重要
从 Azure Stack Hub 构建版本 2108 开始,SQL 和 MySQL 资源提供程序将提供给已获得访问权限的订阅。 如果想要开始使用此功能,或者需要从以前的版本升级, 请打开支持案例 ,我们的支持工程师将指导你完成部署或升级过程。
SQL 资源提供程序在锁定的虚拟机(VM)上运行。 若要启用维护作,需要更新 VM 的安全性。 若要使用最低特权原则执行此作,请使用 PowerShell Just Enough Administration (JEA) 终结点 DBAdapterMaintenance。 资源提供程序安装包包含此操作的脚本。
修补和更新
SQL 资源提供程序未作为 Azure Stack Hub 的一部分提供服务,因为它是加载项组件。 Microsoft根据需要向 SQL 资源提供程序提供更新。
对于 SQL RP V1,发布更新的 SQL Server 资源提供程序时,会提供一个脚本来应用更新。 此脚本将创建新的资源提供程序 VM,将旧提供程序 VM 的状态迁移到新 VM。
对于 SQL RP V2,资源提供程序使用用于应用 Azure Stack Hub 更新的相同更新功能进行更新。
有关详细信息,请参阅 更新 SQL 资源提供程序。
更新提供程序 VM
SQL RP V1 在 用户 VM 上运行,需要在发布时应用所需的修补程序和更新。 可以在安装或更新资源提供程序的过程中安装 Windows 更新包。
SQL RP V2 在隐藏的托管 Windows Server 上运行。 无需修补或更新资源提供程序 VM。 当您更新 RP 时,它将会自动更新。
更新 VM Windows Defender 定义
这些说明仅适用于在 Azure Stack Hub 集成系统上运行的 SQL RP V1。
更新 Windows Defender 定义:
请从 Windows Defender 的安全智能更新 下载 Windows Defender 定义更新。
在定义更新页上,向下滚动到“手动下载更新”。 下载“适用于 Windows 10 和 Windows 8.1 的 Windows Defender 防病毒”64 位文件。
还可以 使用此直接链接 下载/运行 fpam-fe.exe 文件。
创建 PowerShell 会话以连接到 SQL 资源提供者适配器 VM 的维护终结点。
使用维护终结点会话将定义更新文件复制到 VM。
在维护 PowerShell 会话中,运行 Update-DBAdapterWindowsDefenderDefinitions 命令。
安装定义后,建议使用 Remove-ItemOnUserDrive 命令删除定义更新文件。
用于更新定义的 PowerShell 脚本示例
可以编辑并运行以下脚本来更新 Defender 定义。 将脚本中的值替换为环境中的值。
# Set credentials for local admin on the resource provider VM.
$vmLocalAdminPass = ConvertTo-SecureString '<local admin user password>' -AsPlainText -Force
$vmLocalAdminUser = "<local admin user name>"
$vmLocalAdminCreds = New-Object System.Management.Automation.PSCredential `
($vmLocalAdminUser, $vmLocalAdminPass)
# Provide the public IP address for the adapter VM.
$databaseRPMachine = "<RP VM IP address>"
$localPathToDefenderUpdate = "C:\DefenderUpdates\mpam-fe.exe"
# Download the Windows Defender update definitions file from https://www.microsoft.com/wdsi/definitions.
Invoke-WebRequest -Uri 'https://go.microsoft.com/fwlink/?LinkID=121721&arch=x64' `
-Outfile $localPathToDefenderUpdate
# Create a session to the maintenance endpoint.
$session = New-PSSession -ComputerName $databaseRPMachine `
-Credential $vmLocalAdminCreds -ConfigurationName DBAdapterMaintenance `
-SessionOption (New-PSSessionOption -Culture en-US -UICulture en-US)
# Copy the defender update file to the adapter VM.
Copy-Item -ToSession $session -Path $localPathToDefenderUpdate `
-Destination "User:\"
