注释
本文仅介绍外部证书的准备,这些证书用于保护外部基础结构和服务上的终结点。 内部证书在证书轮换过程中单独进行管理。
注释
如果要安装 Azure 容器注册表(ACR),我们建议将外部 ACR 证书的到期日期与其他外部 Azure Stack Hub 证书的到期日期保持一致。 此外,我们建议对用于 ACR 的 PFX 使用与您用于保护其他外部证书 PFX 相同的密码进行保护。
从证书颁发机构(CA)获取的证书文件 必须导入并导出,其属性必须符合 Azure Stack Hub 的证书要求。
本文介绍如何导入、打包和验证外部证书,以便为 Azure Stack Hub 部署或机密轮换做好准备。
先决条件
在打包 Azure Stack Hub 部署的 PKI 证书之前,系统应满足以下先决条件:
- 从证书颁发机构返回的证书以.cer格式(其他可配置格式(如 .cert、.sst 或 .pfx)存储在单个目录中。
- Windows 10 或 Windows Server 2016 或更高版本。
- 使用生成证书签名请求的同一系统(除非要针对的是预打包到 PFX 中的证书)。
- 使用提升的 PowerShell 会话。
继续进行到相应的准备证书(Azure Stack 就绪性检查器)或准备证书(手动步骤)部分。
准备证书(Azure Stack 就绪性检查器)
使用以下步骤通过 Azure Stack 就绪性检查器 PowerShell cmdlet 打包证书:
通过运行以下 cmdlet,从 PowerShell 提示符(5.1 或更高版本)安装 Azure Stack 就绪情况检查器模块:
Install-Module Microsoft.AzureStack.ReadinessChecker -Force -AllowPrerelease指定证书文件的路径。 例如:
$Path = "$env:USERPROFILE\Documents\AzureStack"声明 pfxPassword。 例如:
$pfxPassword = Read-Host -AsSecureString -Prompt "PFX Password"声明要将生成的 PFX 导出到的 ExportPath。 例如:
$ExportPath = "$env:USERPROFILE\Documents\AzureStack"将证书转换为 Azure Stack Hub 证书。 例如:
ConvertTo-AzsPFX -Path $Path -pfxPassword $pfxPassword -ExportPath $ExportPath查看输出:
ConvertTo-AzsPFX v1.2005.1286.272 started.Stage 1: Scanning Certificates Path: C:\Users\[*redacted*]\Documents\AzureStack Filter: CER Certificate count: 11 adminmanagement_east_azurestack_contoso_com_CertRequest_20200710235648.cer adminportal_east_azurestack_contoso_com_CertRequest_20200710235645.cer management_east_azurestack_contoso_com_CertRequest_20200710235644.cer portal_east_azurestack_contoso_com_CertRequest_20200710235646.cer wildcard_adminhosting_east_azurestack_contoso_com_CertRequest_20200710235649.cer