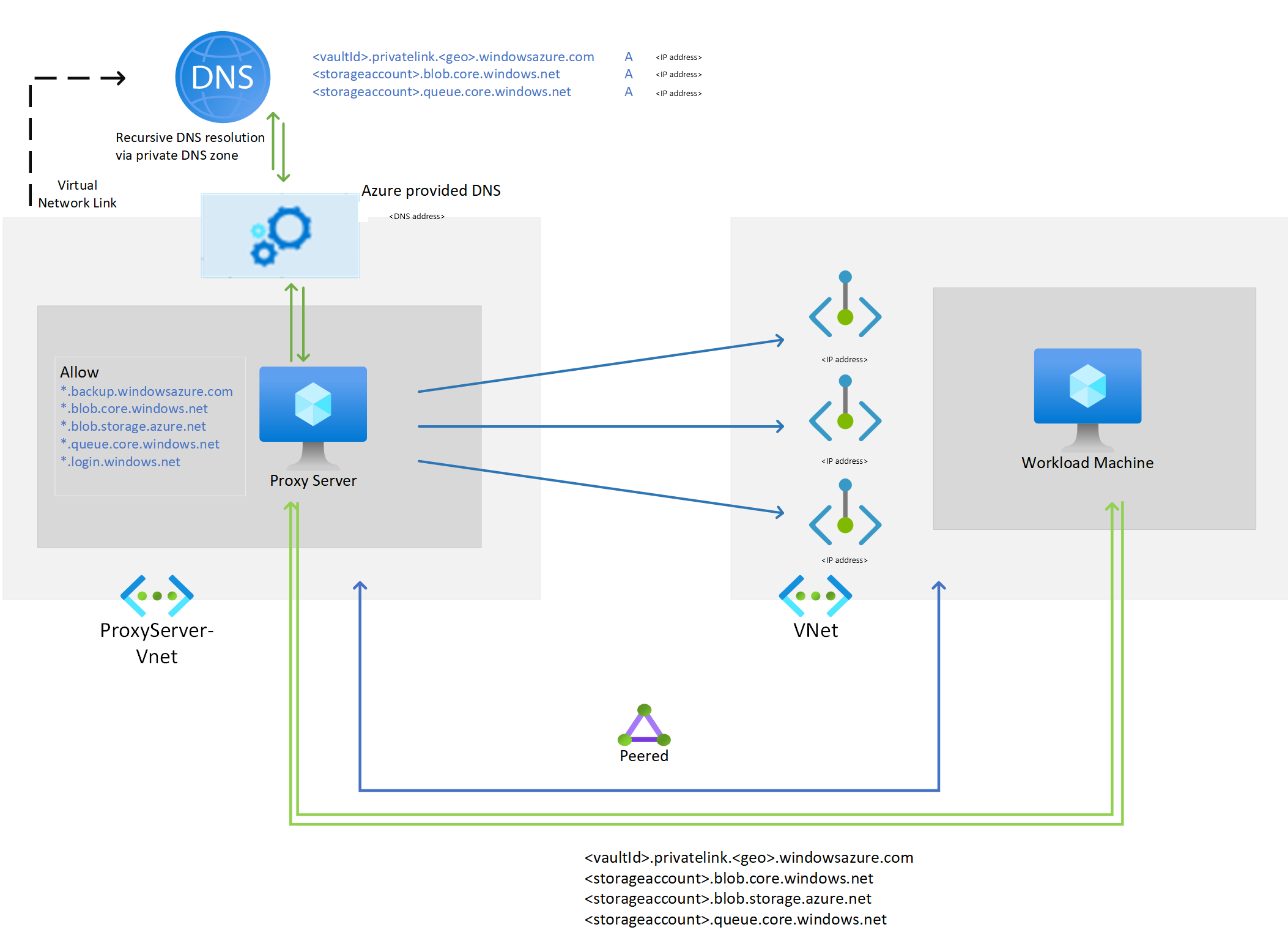
本文提供有关 为 Azure 备份创建专用终结点 的过程以及专用终结点有助于维护资源安全性的方案的信息。
注释
Azure 备份现在为创建专用终结点提供了一种新的体验。 了解详细信息。
在您开始之前
在继续创建专用终结点之前,请确保已阅读 先决条件 和支持 的方案 。
这些详细信息可以帮助您理解在为保管库创建专用终结点之前需要满足的限制条件和先决条件。
为备份快速创建专用终结点
以下部分讨论了在虚拟网络中创建和使用 Azure 备份的专用终结点所涉及的步骤。
重要
强烈建议按照本文档中所述的相同顺序执行步骤。 未能这样做可能会导致保管库无法使用专用终结点,并需要使用新保管库重新启动整个流程。
创建恢复服务保管库
只能为恢复服务保管库创建专用终结点,这些保管库没有受保护的任何项(或者以前未尝试对其进行保护或注册任何项)。 因此,建议创建一个新的保管库来开始。 有关创建新保管库的详细信息,请参阅 “创建和配置恢复服务保管库”。
请参阅 此部分 ,了解如何使用 Azure 资源管理器客户端创建保管库。 这会创建已启用其托管标识的保管库。
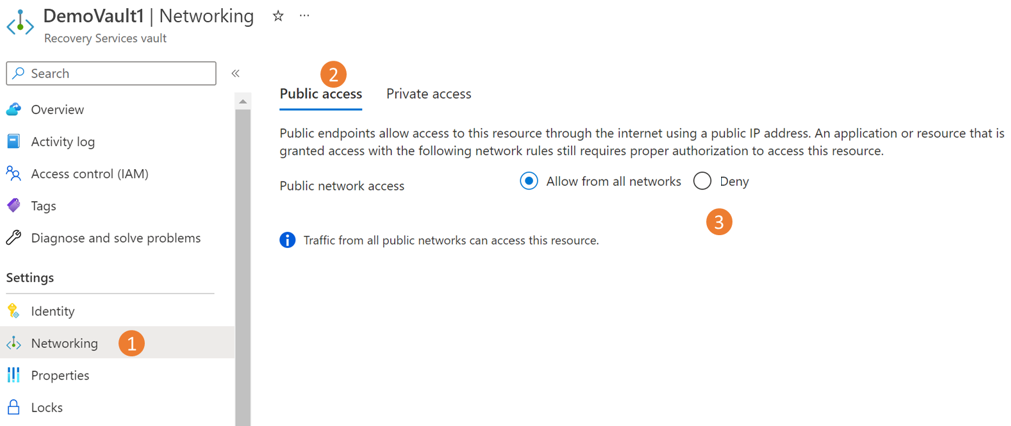
拒绝对保管库的公用网络访问
可以将保管库配置为拒绝来自公用网络的访问。
执行以下步骤:
转到“保管库”>“网络”。
在“公共访问”选项卡上,选择“拒绝”以阻止来自公用网络的访问。
注释
- 在您拒绝访问后,仍然可以访问保险库,但不能将数据从/移入不包含专用终结点的网络。 有关详细信息,请参阅创建用于 Azure 备份的专用终结点。
- 如果公共访问被拒绝且未启用专用终结点,则备份操作会成功,但所有工作负载的还原操作都会失败(虚拟机除外)。 不过,虚拟机的项级恢复也会失败。 请确保仔细配置网络限制。
- 目前不支持禁止公共访问的跨区域还原保管库。
选择“应用”保存更改。
为保管库启用托管标识
托管标识允许保管库创建和使用专用终结点。 本部分介绍如何为保管库启用托管标识。
转到恢复服务保管库>Identity。
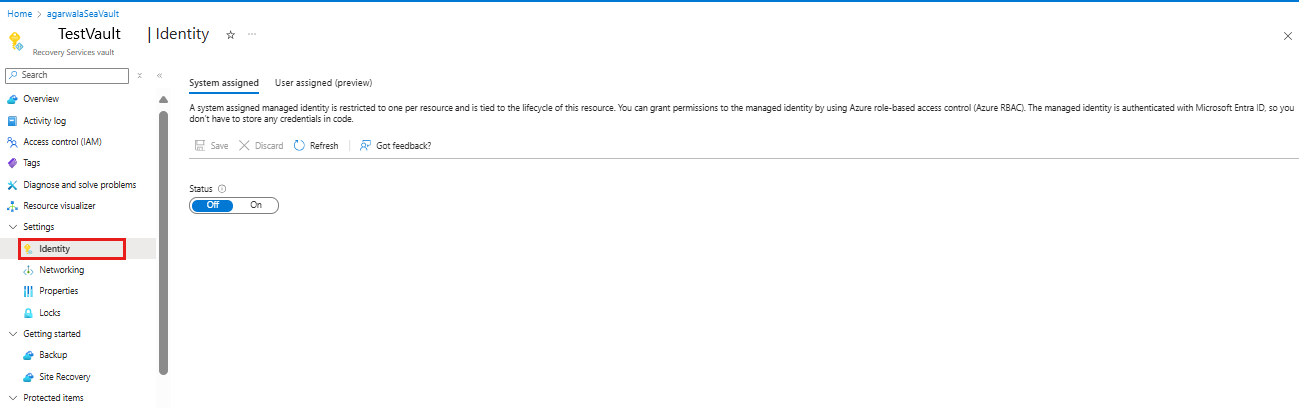
将“状态”更改为“开”,然后选择“保存” 。
生成 对象 ID ,即保管库的托管标识。
注释
启用托管身份后,必须不得禁用(甚至暂时禁用)。 禁用托管标识可能导致出现不一致的行为。
向保管库授予创建所需专用终结点的权限
若要为 Azure 备份创建所需的专用终结点,保管库(保管库的托管标识)必须有权访问以下资源组:
- 包含目标 VNet 的资源组
- 要在其中创建专用终结点的资源组
- 包含专用 DNS 区域的资源组,详述 此处
我们建议将这三个资源组的“参与者”角色授予给保管库(托管标识)。 以下步骤说明如何针对特定资源组执行此作(这需要针对三个资源组中的每一个执行此作):
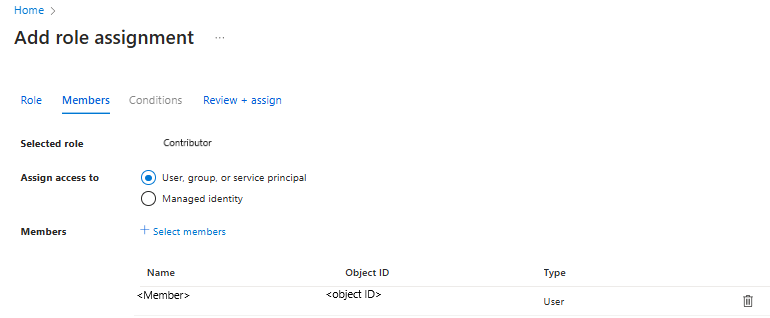
转到资源组,导航到左侧栏中的 访问控制(IAM )。
进入 访问控制后,转到 “添加角色分配”。
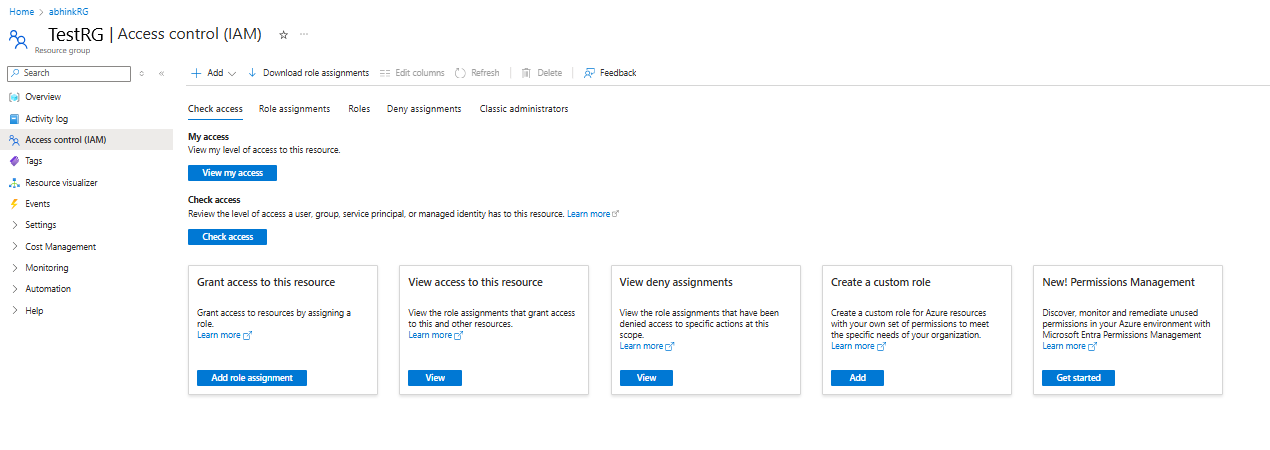
在“添加角色分配”窗格中,选择贡献者作为角色,并使用保管库的名称作为主体。 选择保管库,然后在完成后选择“ 保存 ”。
若要更精细地管理权限,请参阅 手动创建角色和权限。
为 Azure 备份创建专用终结点
本部分介绍如何为保管库创建专用终结点。
导航到上面创建的保管库,转到左侧导航栏上的网络设置,然后单击私有访问。 选择顶部的 “+专用终结点 ”,开始为此保管库创建新的专用终结点。
在 创建专用终结点 过程中,需要指定创建专用终结点连接的详细信息。
基本信息:填写专用终结点的基本详细信息。 该区域应与保管库及备份资源所在的区域相同。
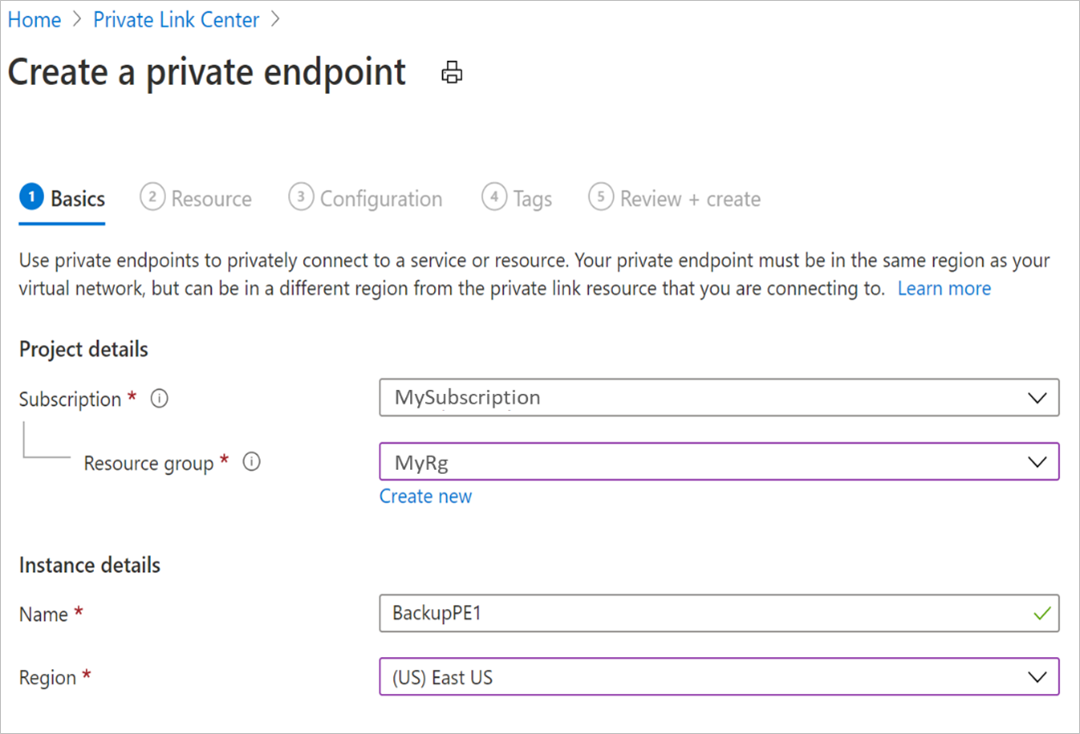
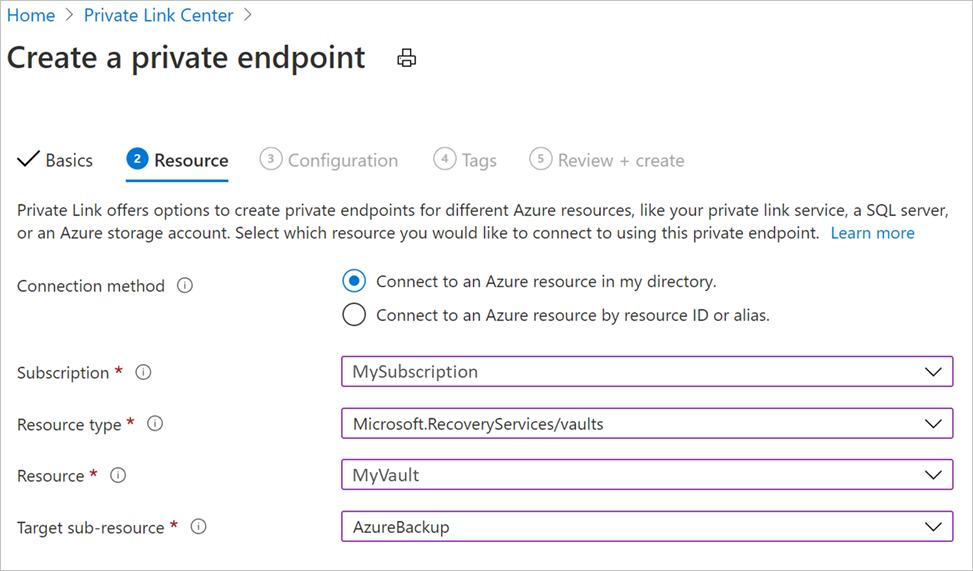
资源:此选项卡要求选择要为其创建连接的 PaaS 资源。 从所需订阅的资源类型中选择 Microsoft.RecoveryServices/vault 。 完成后,选择恢复服务保管库的名称作为 资源 ,选择 AzureBackup 作为 目标子资源。
虚拟网络:在配置中,指定要在其中创建专用终结点的虚拟网络和子网。 这是虚拟机所在的虚拟网络。
若要私下连接,需要所需的 DNS 记录。 可以根据网络设置选择以下方案之一:
- 将专用终结点与专用 DNS 区域集成:如果要集成,请选择 “是 ”。
- 使用自定义 DNS 服务器:如果要使用自己的 DNS 服务器,请选择 “否 ”。
稍后将介绍管理这两个 DNS 记录的方法。
(可选)可以为专用终结点添加标记。