# Install the update definitions.
Invoke-Command -Session $session -ScriptBlock `
{Update-AzSDBAdapterWindowsDefenderDefinition -DefinitionsUpdatePackageFile "User:\mpam-fe.exe"}
# Cleanup the definitions package file and session.
Invoke-Command -Session $session -ScriptBlock `
{Remove-AzSItemOnUserDrive -ItemPath "User:\mpam-fe.exe"}
$session | Remove-PSSession
为 SQL 资源提供程序配置 Azure 诊断扩展
这些说明仅适用于在 Azure Stack Hub 集成系统上运行的 SQL RP V1。
默认情况下,AZURE 诊断扩展安装在 SQL 资源提供程序适配器 VM 上。 以下步骤演示如何自定义扩展,以便收集 SQL 资源提供程序作事件日志和 IIS 日志,以便进行故障排除和审核。
登录到 Azure Stack Hub 管理员门户。
从左侧窗格中选择 虚拟机 ,搜索 SQL 资源提供程序适配器 VM 并选择 VM。
在 VM 的 诊断设置 中,转到“ 日志 ”选项卡,然后选择“ 自定义 ”以自定义正在收集的事件日志。
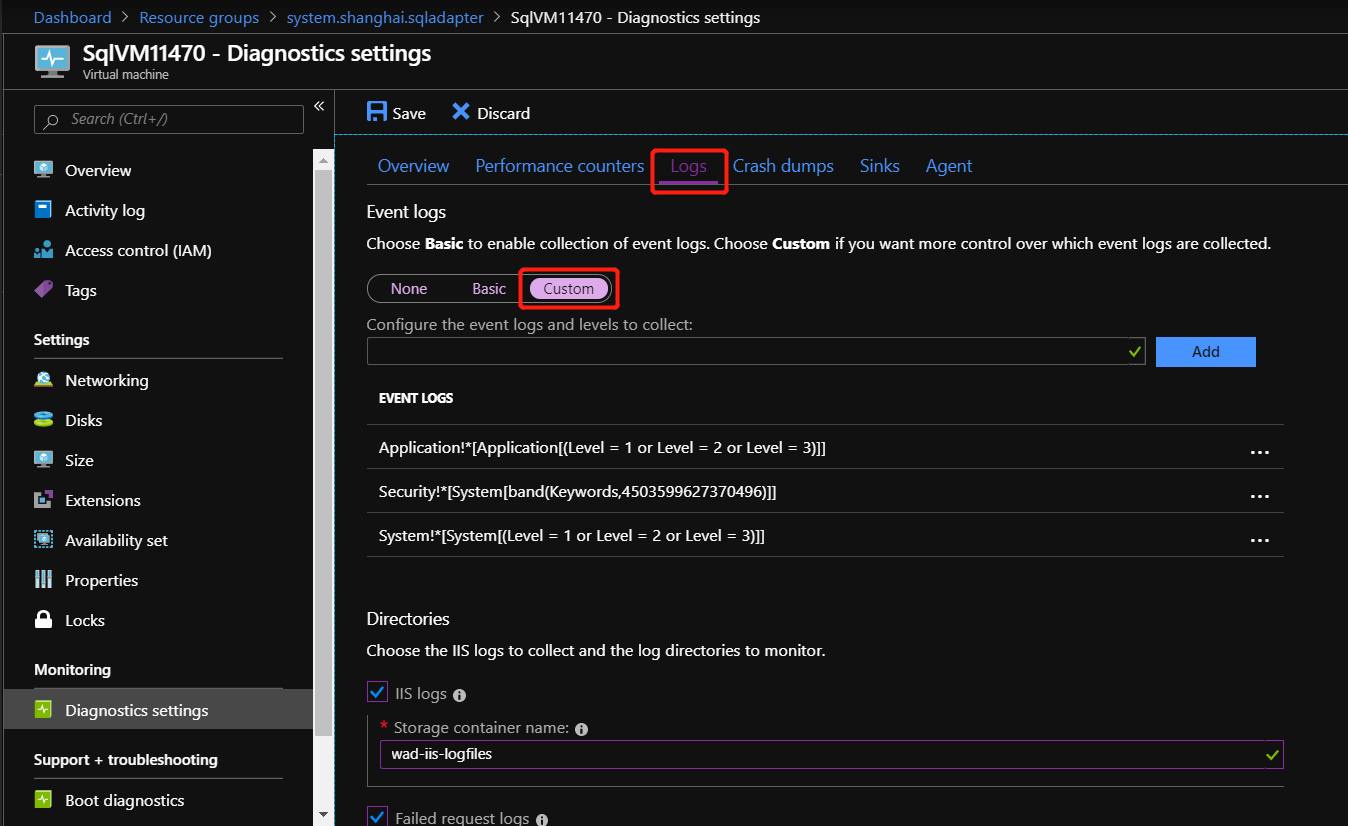
添加 Microsoft-AzureStack-DatabaseAdapter/Operational!* 以收集 SQL 资源提供程序运行事件日志。
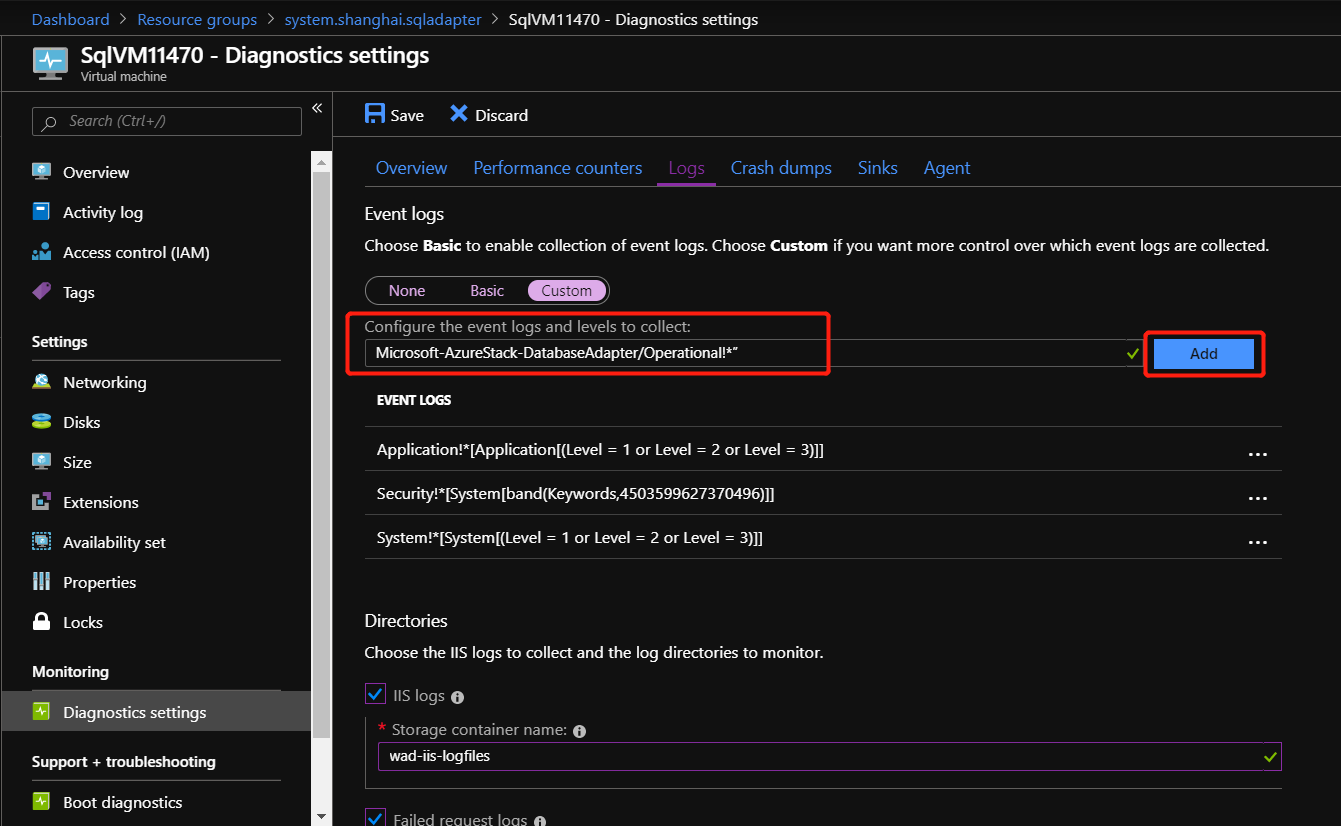
若要启用 IIS 日志的收集,请检查 IIS 日志 和 失败的请求日志。
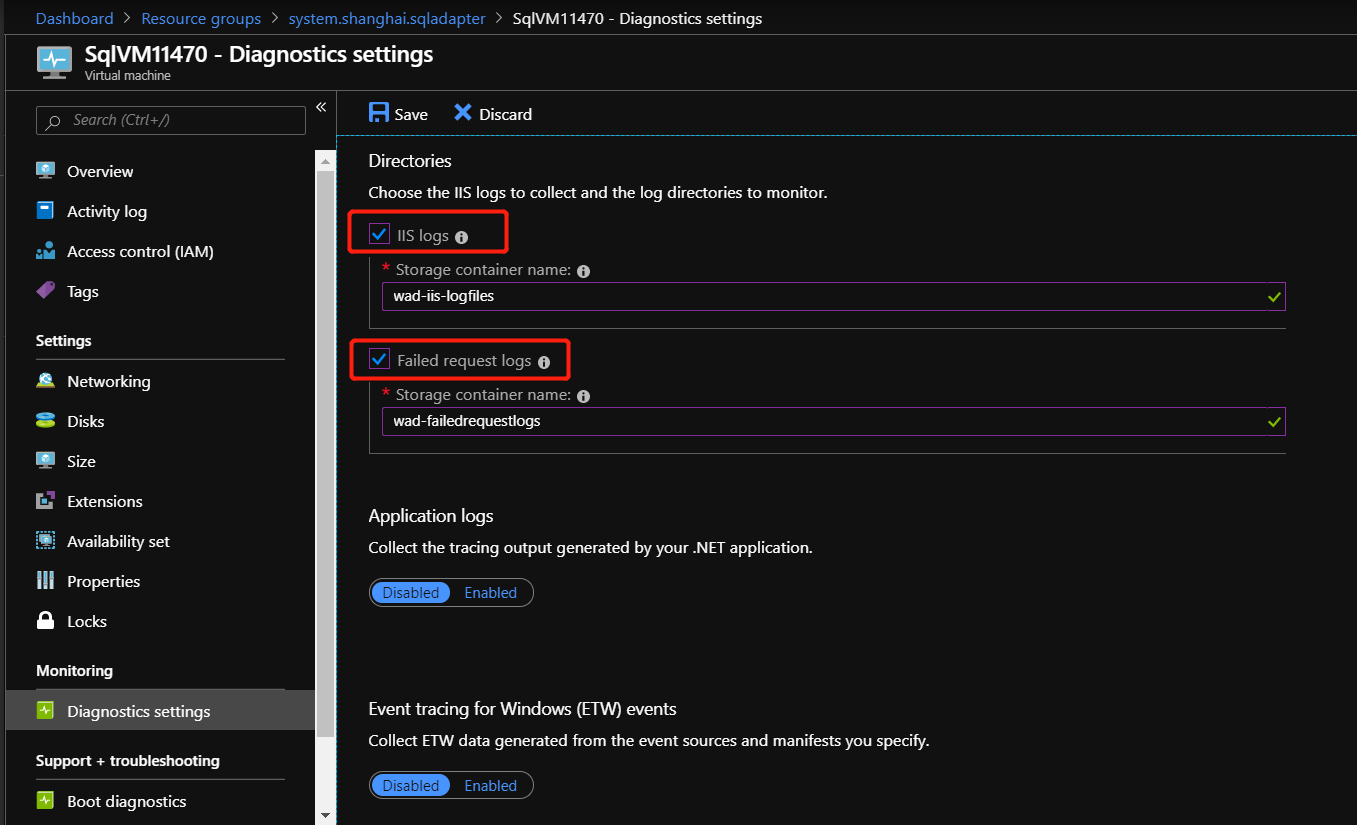
最后,选择“ 保存” 以保存所有诊断设置。
为 SQL 资源提供程序配置事件日志和 IIS 日志收集后,可以在名为 sqladapterdiagaccount 的系统存储帐户中找到日志。
若要了解有关 Azure 诊断扩展的详细信息,请参阅 什么是 Azure 诊断扩展。
更新 SQL 凭据
你负责在 SQL 服务器上创建和维护 sysadmin 帐户。 资源提供程序需要具有这些权限的帐户来管理用户的数据库,但它不需要访问用户的数据。 如果需要更新 SQL 服务器上的 sysadmin 密码,可以使用资源提供程序的管理员界面更改存储的密码。 这些密码存储在 Azure Stack Hub 实例上的 Key Vault 中。
若要修改设置,请选择
密钥轮换策略
这些说明仅适用于在 Azure Stack Hub 集成系统上运行的 SQL RP V1。
