Azure Key Vault 是为密钥、密码、证书等机密及其他机密提供安全存储的云服务。 本快速入门重点介绍部署 Azure 资源管理器模板(ARM 模板)以创建密钥保管库和机密的过程。
Azure 资源管理器模板是定义项目基础结构和配置的 JavaScript 对象表示法 (JSON) 文件。 模板使用声明性语法。 你可以在不编写用于创建部署的编程命令序列的情况下,描述预期部署。
如果你的环境满足先决条件,并且你熟悉如何使用 ARM 模板,请选择“部署到 Azure”按钮。 Azure 门户中会打开模板。
先决条件
若要完成本文,需要做好以下准备:
如果没有 Azure 订阅,请在开始前创建一个试用版订阅。
模板需要使用你的 Microsoft Entra 用户对象 ID 来配置权限。 以下过程获取对象 ID (GUID)。
运行以下 Azure PowerShell 或 Azure CLI 命令:选择“试用”,然后在 shell 窗格中粘贴脚本。 若要粘贴脚本,请右键单击 shell,然后选择“粘贴”。
echo "Enter your email address that is used to sign in to Azure:" && read upn && az ad user show --id $upn --query "Id" && echo "Press [ENTER] to continue ..."请记下对象 ID, 本快速入门的下一部分需要使用该 ID。
查看模板
本快速入门中使用的模板来自 Azure 快速启动模板。
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"metadata": {
"_generator": {
"name": "bicep",
"version": "0.26.54.24096",
"templateHash": "8629186205194254058"
}
},
"parameters": {
"keyVaultName": {
"type": "string",
"metadata": {
"description": "Specifies the name of the key vault."
}
},
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]",
"metadata": {
"description": "Specifies the Azure location where the key vault should be created."
}
},
"enabledForDeployment": {
"type": "bool",
"defaultValue": false,
"metadata": {
"description": "Specifies whether Azure Virtual Machines are permitted to retrieve certificates stored as secrets from the key vault."
}
},
"enabledForDiskEncryption": {
"type": "bool",
"defaultValue": false,
"metadata": {
"description": "Specifies whether Azure Disk Encryption is permitted to retrieve secrets from the vault and unwrap keys."
}
},
"enabledForTemplateDeployment": {
"type": "bool",
"defaultValue": false,
"metadata": {
"description": "Specifies whether Azure Resource Manager is permitted to retrieve secrets from the key vault."
}
},
"tenantId": {
"type": "string",
"defaultValue": "[subscription().tenantId]",
"metadata": {
"description": "Specifies the Microsoft Entra ID tenant ID that should be used for authenticating requests to the key vault. Get it by using Get-AzSubscription cmdlet."
}
},
"objectId": {
"type": "string",
"metadata": {
"description": "Specifies the object ID of a user, service principal or security group in the Microsoft Entra ID tenant for the vault. The object ID must be unique for the list of access policies. Get it by using Get-AzADUser or Get-AzADServicePrincipal cmdlets."
}
},
"keysPermissions": {
"type": "array",
"defaultValue": [
"list"
],
"metadata": {
"description": "Specifies the permissions to keys in the vault. Valid values are: all, encrypt, decrypt, wrapKey, unwrapKey, sign, verify, get, list, create, update, import, delete, backup, restore, recover, and purge."
}
},
"secretsPermissions": {
"type": "array",
"defaultValue": [
"list"
],
"metadata": {
"description": "Specifies the permissions to secrets in the vault. Valid values are: all, get, list, set, delete, backup, restore, recover, and purge."
}
},
"skuName": {
"type": "string",
"defaultValue": "standard",
"allowedValues": [
"standard",
"premium"
],
"metadata": {
"description": "Specifies whether the key vault is a standard vault or a premium vault."
}
},
"secretName": {
"type": "string",
"metadata": {
"description": "Specifies the name of the secret that you want to create."
}
},
"secretValue": {
"type": "securestring",
"metadata": {
"description": "Specifies the value of the secret that you want to create."