wildcard_adminvault_east_azurestack_contoso_com_CertRequest_20200710235642.cer wildcard_blob_east_azurestack_contoso_com_CertRequest_20200710235653.cer wildcard_hosting_east_azurestack_contoso_com_CertRequest_20200710235652.cer wildcard_queue_east_azurestack_contoso_com_CertRequest_20200710235654.cer wildcard_table_east_azurestack_contoso_com_CertRequest_20200710235650.cer wildcard_vault_east_azurestack_contoso_com_CertRequest_20200710235647.cer Detected ExternalFQDN: east.azurestack.contoso.com Stage 2: Exporting Certificates east.azurestack.contoso.com\Deployment\ARM Admin\ARMAdmin.pfx east.azurestack.contoso.com\Deployment\Admin Portal\AdminPortal.pfx east.azurestack.contoso.com\Deployment\ARM Public\ARMPublic.pfx east.azurestack.contoso.com\Deployment\Public Portal\PublicPortal.pfx east.azurestack.contoso.com\Deployment\Admin Extension Host\AdminExtensionHost.pfx east.azurestack.contoso.com\Deployment\KeyVaultInternal\KeyVaultInternal.pfx east.azurestack.contoso.com\Deployment\ACSBlob\ACSBlob.pfx east.azurestack.contoso.com\Deployment\Public Extension Host\PublicExtensionHost.pfx east.azurestack.contoso.com\Deployment\ACSQueue\ACSQueue.pfx east.azurestack.contoso.com\Deployment\ACSTable\ACSTable.pfx east.azurestack.contoso.com\Deployment\KeyVault\KeyVault.pfx Stage 3: Validating Certificates. Validating east.azurestack.contoso.com-Deployment-AAD certificates in C:\Users\[*redacted*]\Documents\AzureStack\east.azurestack.contoso.com\Deployment Testing: KeyVaultInternal\KeyVaultInternal.pfx Thumbprint: E86699****************************4617D6 PFX Encryption: OK Expiry Date: OK Signature Algorithm: OK DNS Names: OK Key Usage: OK Key Length: OK Parse PFX: OK Private Key: OK Cert Chain: OK Chain Order: OK Other Certificates: OK Testing: ARM Public\ARMPublic.pfx ... Log location (contains PII): C:\Users\[*redacted*]\AppData\Local\Temp\AzsReadinessChecker\AzsReadinessChecker.log ConvertTo-AzsPFX Completed注释
使用
Get-help ConvertTo-AzsPFX -Full查看其他选项,例如禁用验证或筛选不同的证书格式。成功验证后,可以针对部署或轮换提供证书,而无需执行任何其他步骤。
准备证书(手动步骤)
可以使用这些手动步骤为新的 Azure Stack Hub PKI 证书打包证书。
导入证书
将从所选 CA 获取的原始证书版本 复制到部署主机上的目录中。
警告
请勿从 CA 直接提供的文件中复制已导入、导出或更改的文件。
右键单击证书并选择 安装证书 或 安装 PFX,具体取决于证书从 CA 传递的方式。
在 证书导入向导中,选择 本地计算机 作为导入位置。 选择“下一步”。 在以下屏幕上,再次选择“下一步”。
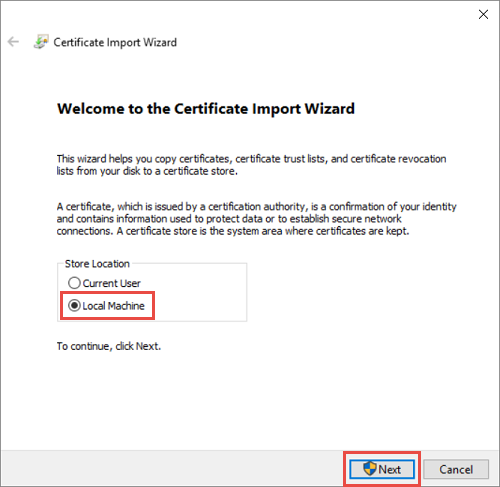 的本地计算机导入位置
的本地计算机导入位置选择将所有证书都放在以下存储中,然后选择企业信任作为存储位置。 选择“确定”关闭证书存储选择对话框,然后选择“下一步”。
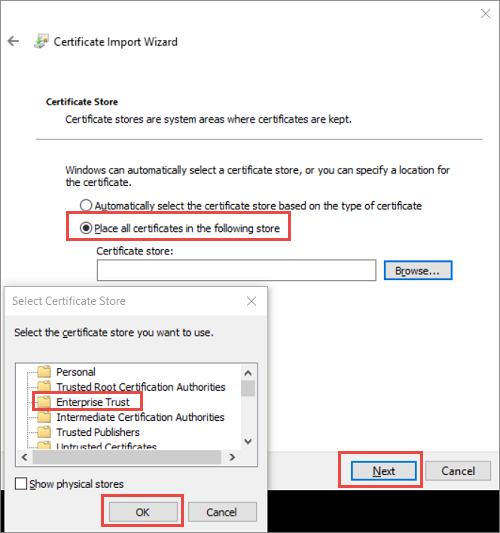
- 如果导入 PFX,会显示一个附加对话框。 在 私钥保护 页上,输入证书文件的密码,然后启用 将此密钥标记为可导出。 选项,允许稍后备份或传输密钥。 选择“下一步”。
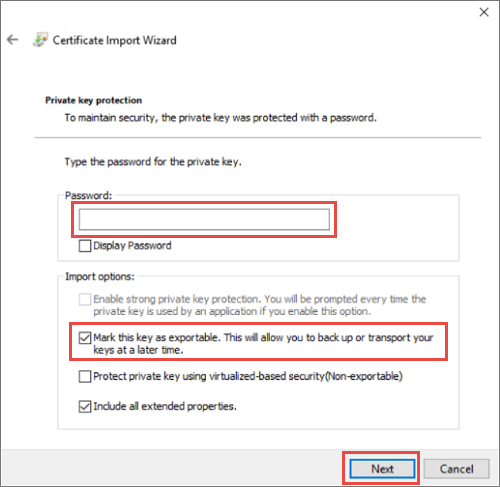
选择“完成”以完成导入。
注释
导入 Azure Stack Hub 的证书后,证书的私钥将存储为群集存储上的 PKCS 12 文件(PFX)。
导出证书
打开证书管理器 MMC 控制台并连接到本地计算机证书存储。
打开Microsoft管理控制台。 若要在 Windows 10 中打开控制台,请右键单击 “开始”菜单,选择 运行,然后键入 mmc,然后按 Enter。
选择文件>添加/删除管理单元,然后选择证书并选择添加。
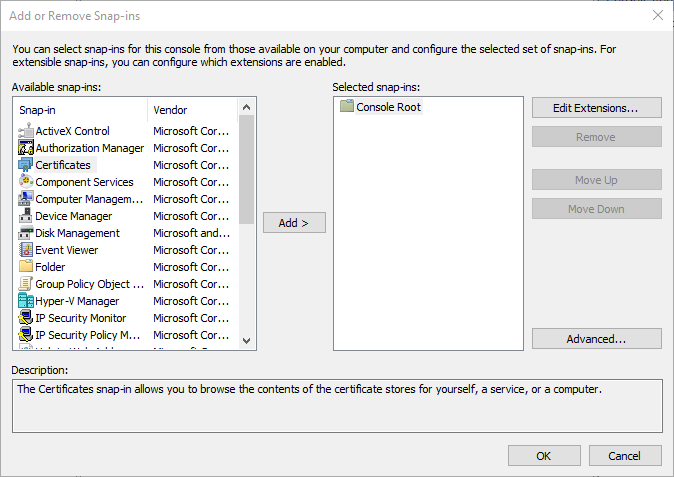 中添加证书管理单元
中添加证书管理单元选择 计算机帐户,然后选择 下一步。 选择“本地计算机”,然后选择“完成”。 选择 “确定” 以关闭“添加/删除 Snap-In”页。
浏览到证书>企业信任>证书位置。 确认在右侧看到你的证书。
在“证书管理器控制台”任务栏中,选择 操作>所有任务>导出。 选择“下一步”。
注释
根据你拥有的 Azure Stack Hub 证书数量,可能需要多次完成此过程。
选择 是,导出私钥,然后选择 下一步。
在“导出文件格式”部分中:
- 选择“包括证书路径中的所有证书(如果可能)”。
- 选择“导出所有扩展属性”。
- 选择“启用证书隐私”。
- 选择“下一步”。

选择 密码 并为证书提供密码。 创建满足以下密码复杂性要求的密码:
- 最小长度为 8 个字符。
- 以下字符中至少有三个字符:大写字母、小写字母、0-9 的数字、特殊字符、非大写或小写字母字符。
记下此密码。 稍后将其用作部署参数。
选择“下一步”。
选择要导出的 PFX 文件的文件名和位置。 选择“下一步”。
选择完成。