本文中的步骤介绍如何运行示例应用 HelloKeyVault ,以便从 Azure Stack Hub 中的密钥保管库检索密钥和机密。
先决条件
如果通过 VPN 连接,则可以从基于 Windows 的外部客户端安装以下先决条件:
创建密钥保管库并注册应用
为示例应用程序做好准备:
- 在 Azure Stack Hub 中创建密钥保管库。
- 在 Microsoft Entra ID 中注册应用。
使用 Azure 门户或 PowerShell 为示例应用做好准备。
注释
默认情况下,PowerShell 脚本在 Active Directory 中创建新的应用。 您可以注册其中一个现有应用程序。
在运行以下脚本之前,请确保为aadTenantName和applicationPassword变量提供值。 如果未指定值 applicationPassword,此脚本将生成一个随机密码。
$vaultName = 'myVault'
$resourceGroupName = 'myResourceGroup'
$applicationName = 'myApp'
$location = 'local'
# Password for the application. If not specified, this script generates a random password during app creation.
$applicationPassword = ''
# Function to generate a random password for the application.
Function GenerateSymmetricKey()
{
$key = New-Object byte[](32)
$rng = [System.Security.Cryptography.RNGCryptoServiceProvider]::Create()
$rng.GetBytes($key)
return [System.Convert]::ToBase64String($key)
}
Write-Host 'Please log into your Azure Stack Hub user environment' -foregroundcolor Green
$tenantARM = "https://management.local.azurestack.external"
$aadTenantName = "FILL THIS IN WITH YOUR AAD TENANT NAME. FOR EXAMPLE: myazurestack.partner.onmschina.cn"
# Configure the Azure Stack Hub operator's PowerShell environment.
Add-AzEnvironment `
-Name "AzureStackUser" `
-ArmEndpoint $tenantARM
$TenantID = Get-AzsDirectoryTenantId `
-AADTenantName $aadTenantName `
-EnvironmentName AzureStackUser
# Sign in to the user portal.
Connect-AzAccount `
-EnvironmentName "AzureStackUser" `
-TenantId $TenantID `
$now = [System.DateTime]::Now
$oneYearFromNow = $now.AddYears(1)
$applicationPassword = GenerateSymmetricKey
# Create a new Azure AD application.
$identifierUri = [string]::Format("http://localhost:8080/{0}",[Guid]::NewGuid().ToString("N"))
$homePage = "https://contoso.com"
Write-Host "Creating a new AAD Application"
$ADApp = New-AzADApplication `
-DisplayName $applicationName `
-HomePage $homePage `
-IdentifierUris $identifierUri `
-StartDate $now `
-EndDate $oneYearFromNow `
-Password $applicationPassword
Write-Host "Creating a new AAD service principal"
$servicePrincipal = New-AzADServicePrincipal `
-ApplicationId $ADApp.ApplicationId
# Create a new resource group and a key vault in that resource group.
New-AzResourceGroup `
-Name $resourceGroupName `
-Location $location
Write-Host "Creating vault $vaultName"
$vault = New-AzKeyVault -VaultName $vaultName `
-ResourceGroupName $resourceGroupName `
-Sku standard `
-Location $location
# Specify full privileges to the vault for the application.
Write-Host "Setting access policy"
Set-AzKeyVaultAccessPolicy -VaultName $vaultName `
-ObjectId $servicePrincipal.Id `
-PermissionsToKeys all `
-PermissionsToSecrets all
Write-Host "Paste the following settings into the app.config file for the HelloKeyVault project:"
'<add key="VaultUrl" value="' + $vault.VaultUri + '"/>'
'<add key="AuthClientId" value="' + $servicePrincipal.ApplicationId + '"/>'
'<add key="AuthClientSecret" value="' + $applicationPassword + '"/>'
Write-Host
下图显示了用于创建密钥保管库的脚本的输出:
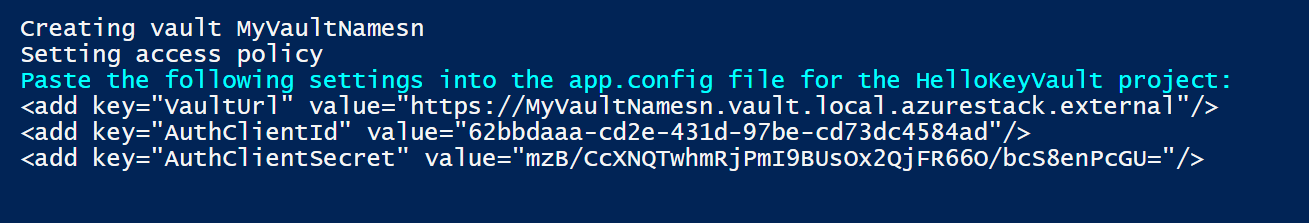
记下上一脚本返回的 VaultUrl、 AuthClientId 和 AuthClientSecret 值。 使用这些值运行 HelloKeyVault 应用程序。
下载并配置示例应用程序
从 Azure Key Vault 客户端示例页下载 Key Vault 示例 。 将 .zip 文件的内容解压缩到开发工作站上。 示例文件夹中有两个应用;本文使用 HelloKeyVault。
加载 HelloKeyVault 示例:
- 浏览到 Microsoft.Azure.KeyVault.Samples>示例>HelloKeyVault 文件夹。
- 在 Visual Studio 中打开 HelloKeyVault 应用。
配置示例应用程序
在 Visual Studio 中:
打开 HelloKeyVault\App.config 文件并查找
<appSettings>元素。使用创建密钥保管库时返回的值更新 VaultUrl、 AuthClientId 和 AuthCertThumbprint 密钥。 默认情况下,App.config 文件带有一个
AuthCertThumbprint占位符。 将此占位符替换为AuthClientSecret.<appSettings> <!-- Update these settings for your test environment --> <add key="VaultUrl" value="URL to your Vault" /> <add key="AuthClientId" value="Client Id of your Service Principal" /> <add key="AuthCertThumbprint" value="Thumbprint of the certificate used for authentication" /> <add key="TracingEnabled" value="false" /> </appSettings>重新生成解决方案。
运行应用
运行 HelloKeyVault 时,应用登录到 Microsoft Entra ID,然后使用 AuthClientSecret 令牌向 Azure Stack Hub 中的密钥保管库进行身份验证。
可以使用 HelloKeyVault 示例来:
- 对密钥和机密执行创建、加密、包装和删除等基本作。
- 将参数(例如
encrypt和decryptHelloKeyVault)传递给 Key Vault,并将指定的更改应用到密钥保管库。