输入详细信息后,继续“查看 + 创建”。 验证完成后,选择“ 创建 ”以创建专用终结点。
批准专用终结点
如果创建专用终结点的用户也是恢复服务保管库的所有者,则会自动批准上面创建的专用终结点。 否则,保管库的所有者必须先批准专用终结点,然后才能使用它。 本部分讨论通过 Azure 门户手动批准专用终结点。
请参阅 使用 Azure 资源管理器客户端手动批准专用终结点 ,以使用 Azure 资源管理器客户端批准专用终结点。
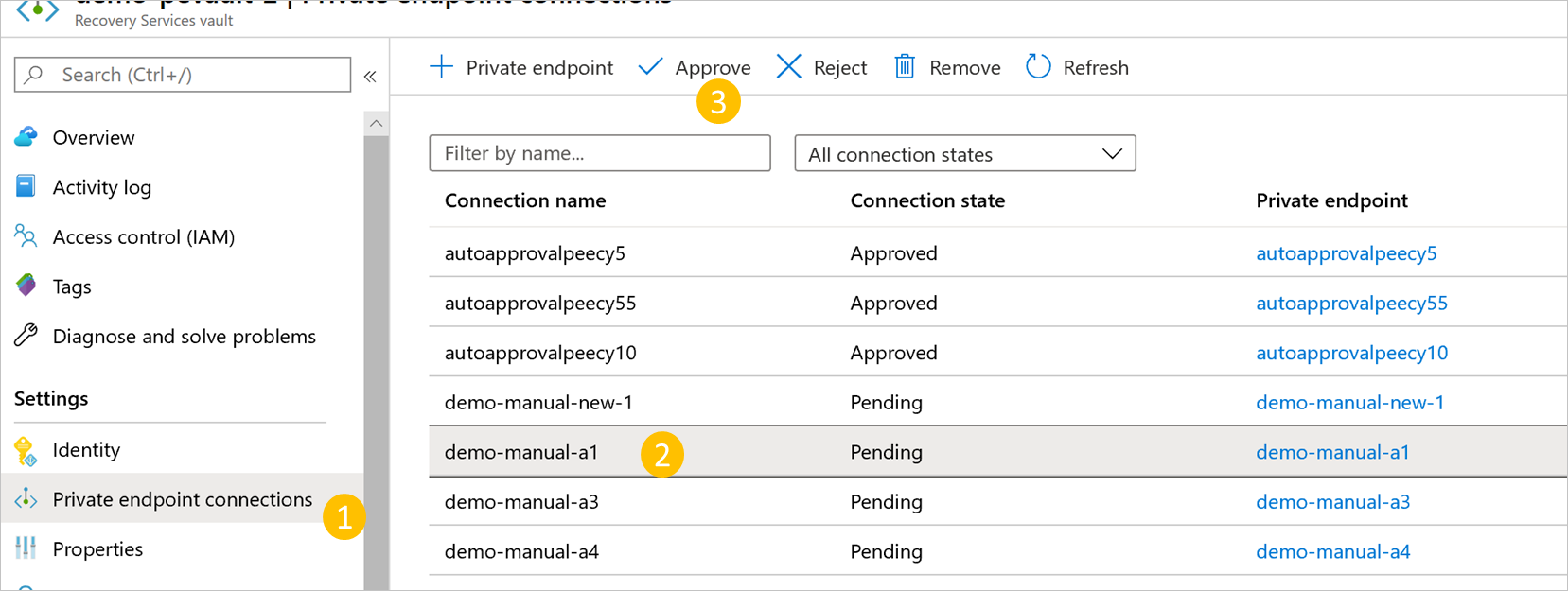
在您的恢复服务保管库中,导航到左侧栏中的专用终结点连接。
选择要批准的专用终结点连接。
选择顶部栏中的 “批准 ”。 如果想要拒绝或删除终结点连接,还可以选择“ 拒绝 ”或 “删除 ”。
管理 DNS 记录
如前所述,需要专用 DNS 区域或服务器中所需的 DNS 记录才能以私密方式连接。 可以直接将专用终结点与 Azure 专用 DNS 区域集成,也可以使用自定义 DNS 服务器根据网络首选项来实现此目的。 这需要针对所有三个服务完成:备份、Blob 和队列。
此外,如果 DNS 区域或服务器存在于与包含专用终结点的订阅不同的订阅中,另一 个订阅中存在 DNS 服务器/DNS 区域时,也请参阅“创建 DNS 条目”。
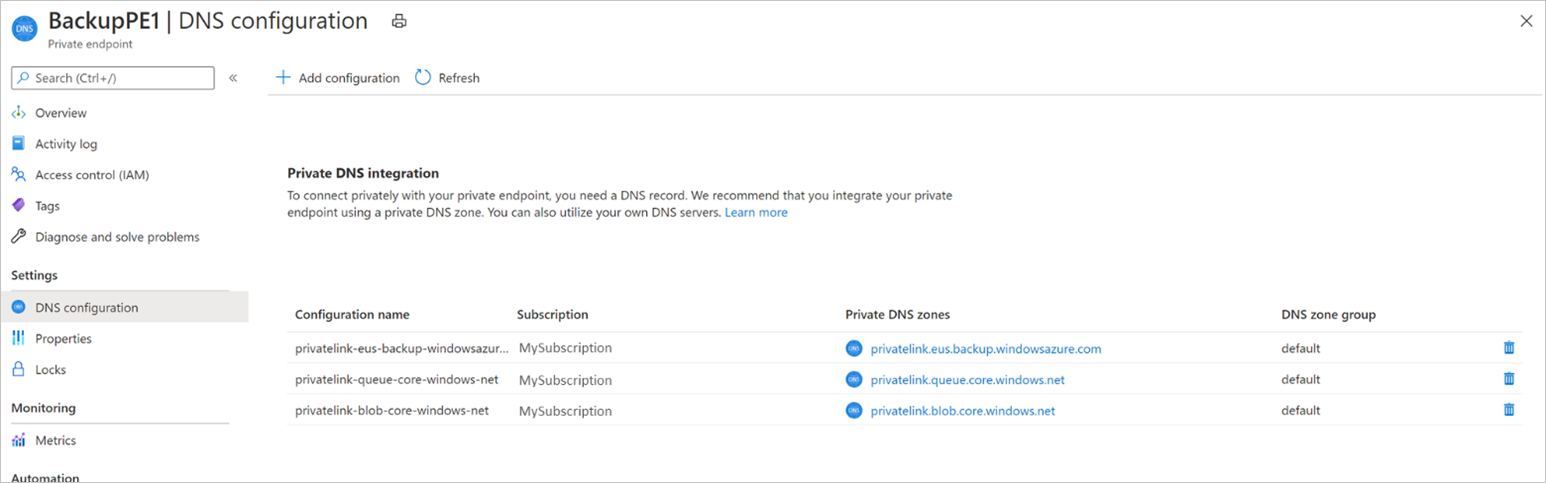
将专用终结点与 Azure 专用 DNS 区域集成时
如果选择将专用终结点与专用 DNS 区域集成,Azure 备份服务将添加所需的 DNS 记录。 可以查看专用终结点的 DNS 配置 下正在使用的专用 DNS 区域。 如果这些 DNS 区域不存在,则会在创建专用终结点时自动创建它们。
注释
分配给保管库的托管标识应有权在 Azure 专用 DNS 区域中添加 DNS 记录。
但是,必须验证虚拟网络(其中包含要备份的资源)是否已与所有三个专用 DNS 区域正确链接,如下所示。
注释
如果使用代理服务器,则可以选择跳过代理服务器或通过代理服务器执行备份。 若要跳过代理服务器,请继续阅读以下各部分。 若要使用代理服务器执行备份,请参阅恢复服务保管库的代理服务器设置详细信息。
验证专用 DNS 区域中的虚拟网络链接
对于上面列出的 每个专用 DNS 区域(用于备份、Blob 和队列),请执行以下操作:
导航到左侧导航栏上的相应 虚拟网络链接 选项。
您应该能够看到为您创建了专用终结点的虚拟网络的条目,如下所示:
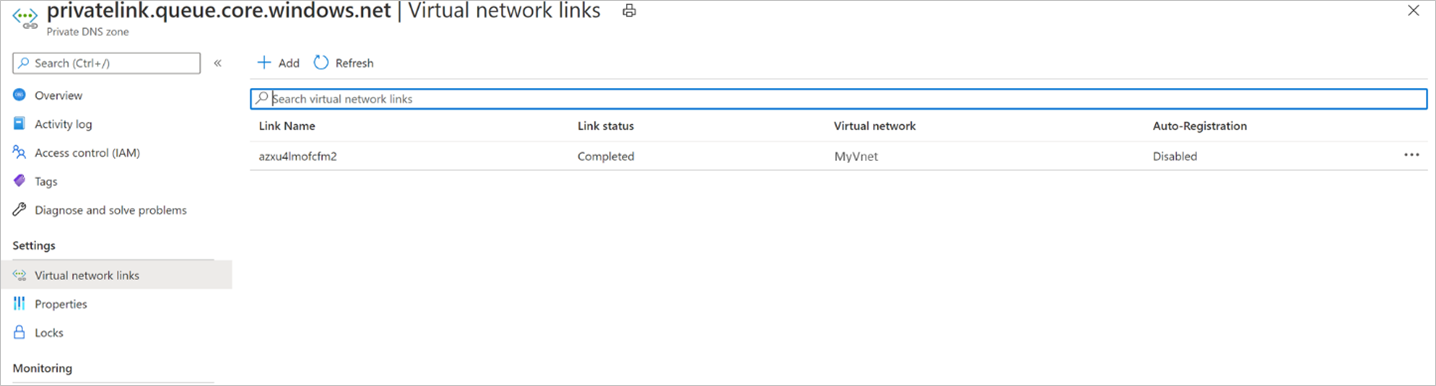
如果您未看到条目,请为没有条目的所有 DNS 区域添加虚拟网络链接。
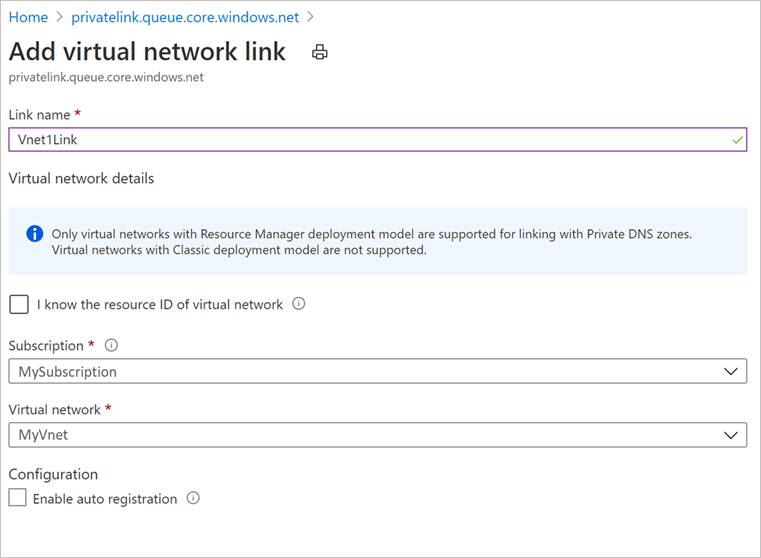
使用自定义 DNS 服务器或主机文件时
如果使用自定义 DNS 服务器,则可以使用备份服务、blob 和队列 FQDN 的条件转发器以将 DNS 请求重定向到 Azure DNS (168.63.129.16)。 Azure DNS 将其重定向到 Azure 专用 DNS 区域。 在此类设置中,请确保存在 Azure 专用 DNS 区域的虚拟网络链接,如 本部分所述。
下表列出了 Azure 备份所需的 Azure 专用 DNS 区域:
区域 服务 privatelink.<geo>.backup.windowsazure.cn备份 privatelink.blob.core.chinacloudapi.cnBlob privatelink.queue.core.chinacloudapi.cn队列 注释
在上述文本中,
<geo>分别引用区域代码(例如 bjb2 和 sha2 分别用于中国北部 2 和中国东部 2)。 参考以下区域代码列表:如果正在使用自定义 DNS 服务器或主机文件,且未设置 Azure 专用 DNS 区域,则需要将专用终结点所需的 DNS 记录添加到 DNS 服务器或主机文件中。
对于备份服务:导航到创建的专用终结点,然后转到 DNS 配置。 然后,为每个 FQDN 和 IP 添加一个条目,将其作为 DNS 区域中的Type A记录显示以备份。
如果正在使用主机文件进行名称解析,请根据格式 -
<private ip><space><backup service privatelink FQDN>在主机文件中为每个 IP 和 FQDN 创建相应条目。对于 Blob 和队列:Azure 备份使用托管标识权限为 Blob 和队列创建专用终结点。 Blob 和队列的专用终结点遵循标准命名模式,它们以
<the name of the private endpoint>_ecs或<the name of the private endpoint>_prot开头,并分别以_blob和_queue为后缀。按照上述模式导航到 Azure 备份创建的专用终结点,然后转到 DNS 配置。 然后,为每个 FQDN 和 IP 添加一个条目,将其作为 DNS 区域中的Type A记录显示以备份。
如果正在使用主机文件进行名称解析,请根据格式 -
<private ip><space><blob/queue FQDN>在主机文件中为每个 IP 和 FQDN 创建相应条目。
注释
Azure 备份可能会为备份数据的保管库分配新的存储帐户,且扩展或代理需要访问相应的终结点。 有关如何在注册和备份后添加更多 DNS 记录的详细信息,请参阅 “使用专用终结点进行备份”部分中的指南 。
使用私有终结点进行备份
当 VNet 中为保管库创建的专用终结点获得批准后,即可开始使用它们来执行备份和还原。
重要
在继续之前,请确保已成功完成文档中的上述所有步骤。 概括起来,必须完成以下清单中的步骤:
- 已创建新的恢复服务保管库
- 已启用保管库以使用系统分配的托管标识
- 已为保管库的托管身份分配了相关权限
- 为保管库创建了专用终结点
- 已批准专用终结点(如果未被自动批准)
- 确保适当添加所有 DNS 记录(自定义服务器的 Blob 和队列记录除外),以下部分将讨论这些记录)
检查 VM 连接
在锁定网络中的 VM 中,确保满足以下条件:
- 该 VM 应可以访问 Microsoft Entra ID。
- 在虚拟机中对备份 URL () 执行
xxxxxxxx.privatelink.<geo>.backup.windowsazure.cn,以确保连接正常。 此命令应返回虚拟网络中分配的专用 IP。
配置备份
确保符合上述清单中的要求并可以成功进行网络访问后,可以继续配置将工作负载备份到保管库的设置。 如果使用自定义 DNS 服务器,则在配置第一个备份后,需要为可用的 Blob 和队列添加 DNS 条目。
首次注册后的 Blob 和队列的 DNS 记录(仅适用于自定义 DNS 服务器/主机文件)
在为启用了专用终结点的保管库中的至少一个资源配置备份后,请按如下所述为 Blob 和队列添加所需的 DNS 记录。
导航到您的资源组,并搜索您创建的私有终结点。
除了你提供的专用终结点名称之外,还将看到另外两个正在创建的专用终结点。 它们以
<the name of the private endpoint>_ecs开头,并分别以_blob和_queue作为后缀。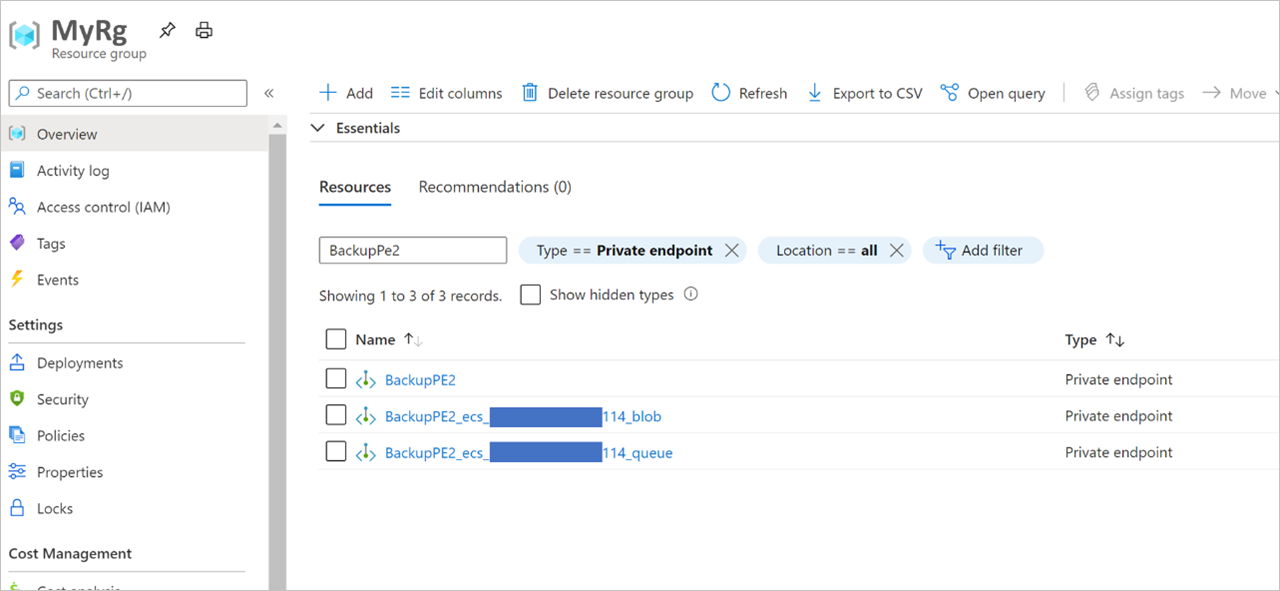
导航到每个专用终结点。 在两个专用终结点的每个 DNS 配置选项中,你将看到一条包含 FQDN 和 IP 地址的记录。 除了前面所述的 DNS 服务器之外,还将这两项添加到自定义 DNS 服务器。 如果使用主机文件,请根据以下格式为每个 IP/FQDN 在主机文件中输入相应的条目:
<private ip><space><blob service privatelink FQDN>
<private ip><space><queue service privatelink FQDN>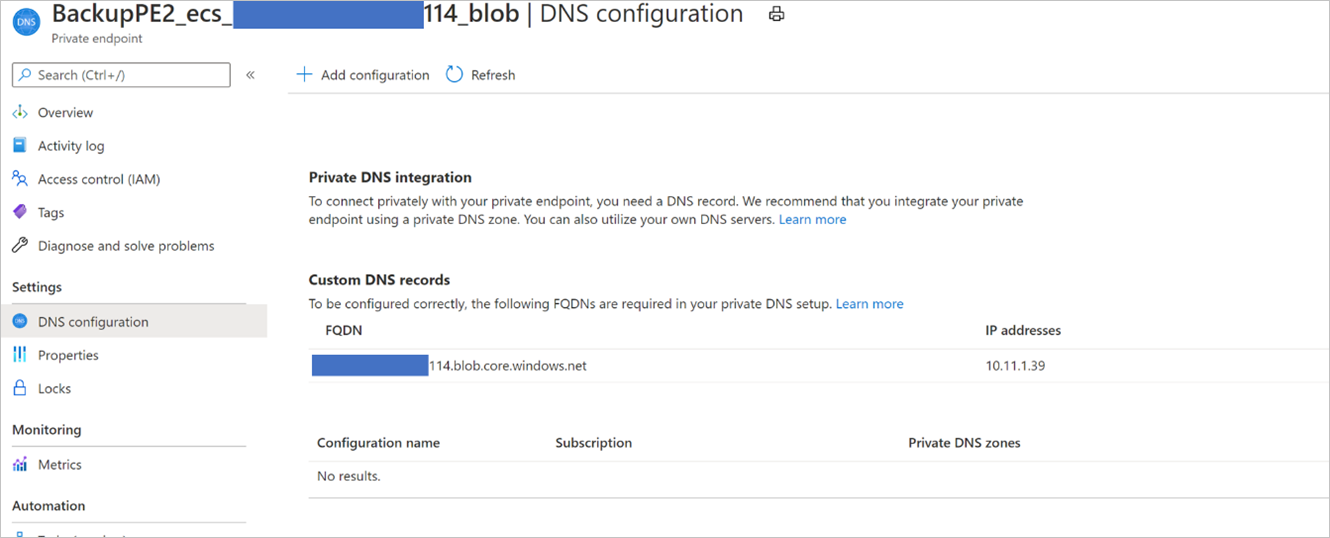
除了上述项外,第一次备份后还需要另一个条目, 稍后将对此进行讨论。
在 Azure VM 中备份和还原工作负载(SQL 和 SAP HANA)
创建并批准专用终结点后,无需在客户端进行任何其他更改即可使用该专用终结点(除非使用了 SQL 可用性组,本部分稍后将对此予以介绍)。 从受保护的网络到保管库的所有通信和数据传输都将通过专用终结点执行。 但是,如果在将某个服务器(SQL 或 SAP HANA)注册到保管库之后删除了该保管库的专用终结点,则需要向该保管库重新注册容器。 不需要停止对它们的保护。
首次备份后的 Blob 的 DNS 记录(仅适用于自定义 DNS 服务器/主机文件)
运行首次备份后,如果你使用的是自定义 DNS 服务器(未启用条件转发),备份有可能会失败。 如果发生这种情况:
导航到您的资源组,并搜索您创建的私有终结点。
除了前面讨论的三个专用终结点之外,现在还会看到第四个专用终结点,其名称以
<the name of the private endpoint>_prot开头,并以_blob结尾。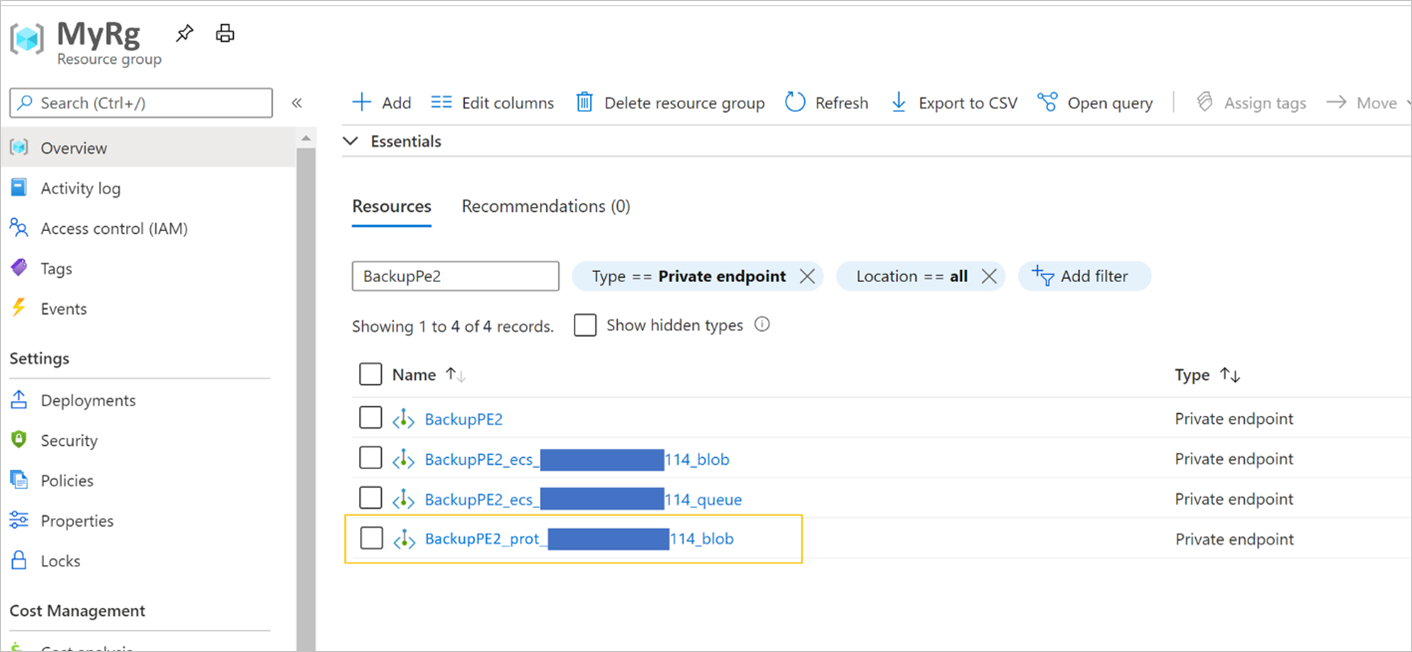
导航到此新的专用终结点。 在 DNS 配置选项中,你将看到包含 FQDN 和 IP 地址的记录。 除了前面所述的服务器之外,将这些条目添加到您的专用 DNS 服务器。
如果使用主机文件,请根据以下格式为每个 IP 和 FQDN 创建主机文件中的相应条目:
<private ip><space><blob service privatelink FQDN>
注释
此时,应该可以从 VM 运行 nslookup,并在处理完保管库的备份和存储 URL 后对专用 IP 地址进行解析。
使用 SQL 可用性组时
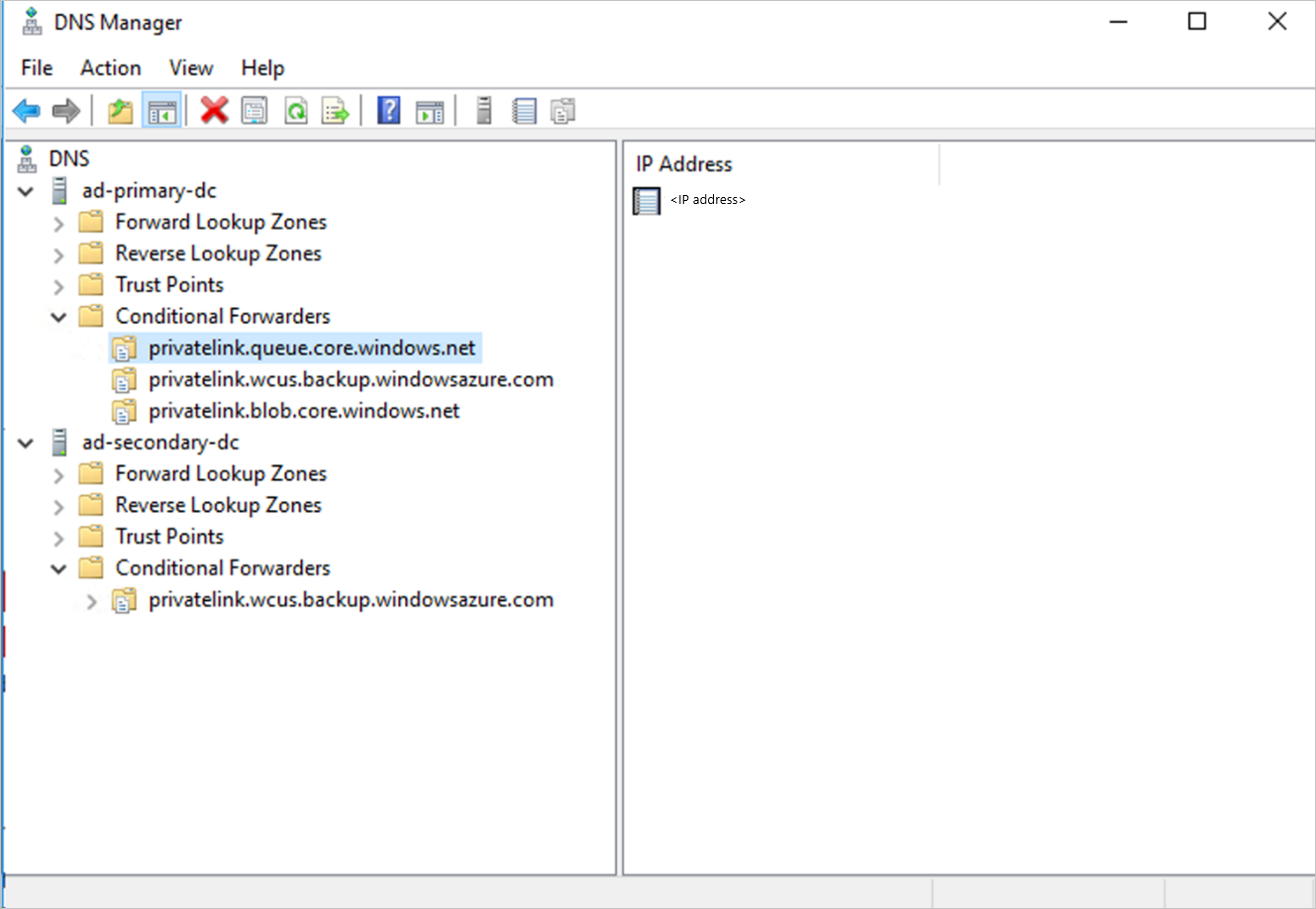
使用 SQL 可用性组 (AG) 时,需要按如下所述在自定义 AG DNS 中预配条件转发:
登录到域控制器。
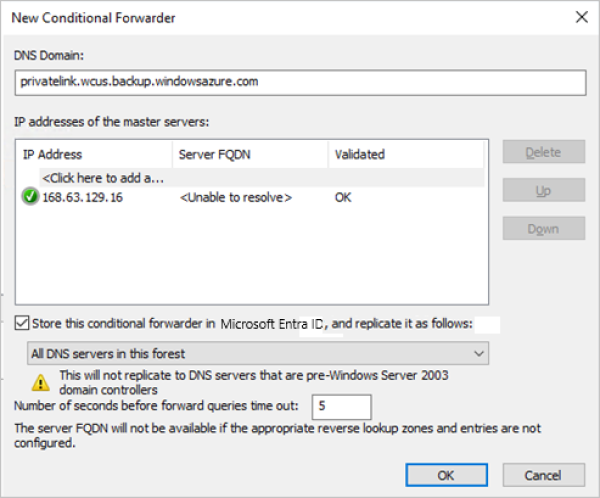
在 DNS 应用程序下,根据需要将所有三个 DNS 区域(备份、Blob 和队列)的条件转发器添加到主机 IP 168.63.129.16 或自定义的 DNS 服务器 IP 地址。 以下屏幕截图显示当您转发到 Azure 主机 IP 时的情况。 如果你使用自己的 DNS 服务器,请替换为你的 DNS 服务器 IP。
通过 MARS 代理和 DPM 服务器进行备份和还原
使用 MARS 代理备份本地资源时,请确保已将本地网络(包含要备份的资源)与包含保管库的专用终结点的 Azure VNet 对等互连,以便可以使用它。 然后可以继续安装 MARS 代理并配置备份,如此处所述。 必须确保所有用于备份的通信仅通过对等网络进行。
但是,如果在将某个 MARS 代理注册到保管库后删除了该保管库的专用终结点,则需要向该保管库重新注册容器。 不需要停止对它们的保护。
注释
- 专用终结点仅支持 DPM 服务器 2022(10.22.123.0) 及更高版本。
- 专用终结点仅支持 MABS V4 (14.0.30.0) 及更高版本。
删除专用终结点
请参阅 此部分 ,了解如何删除专用 EndPoint。
其他主题
使用 Azure 资源管理器客户端创建恢复服务保管库
可以使用 Azure 资源管理器客户端创建恢复服务保管库并启用其托管标识(启用托管标识是必要的,稍后我们将看到原因)。 下面分享了执行此操作的示例:
armclient PUT /subscriptions/<subscriptionid>/resourceGroups/<rgname>/providers/Microsoft.RecoveryServices/Vaults/<vaultname>?api-version=2017-07-01-preview @C:\<filepath>\MSIVault.json
上述 JSON 文件应包含以下内容:
请求 JSON:
{
"location": "chinanorth2",
"name": "<vaultname>",
"etag": "W/\"datetime'2019-05-24T12%3A54%3A42.1757237Z'\"",
"tags": {
"PutKey": "PutValue"
},
"properties": {},
"id": "/subscriptions/<subscriptionid>/resourceGroups/<rgname>/providers/Microsoft.RecoveryServices/Vaults/<vaultname>",
"type": "Microsoft.RecoveryServices/Vaults",
"sku": {
"name": "RS0",
"tier": "Standard"
},
"identity": {
"type": "systemassigned"
}
}
响应 JSON:
{
"location": "chinanorth2",
"name": "<vaultname>",
"etag": "W/\"datetime'2020-02-25T05%3A26%3A58.5181122Z'\"",
"tags": {
"PutKey": "PutValue"
},
"identity": {
"tenantId": "<tenantid>",
"principalId": "<principalid>",
"type": "SystemAssigned"
},
"properties": {
"provisioningState": "Succeeded",
"privateEndpointStateForBackup": "None",
"privateEndpointStateForSiteRecovery": "None"
},
"id": "/subscriptions/<subscriptionid>/resourceGroups/<rgname>/providers/Microsoft.RecoveryServices/Vaults/<vaultname>",
"type": "Microsoft.RecoveryServices/Vaults",
"sku": {
"name": "RS0",
"tier": "Standard"
}
}
注释
通过 Azure 资源管理器客户端在此示例中创建的保管库已使用系统分配的托管标识创建。
对资源组上的权限进行管理
保管库的托管标识需要在包含将要创建的专用终结点的资源组和虚拟网络中具有以下权限:
-
Microsoft.Network/privateEndpoints/*这需要在资源组中的专用终结点上执行 CRUD。 应将其分配到资源组。 -
Microsoft.Network/virtualNetworks/subnets/join/action这是在专用 IP 附加到专用终结点的虚拟网络上所必需的。 -
Microsoft.Network/networkInterfaces/read这是资源组所必需的,才能为专用终结点创建网络接口。 - 专用 DNS 区域参与者角色此角色已存在,可用于提供
Microsoft.Network/privateDnsZones/A/*和Microsoft.Network/privateDnsZones/virtualNetworkLinks/read权限。
可以使用下列方法之一创建具有所需权限的角色:
手动创建角色和权限
创建以下 JSON 文件,并使用节末尾的 PowerShell 命令创建角色:
PrivateEndpointContributorRoleDef.json
{
"Name": "PrivateEndpointContributor",
"Id": null,
"IsCustom": true,
"Description": "Allows management of Private Endpoint",
"Actions": [
"Microsoft.Network/privateEndpoints/*",
],
"NotActions": [],
"AssignableScopes": [
"/subscriptions/00000000-0000-0000-0000-000000000000"
]
}
NetworkInterfaceReaderRoleDef.json
{
"Name": "NetworkInterfaceReader",
"Id": null,
"IsCustom": true,
"Description": "Allows read on networkInterfaces",
"Actions": [
"Microsoft.Network/networkInterfaces/read"
],
"NotActions": [],
"AssignableScopes": [
"/subscriptions/00000000-0000-0000-0000-000000000000"
]
}
PrivateEndpointSubnetContributorRoleDef.json
{
"Name": "PrivateEndpointSubnetContributor",
"Id": null,
"IsCustom": true,
"Description": "Allows adding of Private Endpoint connection to Virtual Networks",
"Actions": [
"Microsoft.Network/virtualNetworks/subnets/join/action"
],
"NotActions": [],
"AssignableScopes": [
"/subscriptions/00000000-0000-0000-0000-000000000000"
]
}
New-AzRoleDefinition -InputFile "PrivateEndpointContributorRoleDef.json"
New-AzRoleDefinition -InputFile "NetworkInterfaceReaderRoleDef.json"
New-AzRoleDefinition -InputFile "PrivateEndpointSubnetContributorRoleDef.json"
使用脚本
下载以下脚本: VaultMsiPrereqScript
转到主文件夹(例如:
cd /home/user运行以下脚本:
./VaultMsiPrereqScript.ps1 -subscription <subscription-Id> -vaultPEResourceGroup <vaultPERG> -vaultPESubnetResourceGroup <subnetRG> -vaultMsiName <msiName>以下是参数:
订阅:**SubscriptionId,其中包含要在其中创建保管库专用终结点的资源组,以及将附加保管库专用终结点的子网
vaultPEResourceGroup:将在其中创建保管库专用终结点的资源组
vaultPESubnetResourceGroup:专用终结点将加入的子网的资源组
vaultMsiName:保管库的 MSI 的名称,该名称与 VaultName 相同
完成身份验证,脚本将采用上面提供的给定订阅的上下文。 如果租户中缺少角色,它将自动创建相应的角色,并将其分配给密钥保管库的 MSI。
使用 Azure PowerShell 创建专用终结点
自动批准的专用终结点
$vault = Get-AzRecoveryServicesVault `
-ResourceGroupName $vaultResourceGroupName `
-Name $vaultName
$privateEndpointConnection = New-AzPrivateLinkServiceConnection `
-Name $privateEndpointConnectionName `
-PrivateLinkServiceId $vault.ID `
-GroupId "AzureBackup"
$vnet = Get-AzVirtualNetwork -Name $vnetName -ResourceGroupName $VMResourceGroupName
$subnet = $vnet | Select -ExpandProperty subnets | Where-Object {$_.Name -eq '<subnetName>'}
$privateEndpoint = New-AzPrivateEndpoint `
-ResourceGroupName $vmResourceGroupName `
-Name $privateEndpointName `
-Location $location `
-Subnet $subnet `
-PrivateLinkServiceConnection $privateEndpointConnection `
-Force
使用 Azure 资源管理器客户端手动批准专用终结点
使用 GetVault 以获得专用终结点的连接 ID。
armclient GET /subscriptions/<subscriptionid>/resourceGroups/<rgname>/providers/Microsoft.RecoveryServices/vaults/<vaultname>?api-version=2017-07-01-preview这将返回专用终结点连接 ID。 可以使用连接 ID 的第一部分检索连接的名称,如下所示:
privateendpointconnectionid = {peName}.{vaultId}.backup.{guid}从响应中获取 专用终结点连接 ID (以及所需的 专用终结点名称),并将其替换为以下 JSON 和 Azure 资源管理器 URI,并尝试将状态更改为“已批准/拒绝/断开连接”,如以下示例所示:
armclient PUT /subscriptions/<subscriptionid>/resourceGroups/<rgname>/providers/Microsoft.RecoveryServices/Vaults/<vaultname>/privateEndpointConnections/<privateendpointconnectionid>?api-version=2020-02-02-preview @C:\<filepath>\BackupAdminApproval.jsonJSON:
{ "id": "/subscriptions/<subscriptionid>/resourceGroups/<rgname>/providers/Microsoft.RecoveryServices/Vaults/<vaultname>/privateEndpointConnections/<privateendpointconnectionid>", "properties": { "privateEndpoint": { "id": "/subscriptions/<subscriptionid>/resourceGroups/<pergname>/providers/Microsoft.Network/privateEndpoints/pename" }, "privateLinkServiceConnectionState": { "status": "Disconnected", //choose state from Approved/Rejected/Disconnected "description": "Disconnected by <userid>" } } }
使用专用终结点为恢复服务保管库设置代理服务器
若要为 Azure VM 或本地计算机配置代理服务器,请执行以下步骤:
添加需要从代理服务器访问的以下域。
服务 域名 港口 Azure 备份 *.backup.windowsazure.cn 443 Azure 存储 *.blob.core.chinacloudapi.cn
*.queue.core.chinacloudapi.cn
*.blob.storage.chinacloudapi.cn443 Microsoft Entra ID
更新了 Microsoft 365 Common 和 Office Online 中第 10 节下提到的域 URL。*.partner.microsoftonline.cn
103.9.8.0/22如果适用。 允许在代理服务器中访问这些域,并将专用 DNS 区域(
*.privatelink.<geo>.backup.windowsazure.cn,*.privatelink.blob.core.chinacloudapi.cn,*.privatelink.queue.core.chinacloudapi.cn)与创建代理服务器的 VNET 链接,或使用包含相应 DNS 条目的自定义 DNS 服务器。
运行代理服务器的 VNET 和创建专用终结点 NIC 的 VNET 应进行对等互连,从而允许代理服务器将请求重定向到专用 IP。注释
在上述文本中,
<geo>分别引用区域代码(例如 bjb2 和 sha2 分别用于中国北部 2 和中国东部 2)。 参考以下区域代码列表:
下图展示了一个使用 Azure 专用 DNS 区域的配置,其中,代理服务器的 VNet 链接到具有所需 DNS 条目的专用 DNS 区域。 代理服务器也可以有自己的自定义 DNS 服务器,上述域可以有条件地转发到 168.63.129.16。 如果使用自定义 DNS 服务器/主机文件进行 DNS 解析,请参阅 有关管理 DNS 条目 和 配置保护的部分。
- 若要自动更新 MARS 代理,需允许访问
download.microsoft.com/download/MARSagent/*。
当 DNS 服务器或 DNS 区域位于另一个订阅中时,创建 DNS 条目
在本部分中,我们将讨论在某个订阅中存在的 DNS 区域使用情况,或者使用与包含恢复服务保管库的专用终结点不同的资源组的情况,例如中心-辐射拓扑结构。 由于用于创建专用终结点的托管标识(和 DNS 条目)仅对创建专用终结点的资源组具有权限,因此还需要所需的 DNS 条目。 使用以下 PowerShell 脚本创建 DNS 条目。
注释
请参阅下面所述的整个过程,以获得所需的结果。 该过程需要重复两次 - 在第一次发现期间(创建通信存储帐户所需的 DNS 条目),然后在第一次备份期间(创建后端存储帐户所需的 DNS 条目)一次。
步骤 1:获取所需的 DNS 条目
使用 PrivateIP.ps1 脚本列出需要创建的所有 DNS 条目。
注释
在下面的语法中,subscription指的是创建保管库专用终结点所需的订阅。
使用脚本的语法
./PrivateIP.ps1 -Subscription "<VaultPrivateEndpointSubscriptionId>" -VaultPrivateEndpointName "<vaultPrivateEndpointName>" -VaultPrivateEndpointRGName <vaultPrivateEndpointRGName> -DNSRecordListFile dnsentries.txt
示例输出
ResourceName DNS PrivateIP
<vaultId>-ab-pod01-fc1 privatelink.bjb2.backup.windowsazure.cn 10.12.0.15
<vaultId>-ab-pod01-fab1 privatelink.bjb2.backup.windowsazure.cn 10.12.0.16
<vaultId>-ab-pod01-prot1 privatelink.bjb2.backup.windowsazure.cn 10.12.0.17
<vaultId>-ab-pod01-rec2 privatelink.bjb2.backup.windowsazure.cn 10.12.0.18
<vaultId>-ab-pod01-ecs1 privatelink.bjb2.backup.windowsazure.cn 10.12.0.19
<vaultId>-ab-pod01-id1 privatelink.bjb2.backup.windowsazure.cn 10.12.0.20
<vaultId>-ab-pod01-tel1 privatelink.bjb2.backup.windowsazure.cn 10.12.0.21
<vaultId>-ab-pod01-wbcm1 privatelink.bjb2.backup.windowsazure.cn 10.12.0.22
abcdeypod01ecs114 privatelink.blob.core.chinacloudapi.cn 10.12.0.23
abcdeypod01ecs114 privatelink.queue.core.chinacloudapi.cn 10.12.0.24
abcdeypod01prot120 privatelink.blob.core.chinacloudapi.cn 10.12.0.28
abcdeypod01prot121 privatelink.blob.core.chinacloudapi.cn 10.12.0.32
abcdepod01prot110 privatelink.blob.core.chinacloudapi.cn 10.12.0.36
abcdeypod01prot121 privatelink.blob.core.chinacloudapi.cn 10.12.0.30
abcdeypod01prot122 privatelink.blob.core.chinacloudapi.cn 10.12.0.34
abcdepod01prot120 privatelink.blob.core.chinacloudapi.cn 10.12.0.26
步骤 2:创建 DNS 条目
创建与上述条目对应的 DNS 条目。 根据使用的 DNS 类型,有两种创建 DNS 条目的替代方法。
案例 1:如果使用自定义 DNS 服务器,则需要从上述脚本为每个记录手动创建条目,并验证 FQDN (ResourceName.DNS) 是否解析为 VNET 中的专用 IP。
案例 2:如果使用 Azure 专用 DNS 区域,可以使用 CreateDNSEntries.ps1 脚本在专用 DNS 区域中自动创建 DNS 条目。 在以下语法中,subscription 是存在专用 DNS 区域的位置。
使用脚本的语法
/CreateDNSEntries.ps1 -Subscription <PrivateDNSZoneSubId> -DNSResourceGroup <PrivateDNSZoneRG> -DNSRecordListFile dnsentries.txt
整个过程摘要
若要通过此解决方法正确设置恢复服务保管库的专用终结点,需要:
- 为保管库创建专用终结点(如本文前面所述)。
- 启动发现过程。 SQL/HANA 的发现会失败, UserErrorVMInternetConnectivityIssue 因为通信存储帐户缺少 DNS 条目。
- 运行脚本以获取 DNS 条目,并为本部分前面提到的通信存储帐户创建相应的 DNS 条目。
- 重新触发发现 这一次,发现应该可以成功。
- 触发备份。 SQL/HANA 和 MARS 的备份可能会失败,因为后端存储帐户缺少 DNS 条目,如本节前面所述。
- 运行脚本,为后端存储帐户创建 DNS 条目。
- 重新触发备份。 这一次,备份应成功。
常见问题
是否可以为现有恢复服务保管库创建专用终结点?
否,只能为新的恢复服务库创建专用终结点。 因此,保险库从未有过受保护的物品。 在创建专用终结点之前,实际上无法尝试将任何物品保护到保管库中。
我试图将某个项目保护到我的保管库中,但操作失败了,保管库中仍然没有存放任何被保护的项目。 是否可以为此保管库创建专用终结点?
否,保管库过去不可能曾试图保护任何物品。
我有一个保管库,该保管库使用专用终结点进行备份和还原。 以后是否可以添加或删除此保管库的专用终结点,即使我的备份项受到保护?
是的。 如果已为保管库创建了专用终结点和受保护的备份项,则可以根据需要添加或删除专用终结点。
Azure 备份的专用终结点能否也用于 Azure Site Recovery?
否,备份的专用终结点只能用于 Azure 备份。 如果服务支持 Azure Site Recovery,则需要为 Azure Site Recovery 创建新的专用终结点。
我遗漏了本文中的一个步骤,但依然继续保护我的数据源。 是否仍可使用专用终结点?
如果不遵循本文中的步骤而继续保护项目,可能会导致保管库无法使用专用终结点。 因此,建议在继续保护项目之前参考此清单。
是否可以使用自己的 DNS 服务器,而不是使用 Azure 专用 DNS 区域或集成的专用 DNS 区域?
可以,可以使用自己的 DNS 服务器。 但是,请确保按照本部分中的建议添加所有必需的 DNS 记录。
执行本文中的过程后,是否需要在服务器上执行任何其他步骤?
按照本文中详述的过程做完后,无需执行其他工作就可以使用专用终结点进行备份和还原。
后续步骤
- 了解 Azure 备份中的所有安全功能。