Azure Policy 的最大优势之一在于它针对订阅或订阅管理组中的资源提供的见解和控制度。 此控件可以防止在错误的位置创建资源、强制实施通用和一致的标记使用情况,或审核现有资源以获取适当的配置和设置。 在所有情况下,Azure Policy 都会生成数据,使你能够了解环境的符合性状态。
在查看符合性数据之前,请务必了解 Azure Policy 中的符合性状态。
可通过多种方式访问策略和计划分配生成的符合性信息:
在探讨符合性报告方法之前,让我们了解符合性信息的更新时间和频率,以及触发评估周期的事件。
评估触发器
已完成的评估周期的结果通过 Microsoft.PolicyInsights 和 PolicyStates 操作在 PolicyEvents 资源提供程序中获取。 有关 Azure Policy Insights REST API 操作的详细信息,请参阅 。
已分配的策略和计划的评估会在各种事件后发生:
- 最近已将策略或计划分配到某个范围。 将分配应用到定义的范围大约需要五分钟,然后评估周期开始针对新分配的策略或计划使用适用的资源。 根据使用的效果,将资源标记为合规、不合规、豁免或未知。 针对大范围的资源评估的大型策略或计划可能需要花费一段时间,因此,在评估周期何时完成方面,无法预先定义预期目标。 完成后,门户和软件开发工具包(SDK)中提供了更新的符合性结果。
- 更新了已分配到某个范围的策略或计划。 此场景的评估周期和计时与新的范围分配相同。
- 资源将通过 Azure 资源管理器、REST API 或受支持的 SDK 部署到包含分配的范围或在其中进行更新。 在此场景中,个体资源的效果事件(追加、审核、拒绝、部署)和符合性状态将在大约 15 分钟后出现在门户与 SDK 中。 此事件不会导致对其他资源进行评估。
- 在
Microsoft.Resources/subscriptions中创建或移动订阅(资源类型 ),并有一个针对订阅资源类型的已分配策略定义。 评估订阅支持的效果(audit、auditIfNotExist、deployIfNotExists、modify),日志记录和任何修正操作大约需要 30 分钟。 - 创建、更新或删除了策略豁免。 在此方案中,会为定义的豁免范围评估相应的分配。
- 标准符合性评估周期。 分配每隔 24 小时自动重新评估一次。 大量资源的大型策略或计划可能需要一些时间,因此评估周期完成时没有预定义的预期。 完成评估后,更新的符合性结果会在门户和 SDK 中提供。
- 来宾配置资源提供程序通过受管理资源更新了符合性详细信息。
- 按需扫描。
注意
根据设计,Azure Policy 免除了资源提供程序下 Microsoft.Resources 的所有资源(可以评估的订阅和资源组除外) 的策略评估。
按需评估扫描
可以使用 REST、Azure CLI、Azure PowerShell 对订阅或资源组的评估扫描。 按需扫描是一个异步过程,需要很长时间才能运行,因为会根据所有分配的策略评估资源。
注意
并非所有 Azure 资源提供程序都支持按需评估扫描。
使用 REST 进行按需评估扫描
作为异步进程,启动扫描的 REST 终结点不是等到扫描完成才能响应。 而是提供一个 URI,用于查询请求的评估的状态。
在每个 REST API URI 中,包含替换为自己的值所使用的变量:
-
{resourceGroupName}:替换为资源组的名称。 -
{subscriptionId}:替换为订阅 ID。
扫描支持评估订阅或资源组中的资源。 使用以下 URI 结构,通过 REST API POST 命令开始按范围扫描:
使用以下命令评估订阅。
POST https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/providers/Microsoft.PolicyInsights/policyStates/latest/triggerEvaluation?api-version=2019-10-01
使用以下命令评估资源组。
POST https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.PolicyInsights/policyStates/latest/triggerEvaluation?api-version=2019-10-01
