在创建一个或多个 Key Vault 之后,可能需要监视 Key Vault 的访问方式、时间和访问者。 有关该功能的完整详细信息,请参阅 Azure Key Vault 日志记录。
记录的内容:
- 所有经过身份验证的 REST API 请求,包括由于访问权限、系统错误或错误请求而失败的请求。
- 对密钥保管库本身的作,包括创建、删除、设置密钥保管库访问策略以及更新密钥保管库属性(如标记)。
- 对 Key Vault 中的密钥和机密执行的操作,包括:
- 创建、修改或删除这些密钥或机密。
- 签名、验证、加密、解密、包装和解包密钥、获取机密以及列出密钥和机密(及其版本)。
- 导致 401 响应的未经身份验证的请求。 例如,缺少持有者令牌、格式不正确或已过期或令牌无效的请求。
- 以下条件的 Azure 事件网格通知事件包括:过期、即将过期和变更保管库访问策略(不记录新版本事件)。 即使密钥保管库上创建了事件订阅,也会记录事件。 有关详细信息,请参阅 Azure Key Vault 作为事件网格源。
先决条件
若要完成本教程,需要一个 Azure 密钥保管库。 可以使用以下方法之一创建新的密钥保管库:
您还需要为日志指定一个目的地。 目标可以是现有或新的 Azure 存储帐户和/或 Log Analytics 工作区。
可以使用以下方法之一创建新的 Azure 存储帐户:
可以使用以下方法之一创建新的 Log Analytics 工作区:
- 使用 Azure CLI 创建 Log Analytics 工作区
- 使用 Azure PowerShell 创建 Log Analytics 工作区
- 在 Azure 门户中创建 Log Analytics 工作区
连接到 Key Vault 订阅
设置密钥日志记录的第一步是连接到包含密钥保管库的订阅(如果有多个订阅与帐户关联)。
使用 Azure CLI,可以使用 az account list 命令查看所有订阅。 然后使用 az account set 命令连接到一个账户:
az account list
az account set --subscription "<subscriptionID>"
使用 Azure PowerShell,可以首先使用 Get-AzSubscription cmdlet 列出订阅。 然后,使用 Set-AzContext cmdlet 连接到其中一个:
Get-AzSubscription
Set-AzContext -SubscriptionId "<subscriptionID>"
获取资源标识符
若要在密钥保管库上启用日志记录,你需要具有密钥保管库的资源 ID 以及目的地(Azure 存储或 Log Analytics 帐户)。
如果记不起密钥保管库的名称,可以使用 Azure CLI az keyvault list 命令或 Azure PowerShell Get-AzKeyVault cmdlet 查找它。
使用密钥保管库的名称查找其资源 ID。 使用 Azure CLI 时,请使用 az keyvault show 命令。
az keyvault show --name "<your-unique-keyvault-name>"
通过 Azure PowerShell,请使用 Get-AzKeyVault cmdlet。
Get-AzKeyVault -VaultName "<your-unique-keyvault-name>"
密钥保管库的资源 ID 采用以下格式:“/subscriptions/your-subscription-ID/resourceGroups/myResourceGroup/providers/Microsoft.KeyVault/vaults/your-unique-keyvault-name。 在下一步骤中请注意这一点。
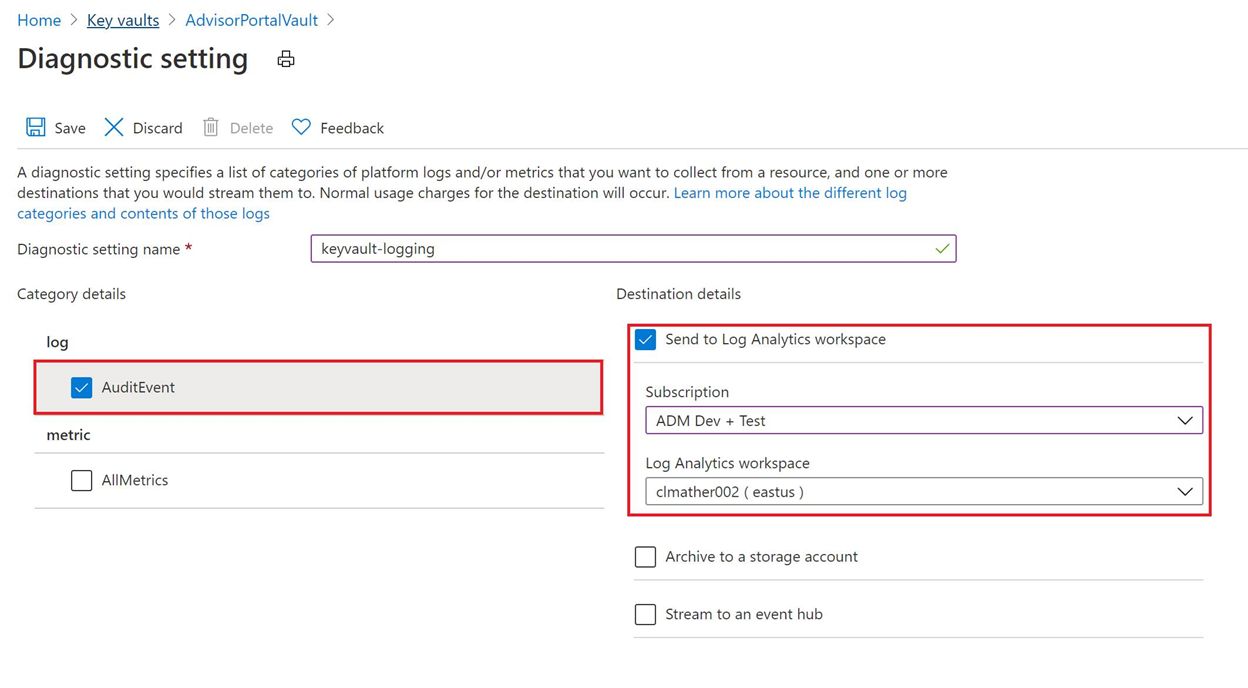
启用日志记录
您可以使用 Azure CLI、Azure PowerShell 或 Azure 门户为 Key Vault 启用日志记录。
- Azure CLI
- Azure PowerShell
- Azure 门户
Azure 命令行接口 (CLI)
使用 Azure CLI az monitor diagnostic-settings create 命令、存储帐户 ID 和密钥保管库资源 ID,如下所示:
az monitor diagnostic-settings create --storage-account "<storage-account-id>" --resource "<key-vault-resource-id>" --name "Key vault logs" --logs '[{"category": "AuditEvent","enabled": true}]' --metrics '[{"category": "AllMetrics","enabled": true}]'
(可选)可以为日志设置保留策略,以便在指定时间后自动删除旧日志。 例如,可以设置自动删除超过 90 天的日志的保留策略。
使用 Azure CLI 时,请使用 az monitor diagnostic-settings update 命令。
az monitor diagnostic-settings update --name "Key vault retention policy" --resource "<key-vault-resource-id>" --set retentionPolicy.days=90
访问日志
您提供的存储帐户中的 insights-logs-auditevent 容器中包含您的 Key Vault 日志。 若要查看这些日志,必须下载 Blob。
首先,列出容器中的所有 Blob。 使用 Azure CLI 时,请使用 az storage blob list 命令。
az storage blob list --account-name "<your-unique-storage-account-name>" --container-name "insights-logs-auditevent"
在 Azure PowerShell 中,使用 Get-AzStorageBlob。 若要列出此容器中的所有 Blob,请输入:
Get-AzStorageBlob -Container "insights-logs-auditevent" -Context $sa.Context
从 Azure CLI 命令或 Azure PowerShell cmdlet 的输出中,可以看到 blob 的名称采用以下格式: resourceId=<ARM resource ID>/y=<year>/m=<month>/d=<day of month>/h=<hour>/m=<minute>/filename.json 日期和时间值使用协调世界时。
由于可以使用同一存储帐户来收集多个资源的日志,因此 blob 名称中的完整资源 ID 可用于仅访问或下载所需的 Blob。
但首先,下载所有 Blob。 使用 Azure CLI 时,请使用 az storage blob download 命令,向其传递 blob 的名称,以及要在其中保存结果的文件的路径。
az storage blob download --container-name "insights-logs-auditevent" --file <path-to-file> --name "<blob-name>" --account-name "<your-unique-storage-account-name>"
使用 Azure PowerShell,使用 Get-AzStorageBlob cmdlet 获取 Blob 列表。 然后通过管道将列表传递给 Get-AzStorageBlobContent cmdlet,将日志下载到所选路径。
$blobs = Get-AzStorageBlob -Container "insights-logs-auditevent" -Context $sa.Context | Get-AzStorageBlobContent -Destination "<path-to-file>"
在 PowerShell 中运行第二个 cmdlet 时, / blob 名称中的分隔符会在目标文件夹下创建完整的文件夹结构。 你将使用此结构下载 Blob 并将其存储为文件。
若要选择性地下载 Blob,请使用通配符。 例如:
如果有多个密钥保管库,并且只想下载一个密钥保管库的日志,请命名为CONTOSOKEYVAULT3:
Get-AzStorageBlob -Container "insights-logs-auditevent" -Context $sa.Context -Blob '*/VAULTS/CONTOSOKEYVAULT3如果有多个资源组,并且只想下载一个资源组的日志,请使用
-Blob '*/RESOURCEGROUPS/<resource group name>/*':Get-AzStorageBlob -Container "insights-logs-auditevent" -Context $sa.Context -Blob '*/RESOURCEGROUPS/CONTOSORESOURCEGROUP3/*'如果要下载 2019 年 1 月的所有日志,请使用
-Blob '*/year=2019/m=01/*':Get-AzStorageBlob -Container "insights-logs-auditevent" -Context $sa.Context -Blob '*/year=2016/m=01/*'
使用 Azure Monitor 日志
可以使用 Azure Monitor 日志中的 Key Vault 解决方案查看 Key Vault AuditEvent 日志。 在 Azure Monitor 日志中,可以使用日志查询来分析数据并获取所需的信息。 有关详细信息,请参阅 监控密钥保管库。
后续步骤
- 有关概念性信息,包括如何解释 Key Vault 日志,请参阅 Key Vault 日志记录。
- 若要了解有关使用 Azure Monitor 对 Key Vault 进行监视的详细信息,请参阅 监视 Key Vault。