Azure 防火墙管理器是一种安全管理服务,可为基于云的安全外围提供集中安全策略和路由管理。
防火墙管理器可为两种网络体系结构类型提供安全管理:
安全虚拟中心
Azure 虚拟 WAN 中心是一种 Microsoft 托管资源,可用于轻松创建中心辐射型体系结构。 当安全和路由策略与此类中心相关联时,它被称为安全虚拟中心。
中心虚拟网络
这是你自己创建并管理的标准 Azure 虚拟网络。 安全策略在与此类中心关联后,会称为中心虚拟网络。 目前仅支持 Azure 防火墙策略。 您可以对等连接包含工作负荷服务器和服务的分支虚拟网络。 还可以在未对等互连到任何分支的独立虚拟网络中管理防火墙。
有关安全虚拟中心和中心虚拟网络体系结构的详细比较,请参阅什么是 Azure 防火墙管理器体系结构选项?
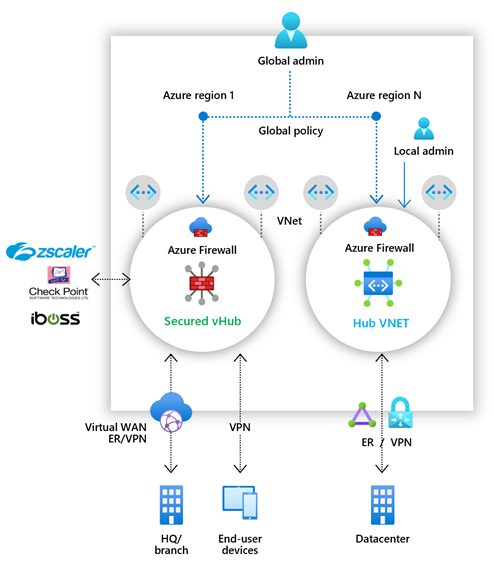
Azure 防火墙管理器功能
Azure 防火墙管理器具有以下功能:
中央 Azure 防火墙部署和配置
可以集中部署和配置多个跨不同 Azure 区域和订阅的 Azure 防火墙实例。
分层策略(全局和本地)
可以使用 Azure 防火墙管理器跨多个安全虚拟中心集中管理 Azure 防火墙策略。 中央 IT 团队可以创作全局防火墙策略,跨团队实施组织范围的防火墙策略。 本地创作的防火墙策略允许 DevOps 自助服务模型,敏捷性更高。
与合作伙伴安全即服务集成,安全性更好
除了 Azure 防火墙,还可以集成合作伙伴安全即服务 (SECaaS) 提供程序,为虚拟网络和分支 Internet 连接提供更多网络保护。
此功能仅在安全虚拟中心部署中可用。
虚拟网络到互联网 (V2I) 流量过滤
- 使用首选合作伙伴安全提供程序筛选出站虚拟网络流量。
- 对 Azure 上运行的云工作负载使用高级用户感知型 Internet 保护。
分支到 Internet (B2I) 流量筛选
利用 Azure 的连接性和全球网络覆盖,轻松为分支连接到互联网的方案添加合作伙伴筛选功能。
有关安全合作伙提供程序的详细信息,请参阅什么是 Azure 防火墙管理器安全合作伙伴提供程序?
集中式路由管理
轻松地将流量路由到安全中心进行筛选和记录,无需在分支虚拟网络上手动设置用户定义路由 (UDR)。
此功能仅在安全虚拟中心部署中可用。
可以将分支到 Internet (B2I) 流量筛选的合作伙伴提供商与用于分支到虚拟网络 (B2V)、虚拟网络到虚拟网络 (V2V) 和虚拟网络到 Internet (V2I) 的 Azure 防火墙同时使用。
DDoS 防护计划
可以在 Azure 防火墙管理器中将虚拟网络与 DDoS 防护计划相关联。 有关详细信息,请参阅使用 Azure 防火墙管理器配置 Azure DDoS 防护计划。
管理 Web 应用程序防火墙策略
可以为应用程序交付平台(包括 Azure Front Door 和 Azure 应用程序网关)集中创建和关联 Web 应用程序防火墙 (WAF) 策略。 有关详细信息,请参阅管理 Web 应用程序防火墙策略。
区域可用性
可以跨区域使用 Azure 防火墙策略。 例如,可以在中国北部创建策略,并在中国东部使用它。
已知问题
Azure 防火墙管理器存在以下已知问题:
| 問题 | Description | 缓解措施 |
|---|---|---|
| 流量分流 | 当前不支持 Microsoft 365 和 Azure 公共 PaaS 流量拆分。 因此,选择 V2I 或 B2I 的合作伙伴提供商时,所有 Azure 公共 PaaS 和 Microsoft 365 的流量也会通过合作伙伴服务发送。 | 调查集线器的流量分配。 |
| 基本策略必须与本地策略位于同一区域中 | 可在与基本策略相同的区域中创建所有本地策略。 仍可以将一个区域中创建的策略应用于另一个区域的安全枢纽。 | 正在调查 |
| 在安全的虚拟中心部署中筛选中心之间的流量 | 尚不支持安全虚拟中心到安全虚拟中心通信筛选。 但是,如果未启用通过 Azure 防火墙进行专用流量筛选,中心到中心通信仍然有效。 | 正在调查 |
| 启用了专用流量筛选的分支之间的流量 | 启用专用流量筛选后,不支持分支到分支流量。 | 调查中... 如果分支到分支连接至关重要,请不要加密专用流量。 |
| 共享同一虚拟 WAN 的所有安全虚拟中心必须位于同一资源组中。 | 此行为现在与虚拟 WAN 中心保持一致。 | 创建多个虚拟 WAN,以允许在不同的资源组中创建安全虚拟中心。 |
| 批量 IP 地址添加失败 | 如果添加多个公共 IP 地址,安全中心防火墙将进入失败状态。 | 添加较小的公共 IP 地址增量。 例如,一次添加 10 个。 |
| 安全虚拟中心不支持 DDoS 防护 | DDoS 防护未与 vWAN 集成。 | 正在调查 |
| 活动日志未得到充分支持 | 防火墙策略当前不支持活动日志。 | 正在调查 |
| 不完全支持的规则描述 | 防火墙策略不在 ARM 导出中显示规则说明。 | 正在调查 |
| Azure 防火墙管理器会覆盖静态和自定义路由,从而导致虚拟 WAN 中心出现停机。 | 不应使用 Azure 防火墙管理器管理使用自定义路由或静态路由配置的部署中的设置。 来自防火墙管理器的更新可能会覆盖静态或自定义路由设置。 | 如果使用静态路由或自定义路由,请使用虚拟 WAN 页管理安全设置,避免通过 Azure 防火墙管理器进行配置。 有关详细信息,请参阅方案:Azure 防火墙 - 自定义。 |