订阅和资源组 REST API 调用返回 202 已接受 状态。 响应标头中包含 location 属性,格式如下:
https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/providers/Microsoft.PolicyInsights/asyncOperationResults/{ResourceContainerGUID}?api-version=2019-10-01
以静态方式为请求的范围生成了 {ResourceContainerGUID}。 如果某个范围已在运行按需扫描,则不会启动新扫描。 改为为新请求提供相同的 {ResourceContainerGUID}location URI 以获取状态。 在评估过程中,location URI 的 REST API GET 命令会返回“202 已接受”。 评估扫描完成后,它会返回“200 正常”状态。 已完成扫描的正文是一个 JSON 响应,其状态为: succeeded。
使用 Azure CLI 进行按需评估扫描
符合性扫描从 az policy state trigger-scan 命令开始。
默认情况下,az policy state trigger-scan 开始评估当前订阅中的所有资源。 若要对特定资源组开始评估,请使用 resource-group 参数。 以下示例在资源组的当前订阅中启动符合性扫描。 替换为 resourceGroupName 资源组的名称:
az policy state trigger-scan --resource-group "resourceGroupName"
利用 no-wait 参数,可以选择在继续之前不等待异步过程完成。
使用 Azure PowerShell 进行按需评估扫描
符合性扫描从 Start-AzPolicyComplianceScan cmdlet 开始。
默认情况下,Start-AzPolicyComplianceScan 开始评估当前订阅中的所有资源。 若要对特定资源组开始评估,请使用 ResourceGroupName 参数。 以下示例在资源组的当前订阅中启动符合性扫描。 替换为 resourceGroupName 资源组的名称:
Start-AzPolicyComplianceScan -ResourceGroupName 'resourceGroupName'
你可以让 PowerShell 在提供结果输出前等待完成异步调用,或者将其作为作业在后台运行。 若要通过 PowerShell 作业在后台运行符合性扫描,请使用 AsJob 参数,并将值设置为对象,例如此示例中的 $job:
$job = Start-AzPolicyComplianceScan -AsJob
你可以通过检查 $job 对象来检查作业的状态。 作业类型为 Microsoft.Azure.Commands.Common.AzureLongRunningJob。 使用 Get-Member 对象上的 $job 查看可用的属性和方法。
在运行符合性扫描时,检查 $job 对象会输出结果,如下所示:
$job
Id Name PSJobTypeName State HasMoreData Location Command
-- ---- ------------- ----- ----------- -------- -------
2 Long Running O... AzureLongRunni... Running True localhost Start-AzPolicyCompliance...
符合性扫描完成后,“State”属性更改为“已完成”。
使用 Visual Studio Code 进行按需评估扫描
适用于 Visual Studio Code 的 Azure Policy 扩展能够运行特定资源的评估扫描。 此扫描是一个同步过程,与 Azure PowerShell 和 REST 方法不同。 有关详细信息和步骤,请参阅 VS Code 扩展的按需评估。
Portal
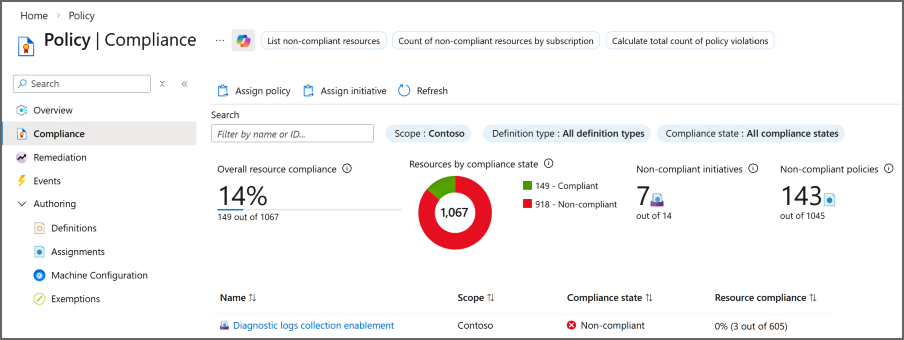
Azure 门户展示了一个图形体验用于可视化和了解环境中的符合性状态。 在“策略”页上,“概述”选项提供了策略和计划符合性的可用范围的详细信息。 除了符合性状态和每个分配的计数以外,该页还包含一个图表,显示过去七天的符合性。 “符合性”页包含上述大量相同信息(图表除外),但提供更多筛选和排序选项。
由于策略或计划可分配到不同的范围,因此表中包含每个分配的范围,以及分配的定义类型。 还提供每个分配项中不合规资源和不合规策略的数量。 选择表中的某个策略或计划可以更深入地了解该特定分配的合规性。
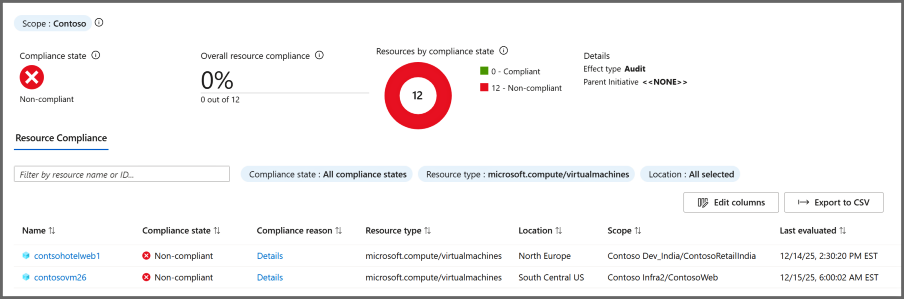
“资源符合性”选项卡上的资源列表显示当前分配的现有资源的评估状态。 选项卡默认为所有的合规状态,但可以进行筛选。
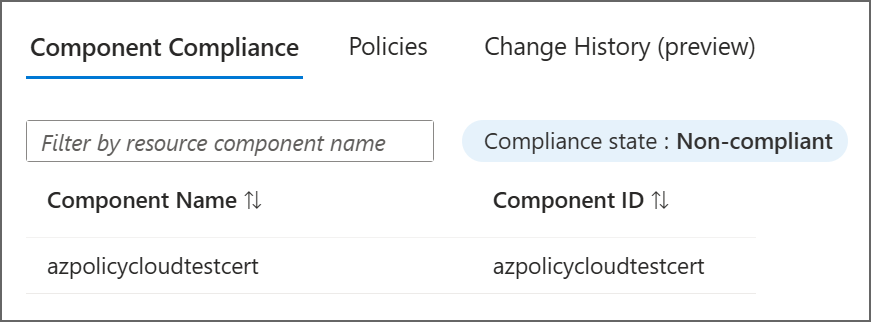
对于 资源提供程序模式 资源,在“ 资源符合性 ”选项卡上,选择资源将打开组件符合性详细信息。 此页面还提供选项卡,以查看分配给此资源的策略和更改历史记录。
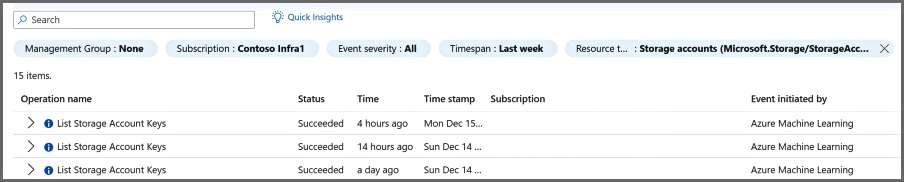
返回“资源符合性”页,右键单击要收集更多详细信息的事件行,然后选择“ 显示活动日志”。 活动日志页将会打开,其中的搜索结果经过预先筛选,显示分配和事件的详细信息。 活动日志提供了有关这些事件的更多上下文和信息。
注意
即使采用上述格式的符合性结果,也可以使用 Azure Resource Graph 查询从门户导出。
命令行
可以使用 REST API、Azure CLI 和 Azure PowerShell 检索门户中提供的相同信息。
REST API
有关 REST API 的详细信息,请参阅 Azure Policy 参考。 还可以使用 Azure CLI 或首选的 REST API 客户端来运行命令。
汇总结果
使用 REST API,可以按容器、定义或分配进行汇总。 下面是使用 Azure 策略见解的按订阅汇总功能在订阅级别执行的汇总示例:
POST https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/providers/Microsoft.PolicyInsights/policyStates/latest/summarize?api-version=2019-10-01
输出汇总了订阅,汇总的符合性在属性中nonCompliantResourcesnonCompliantPolicies。 此请求提供其他详细信息,包括构成不合规号码的每个分配以及每个分配的定义信息。 层次结构中的每个策略对象提供一个可用于获取该级别的更多详细信息的 queryResultsUri。
查询资源
在上一示例中,value.policyAssignments.policyDefinitions.results.queryResultsUri 提供了一个示例 URI,用于特定策略定义的所有不符合资源。 在 $filter 值中,ComplianceState 等于 NonCompliant,PolicyAssignmentId 是针对策略定义指定的,然后又针对 PolicyDefinitionId 本身指定的。 在筛选器中包含 PolicyAssignmentId 的原因是,PolicyDefinitionId 可能在具有不同范围的多个策略或计划分配中存在。 通过指定 PolicyAssignmentId 和 PolicyDefinitionId,可以明确指定想要查找的结果。 以前,我们使用了 PolicyStates 作为 latest,因此将 from 和 to 时间范围自动设置成了过去 24 小时。
queryResultsUri值示例:
https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/providers/Microsoft.PolicyInsights/policyStates/latest/queryResults?api-version=2019-10-01&$from=2025-01-01 04:28:22Z&$to=2025-02-10 04:28:22Z&$filter=ComplianceState eq 'NonCompliant' and PolicyAssignmentId eq '/subscriptions/{subscriptionId}/resourcegroups/rg-tags/providers/microsoft.authorization/policyassignments/37ce239ae4304622914f0c77' and PolicyDefinitionId eq '/providers/microsoft.authorization/policydefinitions/1e30110a-5ceb-460c-a204-c1c3969c6d62'
