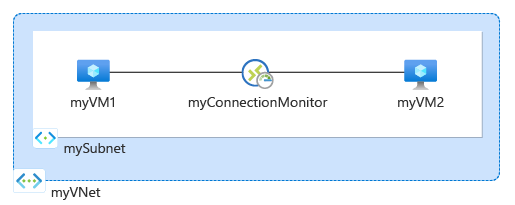
在虚拟机 (VM) 和终结点(例如另一 VM)之间成功通信对于组织来说可能很重要。 有时候,配置更改会导致通信中断。
在本教程中,你将了解如何执行以下操作:
- 创建虚拟网络
- 创建两个虚拟机
- 监视两个虚拟机之间的通信
- 诊断两个虚拟机之间的通信问题
如果没有 Azure 订阅,请在开始前创建一个试用版订阅。
先决条件
- 具有活动订阅的 Azure 帐户。
创建虚拟网络
在本部分,将创建包含两个子网和一个 Azure Bastion 主机的 myVNet 虚拟网络。 第一个子网用于虚拟机,第二个子网用于 Bastion 主机。
登录 Azure 门户。
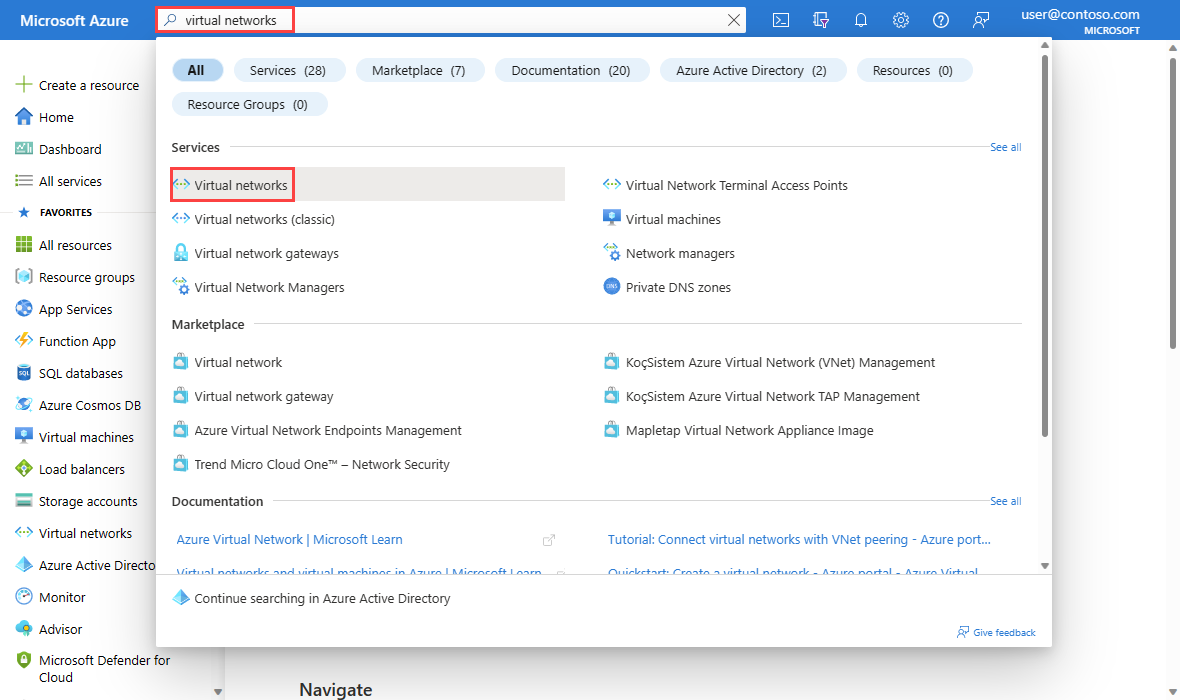
在门户顶部的搜索框中,输入“虚拟网络”。 在搜索结果中,选择“虚拟网络”。
选择“+ 新建”。 在“创建虚拟网络”的“基本信息”选项卡中,输入或选择以下值:
设置 值 项目详细信息 订阅 选择 Azure 订阅。 资源组 选择“新建”。
在“名称”中输入“myResourceGroup” 。
选择“确定”。实例详细信息 虚拟网络名称 输入“myVNet”。 区域 选择“中国东部”。 选择“IP 地址”选项卡,或选择页面底部的“下一步”按钮两次。
接受默认 IP 地址空间 10.0.0.0/16。
选择默认子网旁边的铅笔图标,将其重命名。 在“编辑子网”页的“子网详细信息”下,为“名称”输入 mySubnet,然后选择“保存”。
选择“查看 + 创建”。
检查设置,然后选择“创建”。
创建两个虚拟机
在本节中,你将创建两个虚拟机:myVM1 和 myVM2 以测试它们之间的连接。
创建第一个虚拟机
在门户顶部的搜索框中,输入“虚拟机”。 在搜索结果中,选择“虚拟机”。
在“虚拟机”中,选择“+ 创建”。
在“创建虚拟机”的“基本信息”选项卡中输入或选择以下信息。
设置 值 项目详细信息 订阅 选择订阅。 资源组 选择“myResourceGroup”。 实例详细信息 虚拟机名称 输入“myVM1”。 区域 选择“(亚太)中国东部”。 可用性选项 选择“无需基础结构冗余”。 安全类型 保留默认值标准。 映像 选择“Ubuntu Server 20.04 LTS - x64 Gen2”。 大小 选择大小或保留默认设置。 管理员帐户 身份验证类型 选择密码。 用户名 输入用户名。 Password 输入密码。 确认密码 重新输入密码。 选择“网络”选项卡,或选择“下一步: 磁盘”,然后选择“下一步: 网络”。
在“网络”选项卡上,选择以下值:
设置 值 网络接口 虚拟网络 选择“myVNet”。 子网 选择“mySubnet”。 公共 IP 选择无。 NIC 网络安全组 选择“无”。 选择“查看 + 创建”。
检查设置,然后选择“创建”。
创建第二个虚拟机
重复上一节中的步骤,创建第二个虚拟机,并输入 myVM2 作为虚拟机名称。
创建连接监视器
在本节中,创建一个连接监视器,监视通过 TCP 端口 3389 进行的从 myVm1 到 myVm2 的通信。
