为了保护帐户中存储的数据,Azure Cosmos DB 使用基于机密的授权模型和基于哈希的强消息身份验证代码(HMAC)。 此外,Azure Cosmos DB 使用基于 IP 的访问控制来保护入站防火墙安全。 此模型类似于传统数据库系统的防火墙规则,并将另一层安全性添加到帐户。 使用防火墙,将 Azure Cosmos DB 帐户配置为仅允许从批准的一组计算机或云服务进行访问。 从这些批准的计算机和服务访问 Azure Cosmos DB 数据库中存储的数据仍需要调用方提供有效的授权令牌。
IP 访问控制
默认情况下,如果请求包含有效的授权令牌,可以从 Internet 访问 Azure Cosmos DB 帐户。 若要配置基于 IP 策略的访问控制,用户必须提供 CIDR(无类域间路由)格式的、要作为客户端 IP 允许列表包含的 IP 地址或 IP 地址范围集,这样才能访问给定的 Azure Cosmos DB 帐户。 应用此配置后,来自此允许列表外部的计算机的任何请求都会收到 403 (禁止访问)响应。 使用 IP 防火墙时,某些方案可能需要从 Azure 门户启用访问权限。 有关详细信息,请参阅 来自 Azure 门户的允许请求。 在使用用于 NoSQL、Gremlin 或表帐户的 API 的数据资源管理器时,您还需要更新防火墙配置,将当前的 IP 地址添加到防火墙规则中。 防火墙更改可能需要最多 15 分钟才能传播,在此期间,防火墙的行为可能不一致。
将基于 IP 的防火墙与子网和虚拟网络访问控制相结合。 将这两种策略相结合,可以限制访问具有某个公共 IP 的任何源,和/或从虚拟网络中的特定子网访问任何源。 若要详细了解如何使用基于子网和虚拟网络的访问控制,请参阅从虚拟网络访问 Azure Cosmos DB 资源。
总之,访问 Azure Cosmos DB 帐户始终需要授权令牌。 如果未设置 IP 防火墙和虚拟网络访问控制列表 (ACL),可以使用授权令牌访问 Azure Cosmos DB 帐户。 为 Azure Cosmos DB 帐户设置 IP 防火墙规则或虚拟网络访问列表后,只有来自允许源的请求才能正常工作。 这些请求还必须包含有效的授权令牌才能获取响应。
