本文逐步讲解如何在两个 Azure Stack Hub 环境中设置外部负载均衡器。 你可使用此配置管理不同的工作负载。 在本文中,你将跨两个独立的 Azure Stack Hub 实例将 F5 部署为全局负载均衡解决方案。 你还将跨两个实例部署在 NGINX 服务器中运行的负载均衡的 Web 应用。 它们将在 F5 虚拟设备的高可用性故障转移对之后运行。
你可在 f5-azurestack-gslb GitHub 存储库中找到 Azure 资源管理器模板。
F5 负载均衡概述
F5 硬件(负载均衡器)可能在 Azure Stack Hub 外部,位于托管 Azure Stack Hub 的数据中心内。 Azure Stack Hub 没有用于跨两个单独的 Azure Stack Hub 部署对工作负载进行负载均衡的本机功能。 F5 的 BIG-IP 虚拟版 (VE) 在两个平台上运行。 此设置通过复制支持应用程序服务来支持 Azure 和 Azure Stack Hub 体系结构之间的奇偶校验。 你可在一个环境中开发应用,然后将其移至另一个环境。 你还可对整个生产就绪的 Azure Stack Hub 执行镜像操作,包括相同的 BIG-IP 配置、策略和应用程序服务。 借助该方法,不再需要进行无数小时的应用程序重构和测试,并能够专注于编写代码。