在门户顶部的搜索框中,输入“网络观察程序”。 选择“网络观察程序”。
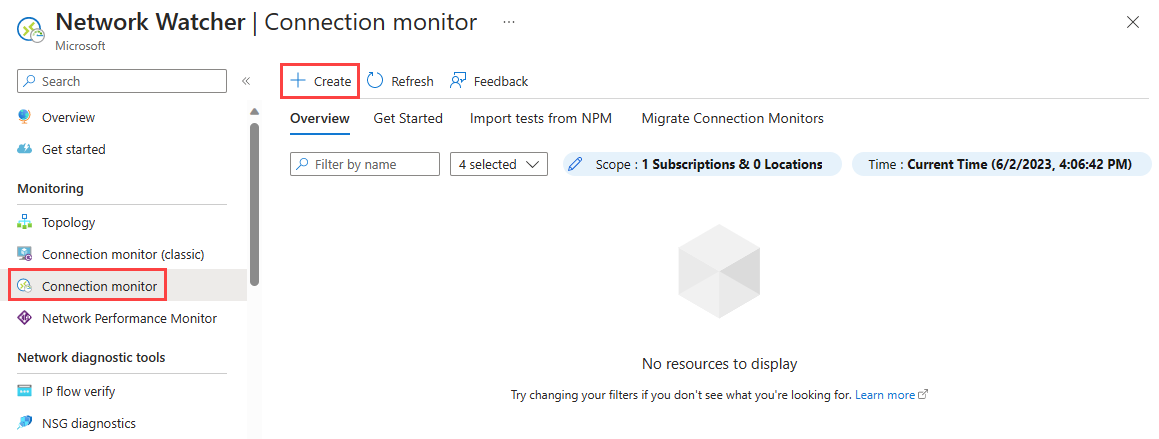
在“监视”下,选择“连接监视器”。
选择“+ 新建”。
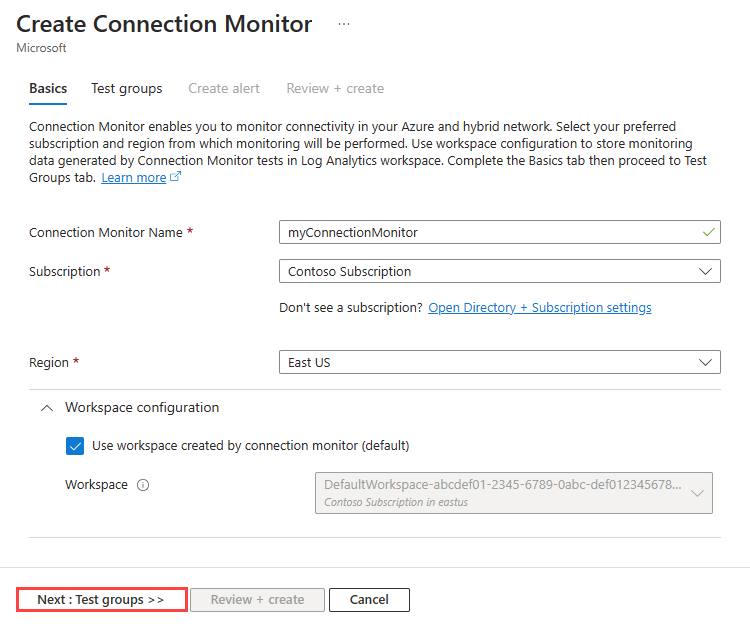
在“创建连接监视器”的“基本信息”选项卡中,输入或选择以下信息:
设置 值 连接监视器名称 输入 myConnectionMonitor。 订阅 选择订阅。 区域 选择“中国东部”。 工作区配置 虚拟机名称 输入“myVM1”。 区域 选择“中国东部”。 工作区配置 保留默认值。 选择“测试组”选项卡,或者选择“下一步:测试组”按钮。
在“测试组名称”中输入 myTestGroup。
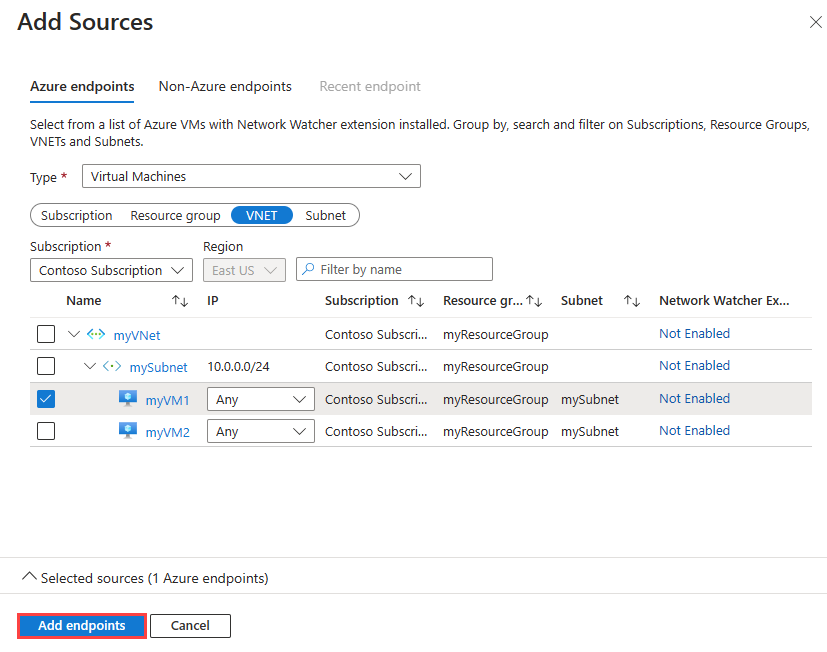
在“添加测试组详细信息”页中,选择“+ 添加源”以添加源虚拟机。
在“添加源”页中,选择“myVM1”作为源终结点,然后选择“添加终结点”。
注意