可以使用 IP 防火墙保护存储在 Azure Cosmos DB 帐户中的数据。 Azure Cosmos DB 支持使用基于 IP 的访问控制来提供入站防火墙支持。 使用以下方法之一在 Azure Cosmos DB 帐户上设置 IP 防火墙:
- 通过 Azure 门户
- 通过使用 Azure 资源管理器模板来以声明方式进行配置
- 通过更新 ipRangeFilter 属性并借助 Azure CLI 或 Azure PowerShell 来以编程方式进行配置
使用 Azure 门户配置 IP 防火墙
若要在 Azure 门户中设置 IP 访问控制策略,请转到 Azure Cosmos DB 帐户页,然后在导航菜单中选择“网络”。 将 “允许从值访问 ”设置为 “所选网络”,然后选择“ 保存”。 如果尚未添加任何 IP 地址,则还需要 选中该框,确认所有 VNet 和 IP 均被阻止。 如果更改公共网络访问设置,例如将其关闭或允许所有网络连接,则删除之前设置的任何防火墙 IP 地址。
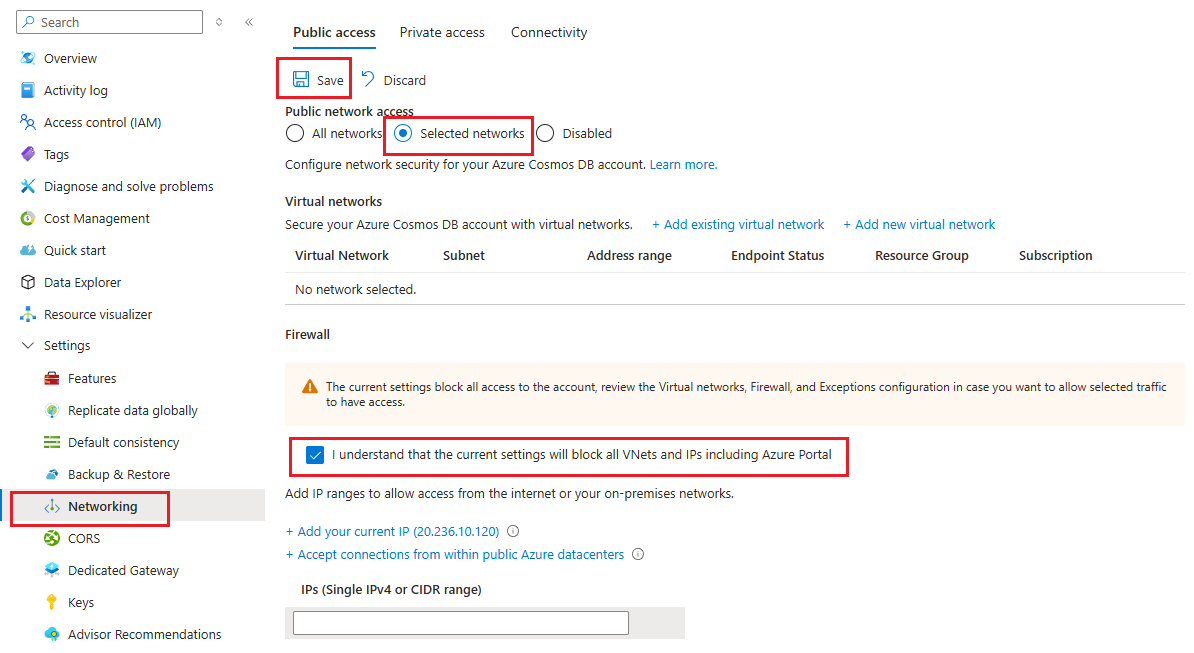
启用 IP 访问控制时,Azure 门户允许你指定 IP 地址、IP 地址范围和交换机。 使用开关可以访问其他 Azure 服务和 Azure 门户。 以下部分提供了有关这些开关的详细信息。
注意
为 Azure Cosmos DB 帐户启用 IP 访问控制时,只有来自允许的 IP 地址的请求才能访问你的帐户。 如果 IP 地址不在允许列表中,则阻止其请求。 除非允许门户访问,否则无法在 Azure 门户中浏览 Cosmos DB 资源。
允许来自 Azure 门户的请求
以编程方式启用 IP 访问控制策略时,可能需要将 Azure 门户服务的 IP 地址添加到 ipRangeFilter 属性,以继续使用某些门户功能。
需要启用此选项的门户方案包括:
- 具体而言,适用于 MongoDB 的 API 或用于 Apache Cassandra 的 API,使用数据资源管理器访问帐户或 https://cosmos.azure.cn
- 对于所有 API,在 Azure 门户中使用以下 Azure Cosmos DB 部分:
- 浏览集合
- Power BI
- Azure Synapse
