本文介绍如何使用已安装 Key Vault 证书部署 Azure Stack Hub 虚拟机(VM)。
概述
证书用于许多方案,例如对 Active Directory 进行身份验证或加密 Web 流量。 可以将证书安全地存储为 Azure Stack Hub 密钥保管库中的机密。 使用 Azure Stack Hub Key Vault 的好处包括:
- 证书不会在脚本、命令行历史记录或模板中公开。
- 证书管理过程已简化。
- 你可以控制访问证书的密钥。
流程说明
以下步骤描述了将证书推送到 VM 所需的过程:
- 创建密钥保管库机密。
- 更新 azuredeploy.parameters.json 文件。
- 部署模板。
注释
你可以从 Azure Stack 开发工具包(ASDK)或通过 VPN 连接的外部客户端使用这些步骤。
先决条件
- 必须订阅包含 Key Vault 服务的套餐。
- 安装适用于 Azure Stack Hub 的 PowerShell。
- 配置 Azure Stack Hub 用户的 PowerShell 环境。
创建密钥保管库机密
以下脚本以 .pfx 格式创建证书,创建密钥保管库,并将证书作为机密存储在密钥保管库中。 机密的 contentType 必须设为 pfx。
重要
创建密钥保管库时必须使用 -EnabledForDeployment 该参数。 此参数可确保可以从 Azure 资源管理器模板引用密钥保管库。
# Create a certificate in the .pfx format
New-SelfSignedCertificate `
-certstorelocation cert:\LocalMachine\My `
-dnsname contoso.microsoft.com
$pwd = ConvertTo-SecureString `
-String "<Password used to export the certificate>" `
-Force `
-AsPlainText
Export-PfxCertificate `
-cert "cert:\localMachine\my\<certificate thumbprint that was created in the previous step>" `
-FilePath "<Fully qualified path to where the exported certificate can be stored>" `
-Password $pwd
# Create a key vault and upload the certificate into the key vault as a secret
$vaultName = "contosovault"
$resourceGroup = "contosovaultrg"
$location = "local"
$secretName = "servicecert"
$fileName = "<Fully qualified path to where the exported certificate can be stored>"
$certPassword = "<Password used to export the certificate>"
$fileContentBytes = get-content $fileName `
-Encoding Byte
$fileContentEncoded = [System.Convert]::ToBase64String($fileContentBytes)
$jsonObject = @"
{
"data": "$filecontentencoded",
"dataType" :"pfx",
"password": "$certPassword"
}
"@
$jsonObjectBytes = [System.Text.Encoding]::UTF8.GetBytes($jsonObject)
$jsonEncoded = [System.Convert]::ToBase64String($jsonObjectBytes)
New-AzResourceGroup `
-Name $resourceGroup `
-Location $location
New-AzKeyVault `
-VaultName $vaultName `
-ResourceGroupName $resourceGroup `
-Location $location `
-sku standard `
-EnabledForDeployment
$secret = ConvertTo-SecureString `
-String $jsonEncoded `
-AsPlainText -Force
Set-AzureKeyVaultSecret `
-VaultName $vaultName `
-Name $secretName `
-SecretValue $secret
运行此脚本时,输出包括机密 URI。 请记下此 URI,因为在将证书推送到 Windows 资源管理器模板中时必须引用此它。 将 vm-push-certificate-windows 模板文件夹下载到开发计算机。 此文件夹包含以下步骤中所需的 azuredeploy.json 和 azuredeploy.parameters.json 文件。
根据环境值修改 azuredeploy.parameters.json 文件。 重要参数是保管库名称、保管库资源组和机密 URI(由上一脚本生成)。 以下部分显示了参数文件的示例。
更新 azuredeploy.parameters.json 文件
根据您所在环境,使用机密 URI、、vaultName以及其他参数更新 VmName 文件。 以下 JSON 文件显示了模板参数文件的示例:
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentParameters.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"newStorageAccountName": {
"value": "kvstorage01"
},
"vmName": {
"value": "VM1"
},
"vmSize": {
"value": "Standard_D1_v2"
},
"adminUserName": {
"value": "demouser"
},
"adminPassword": {
"value": "demouser@123"
},
"vaultName": {
"value": "contosovault"
},
"vaultResourceGroup": {
"value": "contosovaultrg"
},
"secretUrlWithVersion": {
"value": "https://testkv001.vault.local.azurestack.external/secrets/testcert002/82afeeb84f4442329ce06593502e7840"
}
}
}
部署模板
使用以下 PowerShell 脚本部署模板:
# Deploy a Resource Manager template to create a VM and push the secret to it
New-AzResourceGroupDeployment `
-Name KVDeployment `
-ResourceGroupName $resourceGroup `
-TemplateFile "<Fully qualified path to the azuredeploy.json file>" `
-TemplateParameterFile "<Fully qualified path to the azuredeploy.parameters.json file>"
成功部署模板后,会显示以下输出:
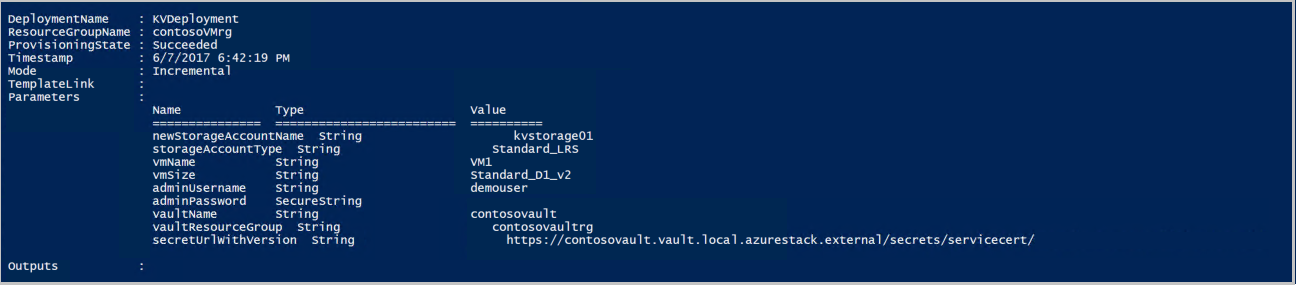
Azure Stack Hub 在部署期间将证书推送到 VM。 证书位置取决于 VM 的作系统:
- 在 Windows 中,证书将添加到 LocalMachine 证书位置,其中包含用户提供的证书存储。
- 在 Linux 中,证书位于 /var/lib/waagent 目录下,其中 X509 证书文件的文件名为 UppercaseThumbprint.crt,私钥为 UppercaseThumbprint.prv。
废止证书
停用证书是证书管理过程的一部分。 无法删除旧版证书,但可以使用 cmdlet 禁用它 Set-AzureKeyVaultSecretAttribute 。
以下示例演示如何禁用证书。 请为VaultName、Name和Version参数使用您自己的值。
Set-AzureKeyVaultSecretAttribute -VaultName contosovault -Name servicecert -Version e3391a126b65414f93f6f9806743a1f7 -Enable 0