适用于:Azure Stack HCI 版本 22H2
本文提供了有关如何为 Azure Stack HCI 操作系统配置防火墙的指导。 它包括出站终结点的防火墙要求,以及内部规则和端口。 本文还提供了有关如何将 Azure 服务标记与 Microsoft Defender 防火墙配合使用的信息。
本文还介绍如何选择性地使用高度锁定的防火墙配置来阻止流向所有目标的流量(允许列表中包含的目标除外)。
如果网络使用代理服务器进行 Internet 访问,请参阅为 Azure Stack HCI 配置代理设置。
出站终结点的防火墙要求
在组织的防火墙上为出站网络流量打开端口 80 和 443 可满足 Azure Stack HCI 操作系统与 Azure 和 Microsoft 更新进行连接的连接要求。
Azure Stack HCI 需要定期连接到 Azure 以:
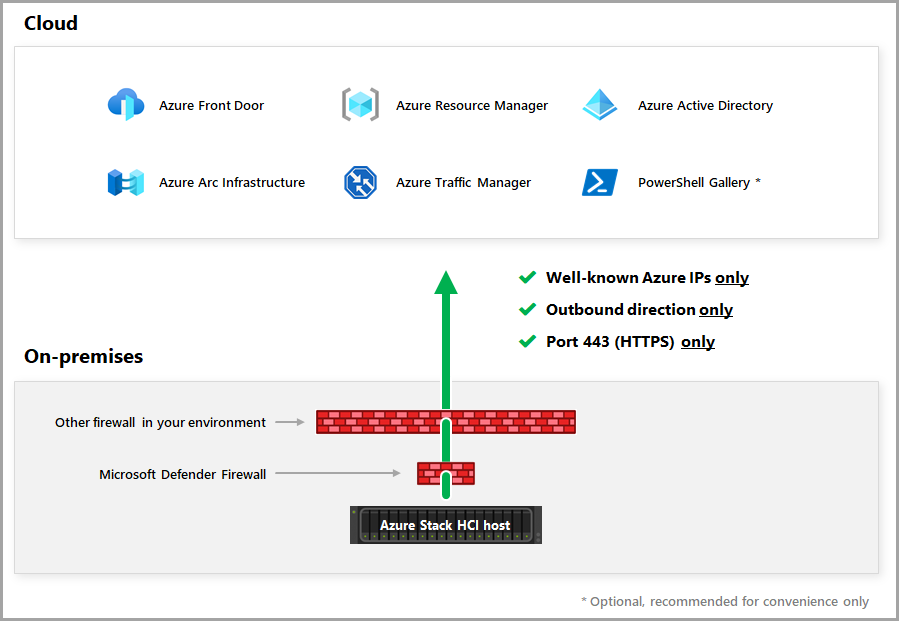
- 众所周知的 Azure IP
- 出站方向
- 端口 80 (HTTP) 和 443 (HTTPS)
重要
Azure Stack HCI 不支持 HTTPS 检查。 确保在 Azure Stack HCI 的网络路径上禁用 HTTPS 检查,以防止出现任何连接错误。
如下图所示,Azure Stack HCI 可能会通过多个防火墙来访问 Azure。
所需的防火墙 URL
下表提供了所需的防火墙 URL 列表。 请确保将这些 URL 包含在允许列表中。
注意
此表中的 Azure Stack HCI 防火墙规则是 HciSvc 系统服务连接所需的最少终结点,不包含通配符。 但是,下表目前包含通配符 URL,这些 URL 将来可能会更新为精确的终结点。
| 服务 | 网址 | 端口 | 说明 |
|---|---|---|---|
| Azure Stack HCI | login.partner.microsoftonline.cn | 443 | 适合 Active Directory,用于身份验证、令牌提取和验证。 |
| Azure Stack HCI | graph.chinacloudapi.cn | 443 | 适合 Graph,用于身份验证、令牌提取和验证。 |
| Azure Stack HCI | management.chinacloudapi.cn | 443 | 适合资源管理器,在群集初始启动到 Azure 来进行注册期间使用并用于取消注册群集。 |
| Azure Stack HCI | dp.stackhci.azure.cn | 443 | 适合推送诊断数据的数据平面,在 Azure 门户管道中使用并用于推送计费数据。 |
| Azure Stack HCI | azurestackhci.azurefd.cn | 443 | 数据平面的上一个 URL。 此 URL 最近已更改。 如果使用这个旧的 URL 注册了群集,则还必须将此 URL 加入允许列表。 |
| 用于服务器的 Arc | aka.ms | 443 | 用于在安装过程中解析下载脚本。 |
| 用于服务器的 Arc | download.microsoft.com | 443 | 用于下载 Windows 安装包。 |
| 用于服务器的 Arc | login.chinacloudapi.cn | 443 | 用于 Microsoft Entra ID |
| 用于服务器的 Arc | login.partner.microsoftonline.cn | 443 | 用于 Microsoft Entra ID |
| 用于服务器的 Arc | pas.chinacloudapi.cn | 443 | 用于 Microsoft Entra ID |
| 用于服务器的 Arc | management.chinacloudapi.cn | 443 | 供 Azure 资源管理器用来创建或删除 Arc 服务器资源 |
| 用于服务器的 Arc | guestnotificationservice.azure.cn | 443 | 用于扩展和连接方案的通知服务 |
| 用于服务器的 Arc | *.his.arc.azure.cn | 443 | 用于元数据和混合标识服务 |
| 用于服务器的 Arc | *.guestconfiguration.azure.cn | 443 | 用于扩展管理和来宾配置服务 |
| 用于服务器的 Arc | *.guestnotificationservice.azure.cn | 443 | 用于扩展和连接方案的通知服务 |
| 用于服务器的 Arc | azgn*.servicebus.chinacloudapi.cn | 443 | 用于扩展和连接方案的通知服务 |
| 用于服务器的 Arc | *.servicebus.chinacloudapi.cn | 443 | 用于 Windows Admin Center 和 SSH 应用场景 |
| 用于服务器的 Arc | *.waconazure.com | 443 | 用于 Windows Admin Center 连接 |
| 用于服务器的 Arc | *.blob.core.chinacloudapi.cn | 443 | 用于已启用 Azure Arc 的服务器扩展的下载源 |
有关所有防火墙 URL 的完整列表,请下载防火墙 URL 电子表格。
建议的防火墙 URL
下表提供了建议的防火墙 URL 列表。 如果出站防火墙受到限制,建议将本部分中所述的 URL 和端口添加到允许列表中。
注意
Azure Stack HCI 防火墙规则是 HciSvc 系统服务连接所需的最少终结点,不包含通配符。 但是,下表目前包含通配符 URL,这些 URL 将来可能会更新为精确的终结点。
| 服务 | 网址 | 端口 | 说明 |
|---|---|---|---|
| Azure Stack HCI 上的 Azure 权益 | crl3.digicert.com | 80 | 使 Azure Stack HCI 上的平台证明服务能够执行证书吊销列表检查,以确保 VM 确实在 Azure 环境中运行。 |
| Azure Stack HCI 上的 Azure 权益 | crl4.digicert.com | 80 | 使 Azure Stack HCI 上的平台证明服务能够执行证书吊销列表检查,以确保 VM 确实在 Azure 环境中运行。 |
| Azure Stack HCI | *.powershellgallery.com | 443 | 获取群集注册所需的 Az.StackHCI PowerShell 模块。 也可从 PowerShell 库手动下载并安装 Az.StackHCI PowerShell 模块。 |
| 群集云见证 | *.blob.core.chinacloudapi.cn | 443 | 用于对 Azure Blob 容器进行的防火墙访问,前提是选择使用云见证作为群集见证(可选)。 |
| Microsoft更新 | windowsupdate.microsoft.com | 80 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
| Microsoft更新 | download.windowsupdate.com | 80 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
| Microsoft更新 | *.download.windowsupdate.com | 80 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
| Microsoft更新 | download.microsoft.com | 443 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
| Microsoft更新 | wustat.windows.com | 80 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
| Microsoft更新 | ntservicepack.microsoft.com | 80 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
| Microsoft更新 | go.microsoft.com | 80 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
| Microsoft更新 | dl.delivery.mp.microsoft.com | 80、443 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
| Microsoft更新 | *.delivery.mp.microsoft.com | 80、443 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
| Microsoft更新 | *.windowsupdate.microsoft.com | 80、443 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
| Microsoft更新 | *.windowsupdate.com | 80 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
| Microsoft更新 | *.update.microsoft.com | 80、443 | 对于 Microsoft 更新,它允许 OS 接收更新。 |
其他 Azure 服务的防火墙要求
根据为 Azure Stack HCI 启用的其他 Azure 服务,可能需要对防火墙配置进行其他更改。 有关每个 Azure 服务的防火墙要求的信息,请参阅以下链接:
- Azure Monitor 代理
- Azure 门户
- Azure Site Recovery
- Azure 虚拟桌面
- Microsoft Defender
- Microsoft Monitoring Agent (MMA) 和 Log Analytics 代理
- Windows 管理中心
- Azure 门户中的 Windows Admin Center
内部规则和端口的防火墙配置要求
对于拉伸群集,请确保站点内和站点间的所有服务器节点之间的相应网络端口处于打开状态(拉伸群集功能仅在 Azure Stack HCI 版本 22H2 中可用)。 你需要适当的防火墙规则,以允许在群集中的所有服务器之间进行 ICMP、SMB(端口 445;如果使用 iWARP RDMA,则还包括适用于 SMB Direct 的端口 5445)和 WS-MAN(端口 5985)双向通信。
使用 Windows Admin Center 中的群集创建向导来创建群集时,向导会针对故障转移群集、Hyper-V 和存储副本自动打开群集中每台服务器上的相应防火墙端口。 如果在每台服务器上使用不同的防火墙,请按照以下部分所述打开端口:
Azure Stack HCI OS 管理
请确保在本地防火墙中配置用于管理 Azure Stack HCI OS(包括许可和计费)的以下防火墙规则。
| 规则 | 行动 | 源 | 目标 | 服务 | 端口 |
|---|---|---|---|---|---|
| 允许进出群集服务器上的 Azure Stack HCI 服务的入站/出站流量 | 允许 | 群集服务器 | 群集服务器 | TCP | 30301 |
Windows 管理中心
确保在 Windows Admin Center 的本地防火墙中配置了以下防火墙规则。
| 规则 | 行动 | 源 | 目标 | 服务 | 端口 |
|---|---|---|---|---|---|
| 提供对 Azure 和 Microsoft 更新的访问权限 | 允许 | Windows 管理中心 | Azure Stack HCI | TCP | 445 |
| 使用 Windows 远程管理 (WinRM) 2.0 以在远程 Windows 服务器上 运行命令 |
允许 | Windows 管理中心 | Azure Stack HCI | TCP | 5985 |
| 对 HTTPS 连接使用 WinRM 2.0, 以在远程 Windows 服务器上运行命令 |
允许 | Windows 管理中心 | Azure Stack HCI | TCP | 5986 |
注意
在安装 Windows Admin Center 时,如果选择“仅通过 HTTPS 使用 WinRM”设置,则需要端口 5986。
Active Directory
确保在 Active Directory(本地安全机构)的本地防火墙中配置以下防火墙规则。
| 规则 | 行动 | 源 | 目标 | 服务 | 端口 |
|---|---|---|---|---|---|
| 允许与 Active Directory Web 服务 (ADWS) 和 Active Directory 管理网关服务的入站/出站连接 | 允许 | Azure Stack HCI | Active Directory 服务 | TCP | 9389 |
故障转移群集
确保在故障转移群集的本地防火墙中配置了以下防火墙规则。
| 规则 | 行动 | 源 | 目标 | 服务 | 端口 |
|---|---|---|---|---|---|
| 允许故障转移群集验证 | 允许 | 管理系统 | 群集服务器 | TCP | 445 |
| 允许 RPC 动态端口分配 | 允许 | 管理系统 | 群集服务器 | TCP | 至少 100 个端口 高于端口 5000 |
| 允许远程过程调用 (RPC) | 允许 | 管理系统 | 群集服务器 | TCP | 135 |
| 允许群集管理员 | 允许 | 管理系统 | 群集服务器 | UDP | 137 |
| 允许群集服务 | 允许 | 管理系统 | 群集服务器 | UDP | 3343 |
| 允许群集服务(在服务器加入操作 期间是必需的。) |
允许 | 管理系统 | 群集服务器 | TCP | 3343 |
| 允许 ICMPv4 和 ICMPv6 来进行故障转移群集验证 |
允许 | 管理系统 | 群集服务器 | 不适用 | 不适用 |
注意
管理系统包括你计划使用 Windows Admin Center、Windows PowerShell 或 System Center Virtual Machine Manager 等工具管理群集的任何计算机。
Hyper-V
确保在 Hyper-V 的本地防火墙中配置了以下防火墙规则。
| 规则 | 行动 | 源 | 目标 | 服务 | 端口 |
|---|---|---|---|---|---|
| 允许群集通信 | 允许 | 管理系统 | Hyper-V Server | TCP | 445 |
| 允许 RPC 端点映射程序和 WMI | 允许 | 管理系统 | Hyper-V Server | TCP | 135 |
| 允许 HTTP 连接 | 允许 | 管理系统 | Hyper-V Server | TCP | 80 |
| 允许 HTTPS 连接 | 允许 | 管理系统 | Hyper-V Server | TCP | 443 |
| 允许实时迁移 | 允许 | 管理系统 | Hyper-V Server | TCP | 6600 |
| 允许 VM 管理服务 | 允许 | 管理系统 | Hyper-V Server | TCP | 2179 |
| 允许 RPC 动态端口分配 | 允许 | 管理系统 | Hyper-V Server | TCP | 至少 100 个端口 高于端口 5000 |
注意
打开一系列高于端口 5000 的端口,以允许 RPC 动态端口分配。 低于 5000 的端口可能已被其他应用程序使用,可能导致与 DCOM 应用程序发生冲突。 以前的经验显示,至少应打开 100 个端口,原因是多个系统服务依赖于这些 RPC 端口来彼此通信。 有关详细信息,请参阅如何配置与防火墙一起使用的 RPC 动态端口分配。
存储副本(拉伸群集)
确保在存储副本(拉伸群集)的本地防火墙中配置了以下防火墙规则。
| 规则 | 行动 | 源 | 目标 | 服务 | 端口 |
|---|---|---|---|---|---|
| 允许服务器消息块 (SMB) 协议 |
允许 | 拉伸群集服务器 | 拉伸群集服务器 | TCP | 445 |
| 允许 Web 服务管理 (WS-MAN) |
允许 | 拉伸群集服务器 | 拉伸群集服务器 | TCP | 5985 |
| 允许 ICMPv4 和 ICMPv6 (如果在使用 Test-SRTopologyPowerShell cmdlet) |
允许 | 拉伸群集服务器 | 拉伸群集服务器 | 不适用 | 不适用 |
更新 Microsoft Defender 防火墙
本部分介绍了如何将 Microsoft Defender 防火墙配置为允许与服务标记关联的 IP 地址连接到操作系统。 服务标记代表给定 Azure 服务中的一组 IP 地址。 Microsoft 会管理服务标记中包含的 IP 地址,并且会在 IP 地址更改时自动更新服务标记,使更新量保持在最低水平。 若要了解详细信息,请参阅虚拟网络服务标记。
将以下资源中的 JSON 文件下载到运行操作系统的目标计算机:Azure IP Ranges 和服务标签 - 公共云。
使用以下 PowerShell 命令打开 JSON 文件:
$json = Get-Content -Path .\ServiceTags_China_20210308.json | ConvertFrom-Json获取给定服务标记(例如
AzureResourceManager服务标记)的 IP 地址范围列表:$IpList = ($json.values | where Name -Eq "AzureResourceManager").properties.addressPrefixes将 IP 地址列表导入到外部公司防火墙(如果你在防火墙中使用允许列表)。
为群集中的每台服务器创建防火墙规则,允许出站 443 (HTTPS) 流量访问指定的 IP 地址范围列表。
New-NetFirewallRule -DisplayName "Allow Azure Resource Manager" -RemoteAddress $IpList -Direction Outbound -LocalPort 443 -Protocol TCP -Action Allow -Profile Any -Enabled True
后续步骤
有关详细信息,请参阅:
- Windows 远程管理的安装和配置中的 Windows 防火墙和 WinRM 2.0 端口部分