本文介绍在设备预配服务 (DPS) 中使用受信任的平台模块 (TPM) 证明预配设备时涉及的概念。 本文与所有参与设备部署准备工作的人员相关。
受信任的平台模块(TPM)是一种硬件安全模块(HSM)。 本文假设您正在使用离散型、固件型或集成型TPM。 软件模拟 TPM 非常适合原型制作或测试,但它们不提供与离散、固件或集成 TPM 相同的安全级别。 不建议在生产环境中使用软件 TPM。
本文仅适用于将 TPM 2.0 与基于哈希的消息身份验证代码(HMAC)密钥支持及其认可密钥配合使用的设备。 TPM 是受信任的计算组的行业范围内 ISO 标准,你可以在 完整的 TPM 2.0 规范 或 ISO/IEC 11889 规范中阅读有关 TPM 的详细信息。本文还假定你熟悉公钥和私钥对,以及它们如何用于加密。
设备预配服务设备 SDK 可处理本文中所述的所有内容。 如果在设备上使用 SDK,则无需实现 TPM 支持。 本文以概念的方式介绍设备预配时在 TPM 安全芯片上发生的情况,并说明了其安全性高的原因。
概述
TPM 使用称为认可密钥(EK)的内容作为安全信任根。 EK 特定于 TPM,更改它相当于把设备变为新设备。
TPM 具有另一种类型的密钥,称为存储根密钥(SRK)。 TPM 的所有者在获取 TPM 的所有权后可以生成 SRK。 获取 TPM 的所有权就是以 TPM 特有的方式表明“某人在 HSM 上设置密码”。如果将 TPM 设备出售给新的所有者,新的所有者可以在获取 TPM 的所有权后生成新的 SRK。 重新生成 SRK 可确保以前的所有者无法使用 TPM。 由于 SRK 特定于 TPM 的所有者,因此可以通过 SRK 将数据封装到该所有者的 TPM 本身中。 SRK 为所有者提供了存储密钥的沙盒,并提供在出售设备(如 TPM)时撤销访问权限的功能。 这就像搬进一栋新房子:拥有所有权就意味着更换门锁,并处理以前业主(SRK)留下的所有家具,但你无法改变房子的地址(EK)。
设置设备后,它具有 EK 和 SRK 可供使用。
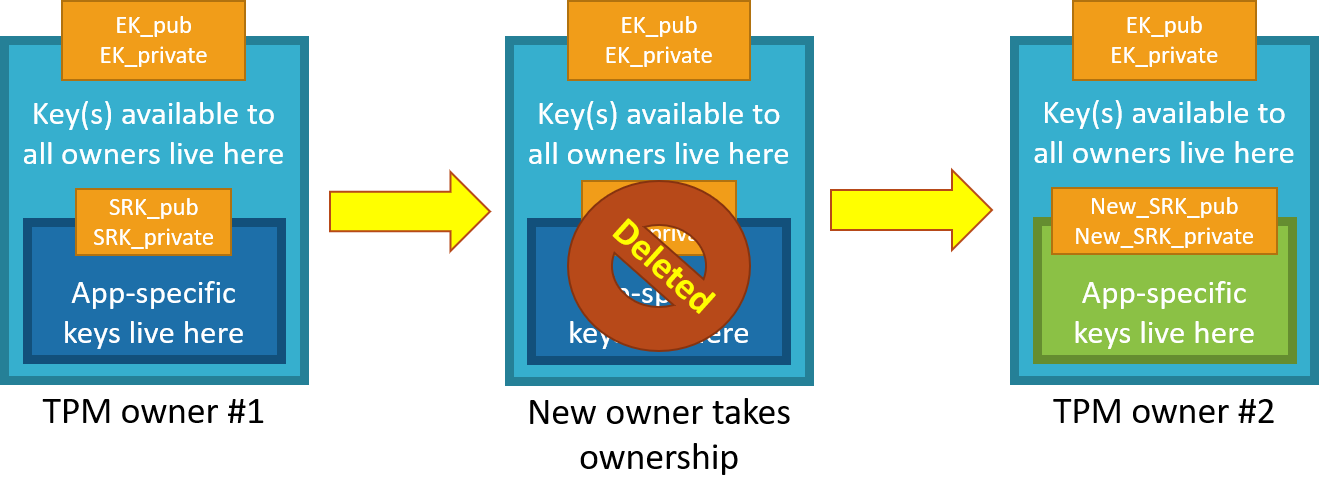
获取 TPM 所有权所涉及的具体步骤因制造商、正在使用的 TPM 工具集和设备作系统而异。
设备预配服务使用 EK 的公共部分 (EK_pub) 来标识和注册设备。 设备供应商可以在制造或最终测试期间读取EK_pub,并将EK_pub上传到预配服务,以便在设备连接到预配时识别设备。 设备预配服务不会检查 SRK 或所有者,因此“清除”TPM 会擦除客户数据,但会保留 EK(和其他供应商数据),设备预配服务在连接到预配时仍可识别设备。
证明过程
带 TPM 的设备在连接到设备预配服务时,该服务会首先根据存储在注册列表中的 EK_pub 来核对提供的 EK_pub。 如果EK_pubs不符,则设备不允许进行预配。 如果 EK_pub 相符,服务就会要求设备通过 nonce 质询证明 EK 专用部分的所有权,该质询是一种用来证明身份的安全质询。 设备预配服务生成一个 nonce,然后使用 SRK 和 EK_pub 先后对其加密。SRK 和 EK_pub 均由设备在初始注册调用过程中提供。 TPM 始终会确保 EK 专用部分的安全。 此安全性可防止伪造,并确保将 SAS 令牌安全地预配到授权的设备。
让我们详细探讨证明过程。
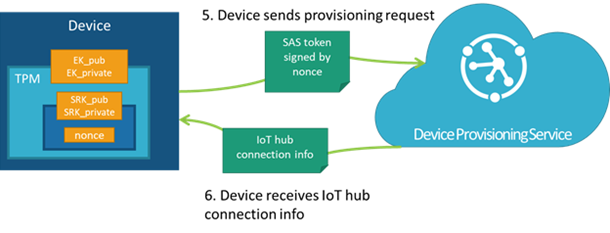
设备请求 IoT 中心分配
首先,设备连接到设备预配服务并请求预配。 为此,设备向服务提供其注册 ID、ID 作用域,以及 TPM 的 EK_pub 和 SRK_pub。 服务将加密的 nonce 传回给设备,要求设备解密该 nonce,然后使用它为 SAS 令牌签名,以便再次进行连接并完成预配。

Nonce 质询
设备获得 nonce 后,会使用 EK 和 SRK 的专用部分将 nonce 解密到 TPM 中;nonce 加密的顺序是将 EK 的信任(不可变)委托给 SRK(在新的所有者获取 TPM 所有权后可以更改)。
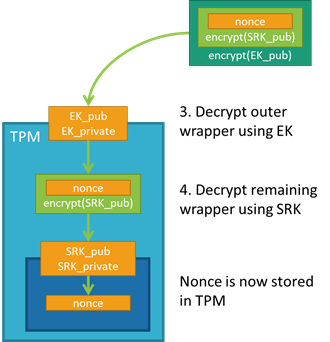
验证 nonce 并接收凭据
然后,设备可以使用解密的 nonce 给 SAS 令牌签名,并使用签名的 SAS 令牌重新建立到设备预配服务的连接。 完成 Nonce 质询以后,服务就会允许设备进行预配。