通过在容器实例中设置环境变量,可为容器运行的应用程序或脚本提供动态配置。 此功能类似于在 --env 命令行中指定参数 docker run。
若要设置容器中的环境变量,请在创建容器实例时进行指定。 本文演示的示例介绍了如何在使用 Azure CLI、Azure PowerShell 和 Azure 门户启动容器时设置环境变量。
例如,如果运行 Microsoft aci-wordcount 容器映像,可以通过指定以下环境变量来修改其行为:
NumWords:发送到 STDOUT 的单词数。
MinLength:单词中最少包含几个字符才将它统计为一个单词。 如果指定较大的数字,将会忽略“of”和“the”等常见单词。
Important
如果需要以环境变量的形式传递机密,Azure 容器实例支持 Windows 和 Linux 容器的安全值。
Note
建议使用 Azure Az PowerShell 模块与 Azure 交互。 若要开始,请参阅安装 Azure PowerShell。 若要了解如何迁移到 Az PowerShell 模块,请参阅 将 Azure PowerShell 从 AzureRM 迁移到 Az。
Azure CLI 示例
若要查看 aci-wordcount 容器的默认输出,请首先使用此 az container create 命令来运行它(不指定环境变量):
az container create \
--resource-group myResourceGroup \
--name mycontainer1 \
--image mcr.microsoft.com/azuredocs/aci-wordcount:latest \
--restart-policy OnFailure
若要修改输出,请在添加 --environment-variables 变量的情况下启动又一个容器,为 NumWords 和 MinLength 变量指定值。 (此示例假定在 Bash Shell 中运行 CLI。如果使用 Windows 命令提示符,请使用双引号指定变量,例如 --environment-variables "NumWords"="5" "MinLength"="8"。)
az container create \
--resource-group myResourceGroup \
--name mycontainer2 \
--image mcr.microsoft.com/azuredocs/aci-wordcount:latest \
--restart-policy OnFailure \
--environment-variables 'NumWords'='5' 'MinLength'='8'
两个容器的状态显示为“已终止”后(使用 az container show 来查看状态),请使用 az container logs 来显示其日志,以便查看输出。
az container logs --resource-group myResourceGroup --name mycontainer1
az container logs --resource-group myResourceGroup --name mycontainer2
容器的输出显示了通过设置环境变量来修改第二个容器的脚本行为的方式。
mycontainer1
[('the', 990),
('and', 702),
('of', 628),
('to', 610),
('I', 544),
('you', 495),
('a', 453),
('my', 441),
('in', 399),
('HAMLET', 386)]
mycontainer2
[('CLAUDIUS', 120),
('POLONIUS', 113),
('GERTRUDE', 82),
('ROSENCRANTZ', 69),
('GUILDENSTERN', 54)]
Azure PowerShell 示例
在 PowerShell 中设置环境变量类似于在 CLI 中进行的相应操作,但需使用 -EnvironmentVariable 命令行参数。
首先,使用此 New-AzContainerGroup 命令在默认配置中启动 aci-wordcount 容器:
New-AzContainerGroup `
-ResourceGroupName myResourceGroup `
-Name mycontainer1 `
-Image mcr.microsoft.com/azuredocs/aci-wordcount:latest
现在请运行以下 New-AzContainerGroup 命令。 此命令在填充数组变量 后指定 NumWords 和 envVars 环境变量:
$envVars = @(
New-AzContainerInstanceEnvironmentVariableObject -Name "NumWords" -Value "5"
New-AzContainerInstanceEnvironmentVariableObject -Name "MinLength" -Value "8"
)
$containerGroup = New-AzContainerGroup -ResourceGroupName "myResourceGroup" `
-Name "mycontainer2" `
-Image "mcr.microsoft.com/azuredocs/aci-wordcount:latest" `
-RestartPolicy "OnFailure" `
-Container @(
New-AzContainerInstanceContainer -Name "mycontainer2" `
-EnvironmentVariable $envVars
)
两个容器的状态均为“已终止”后(使用 Get-AzContainerInstanceLog 来查看状态),请使用 Get-AzContainerInstanceLog 命令来拉取其日志。
Get-AzContainerInstanceLog -ResourceGroupName myResourceGroup -ContainerGroupName mycontainer1
Get-AzContainerInstanceLog -ResourceGroupName myResourceGroup -ContainerGroupName mycontainer2
每个容器的输出显示你如何通过设置环境变量修改了容器运行的脚本。
PS Azure:\> Get-AzContainerInstanceLog -ResourceGroupName myResourceGroup -ContainerGroupName mycontainer1
[('the', 990),
('and', 702),
('of', 628),
('to', 610),
('I', 544),
('you', 495),
('a', 453),
('my', 441),
('in', 399),
('HAMLET', 386)]
Azure:\
PS Azure:\> Get-AzContainerInstanceLog -ResourceGroupName myResourceGroup -ContainerGroupName mycontainer2
[('CLAUDIUS', 120),
('POLONIUS', 113),
('GERTRUDE', 82),
('ROSENCRANTZ', 69),
('GUILDENSTERN', 54)]
Azure:\
Azure 门户示例
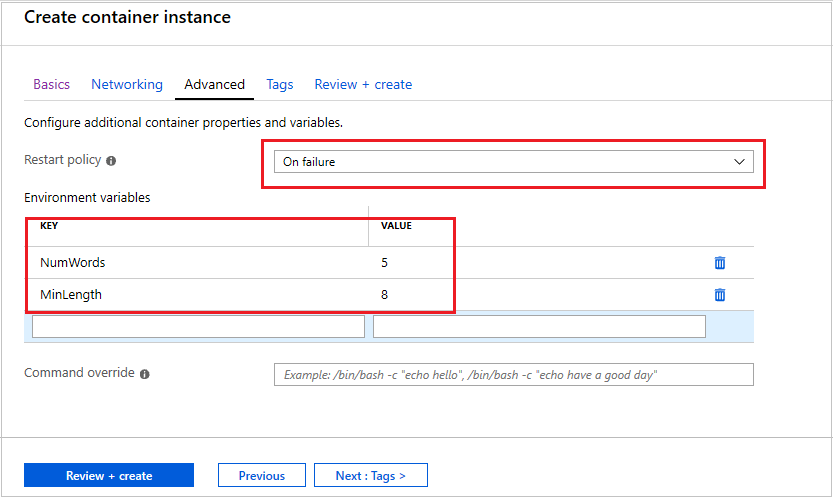
在 Azure 门户中启动容器时,若要设置环境变量,请在创建容器时所在的“高级”页中指定它们。
在“高级”页上将“重启策略”设置为“在故障时”
在“环境变量”下,为第一个变量输入值为 的
NumWords,并为第二个变量输入值为5的MinLength。8选择“查看 + 创建”进行验证,然后部署容器。
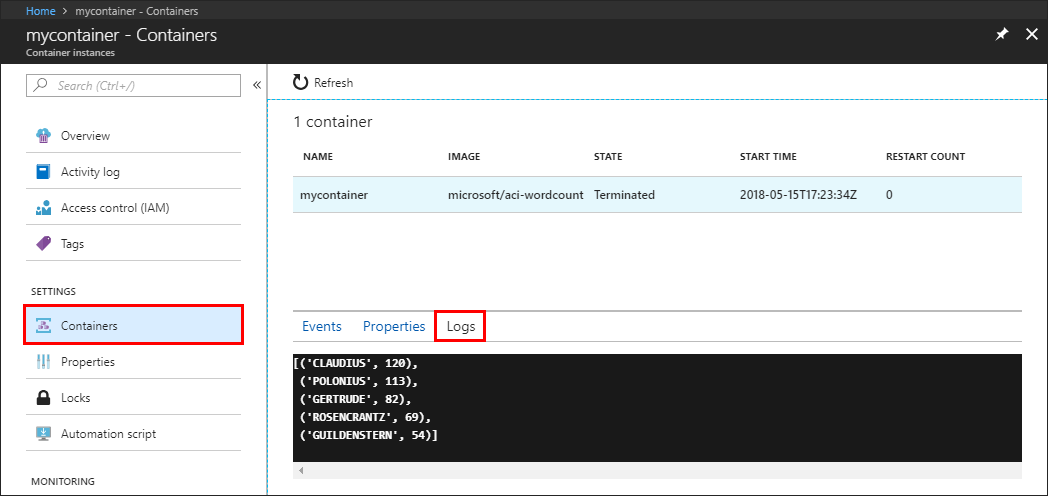
若要查看容器的日志,请在“设置”下选择“容器”,然后选择“日志”。 可以查看环境变量对脚本行为进行的具体更改,这与在此前的 CLI 和 PowerShell 部分显示的输出类似。 仅显示了五个单词,每个的最小长度为八个字符。
Secure values
具有安全值的对象旨在为应用程序保留密码或密钥等敏感信息。 对环境变量使用安全值比将它添加到容器映像中更为安全灵活。 也可以使用机密卷,如在 Azure 容器实例中装载机密卷所述。
具有安全值的环境变量在容器的属性中不可见 - 它们的值只能从容器中访问。 例如,在 Azure 门户或 Azure CLI 中查看的容器属性仅显示安全变量的名称,而不显示其值。
安全环境变量的设置方法为,指定 secureValue 属性(而不是常规 value)作为变量类型。 下面 YAML 中定义的两个变量展示了两种变量类型。
YAML deployment
创建包含下面的代码片段的 secure-env.yaml 文件。
apiVersion: 2019-12-01
location: chinaeast2
name: securetest
properties:
containers:
- name: mycontainer
properties:
environmentVariables:
- name: 'NOTSECRET'
value: 'my-exposed-value'
- name: 'SECRET'
secureValue: 'my-secret-value'
image: mcr.microsoft.com/oss/nginx/nginx:1.15.5-alpine
ports: []
resources:
requests:
cpu: 1.0
memoryInGB: 1.5
osType: Linux
restartPolicy: Always
tags: null
type: Microsoft.ContainerInstance/containerGroups
运行以下命令以使用 YAML 部署容器组(根据需要调整资源组名称):
az container create --resource-group myResourceGroup --file secure-env.yaml
验证环境变量
运行 az container show 命令查询容器的环境变量:
az container show --resource-group myResourceGroup --name securetest --query 'containers[].environmentVariables'
JSON 响应显示不安全的环境变量的键和值,但仅显示安全环境变量的名称:
[
[
{
"name": "NOTSECRET",
"secureValue": null,
"value": "my-exposed-value"
},
{
"name": "SECRET",
"secureValue": null,
"value": null
}
]
]
使用 az container exec 命令(允许在正在运行的容器中执行命令),可以验证是否已设置安全环境变量。 运行以下命令以在容器中启动交互式 bash 会话:
az container exec --resource-group myResourceGroup --name securetest --exec-command "/bin/sh"
在容器中打开交互式 shell 后,可以访问 SECRET 变量的值:
root@caas-ef3ee231482549629ac8a40c0d3807fd-3881559887-5374l:/# echo $SECRET
my-secret-value
Next steps
基于任务的方案(例如对使用多个容器的数据库进行批处理)可以在运行时充分利用自定义环境变量。 若要详细了解如何运行基于任务的容器,请参阅使用重启策略运行容器化任务。