查看事件
创建或更新资源时,将生成策略评估结果。 结果称为“策略事件”。 使用以下 URI 查看与订阅关联的最近策略事件。
https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/providers/Microsoft.PolicyInsights/policyEvents/default/queryResults?api-version=2019-10-01
有关查询策略事件的详细信息,请参阅 Azure Policy 事件。
Azure CLI
适用于 Azure Policy 的 Azure CLI 命令组涵盖 REST 或 Azure PowerShell 中提供的大多数操作。 有关可用命令的完整列表,请参阅 az policy。
获取最顶层分配的策略的状态摘要,该策略具有最高数量的不符合资源。
az policy state summarize --top 1
获取最近评估的资源的状态记录,输出默认值按时间戳降序排列。
az policy state list --top 1
获取所有不合规虚拟网络资源的详细信息。
az policy state list --filter "ResourceType eq 'Microsoft.Network/virtualNetworks'"
获取与特定日期之后发生的不合规虚拟网络资源相关的事件。 使用 from 采用 ISO 8601 格式的日期的参数。
az policy event list --filter "ResourceType eq 'Microsoft.Network/virtualNetworks'" --from '2025-02-10T00:00:00Z'
Azure PowerShell
获取最顶层分配的策略的状态摘要,该策略具有最高数量的不符合资源。
Get-AzPolicyStateSummary -Top 1
获取最近评估的资源的状态记录。 输出默认值按时间戳降序排列。
Get-AzPolicyState -Top 1
获取所有不合规虚拟网络资源的详细信息。
Get-AzPolicyState -Filter "ResourceType eq '/Microsoft.Network/virtualNetworks'"
获取与特定日期之后发生的不合规虚拟网络资源相关的事件。 使用 From 采用 ISO 8601 格式的日期的参数。
Get-AzPolicyEvent -Filter "ResourceType eq '/Microsoft.Network/virtualNetworks'" -From '2025-02-10'
输出包含一个 PrincipalOid 属性,可用于使用 Azure PowerShell cmdlet Get-AzADUser获取特定用户。 替换为 {principalOid} 从上一命令获取的值。
(Get-AzADUser -ObjectId {principalOid}).DisplayName
Azure Monitor 日志
如果具有与订阅关联的活动 Log Analytics 解决方案中的 AzureActivity,则还可以使用 Kusto 查询和AzureActivity表查看新资源和更新资源的评估中的不符合结果。 借助 Azure Monitor 日志中的详细信息,可对警报进行配置,以监视不符合情况。
Azure Resource Graph
合规性记录存储在 Azure Resource Graph (ARG) 中。 可以从 ARG 查询导出数据,以基于感兴趣的范围和策略生成自定义仪表板。 查看有关通过 ARG 导出合规性数据的示例查询。
后续步骤
- 在 Azure Policy 示例中查看示例。
- 查看 Azure Policy 定义结构。
- 查看了解策略效果。
- 了解如何以编程方式创建策略。
- 了解如何修正不符合的资源。
- 参阅使用 Azure 管理组来组织资源,了解什么是管理组。