保护应用程序及其数据通常是开发人员在将应用移至公有云时要考虑的问题。 但不一定要这样做。 你可在 Azure Stack Hub 环境中生成应用,而安全架构师则在 F5 的 Web 应用程序防火墙 (WAF) 上配置必要的设置。 因为知道应用程序将受到相同的行业领先 WAF 的保护,所以可在 Azure Stack Hub 中复制整个堆栈。 使用相同的策略和规则集,就不会存在因使用不同的 WAF 而可能会产生的任何安全薄弱环节或漏洞。
Azure Stack Hub 具有独立于 Azure 的市场。 仅可添加特定项目。 在这种情况下,你可在每个 Azure Stack Hub 上创建一个新的资源组并部署已经可用的 F5 虚拟设备。 在此处,你将看到需要提供公共 IP 地址用于允许两个 Azure Stack Hub 实例之间的网络连接。 实质上,它们都是孤岛,而公共 IP 可让它们在两个位置之间进行通信。
BIG-IP VE 先决条件
将 F5 BIG-IP VE - ALL (BYOL, 2 Boot Locations) 下载到每个 Azure Stack Hub 市场中。 如果它们在门户中不可用,请联系云操作员。
可在以下 GitHub 存储库中找到 Azure 资源管理器模板: https://github.com/Mikej81/f5-azurestack-gslb 。
在每个实例上部署 F5 BIG-IP VE
部署到 Azure Stack Hub 实例 A 和实例 B。
登录到 Azure Stack Hub 用户门户。
选择“+ 创建资源”。
通过键入
F5来搜索市场。选择“F5 BIG-IP VE – ALL (BYOL, 2 Boot Locations)” 。
在下一页的底部,选择“创建”。
创建一个名为“F5-GSLB”的新资源组。
使用以下值作为示例来完成部署:
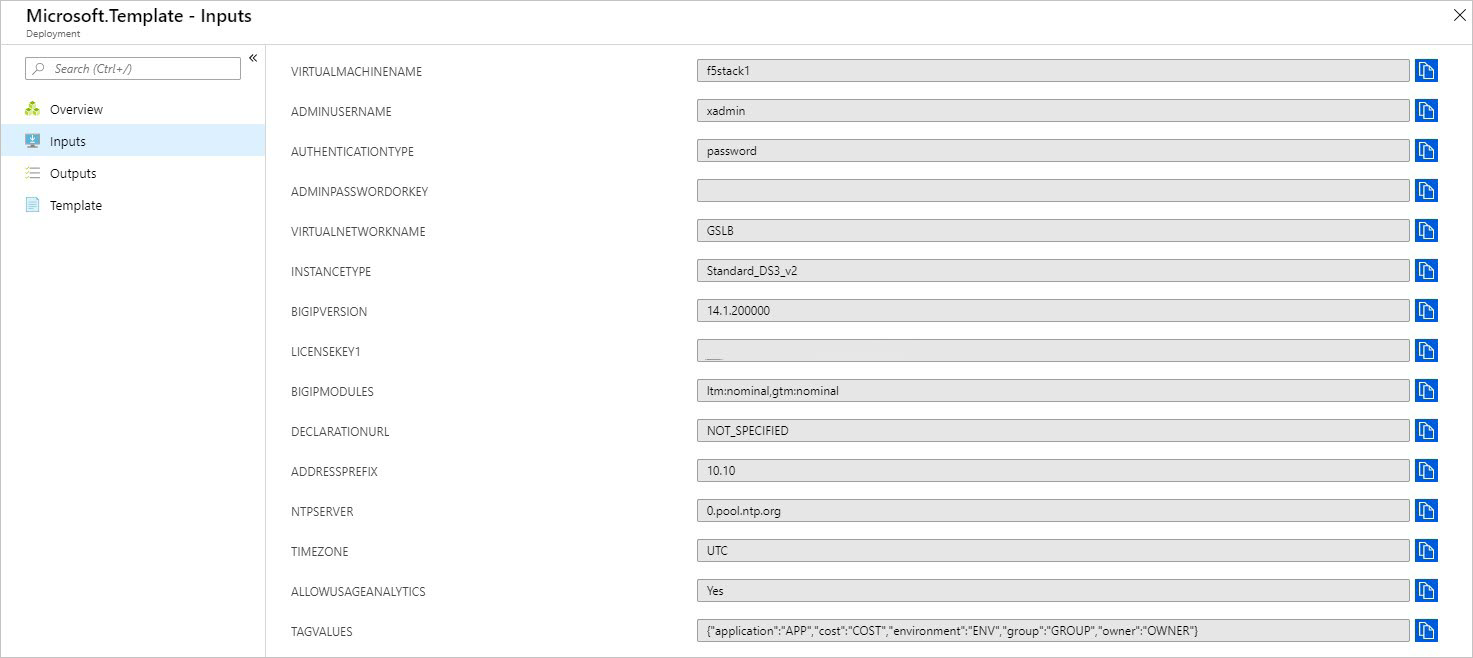
验证部署是否成功完成。
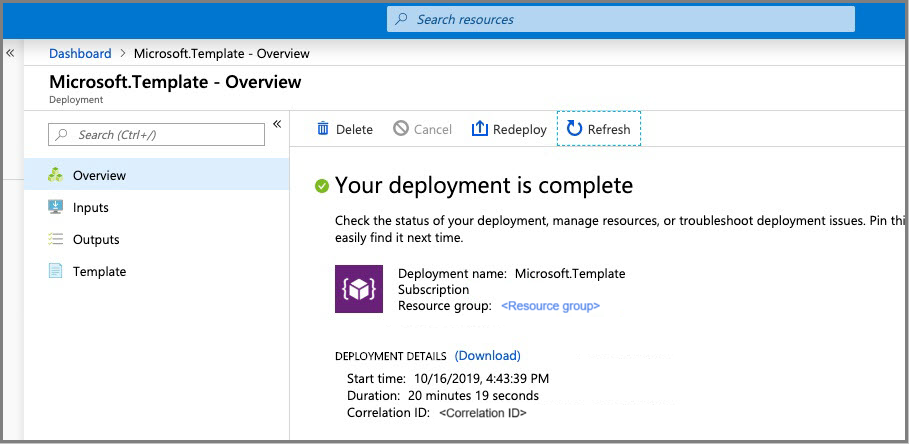
注意
每个 BIG-IP 部署大约需要 20 分钟。
配置 BIG-IP 设备
执行 Azure Stack Hub A 和 B 需要完成的步骤。
登录到 Azure Stack Hub 实例 A 上的 Azure Stack Hub 用户门户,查看通过 BIG-IP 模板部署创建的资源。