将 SQL 和 MySQL 资源提供程序与 Azure Stack Hub 集成系统配合使用时,Azure Stack Hub 操作员负责轮换以下资源提供程序基础结构机密,以确保它们不会过期:
- 部署期间提供的外部 SSL 证书。
- 部署期间提供的资源提供程序 VM 本地管理员帐户密码。
- 资源提供程序诊断用户 (dbadapterdiag) 密码。
- (版本 >= 1.1.47.0) 部署期间生成的 Key Vault 证书。
轮换机密的 PowerShell 示例
重要
成功轮换机密需要在运行以下脚本之前 删除任何现有版本的 Azure Stack Hub PowerShell 模块。
同时更改所有机密。
.\SecretRotationSQLProvider.ps1 `
-Privilegedendpoint $Privilegedendpoint `
-CloudAdminCredential $cloudCreds `
-AzCredential $adminCreds `
-DiagnosticsUserPassword $passwd `
-DependencyFilesLocalPath $certPath `
-DefaultSSLCertificatePassword $certPasswd `
-VMLocalCredential $localCreds `
-KeyVaultPfxPassword $keyvaultCertPasswd
更改诊断用户密码。
.\SecretRotationSQLProvider.ps1 `
-Privilegedendpoint $Privilegedendpoint `
-CloudAdminCredential $cloudCreds `
-AzCredential $adminCreds `
-DiagnosticsUserPassword $passwd
更改 VM 本地管理员帐户密码。
.\SecretRotationSQLProvider.ps1 `
-Privilegedendpoint $Privilegedendpoint `
-CloudAdminCredential $cloudCreds `
-AzCredential $adminCreds `
-VMLocalCredential $localCreds
轮换 SSL 证书
.\SecretRotationSQLProvider.ps1 `
-Privilegedendpoint $Privilegedendpoint `
-CloudAdminCredential $cloudCreds `
-AzCredential $adminCreds `
-DependencyFilesLocalPath $certPath `
-DefaultSSLCertificatePassword $certPasswd
轮换 Key Vault 证书
.\SecretRotationSQLProvider.ps1 `
-Privilegedendpoint $Privilegedendpoint `
-CloudAdminCredential $cloudCreds `
-AzCredential $adminCreds `
-KeyVaultPfxPassword $keyvaultCertPasswd
SecretRotationSQLProvider.ps1 参数
| 参数 | Description | 注释 |
|---|---|---|
| AzureEnvironment | 用于部署 Azure Stack Hub 的服务管理员帐户的 Azure 环境。 仅适用于 Microsoft Entra 部署。 支持的环境名称为 AzureChinaCloud。 | 可选 |
| AzCredential | Azure Stack Hub 服务管理员帐户凭据。 如果用于 AzCredential 的帐户需要多重身份验证(MFA),脚本将失败。 | 强制的 |
| CloudAdminCredential | Azure Stack Hub 云管理员域帐户凭据。 | 强制的 |
| PrivilegedEndpoint | 用于访问 Get-AzureStackStampInformation 的特权终结点。 | 强制的 |
| 诊断用户密码 | 诊断用户帐户密码。 | 可选 |
| VMLocalCredential | MySQLAdapter VM 上的本地管理员帐户。 | 可选 |
| DefaultSSLCertificatePassword | 默认 SSL 证书 (*.pfx) 密码。 | 可选 |
| DependencyFilesLocalPath | 依赖项文件本地路径。 | 可选 |
| KeyVaultPfxPassword | 用于为数据库适配器生成 Key Vault 证书的密码。 | 可选 |
这些说明仅适用于在 Azure Stack Hub 集成系统上运行的 SQL RP V2。
注释
目前,对于增值资源提供商(RPs),仅支持通过 PowerShell 实现机密轮换。
与 Azure Stack Hub 基础结构一样,增值资源提供程序同时使用内部和外部机密。 作为操作员,你负责:
- 提供更新的外部机密,例如用于保护资源提供程序终结点的新 TLS 证书。
- 定期管理资源供应商的密钥轮换。
当机密即将过期时,会在管理员门户中生成以下警报。 完成密钥轮换可以解决以下警报:
- 即将过期的内部证书
- 待处理的外部证书过期
先决条件
为轮换过程做准备:
如果尚未安装, 请先安装适用于 Azure Stack Hub 的 PowerShell Az 模块 ,然后再继续作。 Azure Stack Hub 密钥轮换需要版本 2.0.2-preview 或更高版本。 有关详细信息,请参阅 从 AzureRM 迁移到 Azure Stack Hub 中的 Azure PowerShell Az。
安装 Azs.Deployment.Admin 1.0.0 模块: PowerShell Gallery | Azs.Deployment.Admin 1.0.0
Install-Module -Name Azs.Deployment.Admin
- 如果外部证书即将过期,请在获取/续订 X509 证书之前查看 Azure Stack Hub 公钥基础结构(PKI)证书要求 ,了解重要的先决条件信息,包括所需 PFX 格式的详细信息。 另请查看 “可选 PaaS 证书”部分中为特定增值资源提供程序指定的要求。
为外部证书轮换准备新的 TLS 证书
注释
如果只有内部证书即将过期,则可以跳过本部分。
接下来,创建或续订 TLS 证书来保护增值资源提供程序终结点:
完成为资源提供程序 生成证书签名请求(CSR)中的步骤,以便续订证书 。 此处使用 Azure Stack Hub 就绪性检查器工具创建 CSR。 请务必在步骤“为其他 Azure Stack Hub 服务生成证书请求”中为适用于您的资源提供程序运行正确的 cmdlet。 例如
New-AzsDbAdapterCertificateSigningRequest,用于 SQL 和 MySQLRP。 完成后,将生成的 .REQ 文件提交给证书颁发机构 (CA) 以获取新证书。从 CA 收到证书文件后,请完成 部署或轮换准备证书中的步骤。 再次使用就绪情况检查器工具来处理从 CA 返回的文件。
最后,完成 验证 Azure Stack Hub PKI 证书中的步骤。 再次使用就绪情况检查器工具对新证书执行验证测试。
轮换内部证书
打开以管理员身份运行的 PowerShell 控制台,并完成以下步骤来轮换资源提供程序的外部密钥:
使用操作员凭据登录到 Azure Stack Hub 环境。 请参阅 使用 PowerShell 连接到 Azure Stack Hub 的登录脚本。 请务必使用 PowerShell Az cmdlet(而不是 AzureRM),并替换所有占位符值,例如终结点 URL 和目录租户名称。
确定资源提供程序的产品 ID。 运行
Get-AzsProductDeploymentcmdlet 以检索最新资源提供程序部署的列表。 返回的"value"集合包含每个已部署资源提供者的一个元素。 查找感兴趣的资源提供程序并记下这些属性的值:-
"name"- 包含值第二段中的资源提供程序产品 ID。
例如,SQL RP 部署可能具有产品 ID
"microsoft.sqlrp"。-
运行
Invoke-AzsProductRotateSecretsActioncmdlet 以轮换内部证书:Invoke-AzsProductRotateSecretsAction -ProductId $productId
轮换外部证书
需要首先记下以下参数的值。
| Placeholder | Description | 示例值 |
|---|---|---|
<product-id> |
最新资源提供程序部署的产品 ID。 | microsoft.sqlrp |
<installed-version> |
最新资源提供程序部署的版本。 | 2.0.0.2 |
<package-id> |
包 ID 是通过连接产品编号和安装版本来生成的。 | microsoft.sqlrp.2.0.0.2 |
<cert-secret-name> |
用于存储证书机密的名称。 | SSLCert |
<cert-pfx-file-path> |
证书 PFX 文件的路径。 | C:\dir\dbadapter-cert-file.pfx |
<pfx-password> |
分配给您证书 .PFX 文件的密码。 | strong@CertSecret6 |
打开提升的 PowerShell 控制台并完成以下步骤:
使用操作员凭据登录到 Azure Stack Hub 环境。 请参阅 使用 PowerShell 连接到 Azure Stack Hub 的登录脚本。 请务必使用 PowerShell Az cmdlet(而不是 AzureRM),并替换所有占位符值,例如终结点 URL 和目录租户名称。
获取 product-id 参数值。 运行
Get-AzsProductDeploymentcmdlet 以检索最新资源提供程序部署的列表。 返回的"value"集合包含每个已部署资源提供者的一个元素。 查找感兴趣的资源提供程序并记下这些属性的值:-
"name"- 包含值第二段中的资源提供程序产品 ID。 -
"properties"."deployment"."version"- 包含当前部署的版本号。
-
例如,SQL RP 部署可能具有产品 ID "microsoft.sqlrp"和版本 "2.0.0.2"。
通过连接资源提供程序产品 ID 和版本来生成资源提供程序的包 ID。 例如,使用上一步派生的值,SQL RP 包 ID 为
microsoft.sqlrp.2.0.0.2。使用上一步派生的包 ID,运行
Get-AzsProductSecret -PackageId以检索资源提供程序使用的机密类型列表。 在返回的value集合中,查找属性"Certificate"的值为"properties"."secretKind"的元素。 此元素包含 RP 证书机密的属性。 记下此证书密钥的名称,它由属性中的最后一段"name"标识,位于"properties"的上方。
例如,为 SQL RP 返回的机密集合包含一个名为"Certificate"的SSLCert机密。
使用
Set-AzsProductSecretcmdlet 将新证书导入 Key Vault,该证书将由轮换过程使用。 在运行脚本之前,请相应地替换变量占位符值。$productId = '<product-id>' $packageId = $productId + '.' + '<installed-version>' $certSecretName = '<cert-secret-name>' $pfxFilePath = '<cert-pfx-file-path>' $pfxPassword = ConvertTo-SecureString '<pfx-password>' -AsPlainText -Force Set-AzsProductSecret -PackageId $packageId -SecretName $certSecretName -PfxFileName $pfxFilePath -PfxPassword $pfxPassword -Force最后,使用
Invoke-AzsProductRotateSecretsActioncmdlet 来轮换密钥:Invoke-AzsProductRotateSecretsAction -ProductId $productId
监视机密轮换进度
可以通过在 PowerShell 控制台或管理员门户中选择市场服务中的资源提供程序来监视机密轮换进度:
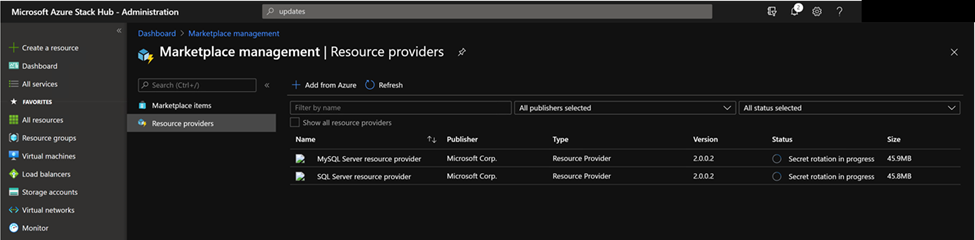
注释
机密轮换时间可能花费超过 10 分钟。 完成后,资源提供程序的状态将更改为“已安装”。
收集诊断日志
Azure Stack Hub 有多种方法可将诊断日志收集、保存和发送到 Azure 支持部门。 从版本 1.1.93 开始,SQL 资源提供程序支持从 Azure Stack Hub 环境收集日志的标准方法。 有关详细信息,请参阅 诊断日志收集。
从版本 1.1.93 开始,SQL 资源提供程序支持从 Azure Stack Hub 环境收集日志的标准方法。 如果使用较旧版本,建议将 SQL 资源提供程序更新到最新版本。
若要从锁定的 VM 收集日志,请使用 PowerShell Just Enough Administration (JEA) 终结点 DBAdapterDiagnostics。 此终结点提供以下命令:
- Get-AzsDBAdapterLog。 此命令将创建资源提供程序诊断日志的 zip 包,并将文件保存到会话的用户驱动器上。 无需任何参数即可运行此命令,并收集过去四个小时的日志。
- Remove-AzsDBAdapterLog。 此命令删除资源提供程序 VM 上的现有日志包。
终结点要求和流程
安装或更新资源提供程序时,将创建 dbadapterdiag 用户帐户。 你将使用此帐户收集诊断日志。
注释
dbadapterdiag 帐户密码与在提供程序部署或更新期间创建的 VM 上本地管理员使用的密码相同。
若要使用 DBAdapterDiagnostics 命令,请创建资源提供程序 VM 的远程 PowerShell 会话并运行 Get-AzsDBAdapterLog 命令。
使用 FromDate 和 ToDate 参数设置日志收集的时间跨度。 如果未指定这两个参数,则使用以下默认值:
- FromDate 比当前时间早四小时。
- ToDate 是当前时间。
用于收集日志的 PowerShell 脚本示例
以下脚本演示如何从资源提供程序 VM 收集诊断日志。