}
}
},
"resources": [
{
"type": "Microsoft.KeyVault/vaults",
"apiVersion": "2023-07-01",
"name": "[parameters('keyVaultName')]",
"location": "[parameters('location')]",
"properties": {
"enabledForDeployment": "[parameters('enabledForDeployment')]",
"enabledForDiskEncryption": "[parameters('enabledForDiskEncryption')]",
"enabledForTemplateDeployment": "[parameters('enabledForTemplateDeployment')]",
"tenantId": "[parameters('tenantId')]",
"enableSoftDelete": true,
"softDeleteRetentionInDays": 90,
"accessPolicies": [
{
"objectId": "[parameters('objectId')]",
"tenantId": "[parameters('tenantId')]",
"permissions": {
"keys": "[parameters('keysPermissions')]",
"secrets": "[parameters('secretsPermissions')]"
}
}
],
"sku": {
"name": "[parameters('skuName')]",
"family": "A"
},
"networkAcls": {
"defaultAction": "Allow",
"bypass": "AzureServices"
}
}
},
{
"type": "Microsoft.KeyVault/vaults/secrets",
"apiVersion": "2023-07-01",
"name": "[format('{0}/{1}', parameters('keyVaultName'), parameters('secretName'))]",
"properties": {
"value": "[parameters('secretValue')]"
},
"dependsOn": [
"[resourceId('Microsoft.KeyVault/vaults', parameters('keyVaultName'))]"
]
}
],
"outputs": {
"location": {
"type": "string",
"value": "[parameters('location')]"
},
"name": {
"type": "string",
"value": "[parameters('keyVaultName')]"
},
"resourceGroupName": {
"type": "string",
"value": "[resourceGroup().name]"
},
"resourceId": {
"type": "string",
"value": "[resourceId('Microsoft.KeyVault/vaults', parameters('keyVaultName'))]"
}
}
}
该模板中定义了两个 Azure 资源:
- Microsoft.KeyVault/vaults:创建 Azure 密钥保管库。
- Microsoft.KeyVault/vaults/secrets:创建密钥保管库机密。
可以在 Azure 快速入门模板中找到更多 Azure Key Vault 模板示例。
部署模板
选择下图登录到 Azure 并打开一个模板。 该模板将创建 Key Vault 和机密。
选择或输入以下值。
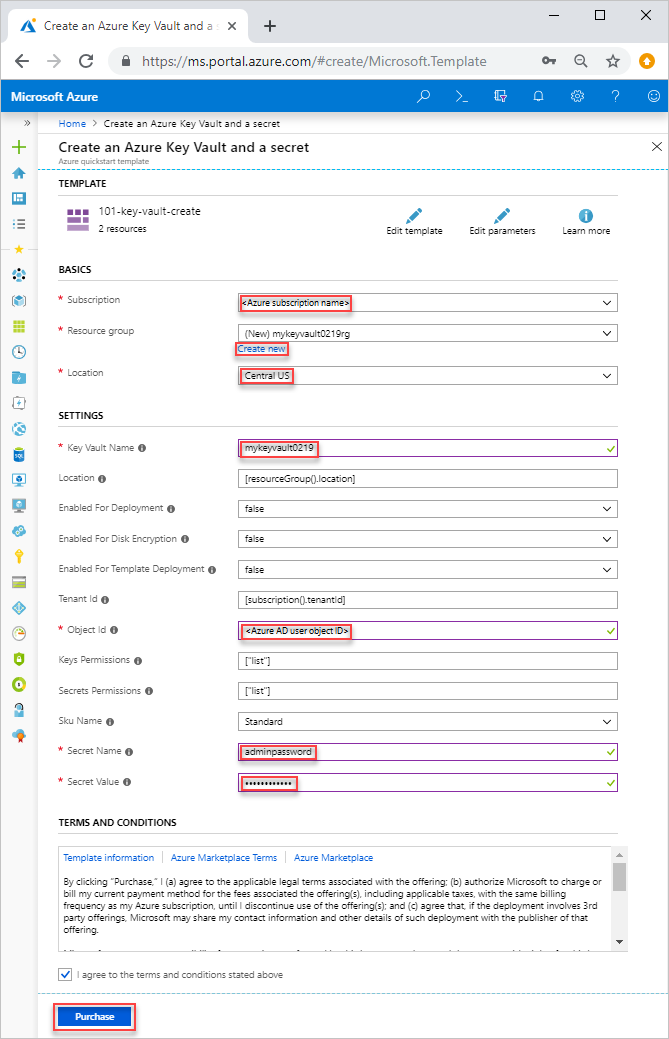
除非另有指定,否则请使用默认值创建密钥保管库和机密。
- 订阅:选择一个 Azure 订阅。
- 资源组:选择“新建”,输入资源组的唯一名称,然后单击“确定”。
- 位置:选择一个位置。 例如,中国北部。
- 密钥保管库名称:输入密钥保管库的名称,该名称在 .vault.azure.cn 命名空间中必须全局唯一。 在下一部分验证部署时,需要该名称。
- 租户 ID:模板函数会自动检索租户 ID。 不要更改默认值。
- AD 用户 ID:输入在先决条件中检索到的 Microsoft Entra 用户对象 ID。
- 机密名称:输入要存储在 Key Vault 中的机密的名称。 例如 adminpassword。
- 机密值:输入机密值。 如果存储密码,则建议使用在“先决条件”中创建的生成密码。
- 我同意上述条款和条件:选中。
选择“购买”。 成功部署密钥保管库后,你会收到通知:
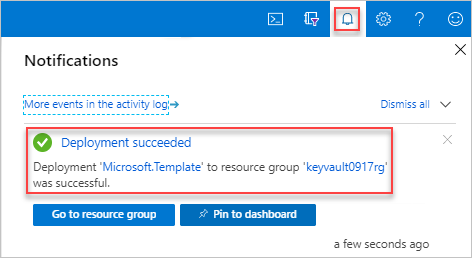
使用 Azure 门户部署模板。 除了 Azure 门户,还可以使用 Azure PowerShell、Azure CLI 和 REST API。 若要了解其他部署方法,请参阅部署模板。
查看已部署的资源
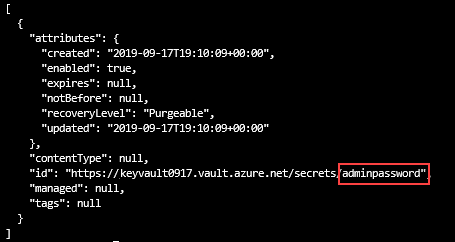
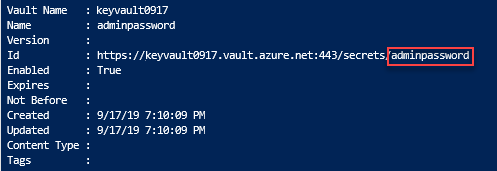
可以使用 Azure 门户检查 Key Vault 和机密,或者使用以下 Azure CLI 或 Azure PowerShell 脚本列出创建的机密。
echo "Enter your key vault name:" &&
read keyVaultName &&
az keyvault secret list --vault-name $keyVaultName &&
echo "Press [ENTER] to continue ..."
输出如下所示:
清理资源
其他 Key Vault 快速入门和教程是在本快速入门的基础上制作的。 如果打算继续使用后续的快速入门和教程,则可能需要保留这些资源。 如果不再需要资源组,可以将其删除,这将删除 Key Vault 和相关的资源。 使用 Azure CLI 或 Azure PowerShell 删除资源组:
echo "Enter the Resource Group name:" &&
read resourceGroupName &&
az group delete --name $resourceGroupName &&
echo "Press [ENTER] to continue ..."
后续步骤
在本快速入门中,你使用 ARM 模板创建了密钥保管库和机密,并验证了部署。 若要详细了解 Key Vault 和 Azure 资源管理器,请继续阅读以下文章。
- 阅读 Azure Key Vault 概述
- 了解有关 Azure 资源管理器的详细信息
- 请参阅 Key Vault 安全性概述