遵循 F5 上有关 BIG-IP 配置项的说明。
配置 BIG-IP 宽泛 IP 列表以侦听部署到 Azure Stack Hub 实例 A 和 B 的设备。有关说明,请参阅 BIG-IP GTM 配置。
验证 BIG-IP 设备的故障转移。 在测试系统上,将 DNS 服务器配置为使用以下值:
- Azure Stack Hub 实例 A =
f5stack1-ext公共 IP 地址 - Azure Stack Hub 实例 B =
f5stack1-ext公共 IP 地址
- Azure Stack Hub 实例 A =
浏览到
www.contoso.com,浏览器会加载 NGINX 默认页。
创建 DNS 同步组
启用根帐户以建立信任。 请遵循更改系统维护帐户密码 (11.x-15.x) 中的说明。 设置信任(证书交换)后,请禁用根帐户。
登录到 BIG-IP 并创建 DNS 同步组。 有关说明,请参阅创建 BIG-IP DNS 同步组。
注意
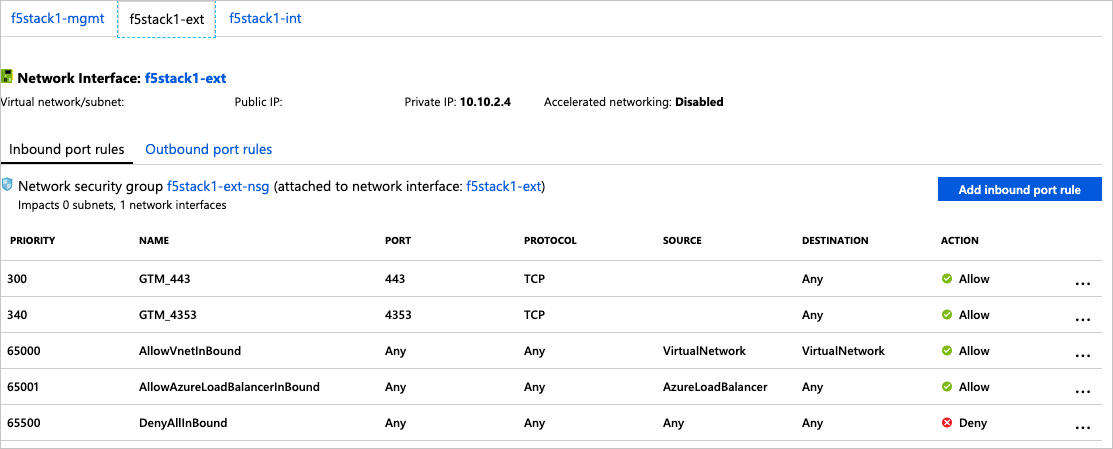
可在 F5-GSLB 资源组中找到 BIP-IP 设备的本地 IP。 网络接口为“f5stack1-ext”,而你可连接到公共 IP 或专用 IP(取决于访问权限)。
选择新资源组“F5-GSLB”并选择“f5stack1”虚拟机,然后在“设置”下选择“网络”。
安装后配置
安装后,需要配置 Azure Stack Hub NSG 并锁定源 IP 地址。
建立信任后,禁用端口 22。
当系统联机时,阻止源 NSG。 管理 NSG 应锁定到管理源,外部 (4353/TCP) NSG 应锁定到其他实例以进行同步。在部署带有虚拟服务器的应用程序前,还应锁定 443。
GTM_DNS 规则设置为允许端口 53 (DNS) 流量进入,且 BIG-IP 解析程序将立即开始工作。 侦听器已创建。
在 Azure Stack Hub 环境中部署基本 Web 应用程序工作负荷,以在 BIG-IP 之后进行负载均衡。 可从在 Docker 上部署 NGINX 和 NGINX Plus 中找到使用 NGNIX 服务器的示例。
注意
在 Azure Stack Hub A 和 Azure Stack Hub B 上部署 NGNIX 实例。
在每个 Azure Stack Hub 实例中将 NGINX 部署到 Ubuntu VM 上的 Docker 容器中后,请验证是否可以访问服务器上的默认网页。
登录到 BIG-IP 设备的管理界面。 在此示例中,使用 f5-stack1-ext 公共 IP 地址。
通过 BIG-IP 公开访问 NGINX。
- 在此任务中,将使用虚拟服务器和池配置 BIG-IP,以允许对 WordPress 应用程序的入站 Internet 访问。 首先,需要为 NGINX 实例标识专用 IP 地址。
登录到 Azure Stack Hub 用户门户。
选择 NGINX 网络接口。
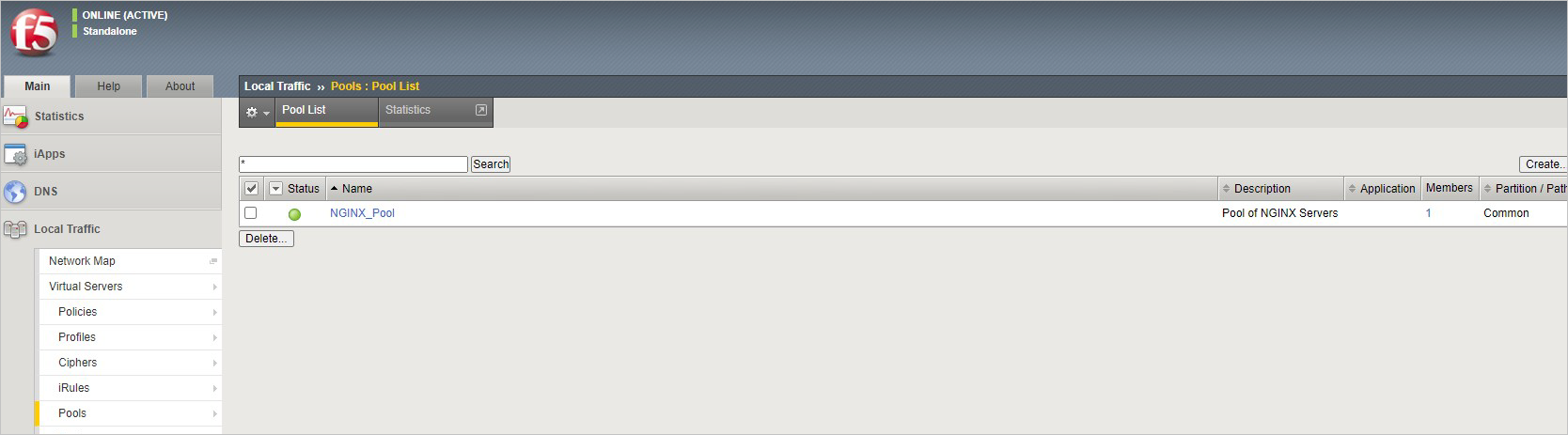
在 BIG-IP 控制台中,转到“本地流量”>“池”>“池列表”,然后选择“+”。 使用表中的值配置池。 将所有其他字段保留为默认值。
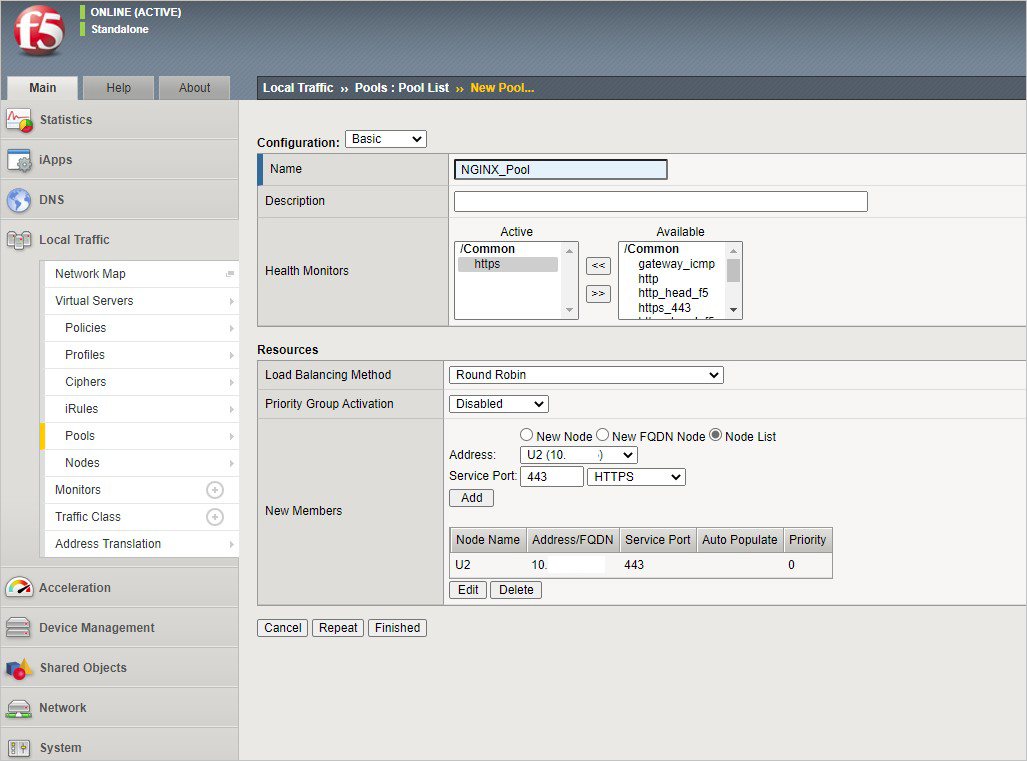
密钥 值 名称 NGINX_Pool 运行状况监视器 HTTPS 节点名称 NGINX 地址 <NGINX 专用 IP 地址> 服务端口 443 选择“完成”。 如果正确配置,池状态为绿色。
现在,你需要配置虚拟服务器。 为此,你首先需要找到 F5 BIG-IP 的专用 IP。
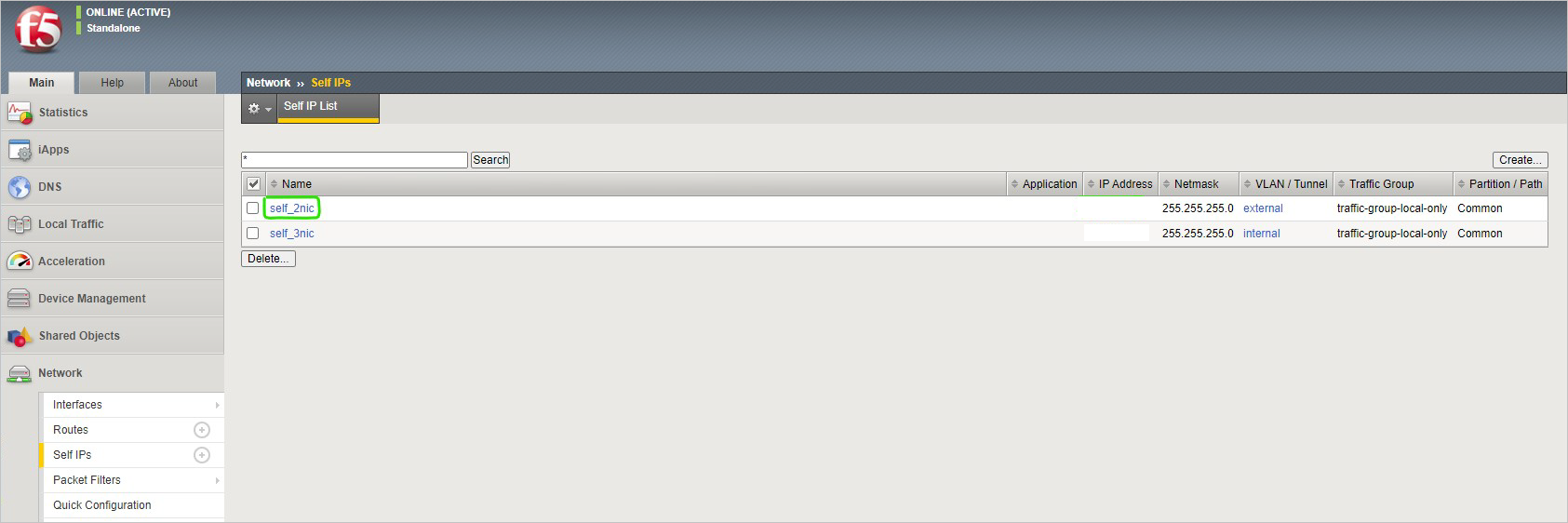
在 BIG-IP 控制台中,转到“网络”>“Self IP”并记下 IP 地址。
通过转到“本地流量”>“虚拟服务器”>“虚拟服务器列表”并选择 + 来创建虚拟服务器。 使用表中的值配置池。 将所有其他字段保留为默认值。
键 值 名称 NGINX 目标地址 <BIG-IP 的自 IP 地址> 服务端口 443 SSL 配置文件(客户端) clientssl 源地址转换 自动映射 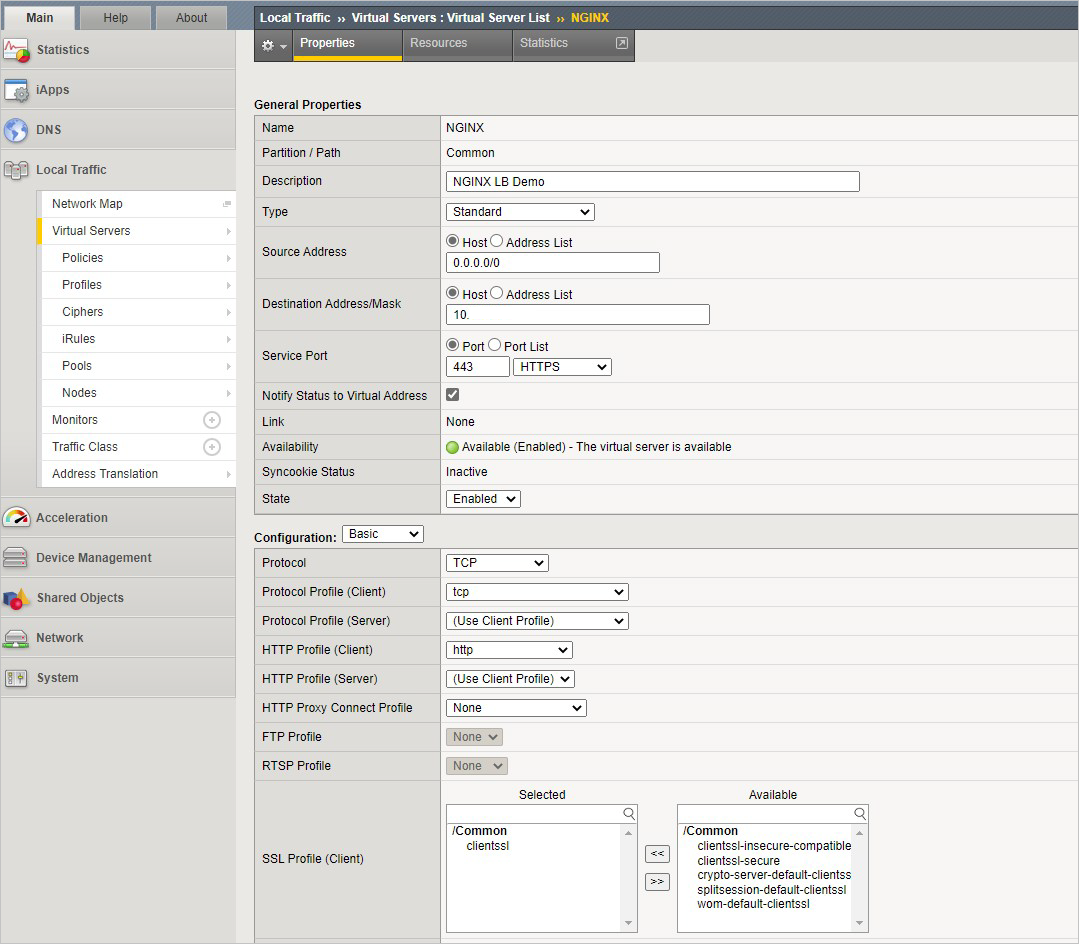
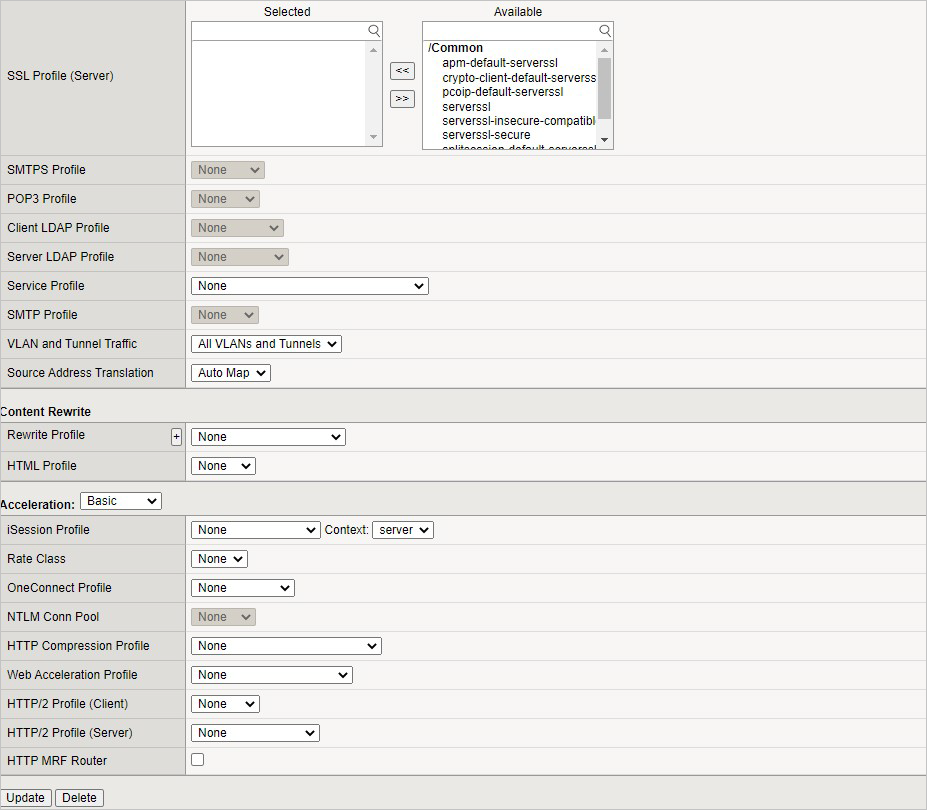
现在,你已完成 NGINX 应用程序的 BIG-IP 配置。 若要验证功能是否正常,请浏览站点并验证 F5 统计信息。
打开浏览器以转到
https://<F5-public-VIP-IP>,并确保它显示 NGINX 默认页。
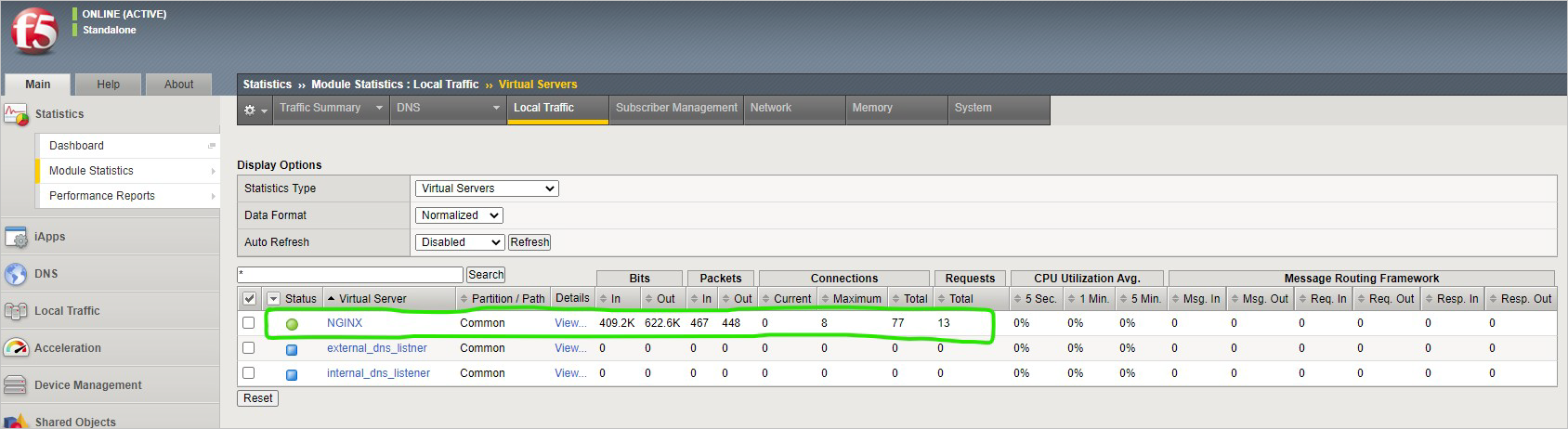
现在,通过导航到“统计信息”>“模块统计信息”>“本地流量”检查虚拟服务器的统计信息,从而验证流量。
在“统计信息类型”下,选择“虚拟服务器”。
更多信息
可找到有关使用 F5 的一些参考文章: