适用于:Azure SQL 数据库
Azure SQL 托管实例
Azure Synapse Analytics
透明数据加密 (TDE) 通过加密静态数据,帮助保护 Azure SQL 数据库、Azure SQL 托管实例和 Azure Synapse Analytics 免受恶意脱机活动的威胁。 它可执行静态数据库、关联备份和事务日志文件的实时加密和解密,无需更改应用程序。 对于所有新部署的 Azure SQL 数据库,默认启用 TDE;对于 Azure SQL 数据库的旧版数据库,必须手动启用 TDE。 对于 Azure SQL 托管实例,在实例级别和新创建的数据库中启用 TDE。 对于 Azure Synapse Analytics,需要手动启用 TDE。
注意
本文适用于 Azure SQL 数据库、Azure SQL 托管实例和 Azure Synapse Analytics(专用 SQL 池 [以前称为 SQL DW])。 有关 Synapse 工作区内专用 SQL 池的透明数据加密的文档,请参阅 Azure Synapse Analytics 加密。
有些被视为客户内容的项(例如,表名、对象名称和索引名称)可能会在日志文件中传输,以供 Azure 提供支持和排查问题。
TDE 对页面级数据执行实时 I/O 加密和解密。 将每个页面读入内存时会将其解密,在写入磁盘之前会将其加密。 TDE 使用称为数据库加密密钥 (DEK) 的对称密钥加密整个数据库的存储。 在数据库启动时,已加密的 DEK 被解密,然后用于解密和重新加密 SQL Server 数据库引擎进程中的数据库文件。 DEK 由 TDE 保护器保护。 TDE 保护器是服务托管的证书(服务托管的透明数据加密)或存储在 Azure Key Vault 中的非对称密钥(客户管理的透明数据加密)。
对于 Azure SQL 数据库和 Azure Synapse,TDE 保护器在服务器级别设置,并由该服务器关联的所有数据库继承。 对于 Azure SQL 托管实例,TDE 保护器是在实例级别设置的,并由该实例上所有加密的数据库继承。 除非另有说明,否则术语“服务器”在整个文档中指的是服务器和实例。
重要
默认情况下,会使用服务托管的透明数据加密将所有新建的 SQL 数据库加密。 如果数据库源经过加密,则通过还原、异地复制和数据库复制创建的目标数据库默认为加密状态。 但是,如果未加密数据库源,则默认情况下不会加密通过 还原、 异地复制和 数据库复制 创建的目标数据库。 在 2017 年 5 月之前创建的现有 SQL 数据库和 2019 年 2 月之前创建的现有 SQL 托管实例数据库默认情况下不会加密。 通过源提供的还原继承加密状态创建的 SQL 托管实例数据库。 若要还原现有的 TDE 加密数据库,必须先将所需的 TDE 证书导入到 SQL 托管实例中。 若要查看某个数据库的加密状态,请在 sys.dm_database_encryption_keys DMV 中执行 SELECT 查询,并检查 列的状态。
注意
TDE 不能用于加密 SQL 数据库和 SQL 托管实例中的系统数据库,例如 master 数据库。
master 数据库包含对用户数据库执行 TDE 操作时所需的对象。 建议不要将任何敏感数据存储在系统数据库中。 例外是 tempdb,它始终由Microsoft拥有的特殊非对称密钥加密。 这是设计使然,并确保临时对象受到保护。
服务托管的透明数据加密
在 Azure 中,TDE 的默认设置是 DEK 受内置服务器证书保护。 内置服务器证书对于每个服务器都是唯一的,使用的加密算法是 AES 256 在密码块链(CBC)模式下。 如果某个数据库存在异地复制关系,则主数据库和异地辅助数据库将受主数据库的父服务器密钥保护。 如果两个数据库连接到同一个服务器,则它们也共享相同的内置证书。 Azure 每年自动轮换这些证书一次,符合内部安全策略,根密钥受 Azure 内部机密存储的保护。 客户可以在 Azure 信任中心提供的独立第三方审核报告中验证 SQL 数据库和 SQL 托管实例是否符合内部安全策略。
Azure 还可按需无缝移动和管理密钥,以实现异地复制和还原。
客户管理的透明数据加密 - 使用自带密钥
客户管理的 TDE 也称为 TDE 的“创建自己的密钥”(BYOK) 支持。 在此方案中,用于加密 DEK 的 TDE 保护器是客户管理的非对称密钥,该密钥存储在客户自有且自行管理的 Azure Key Vault(Azure 的基于云的外部密钥管理系统)中,并且永远不会离开该密钥保管库。 TDE 保护器可由密钥保管库生成。 需要向 SQL 数据库、SQL 托管实例和 Azure Synapse 授予对客户管理的密钥保管库的权限才能对 DEK 进行解密和加密。 如果撤销了服务器对该密钥保管库的权限,则数据库将无法访问,并且所有数据都是加密的。
使用集成了 Azure Key Vault 的 TDE,用户可以控制密钥管理任务,包括密钥轮换、密钥保管库权限、密钥备份,以及使用 Azure Key Vault 功能对所有 TDE 保护器启用审核/报告。 Azure Key Vault 提供中央密钥管理,并支持在密钥和数据管理之间分离职责,以帮助满足安全策略的合规性。 若要详细了解 BYOK for Azure SQL 数据库和 Azure Synapse,请参阅 使用客户管理的密钥进行 Azure SQL 透明数据加密。
若要开始将 TDE 与 Azure Key Vault 集成配合使用,请参阅作指南 PowerShell 和 Azure CLI:通过 Azure Key Vault 中的客户管理的密钥启用透明数据加密。
移动受透明数据加密保护的数据库
对于 Azure 中的操作,不需要解密数据库。 源数据库或主数据库上 TDE 的设置均以透明方式继承在目标系统上。 包括的操作涉及到:
- 异地还原
- 自助时间点还原
- 还原已删除的数据库
- 主动异地复制
- 创建数据库副本
- 将备份文件还原到 Azure SQL 托管实例
重要
Azure SQL 托管实例不支持手动 COPY-ONLY 备份由服务管理的 TDE 加密的数据库,因为用于加密的证书不可访问。 使用时间点还原功能将此类型的数据库移动到另一个 SQL 托管实例,或切换为使用客户托管的密钥。
将受 TDE 保护的数据库导出到 BACPAC 文件时,不会加密数据库的导出内容。 如果导入现有空数据库,加密取决于是否在该数据库上启用了 TDE。 如果在导入过程中创建了新数据库,它将使用 Azure SQL 数据库或 Azure SQL 托管实例的逻辑服务器的默认 TDE 设置。
管理透明数据加密
在 Azure 门户中管理 TDE。
若要通过 Azure 门户配置 TDE,必须以 Azure 所有者、参与者或 SQL 安全管理员的身份建立连接。
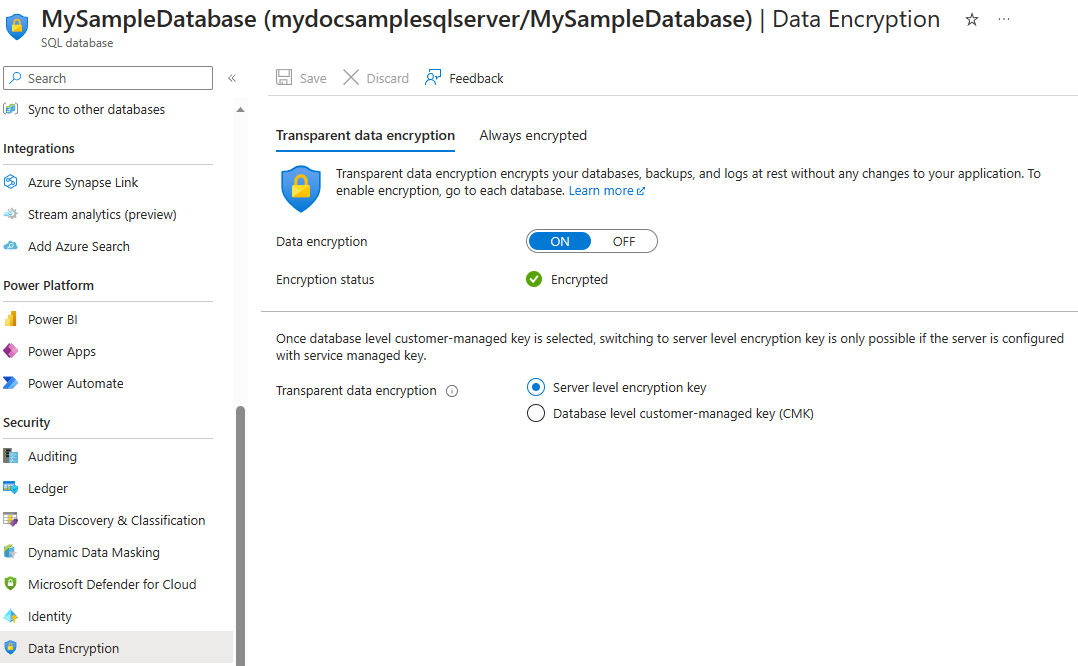
在数据库级别启用和禁用 TDE。 对于 Azure SQL 托管实例,请使用 Transact-SQL (T-SQL) 对数据库启用和禁用 TDE。 对于 Azure SQL 数据库和 Azure Synapse,可在使用 Azure 管理员或参与者帐户登录后,在 Azure 门户网站中管理数据库的 TDE。 在用户数据库下查找 TDE 设置。 默认情况下,使用服务器级别加密密钥。 将为包含数据库的服务器自动生成 TDE 证书。
在服务器级别或实例级别设置 TDE 主密钥(称为 TDE 保护器)。 若要使用支持 BYOK 的 TDE,并使用 Azure Key Vault 中的密钥来保护数据库,请在服务器或托管实例下打开 TDE 设置。
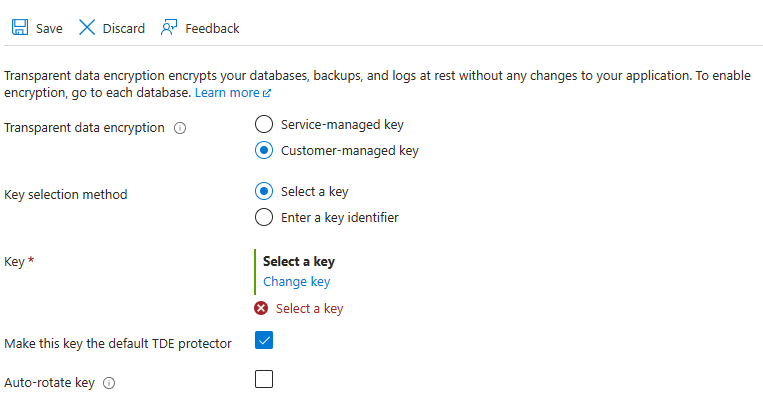
还可以在 Azure SQL 数据库的数据库级别上使用客户管理的 TDE 密钥。 有关详细信息,请参阅在数据库级别使用客户管理的密钥进行透明数据加密 (TDE)。