# Create a new diagnostics endpoint session.
$databaseRPMachineIP = '<RP VM IP address>'
$diagnosticsUserName = 'dbadapterdiag'
$diagnosticsUserPassword = '<Enter Diagnostic password>'
$diagCreds = New-Object System.Management.Automation.PSCredential `
($diagnosticsUserName, (ConvertTo-SecureString -String $diagnosticsUserPassword -AsPlainText -Force))
$session = New-PSSession -ComputerName $databaseRPMachineIP -Credential $diagCreds `
-ConfigurationName DBAdapterDiagnostics `
-SessionOption (New-PSSessionOption -Culture en-US -UICulture en-US)
# Sample that captures logs from the previous hour.
$fromDate = (Get-Date).AddHours(-1)
$dateNow = Get-Date
$sb = {param($d1,$d2) Get-AzSDBAdapterLog -FromDate $d1 -ToDate $d2}
$logs = Invoke-Command -Session $session -ScriptBlock $sb -ArgumentList $fromDate,$dateNow
# Copy the logs to the user drive.
$sourcePath = "User:\{0}" -f $logs
$destinationPackage = Join-Path -Path (Convert-Path '.') -ChildPath $logs
Copy-Item -FromSession $session -Path $sourcePath -Destination $destinationPackage
# Clean up the logs.
$cleanup = Invoke-Command -Session $session -ScriptBlock {Remove-AzsDBAdapterLog}
# Close the session.
$session | Remove-PSSession
SQL Server 资源提供程序版本 1 的已知限制
限制:
部署、升级或机密轮换脚本失败时,标准日志收集机制无法收集某些日志。
解决方法:
除了使用标准日志收集机制,请转到脚本找到的提取文件夹中的 Logs 文件夹,查找更多日志。