本文逐步介绍如何使用 Azure Stack Hub Key Vault 中存储的密码部署 Windows Server 虚拟机(VM)。 使用密钥保管库密码比传递纯文本密码更安全。
概述
可以将类似密码这样的值存储为 Azure Stack Hub 密钥保管库中的机密。 创建机密后,可以在 Azure 资源管理器模板中引用它。 将机密与 Resource Manager 配合使用可提供以下优势:
- 每次部署资源时,无需手动输入机密。
- 可以指定哪些用户或服务主体可以访问机密。
先决条件
- 必须订阅包含 Key Vault 服务的套餐。
- 安装适用于 Azure Stack Hub 的 PowerShell。
- 配置 PowerShell 环境。
以下步骤介绍了通过检索 Key Vault 中存储的密码来创建 VM 所需的过程:
- 创建 Key Vault 机密。
- 更新
azuredeploy.parameters.json文件。 - 部署模板。
注释
你可以从 Azure Stack 开发工具包(ASDK)或通过 VPN 连接的外部客户端使用这些步骤。
创建 Key Vault 机密
以下脚本创建密钥保管库,并将密码作为机密存储在密钥保管库中。 创建密钥保管库时,请使用 -EnabledForDeployment 参数。 此参数可确保可以从 Azure 资源管理器模板引用密钥保管库。
$vaultName = "contosovault"
$resourceGroup = "contosovaultrg"
$location = "local"
$secretName = "MySecret"
New-AzResourceGroup `
-Name $resourceGroup `
-Location $location
New-AzKeyVault `
-VaultName $vaultName `
-ResourceGroupName $resourceGroup `
-Location $location
-EnabledForTemplateDeployment
$secretValue = ConvertTo-SecureString -String '<Password for your virtual machine>' -AsPlainText -Force
Set-AzureKeyVaultSecret `
-VaultName $vaultName `
-Name $secretName `
-SecretValue $secretValue
运行上一个脚本时,输出包括机密 URI(统一资源标识符)。 记下此 URI。 在使用密钥保管库中的密码部署 Windows VM 模板中,需要引用此 URI。 将 101-vm-secure-password 文件夹下载到开发计算机上。 此文件夹包含 azuredeploy.json 文件和 azuredeploy.parameters.json 文件,这些文件将在后续步骤中需要。
请根据环境值修改azuredeploy.parameters.json文件。 特别关注的参数包括保管库名称、保管库资源组和机密 URI(由上一脚本生成)。 以下文件是参数文件的示例。
更新 azuredeploy.parameters.json 文件
根据环境,以 KeyVault URI、secretName、VM 的 adminUsername 值更新 azuredeploy.parameters.json 文件。 以下 JSON 文件显示了模板参数文件的示例:
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentParameters.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"adminUsername": {
"value": "demouser"
},
"adminPassword": {
"reference": {
"keyVault": {
"id": "/subscriptions/xxxxxx/resourceGroups/RgKvPwd/providers/Microsoft.KeyVault/vaults/KvPwd"
},
"secretName": "MySecret"
}
},
"dnsLabelPrefix": {
"value": "mydns123456"
},
"windowsOSVersion": {
"value": "2016-Datacenter"
}
}
}
模板部署
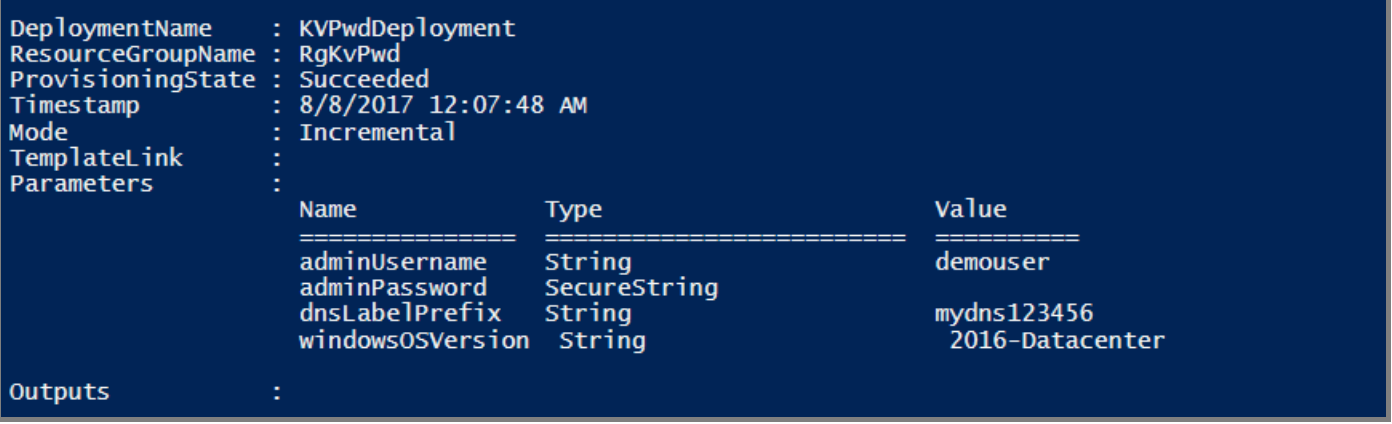
现在使用以下 PowerShell 脚本部署模板:
New-AzResourceGroupDeployment `
-Name KVPwdDeployment `
-ResourceGroupName $resourceGroup `
-TemplateFile "<Fully qualified path to the azuredeploy.json file>" `
-TemplateParameterFile "<Fully qualified path to the azuredeploy.parameters.json file>"
成功部署模板后,将生成以下输出: