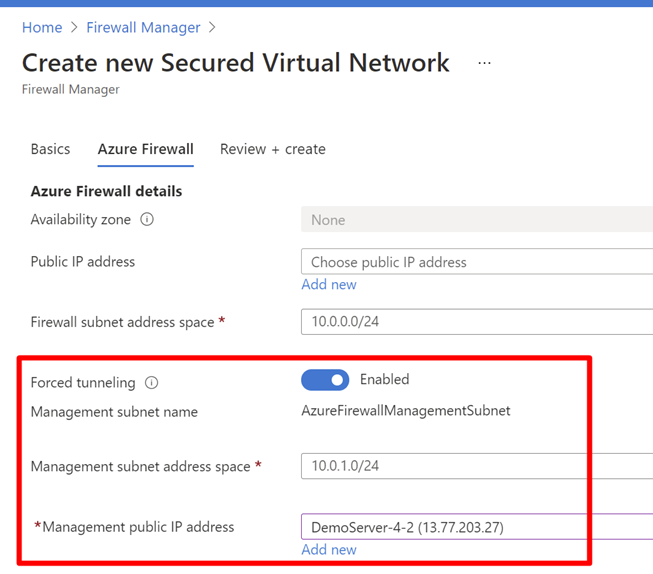
当配置新的 Azure 防火墙时,将所有 Internet 绑定的流量路由到指定的下一个跃点,而不是直接转到 Internet。 例如,你可以通过 BGP 或用户定义路由 (UDR) 来播发默认路由,以便将网络流量强制发送到本地边缘防火墙或其他网络虚拟设备 (NVA),从而在该流量传递到 Internet 之前对其进行处理。 若要支持此配置,必须创建已启用防火墙管理 NIC 的 Azure 防火墙。
你可能不希望直接向 Internet 公开某个公共 IP 地址。 在这种情况下,可以部署启用了管理 NIC 的 Azure 防火墙,而无需公共 IP 地址。 启用管理 NIC 后,它会创建一个管理接口,其中包含 Azure 防火墙用于其操作的公共 IP 地址。 公共 IP 地址仅供 Azure 平台使用,不能用于任何其他目的。 可以在没有公共 IP 地址的情况下配置租户数据路径网络,并且可以强制 Internet 流量通过隧道传输到另一个防火墙或阻止其传输。
对于发往公共 IP 地址的所有出站流量,Azure 防火墙提供自动 SNAT。 如果目标 IP 地址是符合 IANA RFC 1918 的专用 IP 地址范围,Azure 防火墙不会执行 SNAT。 将出口流量直接路由到 Internet 时,此逻辑非常有效。 但是,如果配置强制隧道,则会将 Internet 绑定的流量可能会由 SNAT 转换为 AzureFirewallSubnet 中的某个防火墙专用 IP 地址。 这样可向本地防火墙隐藏源。 通过添加“0.0.0.0/0”作为专用 IP 地址范围,可将 Azure 防火墙配置为无论目标 IP 地址为何都不会执行 SNAT。 通过此配置,Azure 防火墙永远不能将出口流量直接路由到 Internet。 有关详细信息,请参阅 Azure 防火墙 SNAT 专用 IP 地址范围。
Azure 防火墙还支持拆分隧道,这是有选择地路由流量的功能。 例如,可以将 Azure 防火墙配置为将所有流量定向到本地网络,同时将流量路由到 Internet 进行 KMS 激活,确保 KMS 服务器已激活。 可以使用 AzureFirewallSubnet 上的路由表执行此操作。 有关详细信息,请参阅在强制隧道模式下配置 Azure 防火墙 - Azure 社区中心。
重要
如果在虚拟 WAN 中心(安全虚拟中心)内部署 Azure 防火墙,则当前不支持通过 Express Route 或 VPN 网关播发默认路由。 我们正在研究修复措施。
重要
在启用了强制隧道的情况下不支持 DNAT。 由于采用非对称路由,在启用了强制隧道的情况下部署的防火墙无法支持从 Internet 进行入站访问。 但是,具有管理 NIC 的防火墙仍支持 DNAT。
强制隧道配置
启用防火墙管理 NIC 后,AzureFirewallSubnet 现在可以包括到任何本地防火墙或 NVA 的路由,以便在将流量传递到 Internet 之前对其进行处理。 如果在此子网上启用了“传播网关路由”,还可以通过 BGP 将这些路由发布到 AzureFirewallSubnet。
例如,你可以在 AzureFirewallSubnet 上创建一个默认路由并使用你的 VPN 网关作为下一跃点,以到达你的本地设备。 还可以启用“传播网关路由”以获得通向本地网络的合适路由。
如果配置强制隧道,则会将 Internet 绑定的流量由 SNAT 转换为 AzureFirewallSubnet 中的某个防火墙专用 IP 地址,从而向本地防火墙隐藏源。
如果组织对专用网络使用公共 IP 地址范围,Azure 防火墙会通过 SNAT 将流量发送到 AzureFirewallSubnet 中的某个防火墙专用 IP 地址。 但是,可以将 Azure 防火墙配置为不 SNAT 公共 IP 地址范围。 有关详细信息,请参阅 Azure 防火墙 SNAT 专用 IP 地址范围。