可以选择“添加 Azure 门户中间件 IP”选项,以允许访问 Azure 门户的请求,如以下屏幕截图所示:
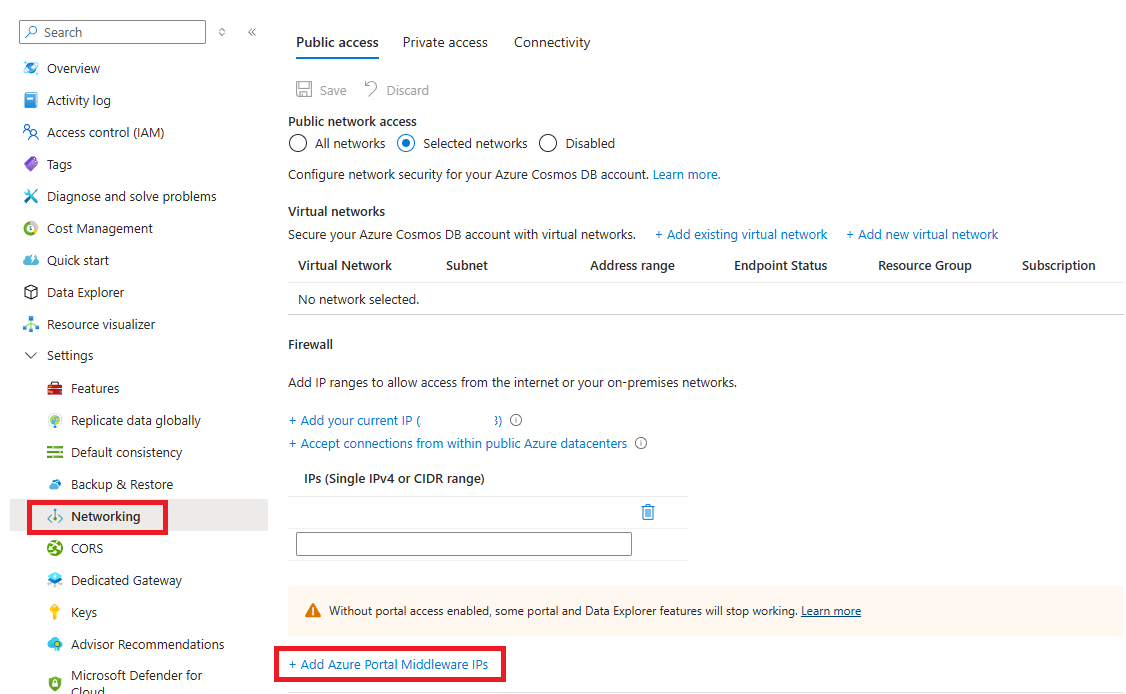
Azure 门户中间件 IP 地址将添加到单独的列表中,如以下屏幕截图所示。 选择 “保存” ,将这些地址添加到数据库帐户。 有关中间件 IP 地址的更多详细信息,可在本文中进一步找到。
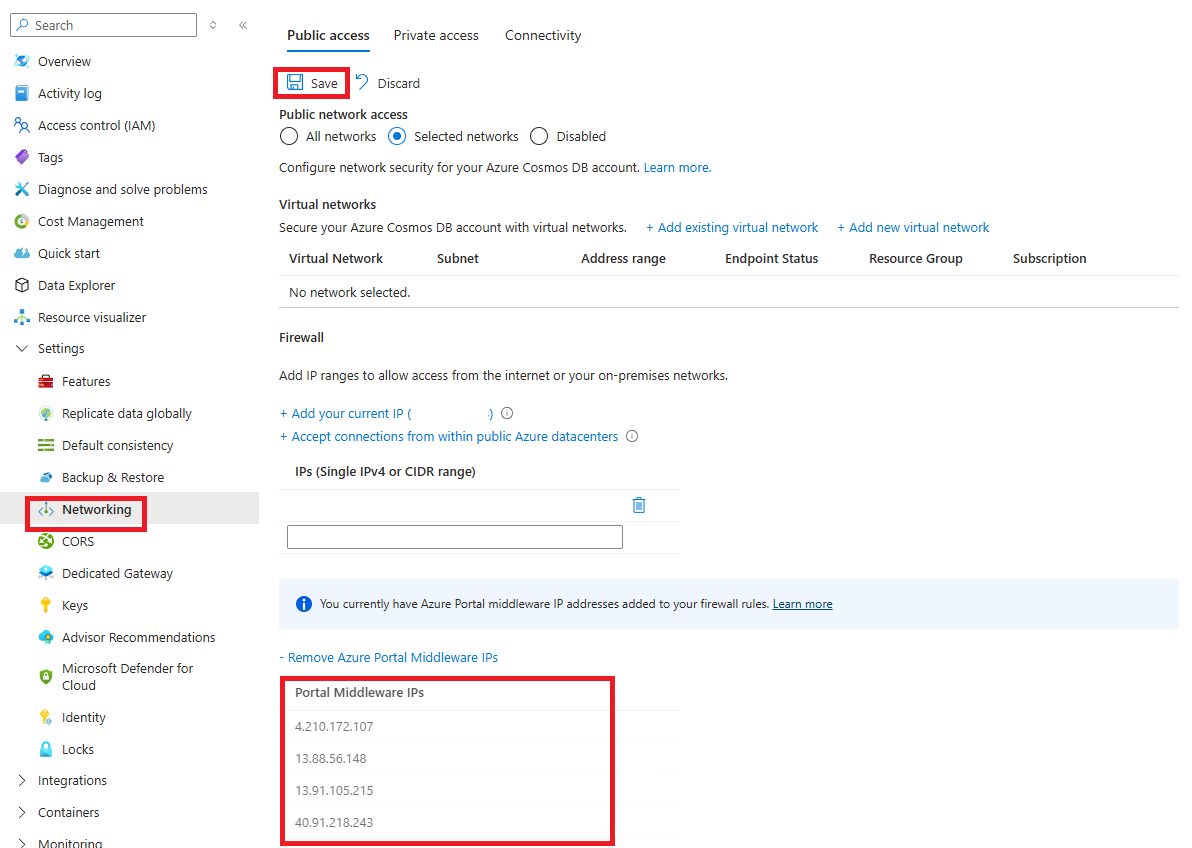
可以通过选择 “删除 Azure 门户中间件 IP” 选项,然后选择“ 保存”来删除 Azure 门户中间件 IP 地址。
Azure 门户中间件 IP 地址
此处列出了 Azure 门户中间件 IP 地址。 某些 IP 地址仅适用于特定的数据库帐户 API。 在门户中添加中间件 IP 地址时,如前所述,只会添加帐户所需的 IP 地址。
例如:
- 对于 NoSQL 帐户的 API,将添加 “所有 ”类别中的 IP 地址。
- 对于用于 MongoDB 帐户的 API,仅添加 “所有 ”和 “MongoDB ”类别中的 IP 地址。
由世纪互联运营的 Azure
| 数据库帐户 API | IP 地址 |
|---|---|
| 全部 |
163.228.137.6、143.64.170.142 |
| 仅 MongoDB |
52.131.240.99、143.64.61.130 |
| 仅 Apache Cassandra API |
40.73.99.146、143.64.62.47 |
旧中间件 IP 地址
Cosmos DB 门户服务最近转换到需要新中间件 IP 地址的新基础设施。 随着该转换的完成,现在可以安全地删除旧基础设施使用的旧 IP 地址。 如果帐户具有防火墙规则中存在的旧中间件 IP 地址,则会显示 “删除 Azure 门户旧中间件 IP ”选项。 选择此选项,然后选择“保存”以删除旧 IP 地址。
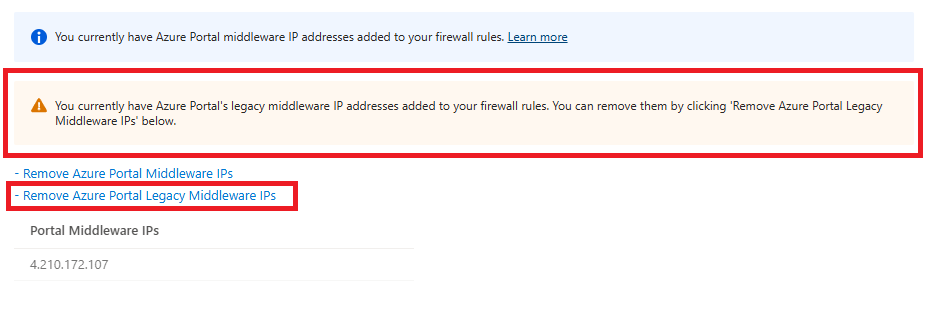
旧 IP 地址依赖于云环境:
| Azure 环境 | IP 地址 |
|---|---|
| Azure 公有云 |
104.42.195.92、40.76.54.131、52.176.6.30、52.169.50.45、52.187.184.26 |
| 由世纪互联运营的 Azure |
139.217.8.252、52.176.6.30、52.169.50.45、52.187.184.26 |
| Azure 美国政府 |
52.244.48.71、52.176.6.30、52.169.50.45、52.187.184.26 |
注意
如果遇到从数据资源管理器连接到 Azure Cosmos DB 帐户的挑战,请查看 数据资源管理器故障排除指南。
允许来自多区域的 Azure 数据中心或 Azure 中的其他源的请求
某些 Azure 服务(如 Azure 流分析和 Azure Functions)不使用固定 IP 地址。 你仍然可以使用 IP 防火墙来控制这些服务的访问。 若要允许从其他 Azure 资源进行访问,请选择 “接受来自 Azure 数据中心内的连接 ”选项。 此选项允许在 Azure 中运行的服务连接到 Cosmos DB 帐户。
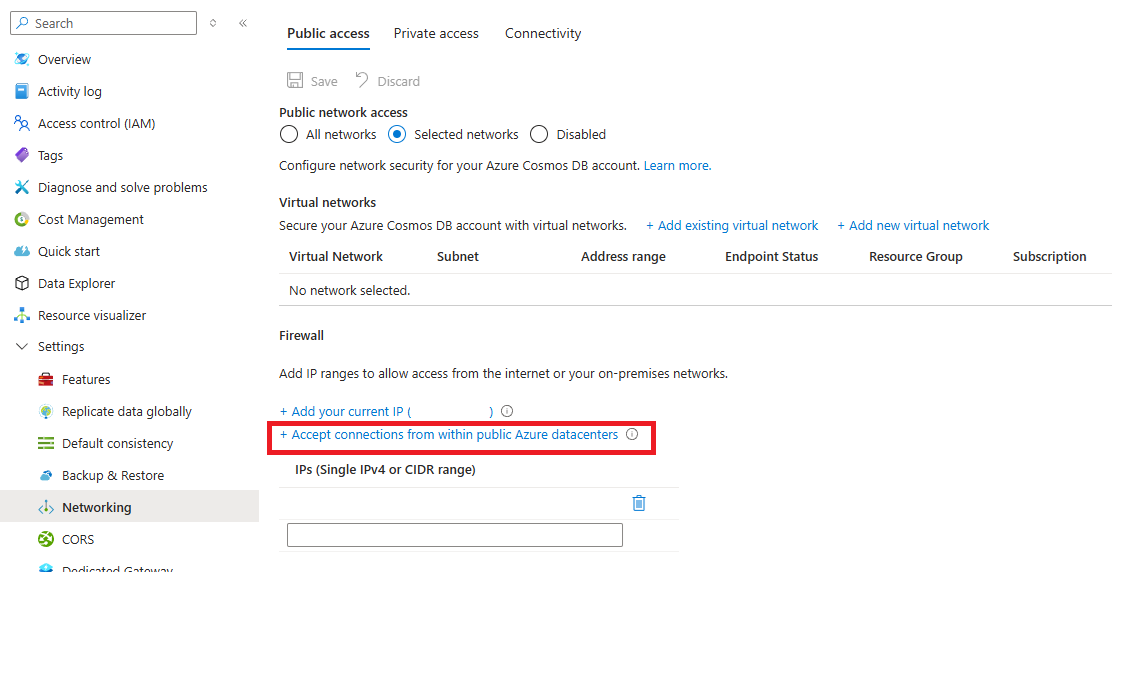
如果启用此选项,则会将 IP 地址 0.0.0.0 添加到允许的 IP 地址列表中。
0.0.0.0 IP 地址仅限从 Azure 数据中心 IP 范围向 Azure Cosmos DB 帐户发送请求。 此设置不允许任何其他 IP 范围访问 Azure Cosmos DB 帐户。
注意
将 publicNetworkAccess 设置为 Disabled 优先于 从 Azure 数据中心选项中的“接受”连接 。 请参阅blocking-public-network-access-during-account-creation
注意
该选项将防火墙配置为允许来自 Azure 的所有请求,包括来自 Azure 中部署的其他客户的订阅的请求。 此选项允许的 IP 地址较为广泛,因为限制了防火墙策略的有效性。 仅当请求并非来自虚拟网络中的静态 IP 或子网时,才使用此选项。 选择此选项将自动允许从 Azure 门户进行访问,因为 Azure 门户在 Azure 中部署。
来自当前 IP 的请求
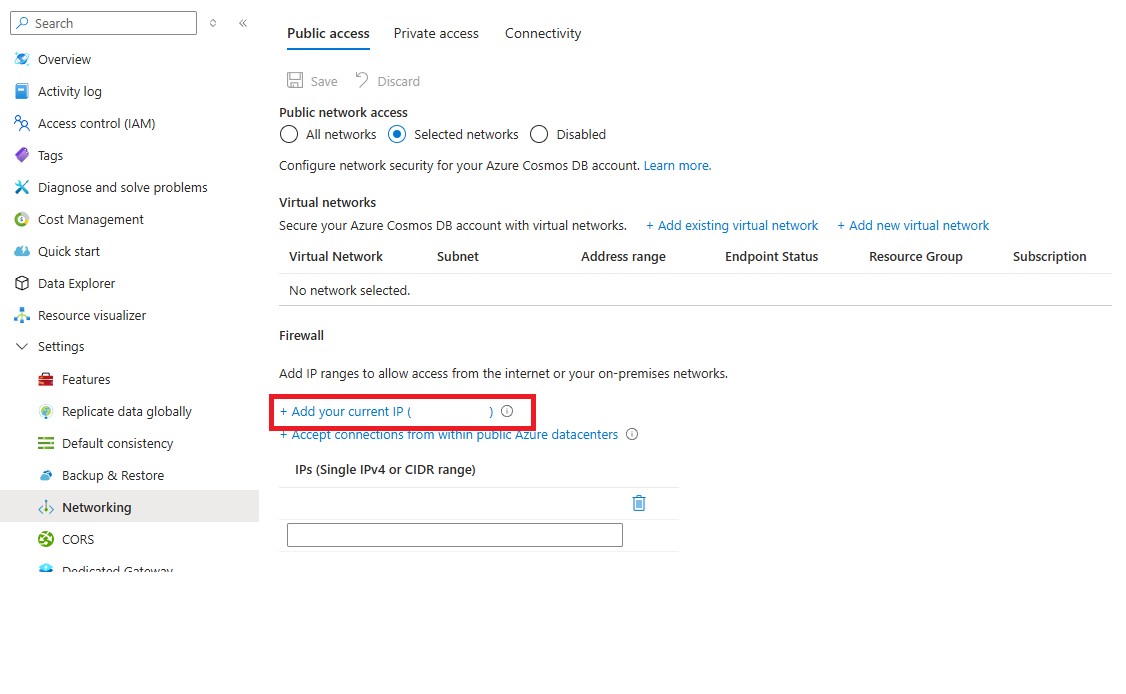
