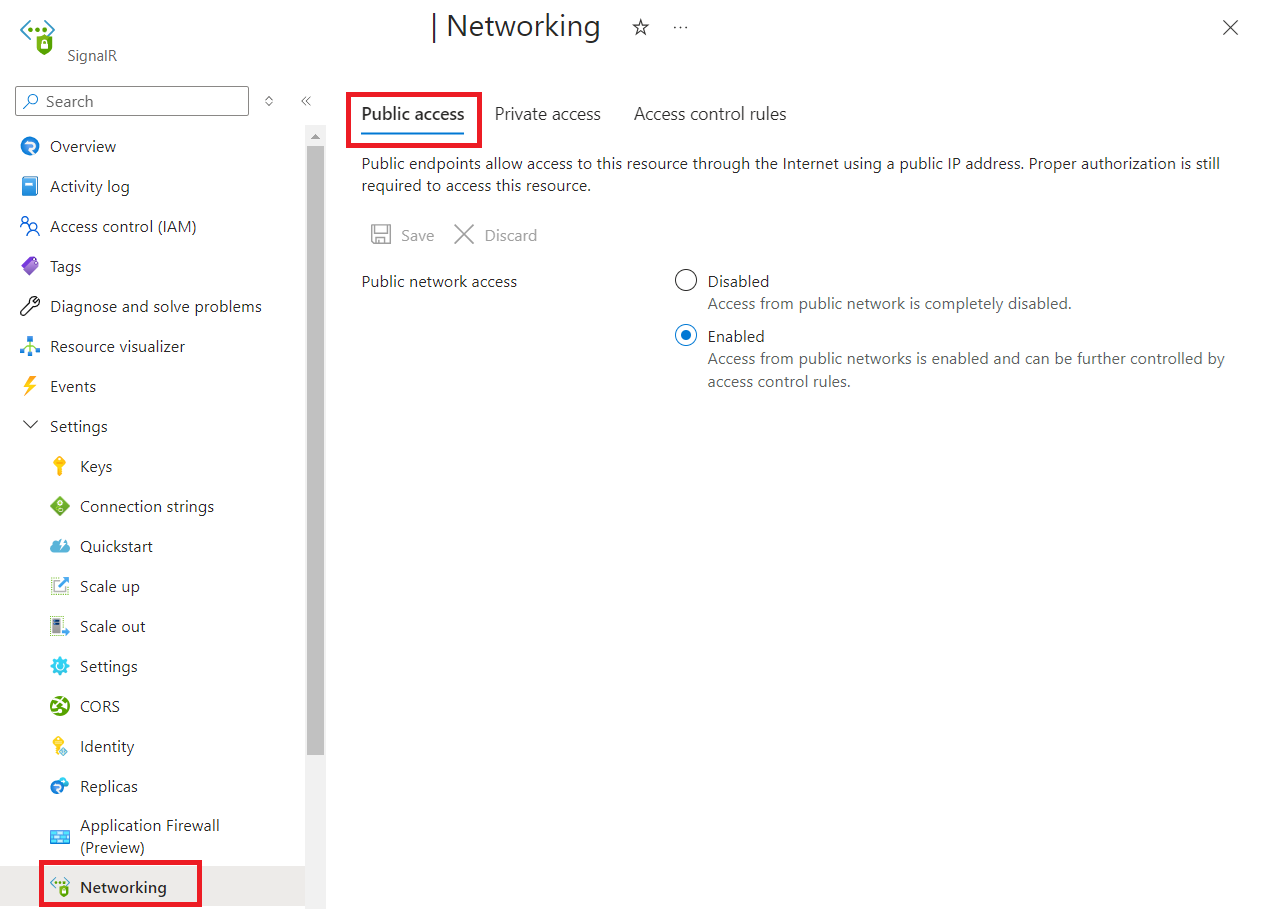
选择“已禁用”或“已启用”。
单击“保存”应用所做的更改。
以下模板禁用公用网络访问:
resource signalr 'Microsoft.SignalRService/SignalR@2024-08-01-preview' = {
name: 'foobar'
location: 'chinanorth3'
properties: {
publicNetworkAccess: 'Disabled'
}
}
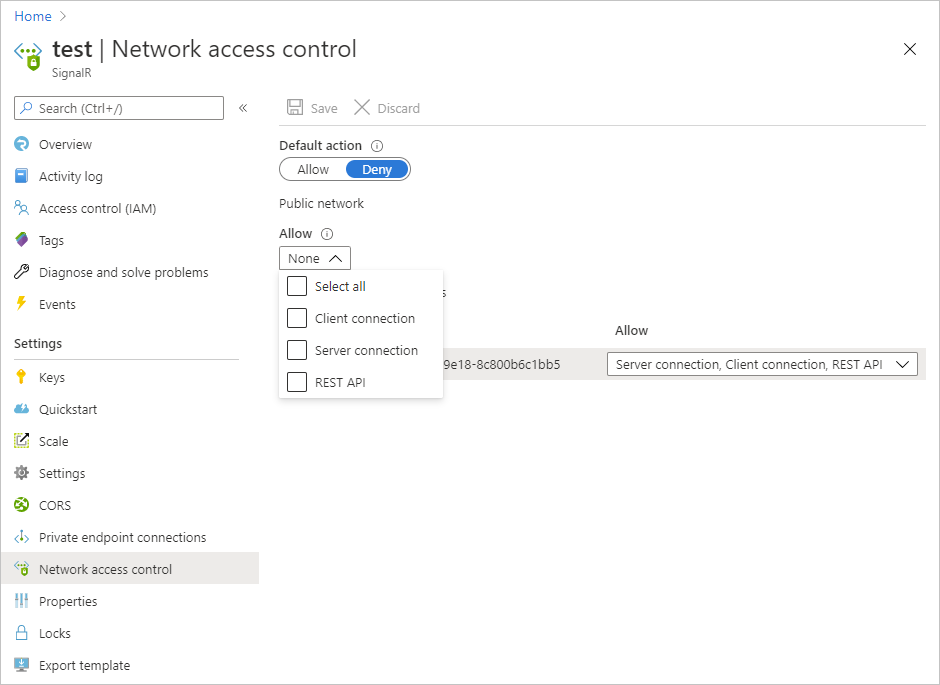
默认操作
如果没有其他规则匹配,则应用默认操作。
转到要保护的 SignalR 服务实例。
在左侧菜单中选择“网络访问控制”。
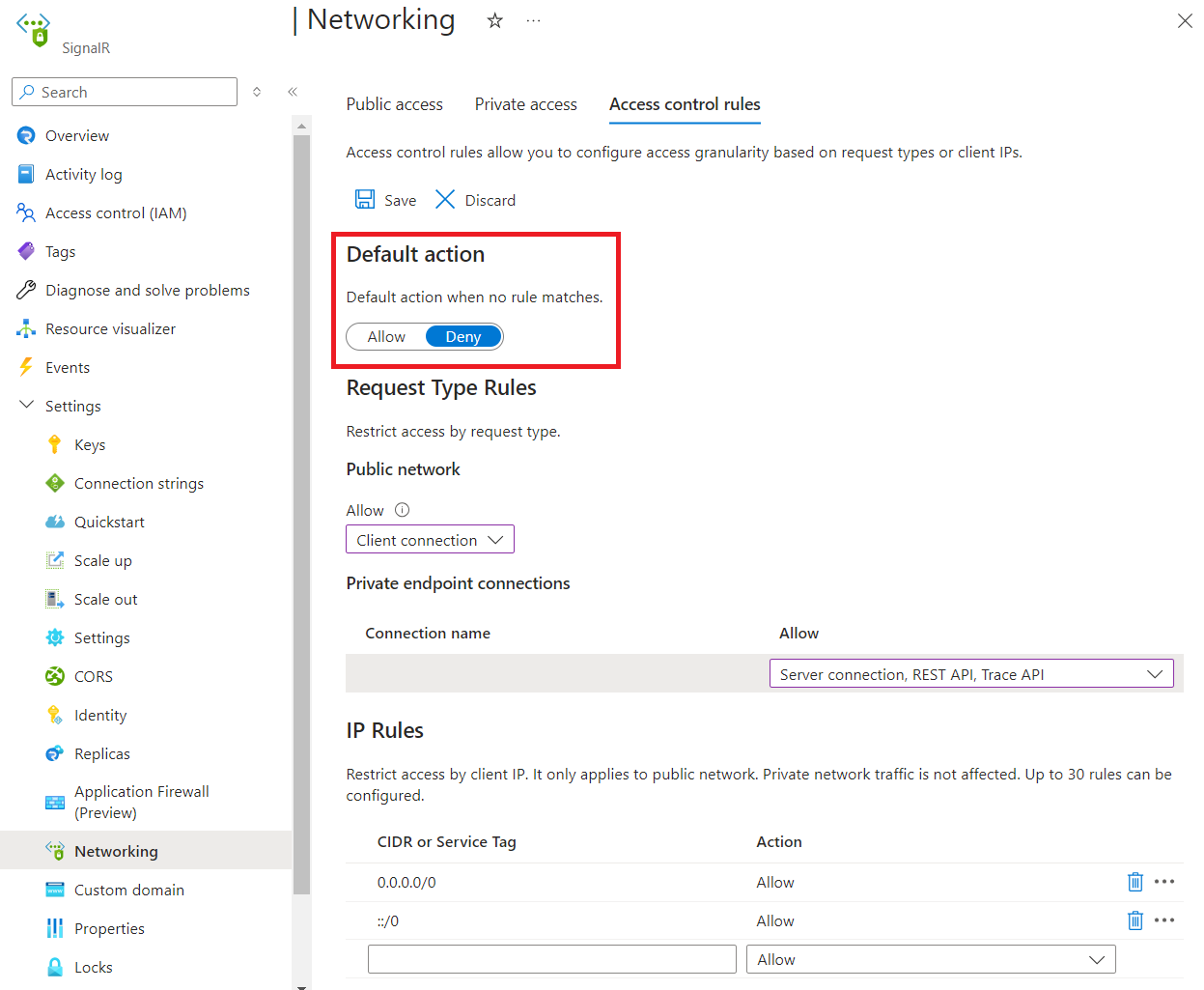
要编辑默认操作,请切换“允许/拒绝”按钮。
单击“保存”应用所做的更改。
以下模板将默认操作设置为 Deny。
resource signalr 'Microsoft.SignalRService/SignalR@2024-08-01-preview' = {
name: 'foobar'
location: 'chinanorth3'
properties: {
networkACLs: {
defaultAction: 'Deny'
}
}
请求类型规则
可以配置规则,以允许或拒绝公共网络和每个专用终结点的指定请求类型。
例如,服务器连接通常是高权限。 为了增强安全性,可能需要限制其来源。 可以配置规则以阻止来自公用网络的所有服务器连接,并且仅允许它们源自特定虚拟网络。
如果没有规则匹配,则应用默认操作。
转到要保护的 SignalR 服务实例。
在左侧菜单中选择“网络访问控制”。
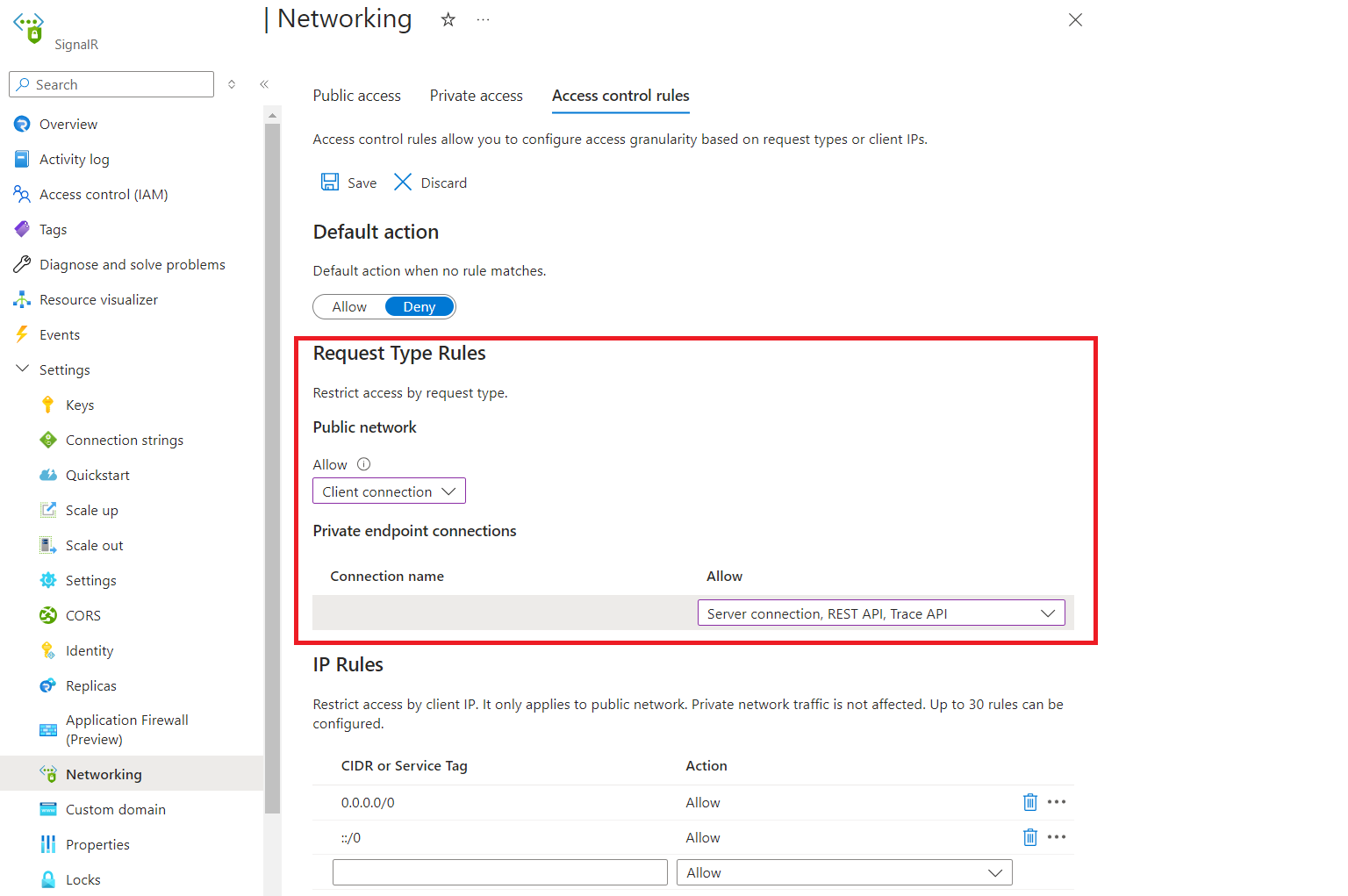
要编辑公用网络规则,请在“公用网络”下选择允许的请求类型。
要编辑专用终结点网络规则,请在“专用终结点连接”下的每行中选择允许的请求类型。
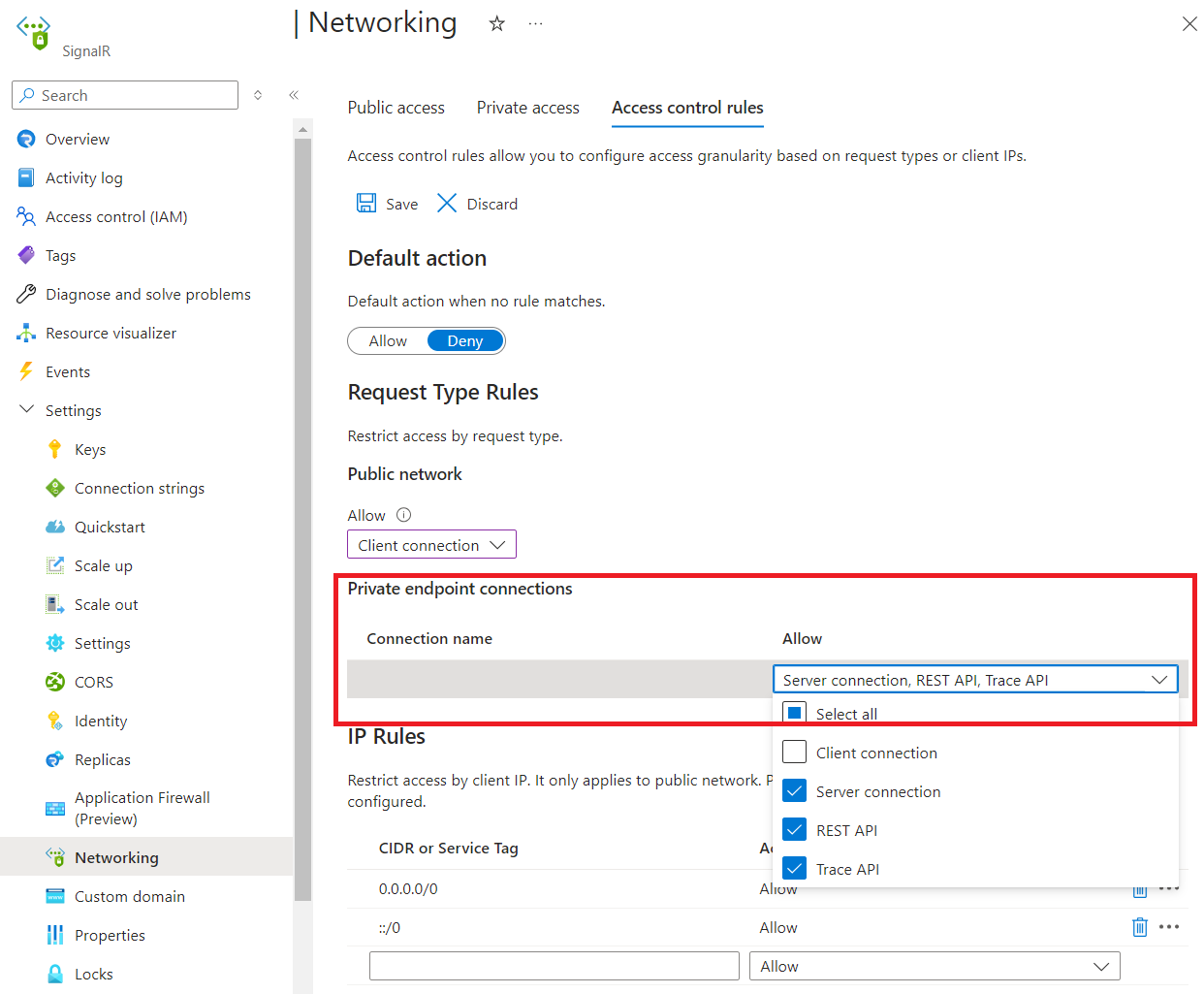
单击“保存”应用所做的更改。
以下模板拒绝来自公共网络的所有请求,但客户端连接除外。 此外,它还仅允许来自特定专用终结点的服务器连接、REST API 调用跟踪调用。
可以在 privateEndpointConnections 子资源中检查专用终结点连接的名称。 它由系统自动生成。
resource signalr 'Microsoft.SignalRService/SignalR@2024-08-01-preview' = {
name: 'foobar'
location: 'chinanorth3'
properties: {
networkACLs: {
defaultAction: 'Deny'
publicNetwork: {
allow: ['ClientConnection']
}
privateEndpoints: [
{
name: 'foo.0000aaaa-11bb-cccc-dd22-eeeeee333333'
allow: ['ServerConnection', 'RESTAPI', 'Trace']
}
]
}
}
IP 规则
IP 规则允许你授予或拒绝对特定公共 Internet IP 地址范围的访问权限。 这些规则可用于允许访问某些基于 Internet 的服务和本地网络,并阻止常规 Internet 流量。
存在以下限制:
- 最多可以配置 30 条规则。
- 必须使用 CIDR 表示法指定地址范围,例如
16.17.18.0/24。 支持 IPv4 和 IPv6 地址。
- 根据定义的顺序评估 IP 规则。 如果没有规则匹配,则应用默认操作。
- IP 规则仅适用于公共流量,并且无法阻止来自专用终结点的流量。
转到要保护的 SignalR 服务实例。
从左侧菜单中选择“网络”。 选择“访问控制规则”选项卡:
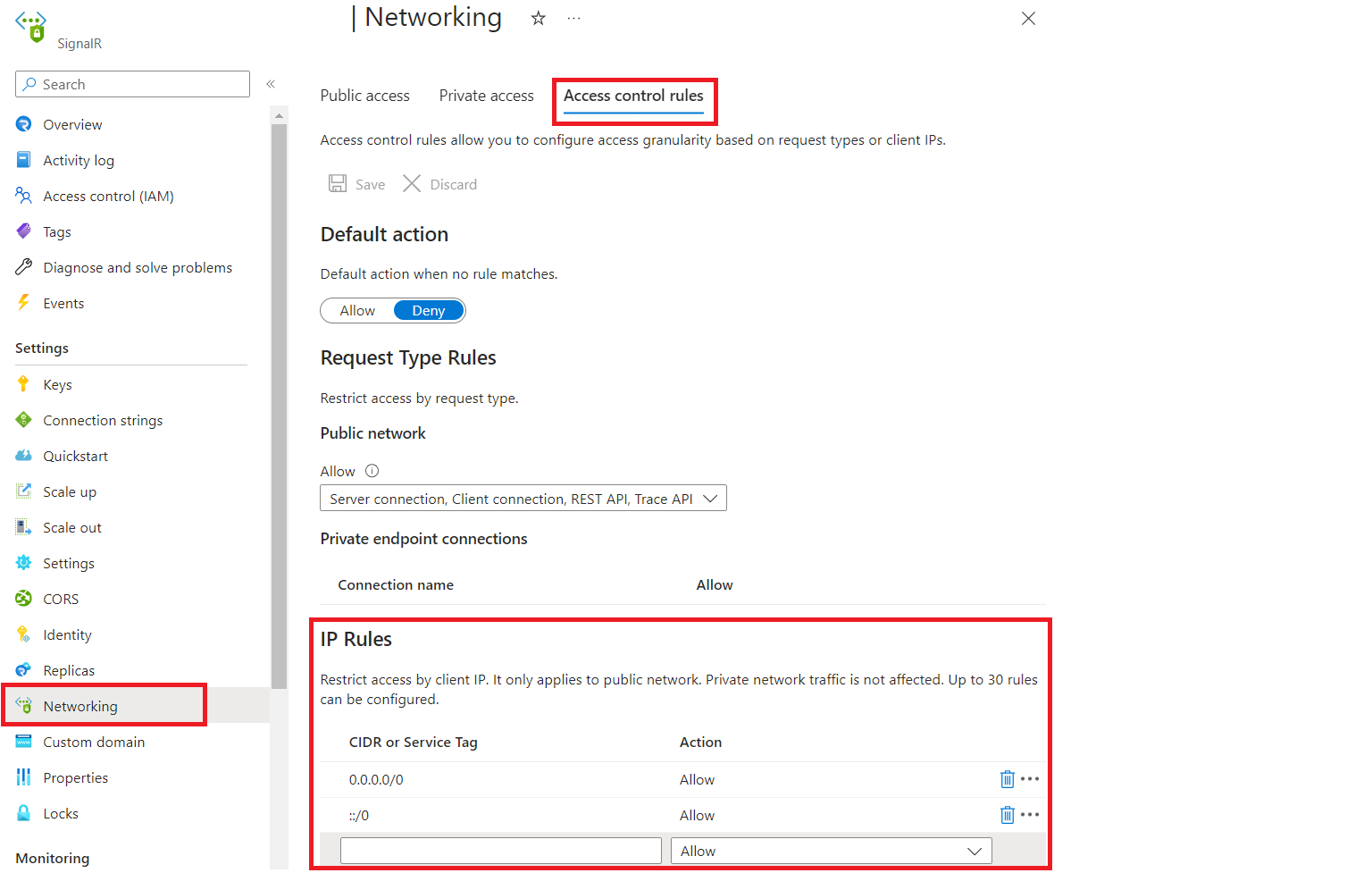
在“IP 规则”部分下编辑列表。
单击“保存”应用所做的更改。
以下模板具有以下效果:
- 允许来自
123.0.0.0/8 和 2603::/8 的请求。
- 来自所有其他 IP 范围的请求被拒绝。
resource signalr 'Microsoft.SignalRService/SignalR@2024-08-01-preview' = {
name: 'foobar'
location: 'chinanorth3'
properties: {
networkACLs: {
defaultAction: 'Deny'
ipRules: [
{
value: '123.0.0.0/8'
action: 'Allow'
}
{
value: '2603::/8'
action: 'Allow'
}
{
value: '0.0.0.0/0'
action: 'Deny'
}
{
value: '::/0'
action: 'Deny'
}
]
}
}
}
后续步骤
详细了解 Azure 专用链接。






