在 Azure Cosmos DB 中限制用户对数据操作的访问
适用对象: NoSQL
MongoDB
Cassandra
Gremlin
表
在 Azure Cosmos DB 中,可通过两种方式来验证与数据库服务的交互:
每种身份验证方法授予对不同操作集的访问权限,但存在某种重叠:
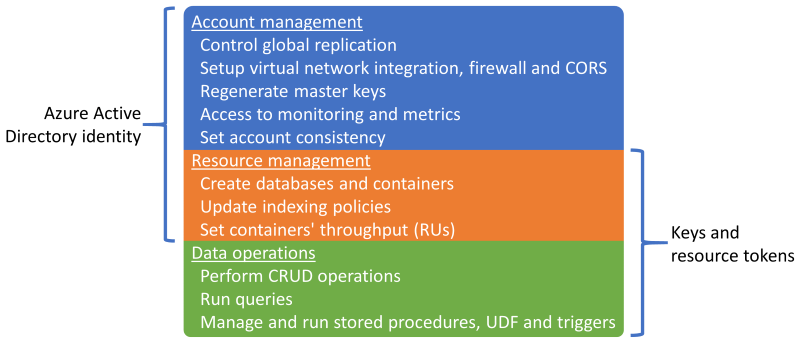
在某些情况下,你可能希望仅限组织中的某些用户执行数据操作(即 CRUD 请求和查询)。 不需要创建或删除资源,或者不需要更改所用容器的预配吞吐量的开发人员通常希望实施这种限制。
可通过应用以下步骤来限制访问:
- 为自己要限制访问权限的用户创建自定义 Microsoft Entra 角色。 该自定义 Active Directory 角色应使用 Azure Cosmos DB 的粒度操作对操作进行精细粒度的访问。
- 不允许使用密钥执行非数据操作。 可以通过将这些操作仅限为 Azure 资源管理器调用来实现此目的。
本文的后续部分将介绍如何执行这些步骤。
注意
若要执行后续部分所述的命令,需要安装 Azure PowerShell 模块 3.0.0 或更高版本,并且在尝试修改的订阅中需要具有 Azure 所有者角色。
在后续部分所述的 PowerShell 脚本中,请将以下占位符替换为特定于环境的值:
$MySubscriptionId- 包含要限制权限的 Azure Cosmos DB 帐户的订阅 ID。 例如:e5c8766a-eeb0-40e8-af56-0eb142ebf78e。$MyResourceGroupName- 包含 Azure Cosmos DB 帐户的资源组。 例如:myresourcegroup。$MyAzureCosmosDBAccountName- Azure Cosmos DB 帐户的名称。 例如:mycosmosdbsaccount。$MyUserName- 要限制其访问权限的用户的登录名 (username@domain)。 例如:cosmosdbuser@contoso.com。
选择 Azure 订阅
Azure PowerShell 命令要求登录,并选择要执行命令的订阅:
Connect-AzAccount -Environment AzureChinaCloud
Select-AzSubscription $MySubscriptionId
创建自定义 Microsoft Entra 角色
以下脚本将为 Azure Cosmos DB 帐户创建具有“仅限密钥”访问权限的 Microsoft Entra 角色分配。 该角色基于 Azure 自定义角色以及 Azure Cosmos DB 的粒度操作。 这些角色和操作是 Microsoft.DocumentDB Microsoft Entra 命名空间的一部分。
首先,创建包含以下内容的名为
AzureCosmosKeyOnlyAccess.json的 JSON 文档:{ "Name": "Azure Cosmos DB Key Only Access Custom Role", "Id": "00000000-0000-0000-0000-0000000000", "IsCustom": true, "Description": "This role restricts the user to read the account keys only.", "Actions": [ "Microsoft.DocumentDB/databaseAccounts/listKeys/action" ], "NotActions": [], "DataActions": [], "NotDataActions": [], "AssignableScopes": [ "/subscriptions/$MySubscriptionId" ] }运行以下命令以创建角色分配,并将其分配给用户:
New-AzRoleDefinition -InputFile "AzureCosmosKeyOnlyAccess.json" New-AzRoleAssignment -SignInName $MyUserName -RoleDefinitionName "Azure Cosmos DB Key Only Access Custom Role" -ResourceGroupName $MyResourceGroupName -ResourceName $MyAzureCosmosDBAccountName -ResourceType "Microsoft.DocumentDb/databaseAccounts"
不允许执行非数据操作
以下命令消除使用密钥执行以下操作的能力:
- 创建、修改或删除资源
- 更新容器设置(包括索引策略、吞吐量等)。
$cdba = Get-AzResource -ResourceType "Microsoft.DocumentDb/databaseAccounts" -ApiVersion "2015-04-08" -ResourceGroupName $MyResourceGroupName -ResourceName $MyAzureCosmosDBAccountName
$cdba.Properties.disableKeyBasedMetadataWriteAccess="True"
$cdba | Set-AzResource -Force