为了简化开发,Azure 门户可帮助识别客户端计算机的 IP 并将其添加到允许的列表。 然后,计算机上运行的应用可以访问你的 Azure Cosmos DB 帐户。
门户将自动检测客户端 IP 地址。 它可能是计算机的客户端 IP 地址,也可能是网络网关的 IP 地址。 请务必在将工作负荷置于生产环境之前删除此 IP 地址。
若要将当前 IP 添加到 IP 列表,请选择“添加当前 IP”。 再选择“保存” 。
来自云服务的请求
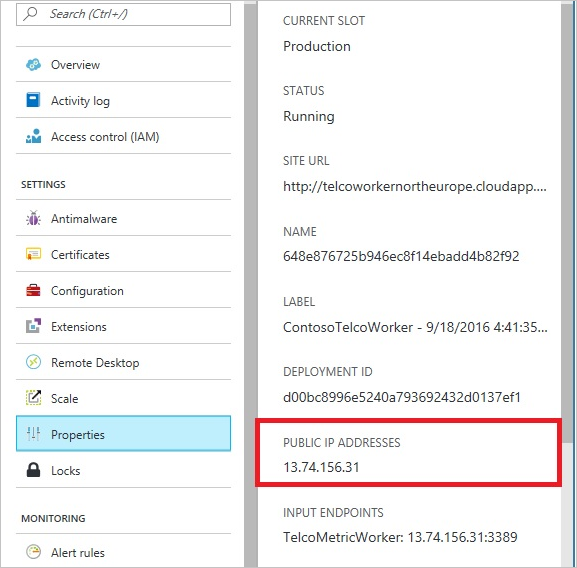
在 Azure 中,云服务是一种使用 Azure Cosmos DB 托管中间层服务逻辑的常用方法。 若要让云服务连接到 Azure Cosmos DB 帐户,请将云服务的公共 IP 地址添加到允许的 IP 列表。 可以通过在 Azure 门户中更新 IP 访问控制策略来执行此作。 此步骤可确保云服务的所有角色实例都有权访问 Azure Cosmos DB 帐户。
如以下屏幕截图所示,可以在 Azure 门户中检索云服务的 IP 地址:
 通过添加角色实例横向扩展云服务时,新实例会自动有权访问 Azure Cosmos DB 帐户,因为它们是同一云服务的一部分。
通过添加角色实例横向扩展云服务时,新实例会自动有权访问 Azure Cosmos DB 帐户,因为它们是同一云服务的一部分。
来自虚拟机的请求
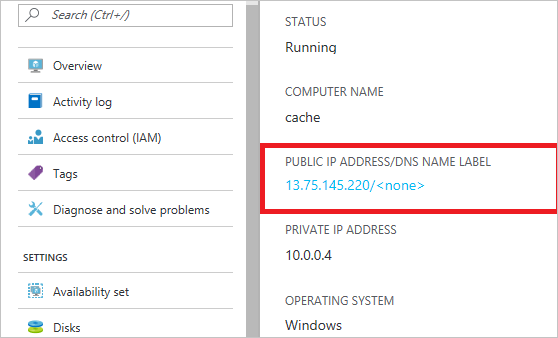
还可以使用虚拟机或虚拟机规模集通过 Azure Cosmos DB 托管中间层服务。 若要让虚拟机连接到 Azure Cosmos DB 帐户,请将其公共 IP 地址添加到允许的列表。 可以通过更新 IP 访问控制策略来执行此步骤。 此配置也适用于虚拟机规模集。 添加公共 IP 地址后,虚拟机可以访问 Cosmos DB 帐户。
如以下屏幕截图所示,可以在 Azure 门户中检索虚拟机的 IP 地址:
将虚拟机实例添加到组时,这些实例会自动获得 Azure Cosmos DB 帐户的访问权限。
来自 Internet 的请求
若要从 Internet 上的计算机连接到 Azure Cosmos DB 帐户,请将该计算机的 IP 地址或 IP 范围添加到允许的列表。 只有添加到此列表的计算机才能访问 Cosmos DB 帐户。
将出站规则添加到防火墙
若要获取要添加到防火墙设置的出站 IP 范围的当前列表,请参阅 “下载 Azure IP 范围和服务标记”。
若要自动生成此列表,请参阅使用服务标记发现 API。
使用资源管理器模板配置 IP 防火墙
若要为 Azure Cosmos DB 帐户设置访问控制,请确保资源管理器模板使用允许的 IP 范围的数组指定 ipRules 属性。 如果为已部署的 Azure Cosmos DB 帐户设置 IP 防火墙,请确保 locations 该阵列与当前部署匹配。 不能同时修改 locations 数组和其他属性。 有关 Azure Cosmos DB 的 Azure 资源管理器模板的详细信息和示例,请参阅 适用于 Azure Cosmos DB 的 Azure 资源管理器模板。
重要
IPRules 属性随 API 版本2020-04-01一起引入。 早期版本改用 ipRangeFilter 属性,该属性是逗号分隔 IP 地址的列表。
示例演示了如何在 API 2020-04-01 或更高版本中公开 ipRules 属性:
{
"type": "Microsoft.DocumentDB/databaseAccounts",
"name": "[variables('accountName')]",
"apiVersion": "2020-04-01",
"location": "[parameters('location')]",
"kind": "GlobalDocumentDB",
"properties": {
"consistencyPolicy": "[variables('consistencyPolicy')[parameters('defaultConsistencyLevel')]]",
"locations": "[variables('locations')]",
"databaseAccountOfferType": "Standard",
"enableAutomaticFailover": "[parameters('automaticFailover')]",
"ipRules": [
{
"ipAddressOrRange": "13.91.105.215"
},
{
"ipAddressOrRange": "4.210.172.107"
},
{
"ipAddressOrRange": "13.88.56.148"
},
{
"ipAddressOrRange": "40.91.218.243"
}
]
}
}
下面是低于 2020-04-01以下任何 API 版本的相同示例:
{
"type": "Microsoft.DocumentDB/databaseAccounts",
"name": "[variables('accountName')]",
"apiVersion": "2019-08-01",
"location": "[parameters('location')]",
"kind": "GlobalDocumentDB",
"properties": {
"consistencyPolicy": "[variables('consistencyPolicy')[parameters('defaultConsistencyLevel')]]",
"locations": "[variables('locations')]",
"databaseAccountOfferType": "Standard",
"enableAutomaticFailover": "[parameters('automaticFailover')]",
"ipRangeFilter":"139.217.8.252"
}
}
使用 Azure CLI 配置 IP 访问控制策略
以下命令演示如何创建具有 IP 访问控制的 Azure Cosmos DB 帐户:
# Create an Azure Cosmos DB account with default values and IP firewall enabled
resourceGroupName='MyResourceGroup'
accountName='mycosmosaccount'
ipRangeFilter='192.168.221.17,183.240.196.255,139.217.8.252'
# Ensure there are no spaces in the comma-delimited list of IP addresses or CIDR ranges.
az cosmosdb create \
-n $accountName \
-g $resourceGroupName \
--locations regionName='China North 2' failoverPriority=0 isZoneRedundant=False \
--locations regionName='China East 2' failoverPriority=1 isZoneRedundant=False \
--ip-range-filter $ipRangeFilter
使用 PowerShell 配置 IP 访问控制策略
以下脚本演示如何使用 IP 访问控制创建 Azure Cosmos DB 帐户:
# Create an Azure Cosmos DB account with default values and IP Firewall enabled
$resourceGroupName = "myResourceGroup"
$accountName = "mycosmosaccount"
$ipRules = @("192.168.221.17","183.240.196.255","139.217.8.252")
$locations = @(
@{ "locationName"="China North 2"; "failoverPriority"=0; "isZoneRedundant"=False },
@{ "locationName"="China East 2"; "failoverPriority"=1, "isZoneRedundant"=False }
)
# Make sure there are no spaces in the comma-delimited list of IP addresses or CIDR ranges.
$CosmosDBProperties = @{
"databaseAccountOfferType"="Standard";
"locations"=$locations;
"ipRules"=$ipRules
}
New-AzResource -ResourceType "Microsoft.DocumentDb/databaseAccounts" `
-ApiVersion "2020-04-01" -ResourceGroupName $resourceGroupName `
-Name $accountName -PropertyObject $CosmosDBProperties
排查 IP 访问控制策略的问题
可使用以下选项排查 IP 访问控制策略的问题:
Azure 门户
为 Azure Cosmos DB 帐户启用 IP 访问控制策略会阻止来自允许的 IP 地址范围列表之外的计算机的所有请求。 若要启用门户数据平面作(如浏览容器和查询文档),请使用门户中的 “防火墙 ”窗格显式允许 Azure 门户访问。
软件开发工具包
从不在允许列表中的计算机使用软件开发工具包(SDK)访问 Azure Cosmos DB 资源时,将返回一个通用 的 403 禁止 响应,且没有额外的详细信息。 检查帐户的允许 IP 列表,并确保将正确的策略配置应用到 Azure Cosmos DB 帐户。
受阻止请求中的源 IP
通过在 Azure Cosmos DB 帐户上启用诊断日志记录来查看每个请求和响应。 会记录带有 403 返回代码的防火墙相关消息。 通过筛选这些消息,可以查看已阻止请求的源 IP。 请参阅 Azure Cosmos DB 诊断日志记录。
来自已启用 Azure Cosmos DB 服务终结点的子网的请求
从启用了 Azure Cosmos DB 服务终结点的虚拟网络中的子网发出的请求会将虚拟网络和子网标识发送到 Azure Cosmos DB 帐户。 这些请求不包含源的公共 IP,因此 IP 筛选器将拒绝它们。 若要允许从虚拟网络中的特定子网进行访问,请添加如何为 Azure Cosmos DB 帐户配置基于虚拟网络和子网的访问中所述的访问控制列表。 应用防火墙规则可能需要多达 15 分钟,在此期间防火墙可能会呈现出不一致的行为。
允许的地址列表中的专用 IP 地址
创建或更新包含专用 IP 地址的允许地址列表的 Azure Cosmos DB 帐户失败。 请确保未在列表中指定专用 IP 地址。