可以使用“订阅”、“资源组”、“VNET”或“子网”筛选器来缩小虚拟机列表的范围。
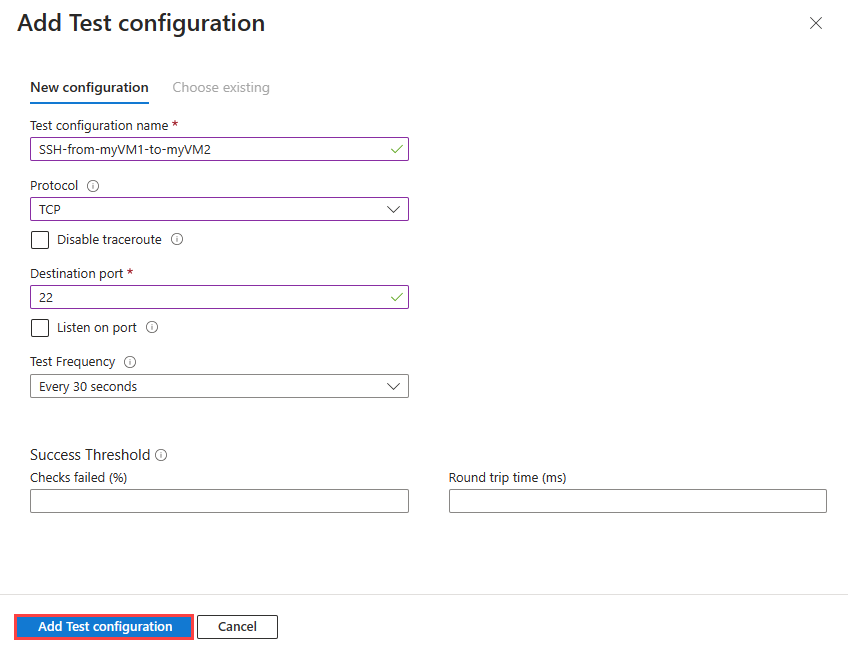
在“添加测试组详细信息”页中,选择“添加测试配置”,然后输入或选择以下信息:
设置 值 测试配置名称 输入 SSH-from-myVM1-to-myVM2。 协议 选择“TCP”。 目标端口 输入 22。 测试频率 选择默认值“每 30 秒”。 选择“添加测试配置”。
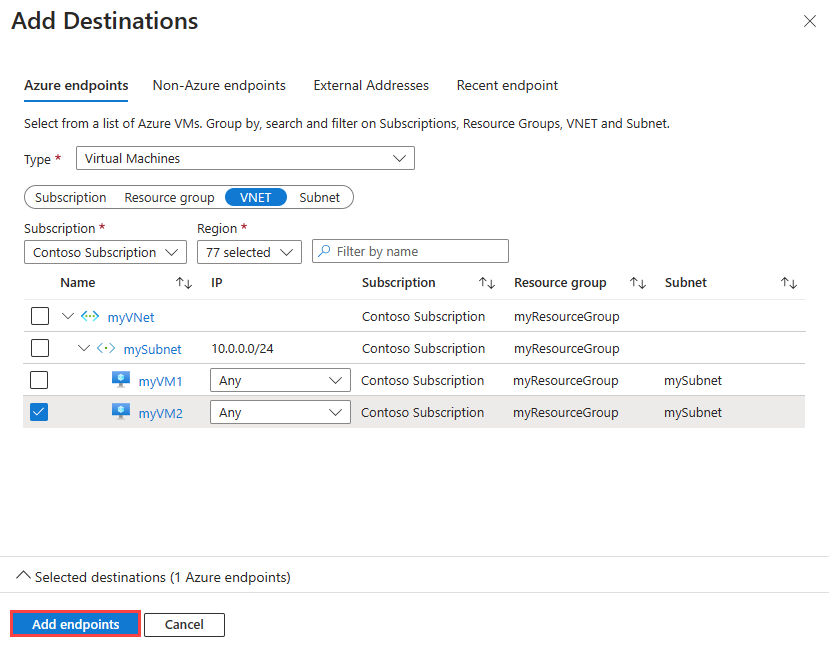
在“添加测试组详细信息”页中,选择“添加目标”以添加目标虚拟机。
在“添加目标”页中,选择“myVM2”作为目标终结点,然后选择“添加终结点”。
注意
除了“订阅”、“资源组”、“VNET”和“子网”筛选器之外,还可以使用“区域”筛选器来缩小虚拟机列表的范围。
在“添加测试组详细信息”页中,选择“添加测试组”按钮。
选择“查看 + 创建”,然后选择“创建”。
查看连接监视器
在本节中,你将查看在上一节中创建的连接监视器的所有详细信息。
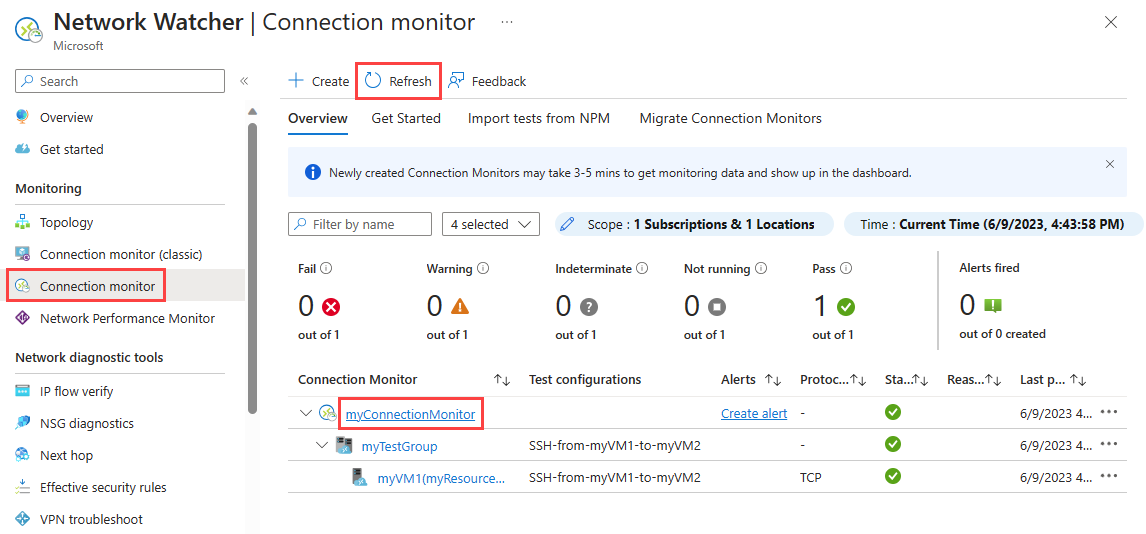
转到“连接监视器”页。 如果在连接监视器列表中看不到 myConnectionMonitor,请等待几分钟,然后选择“刷新”。
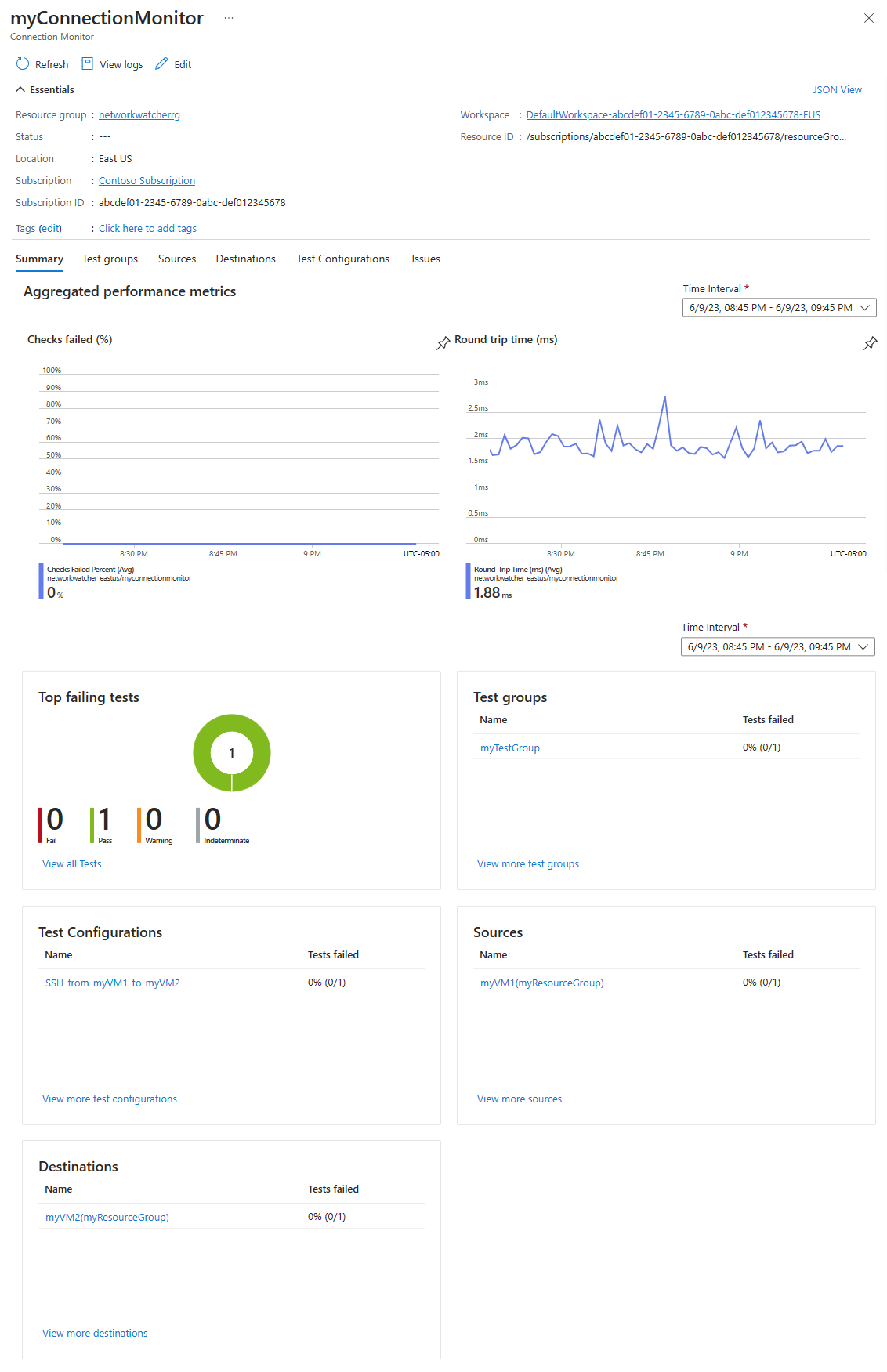
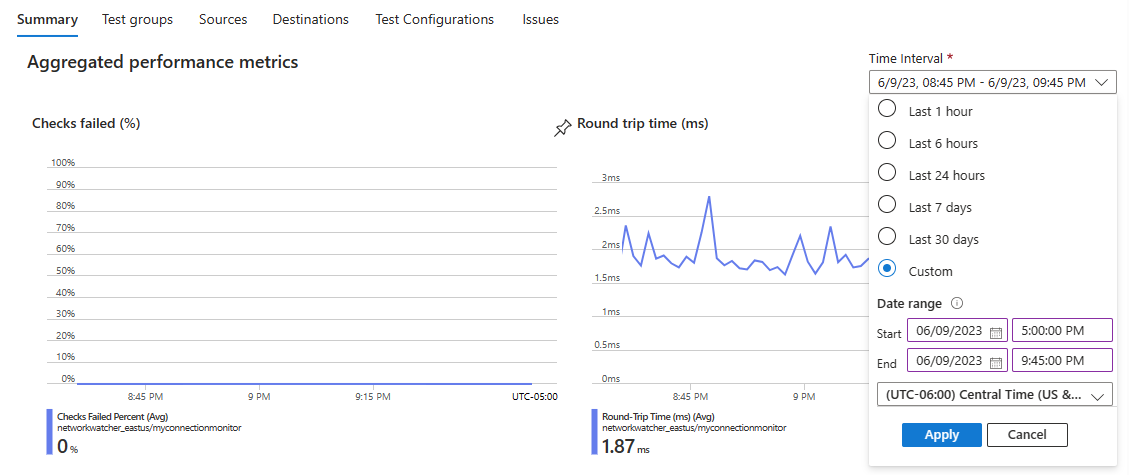
选择 myConnectionMonitor 以查看连接监视器的性能指标,例如往返时间和失败检查的百分比
选择“时间间隔”可调整时间范围,以查看特定时间段的性能指标。 可用时间间隔为“过去 1 小时”、“过去 6 小时”、“过去 24 小时”、“过去 7 天”和“过去 30 天”。 还可以选择“自定义”以指定自定义时间范围。
查看问题
在上一节创建的连接监视器监视 myVM1 与 myVM2 上的端口 22 之间的连接。 如果连接因任何原因失败,连接监视器将检测并记录故障。 在本节中,将通过停止运行 myVM2 来模拟问题。
在门户顶部的搜索框中,输入“虚拟机”。 在搜索结果中,选择“虚拟机”。
在“虚拟机”中,选择“myVM2”。
在“概述”中,选择“停止”以停止运行(解除分配)myVM2 虚拟机。
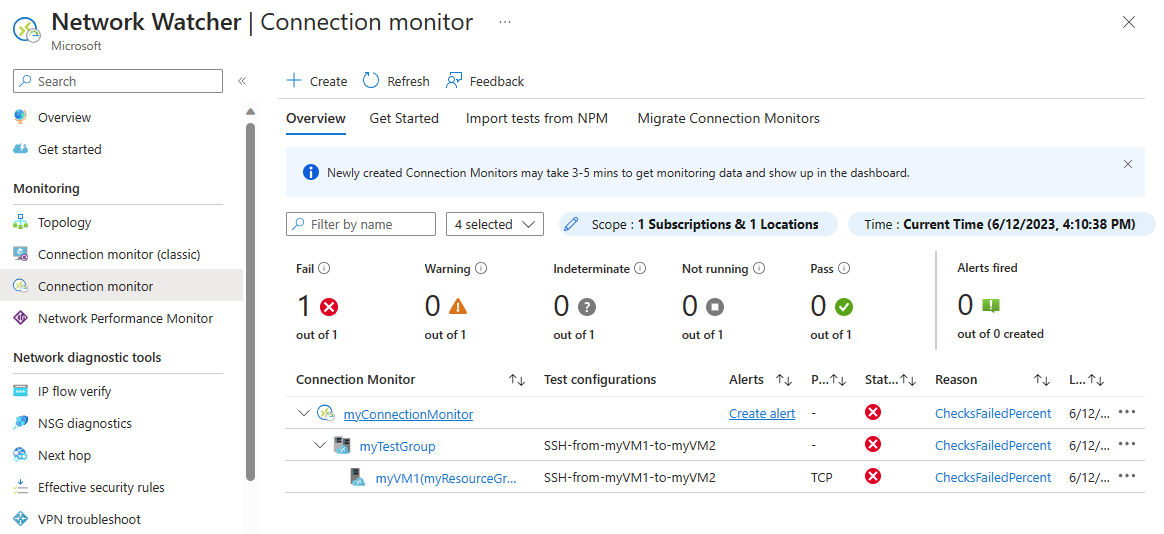
转到“连接监视器”页。 如果在仪表板中看不到失败,请选择“刷新”。
可以看到失败连接监视器的数量在停止运行 myVM2 后变为 1/1,在“原因”下,可以看到故障原因是 ChecksFailedPercent。
清理资源
不再需要 myResourceGroup 资源组时,将其及其包含的所有资源删除:
在门户顶部的搜索框中输入 myResourceGroup。 从搜索结果中选择“myResourceGroup”。
选择“删除资源组” 。
在“删除资源组”中,输入 myResourceGroup,然后选择“删除”。
选择“删除”以确认删除资源组及其所有资源。
下一步
若要了解如何监视虚拟机规模集网络通信,请转到下一篇教程: